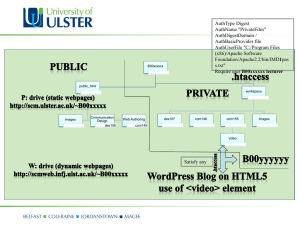
VET – Vetting Commodity IT Software and Firmware
advertisement

VET – Vetting Commodity IT Software and Firmware DARPA – SN – 13 – 07 In about April of 2012 it was noted by the DoD and other groups that foreign governments had access to 80 percent of the world’s communications, event military-grade encryption. This was mainly being done to two companies that provided the world with equipment and services used by 45 of the top 50 telecommunication centers in the world. This company brag that a third of the world’s population is hook up to its network gear, as well as being the third largest of Smart Phone company in the world. This access gave their government’s unbridled, backdoor access into data and proprietary information belonging to some 140 nations. This access could have allowed widespread spying and sabotage in the event of any hostilities . To answer this attach on our communication system on March 26 2013 the president signed into law restrictions on the acquisition of equipment from the offending company / government to not be used by the National Science Foundation, NASA, and the Departments of Commerce and Justice. As well as action being taken by the Australian, British, and Indian governments. In addition DARPS has put out a proposal for the creation of their VET program. This proposal with was dated for 12-19-2012 was extended until 2-12013 covering the tools and technology needed to protect our communication networks. The DARPA VET program will seek to demonstrate that it is technically feasible for the Department of Defense (DoD) to determine that the software and firmware shipped on commodity Information Technology (IT) devices are free of broad classes of backdoors and other hidden malicious functionality. Some common examples of commodity IT devices include mobile phones, network routers, servers, printers, fax, and computer workstations With the main charge to the ACTA from the FCC being to protect the network from harm then it should be a natural next step for the ACTA and the Test LABs to add the DARPA “VET Program” test requirements for testing before an US Number is applied to any device under test. It should also be noted that because the devices being affected to-date, can be both IP and TDM. It is subjected that the device testing requirement governing the ACTA should be extended to cover IP based devices as well. There by covering every types of IT and telecommunication equipment that can be connected to the National Network from harming the Network be it IP or TDM. It should also be noted that with the test sampling requirement on the Test LADs under the ACTA rules that the repeat testing of any device from time to time should keep harmful technology from being added to any device after the fact. The VET program must overcome three major technical challenges in order to demonstrate that potential deployment scenarios, are technically feasible: (1) Defining malice - Given a sample device, how can DoD analysts produce a prioritized checklist of software and firmware components to examine and broad classes of hidden malicious functionality to rule out? (2) Confirming the absence of malice - Given a checklist of software and firmware components to examine and broad classes of hidden malicious functionality to rule out, how can DoD analysts demonstrate the absence of those broad classes of hidden malicious functionality? (3) Examining equipment at scale - Given a means for DoD analysts to demonstrate the absence of broad classes of hidden malicious functionality in sample devices in the lab, how can this procedure scale to non-specialist technicians who must vet every individual new device in DoD before deployment?