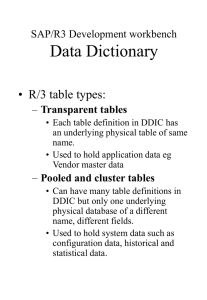
Mobile Enterprise Security
Mark Wright
Senior Systems Consultant, Global Mobility SWAT
Sybase an SAP Company
Thursday, September 29th 2011
Unwired Enterprise Evolution
Global
Client/Server
Internet
Unwired
Enterprise
REACH
Mainframe
Local
Computer Centric
© 2011 SAP AG. All rights reserved.
Human Centric
2
Two Stages of Mobile
Mobile 1.0
Extend the enterprise
© 2011 SAP AG. All rights reserved.
Mobile 2.0
Transform the enterprise
3
Mobility is The New Standard
of all US workers will
be mobile by 2013
% of global workforce that will be
mobile information workers by 2013
Source: “Worldwide Mobile Worker Population 2009–2013 Forecast”,IDC
© 2011 SAP AG. All rights reserved.
4
Consumer Mobility has hit critical mass
There are More Mobile
Phones than Toothbrushes
(5B vs 2.2B)
© 2011 SAP AG. All rights reserved.
5
Mobility Is Not Just About Road Warriors Anymore
Execs
Line of
Business
Managers
Task and Business
Users
Consumers and Ecosystem
Mobile E-Commerce
© 2011 SAP AG. All rights reserved.
Mobile Marketing
Self-Service
6
Key Trends in 2011 and Beyond
Consumerization of IT with
Employee-owned Devices
Momentum of Managed
Mobility Services
Increasing demand for integrated
solutions versus point products
© 2011 SAP AG. All rights reserved.
Increasing demand for
enterprise applications
Shifts in Development
Paradigm and
Ecosystem
7
Enterprise Mobility Trends and Drivers
Trends
• 10B Apple App Store downloads
• 55M Tablets in 2011, 208M by 20141
• 1B smart phones and 1.2B mobile
workers by 20132
Mobility drivers
• Shift to cloud computing
• Consumerization of IT
• Increasing sophistication of devices,
OSs, applications, and networks
• Business demand
Lessons learned
• Security and device management are
a must have and the first step
• A device-agnostic mobility strategy is
critical
• New business scenarios are coming!
1- Gartner 2 – IDC Forecast
© 2011 SAP AG. All rights reserved.
8
What Does This Mean?
MOBILITY
is the new edge we
will use to connect to
our world
© 2011 SAP AG. All rights reserved.
COMPLEXITY
but
of developing and
managing applications,
data, and clients, has
dramatically increased.
9
Mobility Is Not in the Future, It Is Now
Smart phones and tablets
are the dominant computing devices
Enterprises
are building mobile applications today
Tablets forecast
45%
74%
1800
(millions
of units)
1600
1400 of
Mobilephones
smart
Enterprises
commerce
and
are
is
a building
prominent
mobile
marketplace
tablets
and
applications
competitive
today
edge for
are the
dominant
retailers
computing devices
companies
asinathe
priority
will
of retailers
United
implement
enterprise
apps in
Statesmobile
are planning
for m1200
2011commerce
1000
800
Shopping on the
mobile web will
reach
58%
$119 billion
600
400
200
expect to support up to 4
0 different mobile operating
by 2015
2010 2011 2012 2013
2014
system
platforms
Desktop PC
© 2011 SAP AG. All rights reserved.
Mobile PC
10
Interesting market stats
Approximately 1.3 million mobile phones
are stolen EACH YEAR, just in the UK
More than one in three data breaches last year
involved a mobile device
Major US corporations lose by theft
1,985 USB memory sticks, 1,075 smartphones,
and 640 laptops, EVERY WEEK
120,000 cell phones are left in
Chicago taxi cabs EACH YEAR
113 Smart Phones
are lost every
minute!
