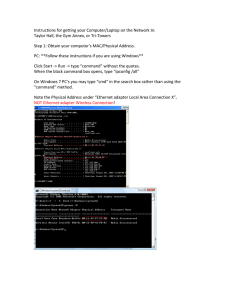
● Intranet is a term used to refer to a private connection of LANs and WANs that belongs to an organization. An intranet is designed to be accessible only by the organization's members, employees, or others with authorization. ● Powerline networking adds the ability to connect a device to the network using an adapter wherever there is an electrical outlet. Uses existing electrical wiring to send data. It does not replace physical cabling, but can add functionality in places where wireless access points cannot be used or cannot reach devices. ● Network security includes protecting the confidentiality of data that is on the network. In this case, because confidential data has been made available to unauthorized users. ● DSL - is always on, high bandwidth, connection that runs over telephone lines. ● CABLE - uses the same coaxial cable that carries television signals into homes to provide internet access. ● Dialup - telephone is much slower than DSL or cable, but is the least expensive option for users because it can use any telephone line and a simple modem. ● Satellite - requires a clear line of sight and is affected by trees and other obstructions. ● Criteria for choosing a network medium: ● ○ Distance ○ Environment ○ Amount of data ○ Speed ○ Cost of the cable/medium Video conferencing and voice calls - utilizes real time audio and video communications. Examples of data traffic that cannot buffer. ○ QoS - will ensure an uninterrupted user experience. ● Minimum requirements for home networks - setting up a firewall, antiviruses, etc. ● Passwords - can be used to restrict access to the VTY and console interfaces. ● Layer 2 switch - there is a switch virtual interface (SVI) that provides a means for remotely managing the device. ● RAM - stores data that is used by the device to support network operations. The running configuration is stored in RAM. This memory is considered volatile memory because data is lost during a power cycle. ● Flash Memory - a type of nonvolatile memory that erases data in units called blocks and rewrites data at the byte level. ● SSH - encrypted ● Telnet - plaintext ● SSH and Telnet - used to connect devices over the network, both are used in-band. ● PuTTY and Terra Term - can be used to make both SSH AND Telnet connections. ● VLANs - a logical overlay network that groups together a subset of devices that share a physical LAN, isolating the traffic for each group. ● Show ip interface brief - command used to display a brief synopsis of the condition of the device interfaces. ● Ipconfig command - used to verify TCP/IP properties on a host. ● Ping - command used to verify layer 3 connectivity ● Traceroute command - is used to trace the network path of packets from source to destination ● Flow control - allows for this by ensuring that data is not sent too fast. ● EIA - organization standard related to electrical wiring, connectors, and the 19 inch racks used to mount networking equipment. ● IPv4 address - uniquely identifies an end device on the network ● Subnet mask - determines the network address portion and host portion for an IPv4 address ● Default gateway - the ip address of the router interface used for communicating with hosts in another network. ● DNS server - the IP address of the Domain Name System server. ● DHCP server - not configured manually on end devices. It will be provided by a DHCP server when an end device requests an IP address. ● Response timeout - if a computer makes a request and does not hear a response within an amount of time, the computer assumes that no answer is coming and reacts accordingly. ● HTTP - governs the way that a web server and client interact ● TCP - manages individual conversations between web servers and clients ● IP - is responsible for delivery across the best path to the destination ● Ethernet - takes the packet from IP and formats it for transmission ● MAC address - physical address in the data link layer ● IP address - logical address ● Network protocols - are implemented in hardware, or software, or both. They interact with each other within different layers of a protocol network. ● Protocol Types ○ Network Communications Protocols - enables one or more devices to communicate over one or more networks. Examples of protocols include: IP, Transmission Control Protocol (TCP), HyperText Transfer Protocol (HTTP), and many more. ○ Network Security Protocols - provides authentication, data integrity, and encryption. Examples include Secure Shell (SSH), Secure Sockets Layer (SSL), and Transport Layer Security (TLS). ○ Routing Protocols - enables routers to exchange routing and path information. Examples include Open Shortest Path First (OSPF) and Border Gateway Protocol (BGP). ○ Service Discovery Protocols - used for the automatic detection of devices or services. Examples of service discovery protocols include Dynamic Host Configuration Protocol (DHCP) which discovers services for IP address allocation, and Domain Name System (DNS) which is used to perform name-toIP address translation. ● Protocol