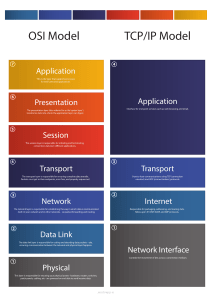
UNIVERSITY OF THE EAST Manila COLLEGE OF COMPUTER STUDIES AND SYSTEMS CCS 3103: Data Communication and Computer Networks Name: Section: Eftekharian Jahromi Nahyan M. CCS_3103 Question: How Activity Number: Activity Name: Activity 1 M2 does the TCP/IP model work? include examples Answer: The TCP/IP model, also known as the Internet Protocol Suite, is a conceptual framework used for understanding the protocols and networking technologies that enable communication over the Internet. It consists of four layers: Application, Transport, Internet, and Link. • Application Layer: This is the topmost layer that deals with user interactions and application-level protocols. It encompasses various protocols such as HTTP, SMTP, FTP, and DNS. These protocols facilitate communication between software applications and enable services like web browsing, email, and file transfer. For example, when you access a website using a web browser, the browser uses the HTTP protocol to request and receive web pages. • Transport Layer: This layer is responsible for end-to-end communication and data flow control. The most prominent protocol in this layer is the Transmission Control Protocol (TCP), which ensures reliable and ordered delivery of data between two devices. Another protocol, User Datagram Protocol (UDP), offers faster but less reliable communication. For example, when you're downloading a file using a BitTorrent client, the transport layer ensures that the file chunks arrive correctly and in the right order. • Internet Layer: This layer is responsible for addressing and routing packets across different networks. The Internet Protocol (IP) is the core protocol here, which assigns unique IP addresses to devices and ensures proper routing of data packets. When you send an email to a friend across the world, the internet layer ensures that the data is routed through various routers to reach its destination. • Link Layer: This layer deals with physical connections and data framing within a local network. It includes protocols like Ethernet, Wi-Fi, and PPP. These protocols define how data is formatted for transmission over the physical medium. For instance, when you're connected to a Wi-Fi network and sending a message, the link layer manages the conversion of data into frames suitable for wireless transmission. Question: How does the OSI model work? include examples Answer: The OSI (Open Systems Interconnection) model is another conceptual framework that serves as a guideline for designing and understanding network architectures. It comprises seven layers: • Physical Layer: This is the lowest layer, dealing with physical connections and electrical signals. It defines how data is transmitted over various physical media like cables and wireless signals. For example, Ethernet cables and fiber optics are part of this layer. • Data Link Layer: This layer ensures error-free transmission over the physical layer. It's divided into two sublayers: Logical Link Control (LLC) and Media Access Control (MAC). MAC addresses, which uniquely identify devices on a network, operate at this layer. An example is the Ethernet protocol. • Network Layer: Responsible for logical addressing, routing, and forwarding of data packets. The Internet Protocol (IP) operates here, assigning IP addresses and facilitating routing decisions. Routers work at this layer to direct traffic between different networks. • Transport Layer: Similar to the TCP/IP model, this layer manages end-to-end communication and data flow control. Protocols like TCP and UDP reside here, ensuring reliable or fast data delivery based on the application's needs. • Session Layer: This layer establishes, maintains, and terminates connections between applications. It manages sessions, allowing data exchange in full-duplex or half-duplex modes. Remote Procedure Call (RPC) is an example of a session-layer protocol. • Presentation Layer: Responsible for data translation, encryption, and compression. It ensures that data from the application layer of one system is presented in a format understandable by the application layer of another. Secure Sockets Layer (SSL) operates at this layer, providing encryption for web communication. • Application Layer: This top layer deals directly with user applications and network services. It houses protocols that provide specific services, such as HTTP for web browsing, SMTP for email, and FTP for file transfer.