In the US, 113 cell phones are lost
EVERY MINUTE
© 2011 SAP AG. All rights reserved.
11
Mobile “Insecurity”
61%
report that business
use of smartphones is
their TOP SECURITY
CONCERN
54%
33%
report at least one
security breach in the
last year
report using data
encryption on mobile
devices
33%
report requiring
advanced
authentication for
corporate
network access
© 2011 SAP AG. All rights reserved.
12
What users are looking for
•
Simplicity and Ease of Use
•
Access to personal data,
photos, movies, apps
•
Access to work email and
work apps/systems
•
Rich Web browsing
•
Freedom of device choice
© 2011 SAP AG. All rights reserved.
13
What it is IT looking for
•
To protect corporate assets from
loss and theft
•
To ensure corporate security policies
are enforced on devices that have
access to the network and data
•
The ability to remotely delete corporate
data on the device
•
Enforce device configurations such as
password, network settings, etc.
•
Asset tracking capabilities
© 2011 SAP AG. All rights reserved.
14
Understanding Mobility Risks and Remedies
Four areas of vulnerability in mobile business operations:
Lost or stolen devices
Risks arising from
combining personal
and work use in
one device
© 2011 SAP AG. All rights reserved.
!
Unauthorized data access
Gaps in device
management and
policy enforcement
15
Lost and stolen devices
User authentication at the device level
Remote lock and wipe
Data encryption
Data fading
Data backup
© 2011 SAP AG. All rights reserved.
16
Unauthorized data access
!
Mobile application provisioning and settings
Remote configuration updates
Event and activity monitoring and logging
Unauthorized access through virus or malware infected
devices
Antivirus software and firewall protection
Remote provisioning of software patches and security
updates
Enforce security policies related to application
downloads
© 2011 SAP AG. All rights reserved.
Activity monitoring and tracking
17
RISKS Related to personal and business use on the same
device
Segregating business functions
on the mobile device
Remote data wipe
Data fading
© 2011 SAP AG. All rights reserved.
18
Gaps in device management and policy enforcement
A single security management platform –
This provides a common security management
console capable of supporting all the device types
and applications that make up a dynamic business
mobility environment
© 2011 SAP AG. All rights reserved.
19
SUMMARY
Risk
Remedies
Data lost due to lost or stolen
devices
•
•
User authentication at the device level
Remote lock and wipe
Data encryption
Data fading
Data backup
Unauthorized user accesses
data with a lost or stolen
phone
•
Same as above
Authorized user gains
unauthorized access to, or
makes inappropriate use of,
proprietary information
•
Security policies
Mobile application provisioning and settings
Remote configuration updates
Event and activity monitoring and logging
Unauthorized access through
virus or malware infected
devices
•
•
•
•
!
•
•
•
•
•
•
Risks arising from combining
personal and work use in one
device
•
•
•
•
© 2011 SAP AG. All rights reserved.
Anti virus software and firewall protection
Remote provisioning of software patches and security
updates
Enforce security policies regarding application downloads
Activity monitoring and tracking
Security policies
Segregating business functions on the mobile device
Remote data wipe
Data fading
20
IT needs to make the rules
•
Security. Anyone who uses their personal smartphone at work should be required to install mobility
management software that enforces passwords, encrypts data and can remotely erase corporate
information on lost or stolen devices.
•
Permissible content. Storing pirated or objectionable content on a personal device that’s utilized for
business should be strictly forbidden. “If you use it for work, it’s a work asset and should be governed by
workplace rules of conduct,”
•
Choice of plan. Companies that cover work-related voice and data charges should make using the
corporate mobile plan mandatory. That way the expenses they underwrite will always be based on low
group rates.
•
Phone number ownership. Employees who leave your firm should take their smartphone with them—but
leave the phone number behind. The last thing you want to do is make it easy for your customers to reach
ex-employees who now work for a competitor. Of course, setting guidelines alone is just a starting point.
