strategic_intelligence_2
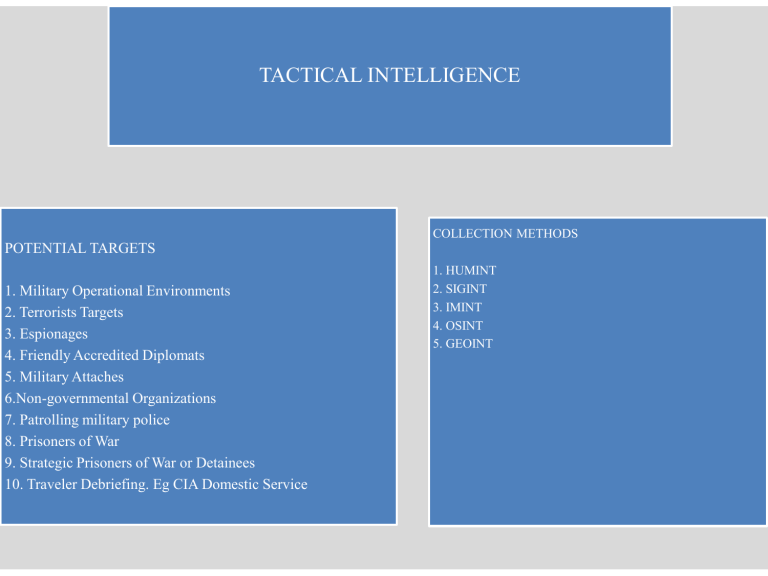
TACTICAL INTELLIGENCE
POTENTIAL TARGETS
1. Military Operational Environments
2. Terrorists Targets
3. Espionages
4. Friendly Accredited Diplomats
5. Military Attaches
6.Non-governmental Organizations
7. Patrolling military police
8. Prisoners of War
9. Strategic Prisoners of War or Detainees
10. Traveler Debriefing. Eg CIA Domestic Service
COLLECTION METHODS
1. HUMINT
2. SIGINT
3. IMINT
4. OSINT
5. GEOINT
POTENTIAL TARGETS
1. Neutral Forces
2. Friendly Forces
3. Civilian Population in an area of combat operation
STRATEGIC INTELLIGENCE
COLLECTION METHOD
1. MASINT
-Electro-optical
-Nuclear
-Geophysical
-Radar
-Materials
-Radiofrequency
2. ACHELON
3. Signal Intelligence
4. Imagery Intelligence
5. OSINT
6. SIGINT
7. TECHINT
8. FININT
9. CYBINT/DNINT
QUIZ: Is CSIS allowed to recruit university students to spy on their colleagues on Campus?
One major method used by CSIS and other security intelligence, and other worldwide security intelligence units and law implementation agencies through the world, is the recruitment of human sources of information. In case a CSIS investigation requires the direction of intrusive devices or human source, the facility is necessary, pursuant to ministerial course, to acquire ministerial approval.
This method of obtaining information is known as open source intelligence. It is however good to note that the information obtained through this process does become verifiable or authentic until it is vitiated and verified by a qualified analyst. Within a university setup, the intelligence unit can obtain information on intentions of foreign nations since students come from different countries. This is a strategic intelligence method. Conversely, the information can also help inform about the plans that terrorists may have on a country’s security since terrorist are more likely to use students to execute their malevolent plans. This is a practical application of human intelligence (HUMINT) and a practical application of OSINT(Open Source Intelligence). This method of obtaining information makes use of both Strategic and Tactical Intelligence.
References
Rapp, Adam, Raj Agnihotri, and Thomas L. Baker. "Conceptualizing salesperson competitive intelligence: an individual-level perspective." Journal of Personal Selling & Sales Management 31, no. 2 (2011): 141-155.
Loshin, David. Business intelligence: the savvy manager's guide . Newnes, 2012.
Marrin, Stephen. "The 9/11 Terrorist Attacks: A Failure of Policy Not Strategic Intelligence Analysis." Intelligence and National
Security 26, no. 2-3 (2011): 182-202.
Stone, Merlin David, and Neil David Woodcock. "Interactive, direct and digital marketing: A future that depends on better use of business intelligence." Journal of Research in Interactive Marketing 8, no. 1 (2014): 4-17.
Koseoglu, Mehmet Ali, Kemal Karayormuk, John A. Parnell, and Michael L. Menefee. "Competitive intelligence: evidence from
Turkish SMEs." International Journal of Entrepreneurship and Small Business 13, no. 3 (2011): 333-349.
Ratcliffe, Jerry H. Intelligence-led policing. Routledge, 2012.