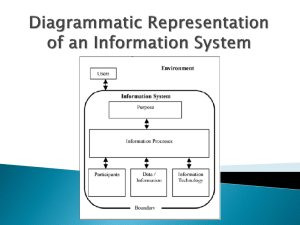
Bennett Jones - standrewsclubav.ca
advertisement

LEXPERT'S REVOLUTIONARY PAYMENT SOLUTIONS 2013 & BEYOND: LEGAL & REGULATORY COMPLIANCE PRIMER Lisa Abe-Oldenburg, Partner, Milos Barutciski, Partner, Stephen Burns, Partner Duncan Card, Partner Bennett Jones LLP June 3, 2012 Introduction Welcome! Program Overview 1. Our Faculty Lisa Abe-Oldenburg, Partner, Bennett Jones LLP Milos Barutciski, Partner, Bennett Jones LLP Stephen Burns, Partner, Bennett Jones LLP Duncan Card, Partner, Bennett Jones LLP Derek Colfer, Head of Mobile Innovation, Visa Canada Catherine Johnston, President and CEO, ACT Canada 2. Course Focus • • Both the "current state" of, and the future trends in, payment solution commercial, legal and regulatory issues Particular focus on: − Security & Privacy − Regulation Issues and Trends − Payment Solution Commercialization 3. Review of Particular Class Interests -2- Recent Payment Solution Developments Lisa Abe-Oldenburg -3- Introduction • • • • Mobile and Prepaid payment developments – apps and systems Who are the solution providers and what alliances are being formed The changing range of stakeholders The technologies involved: how are they being leveraged for added security and user flexibility? -4- Mobile and Prepaid payment developments • • • • • • TechNavio: Global NFC chip market to grow 135.63% over the period 2011-2015 ABI Research: 102 million NFC handsets shipped in 2012; 285M will ship in 2013; 500M in 2014; NFC-enabled smartphone shipments are anticipated to increase by 481% from 2012 to 2015 Deloitte: Expect 300 million NFC smartphones, tablets and eReaders sold in 2013 Frost & Sullivan: By 2015, NFC will be the most-used solution for mobile payment, enabling worldwide transactions totaling about $151.7 billion Gartner Research: 50% of smartphones will have NFC capability by 2015 Berg Insight: 86% of POS terminals in North America will accept NFC payments by 2017 -5- Mobile and Prepaid payment developments – apps and systems • • What is NFC? – near-field communication (e.g. 13.56MHz near- field radio) – Secure, close range, fast (advanced antennas) – Credentials can be exchanged or communicated via NFC technology – Card emulation mode, reader mode or both (P2P) Other options: QR Code & Cloud Based credential storage, management and mobile payments, barcode payments, bluetooth payments, passive NFC and RFID (stickers and fobs) payments and peer-to-peer (p2p) payments. -6- Mobile and Prepaid payment developments – apps and systems • Credentials could include not just Payment Credentials, but also Identification Credentials, Ticketing Credentials, Incentive/Reward Program Credentials, etc. • Credentials are stored in a part of a Secure Element (SE) • Secure Elements can be: – integrated/embedded in device hardware or core/motherboard – removable (iOS, USB, micro SD or SIM) – wearable (EMV chips in tags, fobs, bracelets) -7- Apps and Systems • • • • Mobile Payment via Cellphone – Visa’s First NFC Mobile Payments Trial - March 16, 2006 – Visa PayWave applet Mobile wallet Apps (e.g. Google wallet, Enstream's "Zoompass") – Store and access card credentials, e.g. prepaid, credit, debit, loyalty, etc. Square - mobile POS/card reader Digital Retail Apps - in-aisle payment for seamless customer experience -8- Apps and Systems • • • In November 2012, CIBC launched its Mobile Payment App (now available for Android and Blackberry), allowing contactless payment via Rogers smart phone and CIBC Credit Card In March 2013, Interac processed its first NFC mobile or contactless debit transaction in Canada, which was one of the first globally from a domestic debit network. This achievement in mobile innovation was accomplished in partnership with McDonald's Restaurants of Canada, the participating merchant, RBC Royal Bank, the participating financial institution, Moneris Solutions, the payment service provider facilitating the transactions, and BlackBerry, the mobile device provider. -9- Apps and Systems • Just a few weeks ago, 4 Canadian Credit unions announced that they will be the first financial institutions in Canada to offer remote deposit capture – the ability for depositors to use the camera in their mobile device to snap an image of the cheque they want to deposit and use their mobile banking app to deposit the item electronically. No more taking a cheque to a branch or an ATM. • BMO Bank of Montreal recently announced that consumers can sign up for their MasterPass enabled digital wallet called BMO Wallet in the coming weeks. Mobile wallets provide consumers with more payment options, allowing them to securely load branded credit, prepaid or debit cards into their mobile app or device. With banks, merchants and partners offering their own wallets, the competition will be fierce. - 10 - Who are the solution providers and what alliances are being formed • • • • • • NFC Forum – Certification (devices, programs, interoperability, "plug fests") – Specifications • Data exchange formats, Tag types, Record type definition, device interface controller, protocols – Testing and methodologies – Streamlining certification requirements with other industry organizations VISA and MC certification of SIM cards EMVCo , PTCRB, GCF, GSMA, the Smart Card Alliance, Global Platform and the Mobey Forum Education, information, best practices, addressing roadblocks and providing recommendations Merchant Services Business Association ACT Canada - 11 - Who are the solution providers and what alliances are being formed • In Canada, the federally-appointed Payments Systems Task Force asked the Financial Institutions to develop mobile standards, resulting in the publication by the Canadian Bankers Association of the Canadian NFC Mobile Payments Reference Model (or Guidelines) on May 14, 2012 – The guidelines in the Reference Model were developed and have been adopted by major Canadian banks and credit unions. For the rest of the industry, adherence is optional (e.g. by contract) – The Canadian FI's involved in this initiative (“Industry Initiative Participants”) recognized that : • End users trust FI's to provide safe and secure services and expect to be able to maintain control over which type of payment they use, how they access it and whether their payments have pass code protection • Merchants and consumers also expect transparency at point of sale. - 12 - Who are the solution providers and what alliances are being formed • • • The payment ecosystem takes the coordination of many parties to function effectively By providing early clarity on industry participation in the ecosystem, the guidelines will help stabilize and build efficiencies into the future deployment of mobile payments in Canada Through the guidelines, Industry Initiative Participants established a common reference model for NFC based mobile payments and offered a set of expectations for ecosystem participants. These expectations and the associated interactions create a common foundation, based on voluntary adherence, on which NFC mobile payment services in Canada may be built - 13 - The changing range of stakeholders • • • • • • • • • Smartphone/device/hardware manufacturers (OEMs, e.g. Nokia, Samsung, LG, HTC, BlackBerry, Motorola) Mobile OS providers (e.g. Blackberry, Windows, Android) Wireless/mobile telecom network operators (MNOs, e.g. Bell, Rogers, Telus) SIM card manufacturers (e.g. G&D, Gemalto) Cloud service providers (e.g. Google wallet) Financial institutions, card and credential issuers and acquirers Payment (e.g. credit and debit) network operators, e.g. Visa, MC, Interac Terminal (POS reader) manufacturers Payment Processors (e.g. Moneris) - 14 - The changing range of stakeholders • • • • • • • Trusted third parties (TSMs) for credential provisioning and management (authentication, certification), e.g. G&D, EnStream Mobile payment and wallet App developers and providers (e.g. Google) App stores, e.g. Apple Regulators, law enforcement, policy makers, industry associations Merchants, retailers, transportation, municipalities, governments, schools, hospitals, etc. Loyalty service providers Consumers - 15 - The technologies involved: how are they being leveraged for added security and user flexibility? • • Storage, provisioning and management of card credentials NFC vs. QR Code vs. Cloud – ID stored locally/physically (cards and chips) vs. centrally/online (software and databases) – Security issues, issuance, consumer device capabilities, merchant acceptance, transaction characteristic - 16 - The technologies involved: how are they being leveraged for added security and user flexibility? • • NFC: – Complex issuance: TSM and Secure Element ecosystem – Consumer device capabilities growing: 9 out of the top 10 OEMs support it – Merchant acceptance: Standards based; Growing in select developed countries; US migration to EMV may speed adoption – Transactions treated as "Card Present" – liability risk shifts to card issuer QR Codes: – Simpler issuance: Cloud based mobile application – Consumer device capabilities: Ubiquitous – Only requires data connection; may require camera – Merchant acceptance: Fragmented – No standards; numerous solutions available; Security model not yet fully defined; may require wireless connection – Transactions treated as "Card Not Present" – liability risk shifts to acquirer/merchant - 17 - The technologies involved: how are they being leveraged for added security and user flexibility? • • Cloud – Simpler issuance: Cloud based mobile application – Consumer device capabilities: Ubiquitous – Only requires data connection – Merchant acceptance: Fragmented – No standards; Security model not yet fully defined; requires wireless connection – Transactions treated as "Card Not Present" – liability risk shifts to acquirer/merchant Mobile payments levels of transaction: – Convenience vs. high value/risk transactions • Convenience transactions are low value/risk (e.g., under $50) and may be effected just