Mirage Malware - Clemson University
advertisement

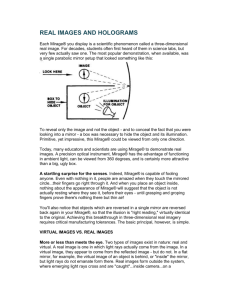
CLEMSON UNIVERSITY MIRAGE MALWARE SIDDARTHA ELETI CONTENTS: 1. WHAT IS MALWARE 2. WHAT IS MIRAGE 3. HOW DOES MIRAGE WORK 4. CONCLUSION WHAT IS MALWARE? • Malware is a malicious program that is meant to disrupt computer operations, gather sensitive information, or gain access to private computer systems. • Malware could be code or scripts or active content etc. • Over the past few decades many malwares like STUXNET, Nimda, myDoom etc. have affected organizations, personal computers etc. and this year among many others its “MIRAGE” . WHAT IS MIRAGE? • Mirage is a malware that has appeared under the radar since April 2012. • Dell SecureWorks has been tracking a cyber espionage campaign that uses a remote access Trojan (RAT) named Mirage (also known as MirageFox. HOW DOES MIRAGE WORK? SPEAR-PISHING • Mirage was intended to attack individuals at big oil and energy companies. • So it uses a technique called Spear-Pishing. • Spear-Pishing is a process of acquiring sensitive information from specific individuals or an organization by masquerading as a trustworthy entity. • In this scenario, the attackers gather personal information about the targets to increase their probability of success. INSTALLATION • The spearpishing emails contains an attachment that includes malicious payload which installs a copy of Mirage on the computer • The attachments are stand-alone executable files that open an embedded PDF and execute the Mirage Trojan in the background • Mirage installs itself into “c:\Windows” or the Users Home directory • It also creates a backboor which waits for instructions from the attacker • Mirage creates registry keys on every boot so that the system remains infected COMMUNICATION • Mirage phones home to its c2 servers using standard HTTP Post request over the ports 80, 443 and 8080. • It can also use SSL for added security. • Iniitial phone-home request contains detailed system information of the infected system. – Example : • Once the c2 server gets this it responds with HTTP response code “200 ok”. • After a successful connection, infected system still sends regular check-in updates with its mac address in it. • All of its communications with its command and control servers are disguised to appear like the URL traffic pattern associated with Google searches. VARIANT 2: • Another variant of Mirage uses HTTP Get requests for communication. • In this variant instead of ‘Mirage’ in the beginning of the message it uses “It is the end of the world and I feel Fine", from the REM song "It's the end of the world." VICTIMS • The picture below shows the sources of infected hosts. • After deep analysis researchers have found one infected host, an executive-level finance manager of the Philippine-based oil company. ATTACKERS • SecureWorks have identified that the attackers were operating out of china. • Used dynamic DNS domains for callbacks to c2 servers. • The hosting companies in US were running Htran. In 2011 analysis the software author was identified as member of Chinese hacker group HUC, the Honker Union of China. • Despite efforts during analysis of home phone activity researches four unique second-level domains were identified of which two shares a common email Id. INTENTIONS • The intention behind the attacks are still not known but they have hit many energy and oil companies world wide. • Its unclear about what kind of data they were trying to steal from the specific targets yet. CONCLUSION • Mirage was a light weight simple malware which proved to be effective because it was able to reach mid and senior-level executives. • This malware represents only a small piece of an ongoing worldwide campaign. • This proves that for a successful campaign only a small quantity of infected systems are required. CITED SITES • http://www.secureworks.com/cyber-threat-intelligence/threats/themirage-campaign/ • http://news.cnet.com/8301-1009_3-57517388-83/cyberspying-effortdrops-mirage-on-energy-firms/ • http://www.scmagazine.com/new-espionage-campaign-tied-to-rsabreach-ghostnet-attacks/article/259991/ • http://en.wikipedia.org/wiki/Malware Thank you