MIRAGE Malware
advertisement

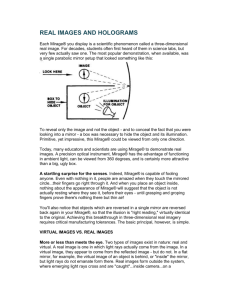
MIRAGE CPSC 620 Project By Neeraj Jain Hiranmayi Pai Table of Contents Introduction Background Analysis Identification of Victims Threat Factors Conclusion Introduction What is a malware? What is a “Mirage” malware? Background Is linked to the same hackers behind the RSA breach last year [1]. Mirage shares attributes with the malware families JKDDOS and Lingbo Mirage Trojan targets mid-level to senior-level executives by sending out spear-phishing email.` Analysis Distribution Vector Behavior Analysis Control and Command Server Operations Variants Distribution Vector The spear phishing emails contain an attachment that includes a malicious payload that installs a copy of Mirage. CTU researchers have identified several files that drop and execute a copy of Mirage onto a target system. These "droppers" are designed to look and behave like PDF documents. Behavior Analysis There are two main variants of the Mirage Trojan. Variants are based on the way the trojan communicates with the command and control (C2) servers. When Mirage executes, the original file copies itself to a folder under C:\Documents and Settings\<USER>\ or C:\Windows\ and then deletes the original file. CTU researchers have observed the following filenames created after execution: svchost.exe ,ernel32.dll, thumb.db, csrss.exe, Reader_SL.exe, MSN.exe Control and Command Server Operations - 1 Mirage tries to send a system profile by contacting the C2 server using a standard HTTP request. This profile contains the CPU speed, memory size, system name and username. It is observed that this communication occurs over ports 80, 443 and 8080 Control and Command Server Operations - 2 Variant 1 Control and Command Server Operations - 3 Raw values Raw hex Raw decimal Encoded decimal Encoded hex Encoded values M 0x4d i 0x69 r 0x72 a 0x61 g 0x67 e 0x65 77 105 114 97 103 101 77 106 116 100 107 106 0x4d 0x6a 0x74 0x64 0x6b 0x6a M j t d k j Control and Command Server Operations - 4 The second variant of Mirage uses HTTP GET requests Variants Several Mirage variants are customized for specific need, not for widespread targeting. One of the variant was found configured with the default credentials of the targeted environments web proxy servers. Identification of Victims Threat Actors When investigating the DNS addresses of the C2 servers, CTU researchers identified several IP addresses of hosting companies based in the United States that are running HTran. In the CTU research team's 2011 analysis of HTran, the software's author was identified as a member of the Chinese hacker group HUC, the Honker Union of China. Conclusion Mirage represents only one small piece of malware involved in an ongoing worldwide campaign[2]. The IP addresses of the systems used by hackers to remotely control Mirage-infected machines belong to the China Beijing Province Network (AS4808), as did three of the IP addresses used in the Sin Digoo campaign [3]. For companies in the targeted industries, using active intrusion detection and prevention systems as well as DNS monitoring for malicious domains is essential to detecting this activity. References 1) 2) 3) http://www.secureworks.com/cyber-threatintelligence/threats/the-mirage-campaign/ http://www.securityweek.com/cyber-espionage-campaigntargets-oil-companies http://www.theregister.co.uk/2012/09/21/mirage_cyberes pionage_campaign/