3rd Party Categories * Risk Assessment
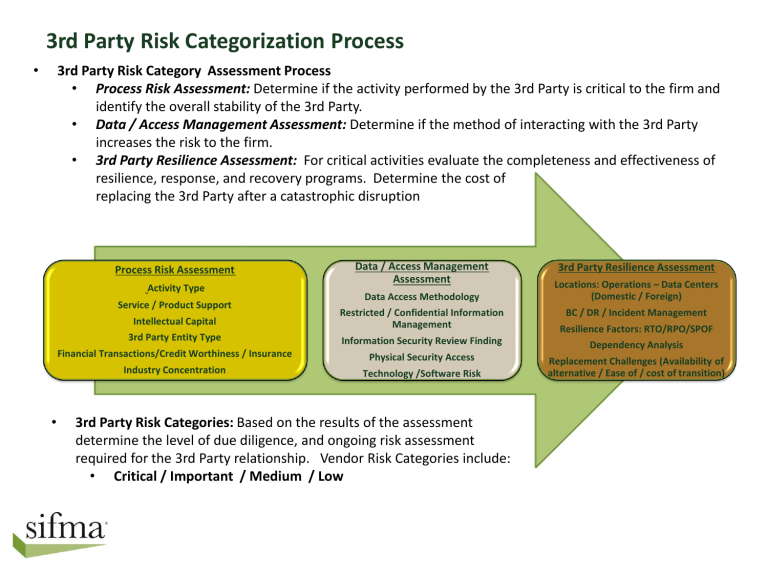
3rd Party Risk Categorization Process
• 3rd Party Risk Category Assessment Process
• Process Risk Assessment: Determine if the activity performed by the 3rd Party is critical to the firm and identify the overall stability of the 3rd Party.
• Data / Access Management Assessment: Determine if the method of interacting with the 3rd Party increases the risk to the firm.
• 3rd Party Resilience Assessment: For critical activities evaluate the completeness and effectiveness of resilience, response, and recovery programs. Determine the cost of replacing the 3rd Party after a catastrophic disruption
Process Risk Assessment
Activity Type
Service / Product Support
Intellectual Capital
3rd Party Entity Type
Financial Transactions/Credit Worthiness / Insurance
Industry Concentration
Data / Access Management
Assessment
Data Access Methodology
Restricted / Confidential Information
Management
Information Security Review Finding
Physical Security Access
Technology /Software Risk
• 3rd Party Risk Categories: Based on the results of the assessment determine the level of due diligence, and ongoing risk assessment required for the 3rd Party relationship. Vendor Risk Categories include:
• Critical / Important / Medium / Low
3rd Party Resilience Assessment
Locations: Operations – Data Centers
(Domestic / Foreign)
BC / DR / Incident Management
Resilience Factors: RTO/RPO/SPOF
Dependency Analysis
Replacement Challenges (Availability of alternative / Ease of / cost of transition)
3rd Party Risk Category Assessment Guidance
Activity Type: Define activity types and associated risks levels.
Service / Product Support:
Determine if the 3 rd Party will support an essential service/product of the firm and the impact to the firm and its customers if the 3 rd Party has a significant business disruption.
Intellectual Capital: Determine if the
3rd Party service provide will have exposure to the firm’s intellectual capital.
3rd Party Entity Type: Define the types of 3rd Party entity and the potential risks associated
(Government / Self-Regulated /
Public / Private)
Financial Transactions /Credit
Worthiness / Insurance: Determine the volume and value of financial transactions involving the 3 rd Party.
Assess if the 3 rd Party’s credit worthiness and if they have adequate insurance coverage.
Industry Concentration: Determine if the 3rd Party service provider supports a significant portion of the marketplace and if that service provider was out of operation how would it impact the industry.
Data Access Methodology: Define the methods for sharing information with
3 rd party service providers and how much risk is associated with each method.
Restricted / Confidential Information
Management: Determine the data privacy levels associated with the 3rd
Party relationship and the level of risk associated with data privacy requirements
Information Security Review Findings:
Critical 3rd Party service providers must go through a comprehensive information security review. Findings associated with this review must be assessed to determine the level of risk to the firm. If needed risk mitigation plans need to be developed before proceeding.
Physical Security Access: Validate that the 3rd Party service provider has adequate physical security to protect their ability to provide services to the firm as defined within the contract.
Technology / Software Risk: Assess the risks associated with the 3 rd Party’s use of technology infrastructure and software. Determine the impact of specialized or customized use of the environment.
Locations: Assess the location of all operations and data centers that will support the service to determine if they are adequately geographically disbursed.
Determine the risk associated with the domestic / international locations of the service provider including exposure to natural and man-made threats.
BC / DR / Incident Management: Assess the effectiveness of the 3rd Party service provider’s business continuity, disaster recovery and incident management programs to determine completeness and effectiveness.
Resilience Factors: Determine the value of various resilience factors for services provided by a 3rd Party Establish value parameters for each factor to determine the level of resilience required for critical services. Factors include: RTO (Recovery
Time Objective), RPO (Recovery Point
Objective), and SPOF (Single Point of
Failure).
Dependency Analysis: Evaluate the dependency of the 3rd Party on additional external resources. Evaluate these relationships based on the potential impact to the service provided to your firm.
Replacement Challenges: Determine the cost in funds and effort to replace a 3rd
Party service provider in the event that the
3rd Party is unavailable for a significant period of time, or has breached its legal obligations to the firm.