Dynamic Access Control and IRM in Windows 2012
advertisement

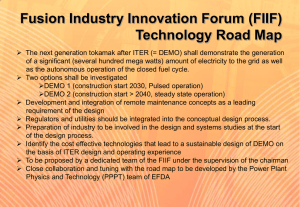
• • • • • • Breach Growth of users and data ? Distributed computing Regulatory and Business Compliance ? Budget Constraints 63K confirmed security incidents for 2013 w/ 1,367 confirmed data breaches. Over 40% targeted at server assets. 2014 Verizon Data Breach Investigations Report ForrSights Hardware Survey, Q3 2012 Forrester Research, Inc 2013: Advanced Malware Detection and Protection Trends, ESG Research 73% of enterprise IT hardware decision makers are concerned about security/privacy issues in virtualized and cloud environments. 92% of enterprises see security capabilities of public service providers a top influence in their purchasing decision.` CSO/CIO department “I need to have the right controls to keep my job” Infrastructure Support “I don’t know what data is in my repositories and how to control it” Content Owner “Is my important data appropriately protected and compliant with regulations” Information Worker “I don’t know if I am complying with my organization’s polices” Demo Data classification Demo Automatic RMS protection Area Properties Information Privacy Information Security Legal Personally Identifiable Information High; Moderate; Low; Public; Not PII Protected Health Information Confidentiality Required Clearance High; Moderate; Low High; Moderate; Low Restricted; Internal Use; Public Compliancy SOX; PCI; HIPAA/HITECH; NIST SP 800-53; NIST SP 800-122; U.S.-EU Safe Harbor Framework; GLBA; ITAR; PIPEDA; EU Data Protection Directive; Japanese Personal Information Privacy Act Discoverability Immutable Intellectual Property Privileged; Hold Yes/No Records Management Retention Retention Start Date Organizational Values Copyright; Trade Secret; Parent Application Document; Patent Supporting Document Long-term; Mid-term; Short-term; Indefinite <Date Value> Impact High; Moderate; Low Department Engineering ;Legal; Human Resources … Project Personal Use <Project> Yes/No Country x 50 Branch x 20 Customers x 100 File Server AD DS User claims User.Department = Finance User.Clearance = High Device claims Device.Department = Finance Device.Managed = True Resource properties Resource.Department = Finance Resource.Impact = High ACCESS POLICY Applies to: @File.Impact = High Allow | Read, Write | if (@User.Department == @File.Department) AND (@Device.Managed == True) 15 Demo Central access policies Files Rule 1 Files Rule 2 Files Rule 3 Customer Defined Access Policy For access to COI information, a user must be a member of the COI for which the data is classified. If data is not classified, only the Owner, Administrators, and SYSTEM have Full Control. Director of compensation, GM Marketing Communications, US Payroll Director, Headcount Data Management, Director of MSA Strategy