by waving the mobile device at the POS terminal • High value/risk (e.g., $50 and greater) tends to require a combination of a mobile device at the POS and a pass code to be entered - 18 - The technologies involved: how are they being leveraged for added security and user flexibility? • SIM card vs. Hardware chip – Control and cost issues • Who will win the wallet war? – Balance between security and convenience; consumers demand both • Requirements for global scale adoption of mobile payments: – Development of industry standards – Overcoming barriers to acceptance – Device and reader terminal availability – Secure provisioning of card credentials • EMV and ISO standards provide security, reliability and interoperability; align with existing card terminal technology - 19 - Security & Privacy Issues Stephen Burns - 20 - PRIVACY & SECURITY TODAY'S DISCUSSION • • • • • A Privacy Primer The Cyber Threat Why We Care The Changing Face of Reasonable Some Practical Advice - 21 - PRIVACY IN A NUT SHELL - 22 - PERSONAL INFORMATION • Personal information is any information about an identifiable individual, other than the person's business title or business contact information when used or disclosed for the purpose of business communications. For example: – Age, income, marital status, dependents and ethnic origin – Social insurance number, drivers license number, credit card numbers, – Employment applications, resumes, reference letters, transcripts – Leasor information: compensation, lease terms, – Internet activity and computer usage – Emergency Response Plans: contact information, schools, • Personal information does not include anonymous or non-personal information (i.e., information that cannot be associated with or tracked back to a specific individual). - 23 - TEN PRINCIPLES • • • • • • • • • • Accountability Identifying Purposes Consent Limiting Collection Limiting Use, Disclosure & Retention Accuracy Safeguards Openness Individual Access Challenging Compliance - 24 - PRIVACY THRESHOLD An organization may collect, use or disclose personal information only for purposes that a reasonable person would consider are appropriate in the circumstances. Where an organization collects, use or discloses personal information, it may do so only to the extent that is reasonable for meeting the purposes for which it was collected, used or disclosed. - 25 - FOUR KEY COMPLIANCE QUESTIONS: • • • • Is the collection, use or disclosure of the personal information for a reasonable purpose? Is the personal information to be collected, used or disclosed limited to that which is necessary to meet the purpose? Is the collection, use or disclosure of the personal information authorized by law without the need to obtain consent from or provide notice to the individuals in question? Where collection, use or disclosure without consent from or notice to the individuals in question is not authorized by law, has the organization obtained consent from or provided notice to the individuals in question for such collection, use or disclosure? - 26 - ACCURACY Personal information shall be as accurate, complete, and up-to-date as is necessary for the purposes for which it is to be used. An organization must make a reasonable effort to ensure that any personal information collected, used, or disclosed by or on behalf of an organization is accurate and complete. - 27 - SAFEGUARDS Personal information shall be protected by security safeguards appropriate to the sensitivity of the information. An organization must protect personal information that is in its custody or under its control by making reasonable security arrangements against such risks as unauthorized access, collection, use, disclosure, copying, modification, disposal or destruction - 28 - ACCOUNTABILITY An organization is responsible for personal information in its possession or custody, including information that has been transferred to a third party for processing. The organization shall use contractual or other means to provide a comparable level of protection while the information is being processed by a third party. An organization is responsible for personal information that is in its custody or under its control. Where an organization engages the services of a person, whether as an agent, by contract or otherwise, the organization is, with respect to those services, responsible for that person’s compliance with this Act. - 29 - OUTSOURCING (AB) OUTSIDE CANADA • Service provider: “any organization, including … a parent corporation, subsidiary, affiliate, contractor or subcontractor, that, directly or indirectly, provides a service for or on behalf of another organization” • Policies and practices to include information about: – the countries outside Canada in which the collection, use, disclosure or storage of personal information occurs or may occur – the purposes for which the service provider has been authorized to collect, use or disclose personal information for or on behalf of the organization • Written information must be made available on request - 30 - OUTSOURCING (AB) NOTICE REQUIRED • Notification is required when: – personal information is collected with consent by a service provider outside Canada – an organization transfers personal information collected with consent to a service provider outside Canada • Notification can be in writing or oral. Must include: – the way an individual may obtain access to written information about the organization’s policies and practices – the name or position name or title of a person who can answer questions about the collection, use, disclosure or storage of personal information by service providers outside Canada • Notice is in addition to general notification under s. 13 - 31 - BREACH REPORTING (AB) • Section 34.1 - organizations must notify the Commissioner of any “incident involving the loss of or unauthorized access to or disclosure” of personal information where a reasonable person would consider that there exists a real risk of significant harm to an individual • Must report “without unreasonable delay” • It is an offence not to notify the Commissioner of a breach under s. 34.1 - 32 - BREACH REPORTING (AB) • Section 19, PIPA Regulation: – description of circumstances of the incident – the date / time period of the incident – description of the personal information involved – an assessment of the risk of harm to individuals – estimated # of individuals – steps taken to reduce the risk of harm to individuals – steps taken to notify individuals of the incident – name/contact information of someone who can answer questions • OIPC AB Breach Notification Form: http://www.oipc.ab.ca/Content_Files/Files/Publications/Breach_Report_For m_2010.pdf - 33 - FEDERAL CHANGES COMING? • • The Privacy Commissioner of Canada released a position paper on May 23, 2013 which offers a roadmaps for modernizing Canada's federal private-sector privacy law Recommendations 1. Stronger enforcement powers • e.g. statutory damages to be administered by the Federal Court, providing the Privacy Commissioner with order-making powers and/or the power to impose administrative monetary penalties where the circumstances warrant. 2. Breach notification and application of penalties for breaches in certain cases 3. Increase transparency • Increased public reporting requirements regarding the use of an exception under PIPEDA which allows law enforcement agencies and government institutions to obtain personal information from companies without consent or a warrant 4. Promote accountability - 34 - THE CYBER THREAT - 35 - THE CYBER THREAT Numerous potential adversaries with differing motivations using a variety of techniques • Adversaries – Sovereign states (e.g. targeted espionage) – Corporate Espionage – Criminals – Hackers / Hacktivists (hacker activists) • Motivations / Objectives – Stealing competitive intelligence – Stealing intellectual property – Siphoning off money – Disrupting operations – Bragging rights - 36 - NATURE OF CYBER ATTACKS • • Multi-pronged approach to penetrate a targeted company – Socially engineering current employees – Inserting moles into the company – Launching cyber attacks over an extended period New Technologies and New Threats – Social media – Mobile banking – Cloud computing – Bring-your-own-device ("BYOD") – Unstructured or "big data" - 37 - SOME CURRENT DATA • According to Verizon 2012 Data Breach Investigations Report: – 855 incidents in 2012, 174 million compromised records. – 98% of breaches stemmed from external agents – 4% of breaches implicated internal employees – 58% of all data theft tied to activist groups – 81% utilized some form of hacking – 96% of attacks were not highly difficult – 85% of breaches took weeks or more to discover – 92% of incidents were discovered by a third party - 38 - INDUSTRIES TARGETED Compromised records by industry group with breaches >1M records removed Taken from the Verizon 2012 Data Breach Investigations Report - 39 - WHY WE CARE - 40 - WHY WE CARE • • • 3 critical characteristics of information that are at risk from cyber attackers: – Confidentiality – Integrity – Availability Attacks on information assets can have an indirect impact on physical assets A cyber attack can also target physical assets more directly (stuxnet worm) • Accuracy, Safeguards and Accountability - 41 - COST OF A BREACH • • • • Lost opportunities, future revenue and market share Reputational harm – Long-term loss of confidence among customers and business partners – Diminished credibility Data loss / information theft Breach notification and regulatory oversight / investigation - 42 - BREACH RESPONSE COSTS • Expenses associated with a comprehensive breach response – Forensic examination (external or internal) to determine the severity and scope of a breach involving compromised computer systems or networks – Hiring third party vendors specializing in comprehensive breach response to provide call centre services – Credit or identity monitoring – Identity restoration if affected parties suffer actual identity theft – Public relations consultation fees - 43 - SECURITIES LAWS • Companies may be required to disclose when its data has been compromised pursuant to Canadian securities laws • New guidance from the SEC specifically outlining how publicly traded companies should disclose online attacks – Minimal disclosure has resulted from this guidance • Reputation, credibility and the speed of disclosure - 44 - LIABILITY FOR BREACH • • Fines and penalties from regulatory and industry bodies Potential civil liability exposure to numerous potential claimants (e.g. consumers, banks, etc.) – cost of defending claims + cost of settlement – Negligence – Breach of warranty – Failure to protect data – Failure to disclose defects in products or services regarding capabilities of protecting data – Unreasonable delay in remedying suspension of service or loss of data – Violations of applicable laws – Unfair or deceptive trade practices - 45 - "NEW" TORTS OF PRIVACY • Starting Point: – D. Warren & L.D. Brandeis, “The Right to Privacy” (1890) 4 Harv. L. R. 193 – William L. Prosser, “Privacy” (1960), 48 Cal. L. R. 383 • Prosser's Four Torts 1. Intrusion upon the plaintiff’s seclusion or solitude, or into his private affairs. 