Functions ○ Addressing - This identifies the sender and the receiver of the message. Addressing protocols include Ethernet, IPv4, IPv6. ○ Reliability - Provides guaranteed delivery mechanisms in case messages are lost or corrupted. TCP provides this function. ○ Flow control - maintains an efficient rate of flow of data between two communicating devices. TCP provides flow control services. ○ Sequencing - Uniquely labels each segment of data. This is useful if the data segments are lost, delayed or received out-of-order. TCP provides sequencing services. ○ Error detection - used to detect if data became corrupted during transmission. ○ Application interface - This function contains information used for process-toprocess communications between network applications. For example, when accessing a web page, HTTP or HTTPS protocols are used to communicate between the client and server web processes. Internet Standards Electronic and Communications Standards OSI Model Layer TCP/IP Model Layer ● An IP packet contains: ● ● ○ Source IP address ○ Destination IP address Bandwidth - capacity of a medium to carry data. Bandwidth quality is determined by: ● Latency - amount of time for data to travel from one given point to another. ● Throughput - the measure of transfer of bits across the media over a period of time. ○ Influenced by: amount of traffic, type of traffic, latency caused by intermediary network devices. ● Goodput - measure of usable data transferred over a period of time. ● Copper cabling: ○ Most common type of cabling ○ Easy to install ○ Inexpensive ○ Limited by distance and signal interference ● Types of copper cabling: ○ Unshielded Twisted-Pair (UTP) ■ Most common ■ Terminated with RJ-45 connectors ■ Consists of 4 pairs of color coded wires ■ Twisted pairs protect from signal interference (EMI, RFI, Crosstalk) ○ Shielded Twisted-Pair (STP) ■ More expensive than UTP ■ Better protection against signal interference using shielding techniques and special connectors ■ Braided or foil shield ○ Coaxial Cable ■ Copper conductor to transmit signals ■ Plastic insulation ■ Copper braid/Metallic foil shield ■ Attaches antennas to wireless devices ■ Can be bundles with fiber-optic wiring for two-way transmission ■ Terminates with BNC, N type and F type connectors T568A and T568B Standards Cable Types and Standards ● IEEE - oversees wireless lan standards MODULE 4 (canvas) ● An Ethernet mac address consists of 48-bit binary value expressed using 12 hexadecimal values ● ● ● ● ● ● Ethernet mac address is 6 bytes in length All MAC addresses are unique to the ethernet device/interface. All vendors that sell ethernet devices must register with the IEEE to obtain a unique 6 code identifier called the OUI. Address Resolution Protocol (ARP) - determines the destination mac address associated with an IPv6 address known as Neighbor Discovery (ND) Broadcast MAC address - FF-FF-FF-FF-FF-FF Ethernet is defined by data link layer and physical layer protocols Ethernet and the OSI Model ● ● MAC sublayer - responsible for data encapsulation and accessing media. Provides data link layer addressing and is integrated with various physical layer technologies. Examples of this sublayer are 802.3. 802.11, or 802.15 LLC sublayer - communicates between the networking software at the upper layers and the device hardware at the lower layers. It places information in the frame that identifies which network layer protocol is being used for the frame. This allows multiple Layer 3 protocols such as IPv4 and IPv6 to use the same network interface and media. ● IEEE 802.3 data encapsulation includes the following: ○ Ethernet frame - This is the internal structure of the Ethernet frame. ○ Ethernet Addressing - The Ethernet frame includes both a source and destination MAC address to deliver the Ethernet frame from Ethernet NIC to Ethernet NIC on the same LAN. ○ Ethernet Error detection - The Ethernet frame includes a frame check sequence (FCS) trailer used for error detection. Ethernet Frame ● ● Preamble and Start Frame Delimiter Fields ○ The Preamble (7 bytes) and Start Frame Delimiter or SFD (1 byte) fields are used for synchronization between the sending and receiving devices. ○ These first eight bytes of the frame are used to get the attention of the receiving nodes. ○ Essentially, the first few bytes tell the receivers to prepare to receive a new frame. Destination MAC Address Field ○ This 6-byte field is the identifier for the intended recipient. ○ ● ● ● ● ● ● ● This address is used by Layer 2 to assist devices in determining if a frame is addressed to them. ○ The address in the frame is compared to the MAC addresses in devices until there is a match. ○ Can be a unicast, multicast, or broadcast address. Source MAC Address Field ○ Identifies the originating NIC or interface of the frame. Type / Length ○ Identifies the upper layer protocol encapsulated in the Ethernet frame. ○ Common values are in hexadecimal, 0x800 for IPv4, 0x86DD for IPv6 and 0x806 for ARP ○ You may also see this field referred to as EtherType. Data Field ○ This field contains