Access Control Intro, DAC and MAC
advertisement

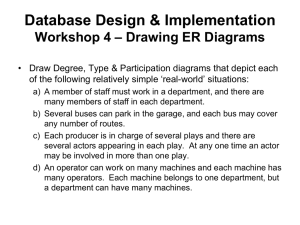
Access Control Intro, DAC and MAC System Security System Security • It is concerned with regulating how entities use resources in a system • It consists of two main phases: • Authentication: uniquely identifying entities • Authorisation: assigning access rights to entities Authentication Phase • It is only concerned with identifying an entity against a known set • Assigning a unique identifier to the entity (i.e., user name) • Using a secret (supposedly) known only to the specific entity • Alternatively, using a unique feature that characterizes the entity Authorisation Phase • Known also as Access Control • “The prevention of unauthorized use of a resource, including the prevention of use of a resource in an unauthorized manner” • It assumes users have been • authenticated to the system • assigned access rights to certain resources on the system (for instance, by an admin) Access Control Requirements • Reliable Input • Authenticated entities • Genuine information • Least Privilege • Entities granted minimum set of access rights • Administrative Duties • Only a special entity should be able to manage access rights for other entities Access Control Refinements • • • • Separation of Duty Fine Vs. Coarse Specifications Open and Closed policies (Automated) Conflict Resolution Access Control Elements • Subject - entity that can access objects • a process representing user/application • Object - access controlled resource • e.g. files, directories, records, programs etc • Access right - way in which subject accesses an object • e.g. read, write, execute, delete, create, search Security Modules Access Control Models • • • • • Discretionary AC (DAC) Mandatory AC (MAC) Role-based AC (RBAC) Usage Control (UCON) Policy-based Access Control Discretionary Access Control • A means of restricting access to objects based on the identity of subjects and/or groups to which they belong. • The controls are discretionary in the sense that a subject with a certain access permission is capable of passing that permission on to any other subject • Subjects are able to assign rights to other subjects on the objects they control • Model used in operating systems and DB management systems • Often provided using an access matrix Access Control Matrix Access Control List Capability List Capability Myths Demolished: http://srl.cs.jhu.edu/pubs/SRL2003-02.pdf Access Matrix Details UNIX Access Control Lists • Modern UNIX systems support ACLs • Can specify any number of additional users / groups and associated rwx permissions • ACLs are optional extensions to std perms Mandatory Access Control • Entities cannot enable other entities to access their resources • It enforces a lattice between labels assigned to subjects and object • security labels: how sensitive or critical a system resource is • security clearances: which entities are eligible to access certain resources MAC: The Bell-LaPadula Model The main goal is to control the confidentiality of information MAC Confidentiality Rules Simple Security Property: No Read-Up Read MAC Confidentiality Rules *(Star)property: No Write-Down Write MAC Confidentiality Rules Strong *(Star)-property: No Write-Down & No Write-up Write MAC: Biba Integrity Model The main goal is to control the integrity of information MAC Integrity Rules Simple Integrity Axiom: No Read Down Read MAC Integrity Rules *(Star)-Integrity Axiom: No Write Up Write Where is MAC used • BLP: Implemented the multi-level security policy for US Department of Defense • BIBA: Implemented in the FreeBSD MAC policy • A combined versions of BLP and BIBA is used in Android Summary • Introduced access control principles • subjects, objects, access rights • Discretionary Access Control • access matrix, access control lists (ACLs), capability tickets • UNIX traditional and ACL mechanisms • Mandatory Access Control • Bell-Lapadula • Biba Resources • Chapter 8 in Mark Stamp, Information Security: Principles and Practice, Wiley 2011. • Matt Bishop, Computer Security: Art and Science, AddisonWesley 2003. Questions?