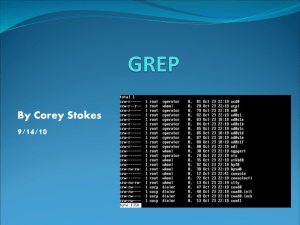
PowerPoint - Broome Community College
advertisement

Windows Memory Forensics: Down the Rabbit Hole Professor James L. Antonakos Computer Science Department Overview This session presents techniques to capture live memory data from a Windows 7 system and process it for relevant forensics information. Techniques to search the captured memory data using regular expressions are covered, as is the nature of protected-mode memory operation, including virtual memory. Topics • • • • • • • My Teaching Goals Building the Memory Image Acquiring the Memory Image First Step: Using STRINGS Second Step: Looking for Stuff Regular Expressions Searching with GREP Topics (continued) • • • • • • • • Analyzing Memory 80x86 Real Mode 80x86 Protected Mode Virtual (Linear) Addressing Paging Demand Paging Malware Analysis Anti-Memory Forensics My Teaching Goals • Get students interested, excited, and curious about computer forensics. • Explain why we want to do memory forensics. • Show students how to use different software tools. • Reinforce knowledge from other courses. • Show students how to learn. • Propose strategies that work (and that do not work). • Increase my own knowledge by learning from students. Building the Memory Image • Do some typical work on a Windows 7 laptop: Open web-based email and send a message. Open Internet Explorer and log into Yahoo email. Open DOS window and get a directory listing. Do Yahoo search for “win7-memory-forensics.” Look at Task Manager and NETSTAT. Check Computer Properties. Building the Memory Image Building the Memory Image Building the Memory Image Building the Memory Image Building the Memory Image Building the Memory Image Acquiring the Memory Image Acquiring the Memory Image Acquiring the Memory Image Acquiring the Memory Image • Consider the memory footprint of the capture tool: win64dd.exe 108 KB FTKImager.exe 6.9 MB • Other software tools: Nigilant32, ProDiscover IR, KntDD • How about no memory footprint via hardware acquisition? Use FireWire’s DMA capability. Tribble, CoPilot, RAM Capture Tool PCI cards… must be preinstalled. First Step: Using STRINGS • Use the STRINGS program to extract ASCII strings from memory dump file. • Command line: Strings physmem.dmp > memstr.txt • Resulting output file is 173 MB in size. • Open memstr.txt with Microsoft Word: Over 18,000 pages of text… but we will see this is a false indicator of the actual page count. Second Step: Looking for Stuff Second Step: Looking for Stuff Second Step: Looking for Stuff Splitting the Results Splitting the Results Splitting the Results Splitting the Results Splitting the Results Splitting the Results Giving one file to each student to examine as a semester project and allowing for 10 seconds to view each page requires an average of 17 hours per document for review. Splitting the Results Regular Expressions • Regular expressions are powerful tools for representing and matching strings. • There are three basic ways to form a regular expression: AB (concatenation, A followed by B) A | B (selection, A or B) A* (0 or more occurrences of A) A+ (1 or more occurrences of A) • Depending on the tool, the actual regular expression will be different. Regular Expressions • Some examples: antonakosjl abc | def a (b | c)*d • The third example can match an infinite number of strings, such as ad, abd, acd, abbd, accd, abcd, acbd, abbbd, acccd, abcbd, abbcd, abcbcbcbcbccbcbbcbcbbcbcbcbbcbcbccd, etc. Regular Expressions • In the Windows GREP tool there are additional ways of representing regular expressions: Use square brackets to represent a group of symbols, such as [0-9] or [a-z] or [A-Z] Use . to match a single character Use + to match 1 or more characters Use \ to match a special symbol Example: to match the string iontransfer@yahoo.com we use the expression iontransfer\@yahoo\.com Searching with GREP • The first thing to do is enter the regular expression you wish to search for: Searching with GREP • Then select the folder: Searching with GREP • Then the type of file to search: Searching with GREP • Now click Finish to begin the search: Searching with GREP • The result of the search, with line numbers: Searching with GREP • Searching for an email address: Searching with GREP • Email address found in two places: Analyzing Memory • One tool for analyzing memory is Mandiant’s Memoryze (and its Audit Viewer front end): Analyzing Memory • Another tool is FTK from AccessData. Here we see a sample of 819 images recovered from the memory image. Note that many images are broken. Analyzing Memory • FTK contains two powerful search tools. This is the Index search window: Analyzing Memory • This is the Live search window. These searches take more time. Ability to use Regular Expressions is built in, along with large list of expressions. Analyzing Memory • Other tools: EnCase PTFinder FTimes Volatility Windows Debugging Tools 80x86 Real Mode • The architecture of the 8x06 protected mode is significantly different from that of real mode. • Real-mode operation refers to the original 8086 (or 8088) architecture, which provided four 16-bit segment registers (CS, DS, ES, and SS), and a 20-bit address bus. • In real mode, addresses are generated by shifting 16bit segment registers to the left by four bits, and adding a 16-bit offset to create a 20-bit physical address. • The 20-bit address supports a 1 MB real-mode addressing space. 