2. Public disclosure of embarrassing private facts about the plaintiff. 3. Publicity which places the plaintiff in a false light in the public eye. 4. Appropriation, for the defendant’s advantage, of the plaintiff’s name or likeness. – US Restatement (Second) of Torts (2010): General Principle § 652 1. One who invades the right of privacy of another is subject to liability for the resulting harm to the interests of the other. 2. The right of privacy is invaded by: a) unreasonable intrusion upon the seclusion of another, as stated in 652B; or b) appropriation of the other's name or likeness, as stated in 652C; or c) unreasonable publicity given to the other's private life, as stated in 652D; or d) publicity that unreasonably places the other in a false light before the public, as stated in 652E. - 46 - "NEW" TORTS OF PRIVACY • Statutory Torts of Invasion of Privacy – British Columbia, Privacy Act – Manitoba, Privacy Act – Saskatchewan, Privacy Act – Newfoundland, Privacy Act • Damages for Breach of PIPA – Alberta, Personal Information Protection Act – British Columbia, Personal Information Protection Act • Damages for Breach of PIPEDA (Humiliation) – Federal: Personal Information Protection and Electronic Documents Act - 47 - "NEW" TORTS : JONES v TSIGE (ONCA) • One who intentionally intrudes, physically or otherwise, upon the seclusion of another or his private affairs or concerns, is subject to liability to the other for invasion of his privacy, if the invasion would be highly offensive to a reasonable person. • "The key features of this cause of action are: – first, that the defendant’s conduct must be intentional, within which I would include reckless; – second that the defendant must have invaded, without lawful justification, the plaintiff’s private affairs or concerns; and – third, that a reasonable person would regard the invasion as highly offensive causing distress, humiliation or anguish" • Damages …"proof of harm to a recognized economic interest is not an element of the cause of action … given the intangible nature of the interest protected, damages for intrusion upon seclusion will ordinarily be measured by a modest conventional sum …" - 48 - THE CHANGING FACE OF REASONABLE - 49 - A GROWING THREAT "Terrorism does remain the FBI's top priority, but in the not-too-distant future, we anticipate that the cyber threat will pose the number-one threat to our country" Robert Mueller, Director of the FBI - 50 - LOTS OF EXAMPLES …. - 51 - CANADA'S CYBER SECURITY STRATEGY • • • • • • Three pillars 1. Securing government systems 2. Partnering to secure vital cyber systems outside the federal government (e.g. critical infrastructure) 3. Helping Canadians to be secure online Canadian Cyber Incident Response Centre National Strategy and Action Plan for Critical Infrastructure Canada-United States Action Plan for Critical Infrastructure Council of Europe Convention on Cybercrime RCMP – Integrated Cyber Crime Fusion Centre - 52 - COUNCIL OF EUROPE CONVENTION ON CYBERCRIME • • • • The first international treaty addressing computer crime and internet crimes by harmonizing national laws, improving investigative techniques and increasing cooperation among nations. Entered into force on July 1, 2004 As of May 2013, 39 states had ratified the convention, and a further 11 states had signed the convention but not ratified it. Canada signed the treaty on November 23, 2011, but has not yet ratified the convention. - 53 - CANADA-UNITED STATES ACTION PLAN FOR CRITICAL INFRASTRUCTURE • • • Announced on July 13, 2010 by Janet Napolitano, Secretary of the U.S. Department of Homeland Security, and Vic Toews, Minister of Public Safety Canada Purpose – strengthen the safety, security and resilience of critical infrastructure in the U.S. and Canada through an enhanced cross-border approach – Enhance coordination and cooperation and facilitate continuous dialogue among cross-border stakeholders to better prevent, respond to, and recover from critical infrastructure disruptions Three key elements 1. Partnerships 2. Information Sharing 3. Risk Management - 54 - PCI - DATA SECURITY STANDARDS • • • Payment Card Industry (PCI) Data Security Standards (DSS) apply to all organizations that hold, process or exchange credit card information. On February 5, 2013, the Cloud Special Interest Group of the PCI Security Standards Council released the PCI DSS Cloud Computing Guidelines to provide specific guidance on the use of cloud computing and maintaining PCI controls in cloud environments. The guidelines are intended for use by organizations investigating, adopting or using cloud computing services as part of a cardholder data environment - 55 - OFFICE OF THE SUPERINTENDENT OF FINANCIAL INSTITUTIONS • OSFI is concerned with the rapid evolution of cyber attacks in terms of frequency, fire power and target • OSFI is planning on increasing its resources in the area of operational risk in order to do more reviews of federally regulated financial institutions (FRFIs), including review of technology risk with a focus on cyber security. - 56 - EUROPEAN CENTRAL BANK • Recommendations for the Security of Internet Payments (January 31, 2013) – Developed by the European Forum on the Security of Retail Payments (SecuRe Pay) – Payment Security Providers (PSPs) have until February 1, 2015 to implement the recommendations – Recommendations, key considerations and best practices applicable to governance authorities PSPs – Key Recommendation – The initiation of internet payments as well as access to sensitive payment data should be protected by strong customer authentication – Proposal – PSPs will accept liability for a fraudulent transaction is payment was properly authorized - 57 - US TREASURY DEPARTMENT • Financial Crimes Enforcements Network (FinCEN) – "Application of FinCEN's Regulations to Persons Administering, Exchanging, or Using Virtual Currencies" – March 18, 2013 – Guidance clarifying how regulations by FinCEN pursuant to the Bank Secrecy Act apply to "users", "administrators" and "exchangers" of "convertible virtual currency" - 58 - PRACTICAL STEPS - 59 - PATH FORWARD • • • • • • • • Identify the most sensitive, 'at risk' information Prioritize the protection of such information Limit access Implement policies and practices Implement real-time monitoring to detect and respond to intrusions Balance cyber security measures against other company objectives (e.g. productivity or collaboration across business boundaries) Benchmark internally and externally Monitor for changing standards - 60 - KEY QUESTIONS? • • • How will systems, applications and information be secured (technical, procedural, physical, contractual measures)? Are there obligations to third parties in respect of their information (confidential, privacy, other)? – Is further outsourcing permitted? – Is consent of a third party required? – What amendments to third party notices / agreements will be required? – Will amendments to privacy policies / practices be required? How will incidents be handled? – Breach Notification – Investigation – Mitigation – Reporting - 61 - Market Issues Duncan Card - 62 - Market Issues – from a legal and regulatory perspective: 1. The number (and specialized roles) of payment solution participants seems to be growing exponentially. Long way from handing over a banknote in exchange for goods or services. The days of only credit intermediaries and third party "brand credit services" between the payor, merchant, each of their banks and the "brand creditor" are long gone. NOW…..a host of value-add intermediaries from turn-key payment services for on-line transactions (PayPal), encryption and security services like authentication, chip manufacturers, payment "apps", device manufacturers to facilitate payment information transfer and enable transactions, to payment processors, network solution providers, affinity programs, payment software management tools, and even consulting services related to payment psychology and sociology. - 63 - 2. Contributor/Participant Integration…especially as merchants provide their own credit accounts; telco's form banks to facilitate payment solutions, online and otherwise; mobile telephones have become "wireless handheld devices" that enable direct data transmission for payment, transaction records, and authentification; Internet websites become "web enablers", such as Gmail (which integrates Google Wallet via a "$" icon to, for example, attach money to your email); perhaps "brand creditors" or telcos or large ISPs will acquire and vertically integrate payment processors, like Visa's acquisition of Cyber Source/Authorize.net – many others; there is also sector integration via personnel mobility…e.g., where the co-founder of Google Wallet (Rob von Behren) joined Braintree!; lastly…First Data bought, (then spun-off), Western Union (2006), but KKR was betting on continued consolidation demand when (in 2007) it, through a leveraged buyout, bought First Data for $26 billion – then First Data bought ICICI Bank's POS business ($80 million) – on and on (by the way, First Data's EVP and General Counsel's name…David Money – natch). 