DHCP Security Analysis
advertisement

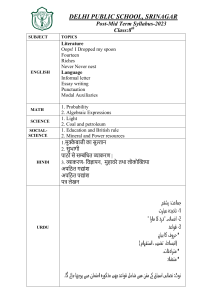
DHCP Security Analysis Dallas Holmes / Matt MacClary ECE 478 Project Spring 2003 What is DHCP? • • • • • • Dynamic Host Configuration Protocol UDP protocol for IP Discovery Based Ratified by the IETF in 1997 Used on most networks OSU utilizes DHCP heavily Why use DHCP? • • • • Simple host configuration “Plug and Surf” Centralized address accounting Distribution of vital host information – Hostname, DNS, WINS, Gateway, etc. 3 Significant Problems 1. Discovery based – Any host can respond to query 2. No server authentication – client trusts any server that responds 3. No client authentication – server may assign an address to any client Problem 1: Anybody can answer • Anybody? – – • An attacker could place a “rouge” server Authoritative (legitimate) server. Who will the client listen to? – Logically “closest” server • • fastest CPU, fastest network, lowest load Server with free leases Changing “logically closest” • Load the authoritative DHCP server • Take all the leases away • Load the network segment How much does it take? Problem 2: Server Authentication • Client must trust what the server sends • Server can send fake DNS servers – client may be shown a misleading resource – client may be denied access to a resource • Server can send invalid gateway address – Attacker could redirect switched traffic – Loss of privacy Which is Real? Real Login Screen Fake Login Screen Problem 3: Host Authentication • Any client may join network – Simply plug in and server assigns address – Some networks configure network trust (MAC) • Client may gain access to network shares • Client may abuse network – Start a rouge DHCP server – Generate heavy traffic or attack other networks Solution • SSL Style Public 3rd Party Certificate Authority – Two-way authentication • Server Certificate • Client Certificate – Requires changes to DHCP server and client • Slow to implement and gain acceptance • Expensive – Certificates cost money – Changing server configurations costs money