Rogue Access Points
advertisement
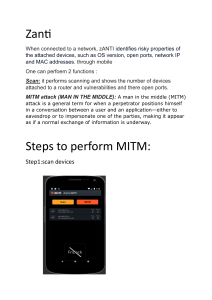
Any unauthorized device that provides wireless access Implemented using software, hardware, or a combination of both It can be intentional or unintentionally set up Employees attempting to put in their own wireless at work Mobile hotspots from cell carriers Honeypot to see what people are up to on your network Nefarious activities… It’s a huge security risk! In a corporate environment it allows unauthorized access to the network Often they’re misconfigured and lack security features Your everyday wireless router Mobile hotspots Wi-Fi Pineapple Hardware Access Point for Man-inthe-Middle attacks Connection from › › › › Mobile Broadband Android Tethering Ethernet Auxillary Wireless Adapter Managed via SSH or the Web Interface Small, easily concealed and battery powered Expandable with community modules MITM attack tools: Karma, DNS Spoof, SSL Strip, URL Snarf, Ngrep and more via the modules Wireless cracking, replay, and deauth attacks with the Aircrack-NG suite Autostart service like karma and reverse ssh for instant attack on power-up Setup with : › Ad-hoc › Connectify (Windows) › Alfa Wireless Lan Utility (for Alfa wireless card on Windows) › Airbase-ng (Linux) Airbase-ng is multi-purpose tool aimed at attacking clients as opposed to the access point itself Implements the Caffe Latte WEP client attack Implements the Hirte WEP client attack WPA/WPA2 handshake capture Act as an ad-hoc access point Act as a full featured AP Filter info by SSID or client MAC address Manipulate and resend packets Encrypt & decrypt sent &received packets -a bssid : set Access Point MAC address -i iface : capture packets from this interface -w WEP key : use this WEP key to encrypt/decrypt packets -h MAC : source mac for MITM mode -f disallow : disallow specified client MACs (default: allow) -W 0|1 : [don't] set WEP flag in beacons 0|1 (default: auto) -q : quiet (do not print statistics) -v : verbose (print more messages) (long --verbose) -M : M-I-T-M between [specified] clients and bssids (NOT CURRENTLY IMPLEMENTED) -A : Ad-Hoc Mode -Y in|out|both : external packet processing -c channel : sets the channel the AP is running on -X : hidden ESSID -s : force shared key authentication -S : set shared key challenge length (default: 128) -L : Caffe-Latte attack (long --caffe-latte) -N : Hirte attack (cfrag attack), creates arp request against wep client (long –cfrag) -x nbpps : number of packets per second (default: 100) -y : disables responses to broadcast probes -0 : set all WPA,WEP,open tags. can't be used with -z & -Z -z type : sets WPA1 tags. 1=WEP40 2=TKIP 3=WRAP 4=CCMP 5=WEP104 -Z type : same as -z, but for WPA2 -V type : fake EAPOL 1=MD5 2=SHA1 3=auto -F prefix : write all sent and received frames into pcap file -P : respond to all probes, even when specifying ESSIDs -I interval : sets the beacon interval (ms) -C seconds : enables beaconing of probed ESSID values (requires -P) Put wireless card 1. airmon-ng start wlan0 in monitor mode 2. airbase-ng -e "Free Wifi" c 1 -v mon0 2. Create SSID on 3. ifconfig at0 up the wireless brctl addbr mitm interface brctl addif mitm eth0 3. Bring up the AP brctl addif mitm at0 ifconfig eth0 0.0.0.0 up 4. Configure the ifconfig at0 0.0.0.0 up bridged adapters dhclient3 mitm 5. Profit 1.