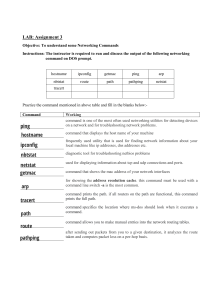
Practical Assignment Nakul Gehlaut 20BAI10019 CSE3006 Q1. Study of basic network command and Network configuration commands. Describes the following some basic networking commands of Linux and Windows based OS with their operations: • Ifconfig: Linux ifconfig stands for interface configurator. It is one of the most basic commands used in network inspection. ifconfig is used to initialize an interface, configure it with an IP address, and enable or disable it. It is also used to display the route and the network interface. Basic information displayed upon using ifconfig are: 1. IP address 2. MAC address 3. MTU(Maximum Transmission Unit) Syntax: ifconfig eth0 <address> netmask <address> • To enable or disable an interface ifconfig can be used to enable or disable an interface. • Ping Linux ping is one of the most used network troubleshooting commands. It basically checks for the network connectivity between two nodes. ping stands for Packet INternet Groper. The ping command sends the ICMP echo request to check the network connectivity. It keeps executing until it is interrupted. Use Ctrl+C Key to interrupt the execution. Syntax: ping <destination> • traceroute Linux traceroute is one of the most useful commands in networking. It is used to troubleshoot the network. It detects the delay and determines the pathway to your target. It basically helps in the following ways: 1. It provides the names and identifies every device on the path. 2. It follows the route to the destination 3. It determines where the network latency comes from and reports it. traceroute <destination> If you don't have the traceroute service installed in your system, you can install it using the following command: sudo apt-get install inetutils-traceroute • Netstat Linux netstat command refers to the network statistics. It provides statistical figures about different interfaces which include open sockets, routing tables, and connection information. Syntax: netstat Output: Observe the output displaying all the open sockets. Variations in netstat command Below are few variations of the netstat command used. 1) To display the programs Syntax: netstat -p This displays the programs associated with the open socket. 2) To get the details of the ports Syntax: netstat -s This gives detailed statistics of all the ports. • nslookup Linux nslookup is also a command used for DNS related queries. It is the older version of dig. Syntax: nslookup <domainName> Example: nslookup mindmajix.com Output: As we see in the output above, it displays the record information relating to mindmajix.com • route Linux route command displays and manipulates the routing table existing for your system. A router is basically used to find the best way to send the packets across to a destination. Syntax: route • host Linux host command displays the domain name for a given IP address and IP address for a given hostname. It is also used to fetch DNS lookup for DNS related query. Example: host mindmajix.com host 149.77.21.18 You can combine the host command with -t, and get DNS resource records like SOA, NS, A, PTR, CNAME, MX, SRV. Syntax: host -t <resourceName> • hostname Linux hostname is the simple command used to view and set the hostname of a system. Syntax: hostname Output: To set the hostname Use the syntax below to set the hostname. Syntax: sudo hostname <newName> The hostname set through this command is not permanent. It will be reset to the name in the hostname file back when the system reboots. • telnet In Linux, the telnet command is used to create a remote connection with a system over a TCP/IP network. It allows us to administrate other systems by the terminal. We can run a program to conduct administration. It uses a TELNET protocol. However, this protocol has some security defects, but it is one of the most used networking protocols due to its simplicity. It is not a secure protocol because it transfers data in unencrypted form. Often Linux user prefers ssh over telnet because ssh transfers data in encrypted form. This utility is similar to the Remote Desktop feature in Windows. The syntax for the telnet is as Follows: telnet hostname/IP address • Ssh The ssh command provides a secure encrypted connection between two hosts over an insecure network. This connection can also be used for terminal access, file transfers, and for tunneling other applications. Graphical X11 applications can also be run securely over SSH from a remote location. Q2. Study of network IP addressing [Both Classful & Classless]. Discuss the Implementing an IP Addressing Scheme. Classless Addressing • Classless Addressing is an improved IP Addressing system. • It makes the allocation of IP Addresses more efficient. • It replaces the older classful addressing system based