Intel® AMT Keyboard, Video, Mouse Redirection - CM
advertisement

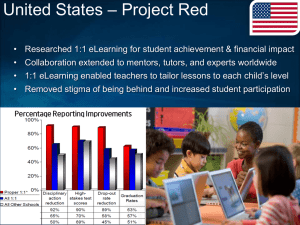
Intel® vPro™ Processor Technology Intel® AMT Keyboard, Video & Mouse Remote Control <Presenter’s Name> Application Engineer Software and Services Group <month>, 2009 Legal Disclaimer Information in this document is provided in connection with Intel products. No license, express or implied, by personnel or otherwise, to any intellectual property rights is granted by this document. Except as provided in Intel's Terms and Conditions of Sale for such products, Intel assumes no liability whatsoever, and Intel disclaims any express or implied warranty, relating to sale and/or use of Intel products including liability or warranties relating to fitness for a particular purpose, merchantability, or infringement of any patent, copyright or other intellectual property right. Intel products are not intended for use in medical, life saving, or life sustaining applications. Intel may make changes to specifications and product descriptions at any time, without notice. Designers must not rely on the absence or characteristics of any features or instructions marked "reserved" or "undefined." Intel reserves these for future definition and shall have no responsibility whatsoever for conflicts or incompatibilities arising from future changes to them. Products referenced herein may be incomplete or contain errors known as errata which may cause the products to deviate from published specifications. Current characterized errata are available upon request. Intel® Active Management Technology requires the computer have an Intel® AMT-enabled Intel chipset, network hardware and software, connection with a power source, and a network connection. Intel® Virtualization Technology requires a computer system with an enabled Intel® processor, BIOS, virtual machine monitor (VMM) and for some uses, certain platform software enabled for it. Functionality, performance or other benefits will vary depending on hardware and software configurations. Intel Virtualization Technology-enabled BIOS and VMM applications are currently in development. Copyright (c) Intel Corporation 2007-2009 * Other names and brands may be claimed as the property of others. Intel Confidential ‹#› Expanding Redirection Capabilities Current Support (Intel® AMT Release 5.x and earlier) • IDE Redirection • Serial Redirection Intel® AMT Release 6 • IDE & Serial Redirection • Keyboard, Video & Mouse (KVM) Remote Control Intel Confidential ‹#› Example Use-Cases Console Computer State Comp A Comp B Comp C Comp D Unhealthy OS unresponsive Rebooting OS Healthy _ OS Blue-screen X Comp A Screen OS Unresponsive Dsfsd.sys failed at mem location 0x1234hfhs Memory dump: 3409afed 3409afed 3409afed 3409afed 3409afed 3409afed Select a machine to manage Boot Process Console Corrupt Network Driver Intel Confidential ‹#› Advantages of KVM Remote Control Works in many situations • • • • • • • OS malfunctions (hung, degraded response) BIOS level OS boot OS installation OS repair (safe mode, system restore) Virtual environments Corrupt network driver or Filtered network traffic Robust, hardware based solution Reduced hardware cost (compared to 3rd party hardware solutions) Intel Confidential ‹#› Terminology Term Definition KVM Server The KVM service running on the managed client. A KVM Server runs in the Intel® vPro™ management engine. KVM Client The ISV console connecting to the KVM Server. sprite A graphic overlay that is drawn directly to the monitor by the integrated hardware. Similar to volume / channel indication on television. Sprite Graphic KVM Session Request Passcode: 123456 KVM Server KVM Client Intel® vPro™ System Remote Console Intel Confidential ‹#› Example Deployment Flow Prior to KVM Remote Control use, several steps with some notable options are required. This occurs in conjunction with Intel® vPro™ Setup & Configuration. System Received & Installed Optional MEBx Settings (manual) •Physically deployed •Intel® vPro™ Drivers / Services Installed •KVM Disable •User Consent Disable (enable remote switch) Configuration (remote) •Set RFB Password •Enable / disable user consent (requires MEBx setting) •Enable / disable port 5900 •Enable redirection listener Intel® vPro™ Setup Optional User Settings •Consent Opt-Out (MEBx) •Session Notifications (IMSS) Intel Confidential ‹#› Example KVM Remote Control Session Console Initiates Session Intel® AMT Authentication •Optional TLS Session Established Session User Notification •IMSS Icon •Sprite Session Established Passcode OR VNC* Authentication User Consent Code Validation Session Terminated Passcode Connect KVM Session Terminated •Console terminates or… •User terminates (IMSS or Physical Disconnect) Intel® vPro™ System Remote Console * Other names and brands may be claimed as the property of others. Intel Confidential ‹#› Example User Consent Flow By default, the user must consent to each KVM Remote Control session. This may be disabled by: •OEM •During USB initiated setup •User opts out through MEBx •Optionally enabled / disabled remotely if allowed in MEBx User calls helpdesk Help-desk connects to Intel® AMT Consent code displayed locally in sprite ME Generates consent code User reads consent code to help-desk Help-desk enters consent code KVM Remote Control session begins Intel Confidential ‹#› Host Wireless Driver Managing All Traffic Intel® AMT Session Established ME Transitions to “Operational” State: Controls Wireless Connection KVM Remote Control Session Begins ME Maintains Control of Wireless Connection During KVM Remote Control Session and Power Control KVM Remote Control Session Ends Wireless Connectivity