3. Consumer Demand • • • • security ease of use mobility speed • • • • integrated into apps accountability – substance – trust payment – "content" integration (Google Wallet) security (again) - 64 - Mobile Payments Regulation Lisa Abe-Oldenburg - 65 - Introduction • • • • • • • • Federal vs. Provincial Regulation Not all payments are regulated Payment Card Networks Act Report of the task Force for the Payments System Review Canadian Bankers Association Guidelines for Mobile Payments Recent amendments to CPA rules and standards Consumer Protection Issues Code of Conduct for the Debit and Credit Industry - 66 - Federal Regulation • • • • • • • Bank Act Federal Act respecting the Canadian Payments Association and the regulation of Systems and arrangements for the making of payments (Canadian "Payments Act") Federal Act respecting payment card networks ("Payment Card Networks Act") Federal Proceeds of Crime (Money Laundering) and Terrorist Financing Act Federal Payment Clearing and Settlement Act Federal Bills of Exchange Act Federal Competition Act - 67 - Federal Regulations • • • • • • The Financial Consumer Agency of Canada, established under section 3 of the Financial Consumer Agency of Canada Act, is responsible for supervising payment card network operators to determine whether they are in compliance with the provisions of this Payment Card Networks Act and the regulations Federally‐appointed Payments Systems Task Force, Canada’s financial institutions (FIs) are taking a leadership role in the area of the emerging field of mobile payments. Canadian Bankers Association (CBA) mobile guidelines Big Data issues – reform is coming Patchwork of Federal and provincial public sector and private sector privacy laws Federal Personal Information Protection and Electronic Documents Act ("PIPEDA") - 68 - Provincial Regulation • Consumer protection laws – provincial statutes and regulations – Most Canadian provinces have enacted laws that govern gift/prepaid and credit cards – BC • Prepaid Purchase Cards Regulation • Business Practices and Consumer Protection Act – Alberta • Reg 146/2008 Gift Card Regulation • Fair Trading Act and Cost of Credit Disclosure Regulation – Manitoba • Consumer Protection Act and Regulations • Prepaid Purchase Card Regulation • Gift Cards Act • Cost of Credit Disclosure Act - 69 - Provincial Regulation • Consumer protection laws – provincial statutes and regulations – Ontario • Consumer Protection Act and Regulations (cover gift and credit cards) – Nova Scotia • Consumer Protection Act and Regulations • Gift Card Regulations – PEI • Consumer Protection Act • Gift Cards Act and Regulations – Quebec • Consumer Protection Act • Money-Services Businesses Act – Also laws in NB, Sask, Nfld, Yukon, Nunavut - 70 - Not all payments are regulated • For example: – mobile p2p payments – loyalty, rewards or points cards, although privacy, ecommerce and advertising laws still apply – AML using prepaid cards • CPA makes rules, bylaws, standards that apply to payments exchanged by members who use these systems for clearing and settlement Voluntary commitments and codes of conduct – for the credit and debit card industry in Canada – to protect the interests of customers of financial institutions • - 71 - Payment Card Networks Act, S.C. 2010, c. 12, s. 1834 • • • • Purpose – to regulate national payment card networks and the commercial practices of payment card network operators "payment card network" means an electronic payment system – other than a prescribed payment system – used to accept, transmit or process transactions made by payment card for money, goods or services and to transfer information and funds among issuers, acquirers, merchants and payment card users. "payment card" means a credit or debit card – or any other prescribed device – used to access a credit or debit account on terms specified by the issuer Does not cover prepaid, loyalty, rewards or points cards - 72 - Payment Card Networks Act • • • "issuer" means an entity or provincial Crown corporation that issues payment cards "acquirer" means an entity that enables merchants to accept payments by payment card by providing merchants with access to a payment card network for the transmission or processing of those payments. "payment card network operator" means an entity that operates or manages a payment card network, including by establishing standards and procedures for the acceptance, transmission or processing of payment transactions and by facilitating the electronic transfer of information and funds - 73 - Report of the Task Force for the Payments System Review • Recommendations – request from the federal government’s Task Force for the Payments System Review that financial institutions develop mobile payment standards – Canadian Banker's Association established guidelines for various participants in the Canadian mobile commerce ecosystem, which most Canadian banks and credit unions have agreed to adhere to - 74 - Canadian Bankers Association Mobile Payments Guidelines (NFC Mobile Payments Reference Model) • • • Objective: to address challenges and provide a framework for the interactions between the different ecosystem participants. Interoperability between the Mobile Network Operators (MNOs, e.g. Rogers, Bell, Telus, Public Mobile, Wind, Videotron) and payment networks (e.g. Visa, MasterCard, Interac) is a key objective for these guidelines. The guidelines outline the functional elements, roles and responsibilities, and interaction models needed for the development of an effective, affordable, and consumer and merchant‐friendly NFC based mobile payments system in Canada Binds only those banks and credit unions that participated in its development (along with their partners), but all participants need to be aware of their requirements - 75 - Canadian Mobile Payments Guidelines (cont.) • Canadian mobile payments solution framework and ecosystem – convenient, open, safe and secure ecosystem – Typically, payment credentials and mobile device hardware are managed by different organizations. This creates a unique challenge as it requires multiple parties to work together to successfully deliver NFC mobile payment services. – The guidelines are limited to the payment model in which payment card credentials are stored on a SIM card or embedded in the secure element of a smartphone, and payment is effected by a user selecting a payment method from the "mobile wallet" stored on the smartphone and tapping the smartphone on an NFC-enabled point-of-sale device. This payment model is presently being rolled out by Canadian financial institutions and mobile network operators. - 76 - Canadian Mobile Payments Guidelines (cont.) • Canadian mobile payments solution framework and ecosystem – Guidelines support Visa, MasterCard and Interac specifications for NFC transactions requiring mobile devices to support the EMV mode and the MSD mode – Guidelines also contain elements from various other guidelines and regimes, including SEPA, GSMA/EPC, EMVCo, GlobalPlatform, PayEz and AFSCM. – focus is on the software required for interoperability of components, NFC mobile devices and POS systems – credential issuers will be able to operate on various NFC mobile devices – NFC contactless reader compliant to ISO 14443 Type A or ISO 14443 Type B will be able to communicate with any NFC mobile device; and any over-the-air platform will be able to communicate with any credential issuer - 77 - Canadian Mobile Payments Guidelines (cont.) • Wallet features and functionality – While the guidelines address both hardware and software issues, the focus is on software; in particular mobile wallet software. The guidelines outline procedures related to mobile wallet design, installation on mobile devices, and execution of mobile payments, including a section on wallet and payment application features, functionality and security – Three types of mobile wallets: • Proprietary wallet design - only payment credentials from the wallet provider may be used to make a payment • Collective wallet design - payment credentials from a group of credential issuers may be used to make a payment • Open wallet design - payment credentials from multiple credential issuers can be used to make payments – Open wallets require agreements and business relationships between credential issuers and wallet providers. - 78 - Canadian Mobile Payments Guidelines (cont.) • Wallet features and functionality – The guideline acknowledges that the industry will gravitate toward proprietary and collective wallets – In order to promote openness, the guideline does not allow mobile wallets, mobile network operators, original equipment manufacturers, secure domain managers and credential issuers to restrict access to payment applications from debit and credit payment networks, prepaid products, transit and loyalty products, and products issued in a foreign currency. – Emphasis on consumer choice for which payment types may be embedded on a smartphone and for whether use will be password protected. - 79 - Canadian Mobile Payments Guidelines (cont.) • Enablement and lifecycle management – Setup steps needed to install, use, maintain and terminate a mobile wallet and payment application on a mobile device, securely bind the applications and manage these applications over customer lifecycle events (e.g. lost or stolen phones) – Importance of sound contractual business relationships among the various participants in the mobile payment ecosystem – Mention possibility of the