You should also provide thorough training, get written agreement from employees to abide by the rules
and punish workers who break them.
© 2011 SAP AG. All rights reserved.
21
Admit personal mobile devices
How do I deny access to unauthorized users? For starters, establish a mandatory security policy
requiring employees to set a strong password on their mobile device and to change it every three to six
months. Mobile management systems can help IT administrators enforce such policies automatically,
without the need for user involvement.
What’s my plan if a personal device gets lost or stolen? Passwords alone won’t be protection enough in
such cases. You’ll need mobile management software offering remote lock and remote wipe capabilities.
Remote lock features enable administrators to temporarily “freeze” a device that may simply have been
misplaced. Remote wipe functionality enables the IT department to erase data from a lost or stolen mobile
device.
How do I remove corporate data from a personal device whose owner is leaving the company? IT
departments that allow enterprise data to reside on a personal device can use management tools to
separate enterprise data from personal data. When an employee leaves, IT can wipe the enterprise data
from that person’s device while leaving personal data unaffected. This approach makes it possible to
cleanse proprietary information from an outgoing employee’s mobile device without also deleting personal
applications and music.
How do I keep prying eyes away from confidential files? Use mobility management software to encrypt
enterprise data, both when it’s in transit to the device over a wireless network and when it’s at “at rest” in the
device’s memory. Use an application platform to develop your internal applications so that you can apply
your company security to that application instead of relying on 3rd parties.
© 2011 SAP AG. All rights reserved.
22
Lessen the threat
•
Be aware of all types of threats to mobile devices, including device loss, malware, bugs, and out-of-date
mobile OS software
•
Create mobile governance policies that emphasize security; educate employees on how to adhere to
those rules
•
Use a mobile management platform that allows IT to centrally deploy, configure, and manage a fleet of
multiplatform mobile devices (whether personally owned or company-purchased)
•
Use mobile management tools that offer IT visibility into device status, so security breaches can be
quickly and automatically shut down
•
Restrict or limit known vulnerabilities, including application download, camera, Bluetooth, or Wi-Fi
•
Implement a portfolio of device security tools that include alphanumeric passcodes, authentication,
encryption, and remote wipe
•
Control download and installation of any apps that give users access to corporate information.
© 2011 SAP AG. All rights reserved.
23
Mobile security as a way of life
•
Support for a broad spectrum of mobile devices
•
The platform must support strong user authentication
•
The platform must support strong encryption
•
Able to set access restrictions and security policies for all mobile business applications
•
The platform must support strong over-the-air controls like remote provisioning, remote device
configuration, remote device lock, and remote data wipe
•
The platform must have a depth of sophisticated security controls and activity monitoring capability
•
The platform must support (as available) antivirus software, firewall protection, including over the air
distribution of patches and security updates
© 2011 SAP AG. All rights reserved.
24
What to do next
•
Discover mobile devices on the network.
•
Determine the back-office systems employees want to access.
•
Formalize user types and set policies.
•
Get ready to take action.
•
Add password and encryption policies plus remote wipe capabilities at a minimum.
•
Consider separating personal data from business data.
•
Enable users to be self-sufficient.
© 2011 SAP AG. All rights reserved.
25
Checklist of Key Moves
•
Change your mind-set. Start viewing workplace use of smartphones as an opportunity rather than a
threat.
•
Ensure that you have firm employee guidelines in place regarding issues such as storing pirated or
objectionable content on a personal mobile device, choosing voice and data plans and getting technical
support.
•
Equip your IT department to realize the productivity-enhancing potential of personal mobile devices by
deploying tools it can use to “mobilize” key business processes; provide mobile access to back-end ERP
and CRM systems; and create graphical, touch-friendly smartphone apps.
•
Thoroughly examine the potential security issues associated with admitting personal mobile devices
to the enterprise, and begin formulating plans for addressing them.
© 2011 SAP AG. All rights reserved.
26
Thank You