the encapsulated data from a higher layer, which is a generic IPv4 packet. ○ All frames must be at least 64 bytes long. ○ If a small packet is encapsulated, additional bits called a pad are used to increase the size of the frame to this minimum size. Frame CHeck Sequence ○ The FCS field is used to detect errors in a frame. ○ It uses a cyclic redundancy check (CRC) ○ The sending device includes the results of a CRC in the FCS field of the frame. ○ The receiving device receives the frame and generates a CRC to look for errors. IPv4 addresses - represented in decimal and binary IPv6 addresses - represented in hexadecimal Ethernet MAC address ○ is a 48-bit address expressed using 12 hexadecimal digits. ○ All vendors that sell Ethernet devices must register with the IEEE to obtain a unique 6 hexadecimal code called the Organizationally Unique Identifier (OUI) ○ A mac address must: ■ Use its assigned OUI as the first 6 hexadecimal digits ■ Assign a unique value in the last 6 hexadecimal digits Ethernet MAC address Types of switching Variants of cut-through switching: Memory buffering methods ● Two of the most basic settings on a switch ○ bandwidth/speed ○ Duplex ■ Duplex and bandwidth settings should match between devices ● ● Full duplex - both ends of the connection can send and receive simultaneously Half duplex - only one end of the connection can send at a time Example of duplex mismatch ● Auto-MDIX - a feature that detects ethernet cable type ● Minimum and Maximum size of an ethernet frame ○ 1518 bytes (Maximum) ○ 64 bytes (Minimum) Network Layer Protocols ● Addressing end devices ● ● ● ○ Must be configured with a unique IP address for identification on the network Encapsulation ○ The network layer encapsulates the protocol data unit (PDU) from the transport layer into a packet. ○ Adds IP header information ■ Source address ■ Destination address ○ Process performed by the source of the IP packet Routing ○ Service to direct the packets to a destination host on another network. ○ To travel to other networks, the packet must be processed by a router. ○ A packet may cross many routers before reaching the destination ○ Each router crossed before reaching the destination is called a “hop” De-encapsulation ○ When the packet arrives at the network layer of the destination host, the host checks the IP header of the packet. If the destination IP address within the header matches its own IP address, the IP header is removed from the packet. After the packet is de-encapsulated by the network layer, the resulting Layer 4 PDU is passed up to the appropriate service at the transport layer. The deencapsulation process is performed by the destination host of the IP packet.\ Basic characteristics of IP: Fields in the IPv4 packet header Limitations of IPv4 Improvements of IPv6 Fields that determine packet lifespan ● IPv4 ○ Time To Live (TTL) ● IPv6 ○ Hop Limit ● Both are the same, but use different names. The TTL/Hop Limit is reduced by one for each time a packet traverses a layer 3 device (switch or router) ● IPv4 and IPv6 address space comparison ○ IPv4 - 4 billion addresses ○ IPv6 - 340 undecillion addresses IPv6 packet header A host can send packets to: Whether a packet is destined for a local host or a remote host is determined by the source end device. The source end device determines whether the destination IP address is on the same network that the source device itself is on. The method of determination varies by IP version: ● Default gateway - is the network device (router or layer 3 switch) that can route traffic to other networks. If a network is a room, the default gateway is a door. A router can learn about remote networks in one of two ways: ● Manually (Static routing) - remote networks are manually entered into the route table using static routes. ○ Route entries that are manually configured ○ The static route includes the remote network address and the IP address of the next hop router. ○ If there is a change in the network topology, the static route is not automatically updated and must be manually reconfigured. ○ Static routes are appropriate for small networks with few or no redundant links. ● Dynamically (Dynamic routing) - automatically learned using a dynamic routing protocol ○ Automatically share routing information with other routers ○ Compensates for any changes in the network topology. ○ Protocols include OSPF, and Enhanced Interior Gateway Routing Protocol (EIGRP). ○ More Routing table acronyms via Show IP route: 1. 2. 3. 4. 5. 6. 7. 8. 9. LLC - Logical Link Control MAC - Media Access Control IP - Internet Protocol OSI - Open Systems Interconnection FCS - Frame Check Sequence ARP - Address Resolution Protocol PDU - Protocol Data Unit TCP - Transmission Control Protocol SLAAC - Stateless Address Auto-Configuration 10. AUTO-MDIX - Media Dependent Interface 11. MTU - Maximum Transmission Unit 12. CSMA/CD - Carrier Sense Multiple Access/Collision Detection 13. CRC - Cyclic Redundancy Check 14. OUI - Organizationally Unique Identifier 15. TTL - Time To Live 16. CAM - Content Addressable Memory