on classes. • It is also known as Classless Inter Domain Routing (CIDR). CIDR Block When a user asks for specific number of IP Addresses, • CIDR dynamically assigns a block of IP Addresses based on certain rules. • This block contains the required number of IP Addresses as demanded by the user. • This block of IP Addresses is called as a CIDR block. Rules For Creating CIDR Block A CIDR block is created based on the following 3 rules- Rule-01: • All the IP Addresses in the CIDR block must be contiguous. Rule-02: • The size of the block must be presentable as power of 2. • Size of the block is the total number of IP Addresses contained in the block. • Size of any CIDR block will always be in the form 21, 22, 23, 24, 25 and so on. Rule-03: • First IP Address of the block must be divisible by the size of the block. Classful Addressing The 32 bit IP address is divided into five sub-classes. These are: • Class A • Class B • Class C • Class D • Class E Each of these classes has a valid range of IP addresses. Classes D and E are reserved for multicast and experimental purposes respectively. The order of bits in the first octet determine the classes of IP address. IPv4 address is divided into two parts: • Network ID • Host ID The class of IP address is used to determine the bits used for network ID and host ID and the number of total networks and hosts possible in that particular class. Each ISP or network administrator assigns IP address to each device that is connected to its network. Rules for assigning Host ID: Host ID’s are used to identify a host within a network. The host ID are assigned based on the following rules: • Within any network, the host ID must be unique to that network. • Host ID in which all bits are set to 0 cannot be assigned because this host ID is used to represent the network ID of the IP address. • Host ID in which all bits are set to 1 cannot be assigned because this host ID is reserved as a broadcast address to send packets to all the hosts present on that particular network. Rules for assigning Network ID: Hosts that are located on the same physical network are identified by the network ID, as all host on the same physical network is assigned the same network ID. The network ID is assigned based on the following rules: • The network ID cannot start with 127 because 127 belongs to class A address and is reserved for internal loop-back functions. • All bits of network ID set to 1 are reserved for use as an IP broadcast address and therefore, cannot be used. • All bits of network ID set to 0 are used to denote a specific host on the local network and are not routed and therefore, aren’t used. Q3. Examining Network Address Translation (NAT) and differentiatebetween Static and Dynamic Routing. To access the Internet, one public IP address is needed, but we can use a private IP address in our private network. The idea of NAT is to allow multiple devices to access the Internet through a single public address. To achieve this, the translation of a private IP address to a public IP address is required. Network Address Translation (NAT) is a process in which one or more local IP address is translated into one or more Global IP address and vice versa in order to provide Internet access to the local hosts. Also, it does the translation of port numbers i.e. masks the port number of the host with another port number, in the packet that will be routed to the destination. It then makes the corresponding entries of IP address and port number in the NAT table. NAT generally operates on a router or firewall. Network Address Translation (NAT) working: Generally, the border router is configured for NAT i.e the router which has one interface in the local (inside) network and one interface in the global (outside) network. When a packet traverse outside the local (inside) network, then NAT converts that local (private) IP address to a global (public) IP address. When a packet enters the local network, the global (public) IP address is converted to a local (private) IP address. If NAT runs out of addresses, i.e., no address is left in the pool configured then the packets will be dropped and an Internet Control Message Protocol (ICMP) host unreachable packet to the destination is sent. Q4. Build a Peer-to-Peer Network using CISCO packet tracer [software tool]: Objective • Create a simple peer-to-peer network between two PCs • Identify the proper cable to connect the two PCs • Configure workstation IP address information • Test connectivity using the ping command. ➔ peer-to-peer network between two PCs ➔ Configure workstation IP address information ➔ Test connectivity using the ping command Q5. Build a Hub-based Network using CISCO packet tracer [software tool]: Objective • Create a simple network with two PCs using a hub • Identify