creation of a central hub organization or central controlling authority to manage those relationships. No detail provided as organization structure, but likely different from the self-regulatory organization proposed by the Task Force for the Payments System Review - 80 - Canadian Mobile Payments Guidelines (cont.) • Transactions – Once the initial setup is complete, an NFC based mobile payment transaction may be performed. – Certain steps are required to perform an NFC mobile payment. The solution is designed to consider low value, high value and high risk transactions. The solution is characterized by a radio frequency short read range distance that requires the mobile handset to be presented close to the contactless reader to enable a transaction. - 81 - Canadian Mobile Payments Guidelines (cont.) • Loyalty and rewards – Loyalty & Rewards is a rapidly evolving space and there are many types of loyalty and reward programs available to consumers (e.g. bonus points and cash‐back programs, loyalty rewards redemptions, merchant‐funded discount and promotional programs, coupons and vouchers) – Sets out guidelines for ensuring that these programs can be integrated with NFC mobile payments and how loyalty and rewards programs, couponing rebates and vouchers will operate, whether operated by merchants, issuers or other ecosystem participants – Merchants and application developers must be mindful to follow the standards set out in the guidelines, including the use of ISO/IEC 14443 for the transmission of loyalty and rewards data using NFC - 82 - Canadian Mobile Payments Guidelines (cont.) • Data and security – General guideline that each ecosystem participant should only have access to the minimum information required to perform its primary role. – Default should be to protect consumer and merchant data – It is not clear who would have access to consumer purchasing information that would be of interest to merchants. – Detailed data and security guidelines and standards are set out in the guideline PCI-DSS compliance is the standard for data protection – The data and security standards may affect development and use of wallet and payment apps in Canada, as the guideline allows information about transactions, loyalty programs and consumers to be used only in certain ways - 83 - Canadian Mobile Payments Guidelines (cont.) • Government reaction – The voluntary Code of Conduct for the Credit and Debit Card Industry in Canada (the Code) must be revised for the quickly evolving mobile payment ecosystem – Code amendments would need to anticipate all forms of emerging mobile payment technology – Out-of-scope of the guidelines are remote mobile payments, storing of payment credentials on micro SD memory cards and NFC cases, the use of cloud-based mobile payments (where credentials are stored on a server and accessed by Internet), barcode, bluetooth, passive NFC and RFID and p2p based payments - 84 - Recent amendments to Canadian Payments Association (CPA) rules and standards • • • CPA operates pursuant to a legal framework set out in the federal Canadian Payments Act CPA’s mandate to establish and operate national systems for the clearing and settlement of payments within Canada, principally the Automated Clearing Settlement System (ACSS) and the Large Value Transfer System (LVTS), as well as the US Bulk Exchange (USBE). Pursuant to the Act, the CPA develops and implements rules, standards, and procedures that apply to payments exchanged by CPA members who use these systems for clearing and settlement. - 85 - Recent amendments to CPA rules and standards • Amendments to Automated Clearing and Settlement System (ACSS) Rules and Standards came into effect on April 22, 2013 • The rules that were amended include RULE E3, which governs the Exchange of credit-driven Canadian dollar electronic data interchange (EDI) Payment Items amongst Canadian financial institutions, for the purpose of Clearing and Settlement – Part I sets out the general rules relating to the Exchange of such Items for the purpose of Clearing and Settlement (including systems, software maintenance and disaster recovery) – Part II sets out the technical specifications applicable to the Exchanges. - 86 - Recent amendments to CPA rules and standards • • The amendments deal with the Direct Participant’s reporting obligations to the CPA in the event of encountering a Severity 1 Contingency Situation. A “Severity 1 Contingency Situation” occurs when the Direct Participant cannot receive or process EDI Transmissions. - 87 - Recent amendments to CPA rules and standards • Amendments were also made to Standard 014, the Clearing Replacement Document Design Standard, which sets out the minimum mandatory requirements for the creation and use of Clearing Replacement Documents (CRDs). – “Clearing Replacement Document” or “CRD” means a form of Image Printout that meets the specifications in Standard 014, and which may be used for presentment and return purposes in place of an original paper Payment Item in accordance with Rule A10. – This standard will ensure that all CRDs that are generated for the purpose of replacing an original paper payment item (e.g. a cheque) for presentment to a Drawee may be processed accurately and efficiently by the Drawee. – Compliance with this standard is important for remote deposit of cheques. - 88 - Recent amendments to CPA rules and standards • In addition to financial institutions, Mobile payments processors and software developers need to ensure the images of payment items created by mobile devices will meet the technical requirements of Standard 014. - 89 - Consumer Protection Issues • Consumers with credit cards from banks are protected by Bank Act regulations that require: – Disclosure of the interest rate at the time of solicitation or application, and on every one of your monthly statements – Statements to include itemized transactions, the amount you must pay on or before the due date in order to have the benefit of a grace period – Disclosure of the previous month’s payments and the current month’s purchases, credit advances, as well as interest and non-interest charges – Plain language information for customers – Rules on advertising – Limits on consumer liability in the event of fraud - 90 - Consumer Protection Issues • • Canadian Code of Practice for Consumer Debit Card Services Principles of Consumer Protection for Electronic Commerce – Voluntary code for Canadian Bankers Association members – Provides a framework for commerce over open networks, including the internet • Equivalent protection – “Consumers” should not be afforded any less protection in “electronic commerce” than in other forms of commerce. Consumer protection provisions should be designed to achieve the same results whatever the medium of commerce. • Harmonization – Canadian governments should adapt existing consumer protection laws to apply to electronic commerce, and should strive to harmonize provisions across jurisdictions without requiring any jurisdiction to lower its standards. - 91 - Consumer Protection Issues • • Principles of Consumer Protection for Electronic Commerce (cont.) • International consistency – Without compromising the level of protection provided to consumers under the principles in this document or under existing laws, the Canadian consumer protection framework should be consistent with directions in consumer protection established by international bodies such as the Organisation for Economic Co-operation and Development. Principles in Summary: 1. Consumers should be provided with clear and sufficient information to make an informed choice about whether and how to make a purchase. 2. “Vendors” should take reasonable steps to ensure that the consumer’s agreement to contract is fully informed and intentional. 3. Vendors and “intermediaries” should respect the privacy principles set out in the CSA International’s Model Code for the Protection of Personal Information. - 92 - Consumer Protection Issues • Principles of Consumer Protection for Electronic Commerce (cont.) 4. Vendors and intermediaries should take reasonable steps to ensure that “transactions” in which they are involved are secure. Consumers should act prudently when undertaking transactions. 5. Consumers should have access to fair, timely, effective and affordable means for resolving problems with any transaction. 6. Consumers should be protected from unreasonable liability for payments in transactions. 7. Vendors should not transmit commercial E-mail without the consent of consumers, or unless a vendor has an existing relationship with a consumer. 