Management traffic passes through the host wireless driver when operational. (“Pipe” mode) The management engine (ME) manages wireless connectivity when the host driver is absent. (“Operational” mode) Intel® AMT implements “link sensitive” behavior during some use-cases to avoid connectivity interruptions. Starting with Intel® AMT 6.0, you can control the link preference to fit your usecase through AMT_EthernetPortSettings.SetLinkPreference ME Transitions to “Pipe” State: Host Manages Wireless Connection (if available) Intel Confidential ‹#› Simple Connection Option Console GUI RFB • Standard VNC or… • ISV Console Intel® vPro™ Platform • RFB port 5900 Intel Confidential ‹#› Enhanced Intel® AMT Connection Console GUI •ISV Console or… •Integrated VNC* Viewer C API Viewer Library RFB •RFB API SDK Proxy Library •Digest Authentication or… •Kerberos •TLS RFB TLS Intel® vPro™ Platform •Intel® AMT ports 16994/16995 * Other names and brands may be claimed as the property of others. Intel Confidential ‹#› Protocols RealVNC* Remote Frame Buffer (RFB) Protocol • • • • http://www.realvnc.com/docs/rfbproto.pdf (RFB 3.8) Supporting versions 3.8 and 4.x Uses port 5900 (default) Adds RFB password for port 5900 (VNC Authentication) KVM Remote Control Protocol • Implemented as proxy • Uses ports 16994/16995 • Listens on port 5900 (default) • Extends RFB capabilities • Digest & Kerberos authentication • TLS Encryption * Other names and brands may be claimed as the property of others. Intel Confidential ‹#› Protocol & Viewer Options Protocol Options Viewer Compatibility KVM Server Remote Frame Buffer 3.8 3rd Party • Open source RealVNC 3.8 • Improved performance • No GPL code • Enhanced error reporting • Licensed separately by RealVNC* Viewer Remote Frame Buffer 4.x † Real VNC* X Intel® vPro™ X RealVNC 4.x (Intel® SDK) † RealVNC 4.x † X X X † † 3rd Party X * Other names and brands may be claimed as the property of others. † Compatibility depends on 3rd party implementation. Intel Confidential ‹#› SDK Components RealVNC* Viewer Library •Customized for use with Intel® vPro™ Technology •Binary only •RFB 4.x •C interface •Integrated viewer •Licensed separately by RealVNC KVM Proxy Library / Sample •Source provided •Listens for viewer •Proxies RFB through Intel® AMT Redirection Protocol •SOCKS proxy Viewer Sample •Demonstrates custom viewer and proxy use Documentation * Other names and brands may be claimed as the property of others. Intel Confidential ‹#› Configuration (partial list) MEBx (local configuration screens) • Disable / enable KVM Remote Control (just like legacy redirection features) • Disable / enable user consent requirements Intel® AMT (network interface) • Disable / enable KVM Remote Control (if enabled in MEBx) • Set RFB password • Enable / disable port 5900 for legacy VNC connections • Ports 16994/16995 available for Intel® AMT redirection connections • Disable / enable user consent (if allowed by MEBx) • User consent timeouts and session timeouts Intel® Management & Security Status • Select sprite language • Notification options • Hot-key disconnect Intel Confidential ‹#› Architecture Considerations Distributed Distributed Console Console Console Console GUI Console GUI Console GUI VNC Library Intel® AMT Redirection Proxy (Example #1) (Example #2) TLS (SDK Sample) VNC Library VNC Library TLS RFB Integrated Intel® AMT Redirection Proxy Intel® AMT Redirection Proxy Central Server Central Server Intel Confidential TLS ‹#› Discrete Graphics Considerations KVM Session Supported KVM Session Closed • Integrated Graphics Enabled / Selected • Switchable Graphics: Boot Process • Switchable Graphics: Integrated Selected by OS • No Integrated Graphics / Discrete Only • Integrated Graphics Disabled • Switchable Graphics: Discrete Selected by OS KVM Requires Active, Integrated Graphics Intel Confidential ‹#› Summary Keyboard, Video & Mouse (KVM) Remote Control Added in AT6 For New Use-Cases Basic Protocol is RealVNC* Remote Frame Buffer (RFB) 3.8 or 4.x Intel® KVM Remote Control Proxy Gives Greater Security * Other names and brands may be claimed as the property of others. Intel Confidential ‹#› Intel Confidential ‹#› BACKUP Intel Confidential ‹#› Remote KVM Protocols APF VNC* Library RFB Intel® Redirection Proxy TLS Intel® Remote Connectivity Gateway Intel® vPro™ Platform * Other names and brands may be claimed as the property of others. Intel Confidential ‹#› Access Monitor – KVM Related Events •KVM session start •KVM session end •KVM enable •KVM disable •RFB password failed X times •KVM user consent options changed •RFB password changed Intel Confidential ‹#› Intel® Management and Security Status (IMSS) Enhancements •Display the enabled/disabled status of the KVM feature •Indicate if there is an active KVM session •Notify the user that a KVM session is starting •Provide an option to stop the KVM session •Select language for sprite messages Intel Confidential ‹#› User Consent Switches • Remote user consent control through API • IPS_KVMRedirectionSettingData -> OptInPolicy • Must be allowed by firmware setting • OEM sets the default • OEM settings may be OEM Setting: Allow Remote User Consent Control Default Settings No Yes MEBx Setting: Allow Remote User Consent Control No Yes overridden by MEBx AMT Admin: User Consent Setting Required User Consent Not Required KVM Session Intel Confidential ‹#› KVM BIOS/FW Settings Matrix Recommended OEM Settings KVM Enabled (Y/N) User Consent (On/Off) Remote Config of User Consent (On/Off) Manual Touch for IT (Yes/No) Yes On On No Yes Off On No Yes On Off Yes Yes Off Off Yes No On or Off On or Off Yes Good for IT, no touch Bad for IT, requires touch Intel Confidential ‹#›