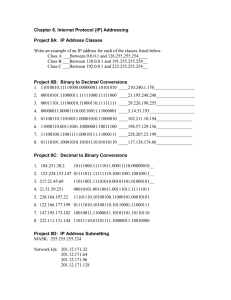
JMJ Marist Brothers College of Engineering and Technology NOTRE DAME OF MARBEL UNIVERSITY City of Koronadal, South Cotabato Laboratory Activity Subnetting by Number of Host _________________________________ COMPUTER NETWORK AND SECURITY LABORATORY CPEPC 122 – CPE3 ________________________________ BY: Adrean Rey Tiu Huan LAB DATE: April 24, 2023 DUE DATE: April 24, 2023 JMJ Marist Brothers College of Engineering and Technology NOTRE DAME OF MARBEL UNIVERSITY City of Koronadal, South Cotabato ABSTRACT The objective of the laboratory activity “Subnetting by Number of Host” was to solve the number of subnets using the number of Host. And assign the ip’s to the computers. And lastly to design the network using cisco packet tracer. INTRODUCTION Every computer needs and IP addresses because it helps make it easier to identify the hardware that is connected to your network. It is necessary to arrange the IP addresses logically in order to find a certain device. When it comes to maintaining network efficiency, subnetting really excels. A network may include hundreds of thousands of connected devices, and the traffic flow may be complicated by the IP addresses that match them. Subnetting limits the number of devices that can use an IP address. This gives an engineer the ability to create subnetworks using subnetting, which organizes data so that it may travel without having to touch every part of the more complicated routers. To accomplish this, an engineer must match each IP address class to a subnet mask. Similar to an IP address, a subnet mask is only applicable to internal networks. This mask makes it easier to distinguish between the portions of an IP address that correspond to the network and the portions that pertain to the host, enabling some data to be delivered over particular routes depending on its destination. A subnet mask is the instrument that allows a router to match an IP address to a certain JMJ Marist Brothers College of Engineering and Technology NOTRE DAME OF MARBEL UNIVERSITY City of Koronadal, South Cotabato subnetwork. The purpose of subnetting is to establish a computer network that is quick, efficient, and robust. PROCEDURE I use Cisco Packer tracer software to this activity and copy the design provided by the lab report as shown on the picture. The problem is to assign IP address on each device to do that I solve using the formula thought to us. JMJ Marist Brothers College of Engineering and Technology NOTRE DAME OF MARBEL UNIVERSITY City of Koronadal, South Cotabato DATA/OBSERVATIONS Network Device Specific IP Address Subnet #6 Router Interface 192.168.15.1 PC#1 192.168.15.2 PC#2 192.168.15.246 Router Interface 172.18.252.1 PC#1 172.18.252.2 PC#2 172.18.252.253 Router Interface 192.168.100.1 PC#1 192.168.100.126 PC#2 192.168.100.2 Router Interface 172.16.128.1 PC#1 172.16.128.2 PC#2 172.16.128.252 Router Interface 10.123.240.1 PC#1 10.123.240.2 PC#2 10.123.240.252 Router Interface 192.168.200.1 PC#1 192.168.200.2 PC#2 192.168.200.238 Subnet #1000 Subnet #120 Subnet #500 Subnet #300 Subnet # 15 JMJ Marist Brothers College of Engineering and Technology NOTRE DAME OF MARBEL UNIVERSITY City of Koronadal, South Cotabato Finished worked This table shows the first valid address, the last valid address, network address and broadcast address, this was used on the devices on the cisco packet tracer. CONCLUSION Therefore I conclude we can get the number of subnets using the number of Host given by simply applying it to the formula 2^m-2 where n is the number of host and minus two for the broadcast and network address. With the results it helps us identify the valid ip’s, network address and broadcast address. I learned that the number of JMJ Marist Brothers College of Engineering and Technology NOTRE DAME OF MARBEL UNIVERSITY City of Koronadal, South Cotabato network plays a major role in subnetting this allows you to solve the number of subnets. And the number of networks are the masked bits of the subnet mask. The activity requires us to think critically about how to correctly enter the addresses and ping them to other PCs. REFERENCES https://www.simplilearn.com/tutorials/cyber-security-tutorial/what-is-sub-netting https://www.fieldengineer.com/skills/subnetting