8. Government, business and consumer groups should promote consumer awareness about the safe use of electronic commerce. - 93 - Consumer Protection Issues • Provincial consumer protection statutes and regulations – Consumer agreements have specific requirements, e.g. minimum payment obligations, disclosure, signature, writing, delivery, content/terms, express opportunity to accept or decline, cooling off periods, cancellation rights, amendment – Internet Agreements are formed by text-based Internet communications have their own unique requirements – Ont. CPA - "Internet" means a decentralized global network connecting networks of computers and similar services to each other for the electronic exchange of information using standardized communication protocols – Not clear how this will apply to mobile computing - 94 - Consumer Protection Issues • Provincial consumer protection statutes and regulations – Also separate requirements for: • Remote Agreements – when the consumer and supplier are not present together • Direct Agreements – when the consumer agreement is negotiated or concluded at a place other than the supplier's place of business or marketplace • Credit, credit card and payday agreements with consumers – E.g. liability for unauthorized credit card charges capped at $50 (CPA, s. 69 and CPAR, s. 58) • Ont. Reg. 17/05 under CPA - Gift card agreements - 95 - Code of Conduct for the Debit and Credit Industry In Canada • • Code came into effect in August 2010 to help merchants and consumers clearly understand the costs and benefits of credit and debit cards When initially developed, the Code underwent extensive consultations with merchant and consumer associations, debit and credit card networks, payment processors, and credit card issuers across Canada - 96 - Code of Conduct for the Debit and Credit Industry In Canada • • • Purpose – to demonstrate the industry's commitment to: – Ensuring that merchants are fully aware of the costs associated with accepting credit and debit card payments thereby allowing merchants to reasonably forecast their monthly costs related to accepting such payments – Providing merchants with increased pricing flexibility to encourage consumers to choose the lowest-cost payment option – Allowing merchants to freely choose which payment options they will accept Code applies to credit and debit card networks and their participants (i.e. card issuers and acquirers) Code incorporated into payment card networks' contracts, governing rules and regulations - 97 - Code of Conduct for the Debit and Credit Industry In Canada • • • • • Task Force for the Payments System Review and the Canadian Guidelines for Mobile Payments called for review of the Code On Sept 18 2012, Harper Government announced Code of Conduct expansion to mobile payments, and released a proposed Addendum to the Code for public consultation, circulated for 60 days comment. Comments were invited on whether the Addendum should apply to other entities enabling mobile payments Elements 1, 2, 3, 5, and 9, will continue to apply to mobile payments as written Clarifications are proposed to Elements 4, 6, 7, 8 and 10 to guide their application to mobile payments. - 98 - Code of Conduct for the Debit and Credit Industry In Canada • • The Code covers several methods of making payments, including point-of-sale, Internet and telephone. The proposed Addendum extends the application of the Code to credit and debit card networks and their participants that offer mobile payments at the point of sale For the purposes of the Addendum, references to “payment card” networks and “payment card” network rules shall be interpreted to include credit and debit payment applications (referred to as “payment apps”) offered by payment card networks which can be accessed by consumers using a mobile device. Payment apps may be stored separately or centrally (i.e., in a digital/mobile wallet) on a mobile device - 99 - Code of Conduct for the Debit and Credit Industry In Canada • • Financial Consumer Agency of Canada (FCAC) monitors and enforces compliance with the code 10 Elements 1. Transparency and disclosure of information to Merchants • Rates and fees, e.g. interchange, discounts • Transaction details, e.g. number, volume, type 2. 90 days notice for rate/fee changes (unless pre-determined schedule in merchant contract), 180 days for structural changes 3. Cancellation of contract by merchant without penalty within 90 day period - 100 - Code of Conduct for the Debit and Credit Industry In Canada 4. Merchant can choose to accept only credit or debit payments from a network, without having to accept both Payment card network rules will ensure that merchants who accept credit or debit card payments from a particular network through a mobile device will not be obligated to accept all products available in that payment network’s mobile wallet. 5. Merchants allowed to provide different discounts for different methods of payment among different networks (e.g. cash, debit card, credit card) - 101 - Code of Conduct for the Debit and Credit Industry In Canada 6. Competing domestic applications from different networks shall not be offered on the same debit card. However, non-competing complementary domestic applications from different networks may exist on the same debit card. • A debit card may contain multiple applications, such as PIN-based and contactless. A card may not have applications from more than one network to process each type of domestic transaction, such as POS, Internet, telephone, etc. This limitation does not apply to ABM or international transactions Competing domestic debit apps can be stored on, or accessed by the same mobile device, provided that they are represented as a separate payment app and consumers can select which payment app shall be used for a transaction. - 102 - Code of Conduct for the Debit and Credit Industry In Canada • 10 Principles (cont.) 7. Co-badged debit cards must be equally branded • Available payment networks on payment cards must be clearly indicated • No preferential branding. Logos must be same size, side and either colour, black or white. The principle of equal branding applies to all representations of payment apps (i.e. credit and debit) available on, or through, a mobile device. Payment card network rules shall ensure that consumers have full discretion to establish any default preference(s) for payment options. Establishing default preferences should be done by users based on a clear and transparent process and users should be able to easily change default settings. - 103 - Code of Conduct for the Debit and Credit Industry In Canada • 10 Principles (cont.) 8. Debit and credit card functions shall not co-reside on the same payment card • Problems with access to different accounts, with different terms, fees and features – consumer confusion Credit and debit card functions shall not co-reside on the same payment app. Credit and debit payment apps can be stored on, or accessed by the same mobile device, provided that they are clearly separate payment apps. 9. Premium cards (which have higher than average interchange rates) may only be given to consumers who apply or consent, and who have certain spending and/or income thresholds - 104 - Code of Conduct for the Debit and Credit Industry In Canada • 10 Principles (cont.) 10. Negative option acceptance is not allowed • If payment card networks introduce new products or services, merchants shall not be obligated to accept those new products or services. Merchants must provide their express consent to accept the new products or services. Stakeholders are invited to provide comments on whether express consent should be required from merchants to accept debit or credit payment applications through a mobile device, where fees to merchants remain unchanged and no new infrastructure purchases are required. - 105 - Code of Conduct for the Debit and Credit Industry In Canada • • • February 13, 2013, the FCAC issued Commissioner's Guidance CG-10 in respect of the Code, to address the lack of transparency in respect of some sales and business practices; a lack of clarity of disclosures where multiple merchant service agreements are required; and multiple contract cancellation fees The Guidance clarifies certain requirements of the Code in respect of payment card networks that operate in Canada and their participants, including, for the first time, independent sales organizations (ISOs) and other service providers (e.g., processors, terminal lessors) Payment card network operators (PCNO) were to incorporate the amendments into their operating rules by May 14, 2013, with all industry participants expected to comply within 180 days of the date that PCNO operating rules were amended - 106 - Regulations on prepaid cards • • • October 24, 2012 - The Minister of Finance and Deputy Commissioner of the Financial Consumer Agency of Canada (FCAC), announced new regulations to protect consumers when using prepaid credit cards The proposed Federal regulation will eliminate expiry dates on non-promotional prepaid credit products (while allowing for alternative funds access mechanisms for phased out products), and prevent the levy of certain fees without express consent of the user Initial fees on the product are allowed, but subject to strict disclosure requirements - 107 - Regulations on prepaid cards • To support informed financial decision making, the proposed Regulations would require disclosure of fees in an information box to appear prominently on the exterior packaging and other documentation prior to issuance. The proposed Regulations would also require that information pertinent to continued usage be available on the product, including where to access the full terms and conditions of usage and a tollfree number to access the remaining balance - 108 - Regulations on prepaid cards • Apply to prepaid payment products that are issued in Canada by an "institution", meaning: (a) a bank, as defined in section 2 of the Bank Act; (b) an authorized foreign bank, as defined in section 2 of the Bank Act; (c) a retail association, as defined in section 2 of the Cooperative Credit Associations Act; (d) a company, as defined in subsection 2(1) of the Insurance Companies Act; (e) a foreign company, as defined in subsection 2(1) of the Insurance Companies Act; or (f) a company, as defined in section 2 of the Trust and Loan Companies Act. - 109 - Payment Card Industry (PCI) Data Security Standard (DSS) • • • • • The PCI Security Standards Council developed standards and supporting materials to enhance payment card data security A framework of specifications, tools, measurements and support resources to help organizations ensure the safe handling of cardholder information at every step including prevention, detection and appropriate reaction to security incidents. Need broad adoption of consistent global data security measures Baseline of technical and operational requirements designed PCIDSS can be licensed from the PCI Security Standards Council, LLC, Wakefield, MA , which owns the copyright in the specifications and materials, under Delaware law - 110 - Payment Card Industry (PCI) Data Security Standard (DSS) • • To help software vendors and others develop secure payment applications, the Council maintains the Payment Application Data Security Standard (PA-DSS) and a list of Validated Payment Applications. The Council also provides training to professional firms and individuals so that they can assist organizations with their compliance efforts. The Council maintains public resources such as lists of Qualified Security Assessors (QSAs), Payment Application Qualified Security Assessors (PA-QSAs), and Approved Scanning Vendors (ASVs). Large firms seeking to educate their employees can take advantage of the Internal Security Assessor (ISA) education program. - 111 - Payment Card Industry (PCI) Data Security Standard (DSS) • Canadian FI's have adopted PCI DSS • PCI DSS requires organizations that collect, process, transmit or store cardholder data to uphold and maintain the data security standards set by the payment industry worldwide and managed by the PCI Security Standards Council (PCI SSC) • FI's typically require all merchants who collect, process, transmit or store cardholder data to comply with PCI DSS. – pursuant to their processing services agreement • Failure to comply with PCI DSS and the Payment Card Networks’ Compliance Programs may result in a Merchant being subject to fines, fees or assessments and/or termination of processing services - 112 - Payment Card Industry (PCI) Data Security Standard (DSS) • • • PCI DSS is a multifaceted security standard that includes requirements for security management, policies, procedures, network architecture, software design and other critical protective measures The result is a comprehensive standard intended to help organizations protect consumer cardholder data Key requirements of PCI DSS: – Build and Maintain a Secure Network • Install and maintain a firewall configuration to protect cardholder data • Do not use vendor-supplied defaults for system passwords and other security parameters - 113 - Payment Card Industry (PCI) Data Security Standard (DSS) – Protect Cardholder Data • Protect stored cardholder data • Encrypt transmission of cardholder data across open, public networks – Maintain a Vulnerability Management Program • Use and regularly update anti-virus software • Develop and maintain secure systems and applications – Implement Strong Access Control Measures • Restrict access to cardholder data by business need-to-know • Assign a unique ID to each person with computer access • Restrict physical access to cardholder data – Regularly Monitor and Test Networks • Track and monitor all access to network resources and cardholder data • Regularly test security systems and processes – Maintain an Information Security Policy - 114 - Payment Card Industry (PCI) Data Security Standard (DSS) • • • • • PCIDSS requirements need to be considered in all contracts with participants in mobile payments Trickle-down effect from merchant obligations - service providers that store, process, or transmit cardholder data on behalf of a merchant or other service providers must comply with PCI DSS and validate their compliance using the appropriate method Merchant levels and the validation requirements for each level, as determined by Visa Canada and MasterCard Data security firms (qualified security assessors) such as Trustwave provide information security and PCI compliance services The PCI DSS and supporting documentation can be found at https://www.pcisecuritystandards.org - 115 - PIN Security Requirements • • For device vendors and manufacturers, the PCI Security Standards Council provides the PIN Transaction Security (PTS) requirements, which contains a single set of requirements for all personal identification number (PIN) terminals, including POS devices, encrypting PIN pads and unattended payment terminals. The Council also provides a list of approved PIN transaction devices - 116 - Payment Application Data Security Standard (PA-DSS) • • Also managed by the PCI SSC. This standard is based on Visa’s Payment Application Best Practices (PABP). Many merchants deploy third party payment applications that are tailored to their business needs to assist them in accepting credit card payments. The goal of PADSS is to assist software vendors in developing secure payment applications that do not store prohibited data, such as full magnetic stripe data, card verification values, or PIN data, and ensure their payment applications support compliance with the PCI DSS standard. Vulnerable payment applications that store prohibited data are the leading cause of account data compromises among small merchants. - 117 - Payment Application Data Security Standard (PA-DSS) • • Payment applications that are sold, distributed or licensed to third parties are subject to the PA-DSS requirements. In-house payment applications developed by merchants or service providers that are not sold to third parties are not subject to the PA-DSS requirements, but must still be secured in accordance with the PCI DSS. PA-DSS is not applicable to standalone point-of-sale terminals, database software or web server software. Further information on PA-DSS including a list of payment applications that have validated their compliance to PA-DSS can be found at: www.pcisecuritystandards.org - 118 - Mobile Payments Regulation Milos Barutciski - 119 - Anti-Money Laundering Regulation • Background to AML regulation – Financial Action Task Force (FATF) – FATF Recommendations – Proceeds of Crime (Money Laundering) and Terrorist Financing Act (PCTFA) – Financial Transactions and Reports Analysis Centre of Canada (FINTRAC) - 120 - Overview of Money-Laundering • Essential elements of money-laundering – Placement – Layering – Integration • Typologies – FINTRAC Typologies Reports - 121 - Overview of AML Regulation (1) • Scope of application • Reporting entities – Financial entities – Life insurance – Money services businesses – Securities dealers – Real estate brokers – Casinos – Accountants – Other - 122 - Overview of AML Regulation (2) • • • • • Know-your-client (KYC) obligations Verification/Authentification Record-keeping Politically Exposed Foreign Persons Reporting – Large cash transactions – Electronic funds transfers – Cross-border transfers – Suspicious transactions - 123 - Overview of AML Regulation (3) • Mandatory compliance policy • Tipping • Offenses and penalties – Criminal offence – Administrative monetary penalties (AMPs) - 124 - AML and New Payments Methods • Mobile and prepaid payments developments • AML concerns with new payment methods – Identification/Anonymity – Value limits – Funding methods – Geographic scope/cross-border • Gaps in the AML regulatory system • Monitoring and mitigating risk - 125 - AML and New Payment Methods: Policy Responses • 2010 FATF Report on New Payment Methods • 2011 Finance Canada Consultations on Strengthening Canada's Anti-Money Laundering and Anti-Terrorist Financing Regime • 2012 Report of the Senate Standing Committee on Banking, Trade & Commerce - 126 - Commercialization of Payment Solutions Duncan Card - 127 - Commercialization of Payment Solutions A CHALLENGING ENVIRONMENT FOR COMMERCIALIZATION 1. New solutions…continuously: • • • • digital currency, e.g. bitcoin (BTC) cryptocurrencies electronic barter systems merchant currency (often tied to affinity programs, but tradable) technology innovations (hardware, devices, equipment, chips, software, processes) 2. New participants…constantly: • • • • • • • • • value-add intermediaries telco engagement ISP/web engagement tech product/equipment software vendors – payment "apps" network managers consumer devices off-shore services payment integration management - 128 - 3. Context of Security – fast moving target: • privacy legislation, regulatory oversight, and enforcement • enterprise crime – going after information that others have about individuals and companies • "hackers" – both attacking commercial and personal targets • organized crime - 4. physical and online theft of personal and financial information money laundering (e.g. overpayment of merchant accounts, then direction to pay) identity theft • information cyber security – Mandiant Report, State Sponsored unauthorized access to IP and confidential information • Cyber Warfare – mostly third parties (organized crime, "ethical" associations, non-state agents, such as terrorists, state sponsored agents, and governments), attack critical infrastructure, including financial systems of all types = payment system risk Rapid Proliferation of Value-Add Participants • from simply handing over money to a merchant, to a series of credit/debit obligations transacted through a myriad of diverse technologies and global contributors who are both visible and invisible to the consumer • everyone wants a piece of the money trail – as they say, "follow the money" • everyone wants to take a piece of that money trail along the way, one way or another, giving rise to new economies – micro payments are like very small royalties paid over a vast number of transactions - 129 - COMMERCIAL IMPLICATIONS 1. Since micro-royalty structures for intermediaries will be shared over vast numbers of transactions, having a significant market share in your contribution is important. 2. Significant market share means having "the killer app", or owning a particular space in the entire process, or adding up your roles/contributions (e.g. wireless device + the app chip + security and authentification + telco services + billing services + being the consumer's bank in the process) 3. The more intermediaries who come to the party, the harder the "end-to-end solution" is to operate, keep secure and manage – so payment solution governance and management systems are increasing in importance. 4. What are all of the contractual relationships, and which contributors do not have contractual priority with other contributors to the solution? 5. Who will, from a brand management perspective, own the merchant and/or the consumer? Who will be the brand key point of contact? 