80x86 Protected Mode • In protected-mode, memory addresses are generated in a totally different way. • Segment registers are now called segment selectors, and point to a structure called a segment descriptor. • The segment descriptor contains addressing and control information which is used to control how a 32-bit linear address is generated. • These addresses may then be further translated by a paging mechanism before emerging as a physical address somewhere in the Pentium's 4 GB addressing space. Virtual (Linear) Addressing Paging • The 80x86 protected mode supports translation of virtual (linear) addresses into physical addresses. • This is done through the use of special tables that map portions of the virtual address into actual physical memory locations. • Physical memory is divided into fixed-size page frames of 4KB each. • 32-bit virtual (linear) addresses generated by a running task select entries in the systems page directory and page table, which translate the upper 20 bits of the virtual address into the actual physical address where a page frame is located. • The lower 12 bits of the virtual address are not translated and point to one of 4,096 byte locations within a page frame. Paging Paging • How is a 32-bit virtual address translated into a physical address? • The upper 10 bits of the virtual address select one of 1,024 entries in the page directory. • The base address of the page directory is stored in the page directory base register (PDBR). • Each entry in the page directory is 4 bytes wide and contains the base address of a page table. Paging • The next 10 bits from the virtual address select one of 1,024 entries in the page table pointed to by the page directory entry. • This entry is also 4 bytes wide and contains the base address of the actual physical memory page frame. • This address is combined with the lower 12 bits of the virtual address to access the desired location in memory. Paging Paging (An Example) Paging • Page translation allows the physical memory used by a system to be much smaller than the linear addressing space. • For instance, the Pentium’s 4GB linear addressing space may be mapped to a physical memory of only 512MB. • The pages used by a program do not need to be stored consecutively. • A program’s code and data may be spread out all over physical memory, and even moved around (with help from the hard disk) while the program is executing! • This helps to explain why the linear addresses are also called virtual addresses, since they have no relation to the actual physical memory address used, except for the lower 12 bits. Demand Paging Demand Paging Demand Paging Demand Paging Demand Paging Demand Paging Demand Paging Demand Paging • Since the PARTINFO.SYS file contains copies of data that was previously in RAM, it has forensic value. • Locating individual items of data by tracing their virtual addresses will require effort and patience. • Pages can move around during a live capture of RAM, so memory image may be not 100% faithful. • In addition to PARTINFO.SYS we also want to examine HIBERFIL.SYS, the system hibernation file, which contains a complete copy of RAM contents. Malware Analysis • Capture malware process running in memory using LordPE. Malware Analysis • Right-click on process and select the dump full option. Malware Analysis • Why use LordPE or some other tool? Capture process as it exists in RAM (including data associated with the process… perhaps this includes a digital signature that can decrypt the process communication). Process may have come in via network (Witty worm) and not reside anywhere on disk. Process may be encrypted (packed) while residing on disk and decrypted (unpacked) after loading into RAM. Having process image allows it to be loaded and executed by a debugger (such as OllyDbg or IDA Pro) for investigation. Anti-Memory Forensics • Malware can employ tricks to suppress attempts at memory forensics, such as: Break links in EPROCESS data structure to hide process (DKOM – Direct Kernel Object Manipulation). Modify process data structure to change its signature. • If operating system is compromised (via rootkit), can a captured memory image be trusted? • How does FireWire’s DMA capability provide some relief? Is it foolproof? Anti-Memory Forensics • FireWire goes through Northbridge chipset to get at motherboard RAM via built-in memory controller. • Reprogram Memory-Mapped I/O registers in Northbridge to redirect memory accesses by DMA controller and provide “garbage” memory reads. • See Joanna Rutkowska (COSEINC Advanced Malware Labs) presentation “Beyond The CPU: Defeating Hardware Based RAM Acquisition” for a detailed explanation. Thank You ! Professor James L. Antonakos antonakos_j@sunybroome.edu (607) 778-5122