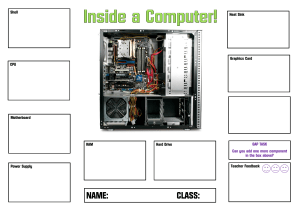
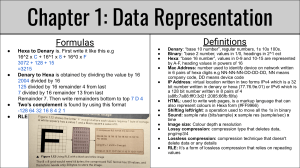
Year 9.1 Knowledge Organiser E-safety Identity Theft: Crime stealing someone’s identity and impersonating them It is illegal and could cause distress to someone Social Engineering and Phishing: Tricking someone into giving away their personal details. Phishing is done over an email Digital Footprint: The trail of data you create when online visiting websites Central Processing Unit (CPU) Is used for processing data (the brains of the computer) Control Unit (CU) Controls and monitors the hardware attached to the system Arithmetic Logic Unit (ALU) Carries out the arithmetic and logical operations Instructions will be fetched, decoded, then executed Memory Random Access Memory (RAM): ➢ Temporary Memory ➢ Volatile – needs power to retain memory ➢ Stores the programs and data that is currently in use Logic Gates Computer Science Department Binary (Base 2) 128-64-32-16-8-4-2-1 0 0 1 1 1011 = 8+0+2+1= 11 2 2 Hex Base 16 3 3 Read Only Memory (ROM): ➢ Non Volatile – does not need power to retain memory ➢ Tells the computer how to start Virtual Memory: ➢ When the RAM is full ➢ Secondary storage is used as temporary RAM ➢ Data is moved to VM and back to RAM when needed Networks Two or more computers connected together to share resources Topology: The arrangement of a network AF A F 4 4 10 15 5 5 1010 1111 6 6 7 7 8 8 9 9 10101111 Database: Table: Collection of related data held in a structured format Little Man Computer (LMC) CPU Simulator *peterhigginson.co.uk/LMC A 10 Query: Ask your database a question B 11 Report: Displaying the results of your queries D 13 Structured Query Language (SQL): Manipulating a database C ADD INP DAT SUB OUT BRZ Sound Representation Sound is stored in binary Sample rate - the number of audio samples captured every second Bit depth - the number of bits available for each clip Bit rate - the number of bits used per second of audio STA BRP BRA LDA HLT 12 E 14 F 15