the proper cable to connect the PCs to the hub • Configure workstation IP address information • Test connectivity using the ping command ➔ simple network with multiple PCs using a hub ➔ Configure workstation IP address information ➔ Test connectivity using the ping command Q6. Build a Switch-based Network using CISCO packet tracer [software tool]: Objective • Create a simple network with two PCs using a switch • Identify the proper cable to connect the PCs to the switch • Configure workstation IP address information • Test connectivity using the ping command ➔ A simple network with two PCs using a switch ➔ Configure workstation IP address information ➔ Test connectivity using the ping command Q8. Determine the host and network portion of the IP address. With the following IP host addresses, indicate the following: • Class of each address • Network address or ID • Host portion • Broadcast address for this network • Default subnet mask Host IP Address Addr. Class 216.14.55.137 C A B C B 123.1.1.15 150.127.221.244 194.125.35.199 175.12.239.244 Network Address Host Address Network Default Broadcast Subnet Mask Address 216.14.55.0 137 216.14.55.255 255.255.255.0 123.0.0.0 1.1.15 123.255.255.255 255.0.0.0 150.127.0.0 221.244 150.127.255.255 255.255.0.0 194.125.35.0 199 194.125.35.255 255.255.255.0 175.12.0.0 239.244 175.12.255.255 255.255.0.0 Q9. Given an IP address of 142.226.0.15 and a subnet mask of 55.255.255.0, answer the following questions: a. What is the binary equivalent of the second octet? Ans. 11100010 b. What is the Class of the address? Ans. Class B c. What is the network address of this IP address? Ans. 142.226.0.0 (First two octets followed by zeros) d. Is this a valid IP host address? Ans. Yes e. Why or why not? Ans. The network part of the address (the first 2 octets or 16 bits) is 142.226 which is a valid class B address. The host part (last 2 octets or 16 bits) is 0.15 or 00000000.00001111. Since all 16 bits of the host ID are not all zeros or all ones it is a valid host address. Q10. What are the essential steps to successfully configure a LAN and a WAN in your system, if your system does not have any desired software, hardware, and protocol installations? Create Network 1. Identify the local services that you want available on the network. Identify network-attached printers, network disk drives, any server that will share printers or disks. 2. Identify how many devices will have to connect to the network. Each device, server or workstation will require a unique address. 3. Run cables to workstations where possible. A wired LAN will always get better performance and be more secure than a wireless LAN. Wherever possible, run a cable to servers, printers, IP phones or work locations. Run a cable to any area where you are likely to work. Use standard Ethernet cables or building wiring as installed according to the TIA-568 standard. 4. Select and purchase a switch or cable router. The simple secure way to connect to the Internet is to use a cable router. Many makes and models are available. If the model you choose does not have enough ports to connect all of your computers, then you will need to purchase a switch as well. 5. Configure the WAN port of the cable router. Configuration details will vary from vendor to vendor. Key information you will need to configure the WAN port will be supplied by your internet service provider. 6. Configure the LAN ports of your cable router. Most cable routers will act as a Dynamic Host Configuration Server, or DHCP server. This means that the router will give addresses to workstations automatically. Be certain that the address pool has enough addresses for all of the workstations. Make certain that there are enough addresses outside of the range for any hosts that need static addresses. For example, a network address with a mask of 255.255.255.0 has a total of 254 hosts. If the dynamic pool has 200 addresses available, that means the remaining 54 addresses are available to give printers or servers static addresses. 7. Connect the wires for the network. Workstations and servers can be connected with standard Ethernet cables. Connect the switch to the cable router LAN ports by using the up-link or straight port on the switch. If the switch does not have an uplink port, connect any standard port of the switch to a LAN port on the cable router with an Ethernet crossover cable. Ethernet rossover cables can be purchased at any electronics store. 8. Test the services and Internet connectivity. Test each of the workstations to ensure they can connect to the Internet and test any local servers and printers. Print test pages on the shared printers. Tests read and write permissions on shared file servers by copying files to the servers and copying files from the server to a workstation.