6. Will the convergence of so many participants be balanced, stable, seamless, wellmanaged (risk and otherwise) or, will it create more "cracks" through which the metaphorical penny might drop? 7. How do regulators (and regulations) keep up to date, hence the risk of ad hoc or de facto legal or regulatory disapproval over an otherwise excellent payment solution (or key parts of it)? - 130 - PAYMENT SOLUTION COMMERCIALIZATION – STRUCTURAL LEGAL ISSUES 1. Sorting Out Who Contributes What, and on what basis. • draw diagrams of both the end-to-end payment solution, and include all of the contributors and the operational (functional) overview of what each contributor brings to the solution • assess which contributor is providing what good/service to which other contributor on a commercial basis – is there privity of contract • which contributors do other contributors depend upon for the delivery of goods/services into the payment solution without any commercial or contractual obligations between them • Real Danger of technology, process, brand alliance and trade-mark flooding and confusion as the market becomes overcrowded with a proliferation of vastly different payment methods – at one point, many predict the payment market will "simplify or narrow down" leaving many excellent consortia by the side of the road - 131 - PAYMENT SOLUTION COMMERCIALIZATION – STRUCTURAL & LEGAL ISSUES 2. Commercial Structure & Risk Management • which participant "owns" the payment solution? Brand or Reputation? • is there a "prime contractor" sponsor? • are there numerous "side deals" coming together in the consortium? • where are the risks and liabilities along the payment chain, and which participants hold which particular risks? • what are the co-opetition risks? Is the telco in the consortium also a competing bank? Will other participants disintermediate banks, e.g. Google $ • what fees will be deducted from the consumer transaction, and of those fees…how much will be paid to "process partners" $100 transaction → reasonable estimate that $3.00 will be deducted along the money trail (credit card interchange, issuing bank, processor, merchant account → of that $3.00, what will be paid for related intermediary services (authentification, technology licensors, device owners, third party processors)? - 132 - PAYMENT SOLUTION COMMERCIALIZATION – STRUCTURAL & LEGAL ISSUES 3. Contract Terms • • • • define the good/service contribution/obligations warrant operational/functional performance warrant compatibility of each good/service with all of consortia "pieces" (fit) stipulate what all of the other pieces are that are required (as a condition precedent) for your piece to fit: • • • • • • • • chip (ID) wireless device security payment apps • • • • network provider payment processor authentification e-commerce app and POS tech • • • • bank/issuer credit card payment app gateway financial compensation personal information: protect; confidential; compliance with laws customer ownership + who keeps what transaction information? brand identification – who will the solution be branded by: the bank; the telco; the credit card • Bell Mobile Wallet • Google Wallet • Vision Mobile Platform • CIBC Mobile Payment App • Rogers Suretap™ ("turns your wireless smart phone into a mobile wallet") - 133 - PAYMENT SOLUTION COMMERCIALIZATION – STRUCTURAL & LEGAL ISSUES 3. Contract Terms (con't) • • • • • • to what extent should contributors/participants be liable for the conduct of their side-deal contractors (to what extent are those products/services included?)) audit rights – performance verification and "problem diagnostics" – how do contract parties get access to non-contract participant information? payment solution problem: identification, assessment, diagnostics, fixes, process revisions, improvements individually and collectively (cooperation) both as between the parties and extending to non-contract contributors (e.g. various solution apps) third party liability and "class damages" – merchants and consumers and both as between the parties how does the "brand prime" contractually limit and exclude liability with merchants/consumers to protect entire consortium? LOL Clauses: what is the aggregate transaction value; how does that value relate to the possible harm that could be caused (depending upon the particular contribution); what is reasonable? - 134 - PAYMENT SOLUTION COMMERCIALIZATION – STRUCTURAL LEGAL ISSUES 3. Contract Terms (con't) • • • • • solution-wide audit participation – regulatory, consumer protection, criminal investigations, privacy investigations, participant investigations (e.g. Visa or Master Card) require each of the consortium participants to report any breach of their agreements by them (in writing, promptly, reasonable information, rootcause analysis, what the impact is, and both remediation and avoidance) payment solution multi-party management – regular and organized full consortium meetings; steering committee; minutes (subject to attending legal counsel re: off record information); dispute resolution; change management; providing collective oversight and governance (without any authority to amend the associated contracts!) dispute resolution: ADR = confidential/expert/fast dovetail all of the consortium contracts on key solution issues: e.g., audit, reporting, change management, ADR and other terms where all participants will have to move in the same direction - 135 - In-House Counsel Primer: Oversight, Compliance & Implementation Duncan Card - 136 - In-House Counsel Primer: Oversight, Compliance & Implementation ……taking a very broach approach…… 1. Commercial Context 1.1 Who are all of the participants or parties? 1.2 What goods/services are being provided by whom to whom? 1.3 What are the contractual vs. non-contractual relationships? 1.4 What are the "contribution" pre-conditions – which party must provide what goods/services for client to perform? 1.5 Do the parties have the right/authorization to provide their respective contributions: IP, contractual, regulatory? 1.6 What is your client's business objective? Desired outcome? Business case? Transaction ROI? 1.7 How to fully protect client interests to promote and facilitate that outcome/objective: brand positioning; own the customer; IP ownership; prevent unfair competition by others; exclusivity…etc.? 1.8 Map out any consortium transactions in a diagram to understand all commercial relationships. - 137 - In-House Counsel Primer: Oversight, Compliance & Implementation 2. Legal & Regulatory Assessment 2.1 Trade Association Agreement: standards; affiliation contracts; existing commercial obligations to third parties; trade association guidelines (e.g. CBA Guidelines For Mobile Payments); Federal Government – Code of Conduct for Credit & Debit Cards, Canadian Payments Association rules; codes of conduct; consider applicability of domestic and foreign trade rules; requirements and restrictions. 2.2 Privacy: Domestic federal and provincial; applicability of foreign laws and regulations (e.g. cross-border payment networks); related security measure requirements; "cloud" risks. 2.3 Payment Card Networks Act. 2.4 Anti Money Laundering. 2.5 Records & Data Management Laws/Regulations: on a sector-by-sector basis, depending upon how regulated the industry is; tax records requirements; customs records requirements; GAAP requirements for creation and maintenance of electronic records; vulnerability of data to third party access/interception (e.g. U.S. Patriot Act); "cloud" risks. - 138 - In-House Counsel Primer: Oversight, Compliance & Implementation 2. Legal & Regulatory Assessment (con't.) 2.6 Competition Law: identify the legal concerns (especially for coopetition transactions) and develop a management strategy (if possible). 2.7 International Settlements (Immunity) Act. 2.8 Consumer Protection Laws. 2.9 Federal Payments Act – and any corresponding U.S./foreign laws (e.g. U.S. Electronic Funds Transfer Act, first enacted in 1978). 2.10 Payment Clearing & Settlement Act. 2.11 Currency Act, e.g. section 8 identifies legal tender for payment as coins or banknotes. 2.12 Many emerging provincial laws, e.g. gift cards, pre-pad cards, and "moneyservices" laws. - 139 - In-House Counsel Primer: Oversight, Compliance & Implementation 3. General Contractual Issues 3.1 Define the contribution, goods or services: detailed operational, functional and technical specifications. 3.2 Pre-Conditions: third party product compatibility, inter-operability and connectivity; what other contributions your contributor will require, prefer or request; beta-testing terms/trial; third party contractual rights/participation being secured; regulatory approvals; use/opinions, including guideline/rule/code compliance. 3.3 Term, Right of Extrication, Wind-down transition. 3.4 Financial Issues: compensation; shared cost; audits? 3.5 Brand Control: ownership; recognition or invisible? 3.6 Ownership: results of test; operational data rights (license; customer identity; customer (payment solution) behaviour; each participant's experience as related to your contribution. - 140 - In-House Counsel Primer: Oversight, Compliance & Implementation 3. General Contractual Issues (con't.) 3.7 Risk Management: notice of breach; notice of claims; ADR; cooperate if ADR/litigation with third parties; JMC governance; LOL; indemnities; insurance coverage; inspections/audit for compliance with contract (direct or third party); quality assurance program; compliance with laws, regulation and all applicable codes, guidelines, rules and charters that are included in "Law" definition. 3.8 Security obligations, independent assessment and testing; change management; incident reporting; reputation management plan/policy; critical/crisis response/fix policy; contractual (downstream) liability control (from LOL to class actions). 3.9 Key Person/Management Requirements. 3.10 Non-Competition Provisions: dance partner fidelity. - 141 - Thank you! Question & Answer Lisa Abe-Oldenburg, Partner, Milos Barutciski, Partner, Stephen Burns, Partner Duncan Card, Partner