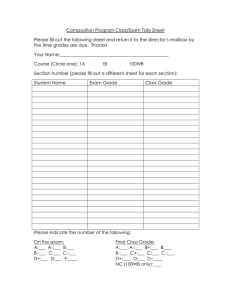
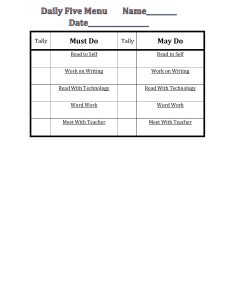
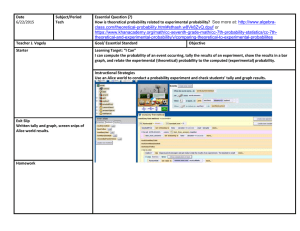
Download From http http://caknowledge.in/ S. No 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 Mo 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 314 315 316 317 318 319 320 321 322 323 324 325 326 327 328 329 330 331 332 333 334 335 336 337 338 339 340 341 342 343 344 345 346 347 348 349 350 351 352 353 354 355 356 357 358 359 360 361 362 363 364 365 366 367 368 369 370 371 372 373 374 375 376 377 378 379 380 381 382 383 384 385 386 387 388 389 390 391 392 393 394 395 396 397 398 399 400 401 402 403 404 405 406 407 408 409 410 411 412 413 414 415 416 417 418 419 420 421 422 423 424 425 426 427 428 429 430 431 432 433 434 435 436 437 438 439 440 441 442 443 444 445 446 Download From http http://caknowledge.in/ More Q Questions In IDEA, Statistics functions can be applied on_________. In IDEA, increment value in Stratification function can be fixed or free interval. In IDEA, Stratified Random functions is a part of which menu. Which of the following is not an Audit Software Using which functions to perform more complex calculations and exception testing in IDEA? Which of the following are categories of computer audit function ? In the following list which is a audit function? Which is the following step involved in a source code review methodology ? In IDEA which functions should be used to find repeated values ? In IDEA, Stratification functions can be applied on which type of data ? In IDEA,Summarization accumulates the values of Numeric fields for each____________. In which sampling,selecting sampling units using a fixed interval between selections is_________ Ensures that all combinations of sampling units in the population have an equal chance of selectio is____________. Input Control method is a part of Application Control Group. Which is the following type of check that can be run when data is input through terminal ? In _______system money transfers are done on a one to one basis while in _______system transfe in batches. All the money transfers take place in the books of the _________________ ________system of money transfer is primarily used for large transactions. In RTGS, the STP generates an ___________for every outbound RTGS transaction. STP stands for ________________________________ in terms of CBS. ________ is a method of creating virtual networks within a physical network. CMS stands for ______________________________ in terms of CBS. Which of the following statements is true? The Management Controls does not include ___________ _______is supported by advanced technology infrastructure and has high standards of business functionality. CBS Software resides in a Central application server which is located in the ___________ A________ that runs the core banking solutions (CBS) and is centrally accessed by the branches The _________of the application is capable of only entering the data at the end point that is branc The application server would be placed in a trusted inside zone in a separate ____________ Application software would access the ________ __________ are capable of being connected only when devices are connected to a switch. _____________refers to the process of developing software which would produce the required ou from the input provided of course, using the necessary hardware and communication systems. The______________is essential to ensure that computer security records are stored in sufficient d appropriate period of time. All the various servers in the central data centre are seggregated through _______ The __________ is a complete process in the computer so that it ensures that data that is fed in co to certain prerequisite conditions. When the central Data base is busy with central end of day activities or for any other reason, the f containing the account balance of the customer is sent to the ATM switch. Such a file is called ___ The IBDS is located in a ____________ The main components of Internet Banking system consist of __________ Copy of the Anti Virus Software was updated promptly and regularly at the Data Centre and push all of the servers and in all the systems in the branches by ________ The __________which is also residing in the server at the branch actually does the banking opera In Core Banking concept all the systems of the bank are connected to the Central office by means connectivity which may be either a _________ or a dial up line. The ________ is generated by the software and directly sent to equipment for printed the Pin Mai ____________would also include the existence of built in controls in the system to ensure proper processing of input data so as to provide the required output. ____________refers to an arrangement wherein the issuing bank acts on the request and instructi customer. _______________ is a process by which the bank ensures the maintenance and recovery of opera At which phase of testing the version of software is called “ beta version”? Finacle developed by _________ The number that is stored in the ATM switch is the difference of which of the following number? The information retrieval of transactions taking place at ATM located at remote locations is throu _________ The number that is generated as soon as the customer inserts the card in the ATM machine is ____ The tab in Expression Builder in which we write expressions is known as _____________. The criteria expression LIKE?B*. __________ queries are useful for summarizing information, and are somewhat similar to pivot ta MS-Excel. While entering record in Datasheet view, in which order the records can be entered When you delete the record in form, it deletes the record from__________. Having clause is used in the aggregate query in MS Access 2010 The controls that are not linked to any field of the table or query on the form are known as _____ Which property of the form can be used to insert a background image in MS Access 2010? ___________ is a report that is inserted in another report in MS Access 2010. A bound main report is based on a ______________ and its _____________ contain realted infor DDL stands for ____________ A___________used to compare multiple values of categories or differences over a period of time A________used to compare trends over a period of time. To create a read-only copy of the database, which of the following file format can be used? The database administrator created a split database and created a front-end database and back-end file.Which of the file should be stored on the server ? In which formats can the Collect Data through email message feature can send the data entry form Once a mail is sent using the collect data through email message feature in Access 2010. The mai can be checked using________________. The ___________ type of data cannot be collected using Collect data through email messages. What is the memo data type field used for? The filter By selection feature allows you to filter: DML stands for _____________ Which editor was provided for use with Access Basic? How do you update Pivot Table report data after changes are made to the source data? What are the different views to display a Table ? Which Of The Following Creates A Drop Down List Of Values To Choose From? A __________ Enables You To View Data From A Table Based On A Specific Criterion The Database Language That Allows You To Access Or Maintain Data In A Database DCL Provides Commands To Perform Actions Like Which is not a Database Model ? Which Of The Field Has Width 8 Bytes? This Is The Stage In Database Design Where One Gathers And List All The Necessary Fields For Database Project. Whenever a tables gets update, the dependent query will The Third Stage In Designing A Database Is When We Analyze Our Tables More Closely And Cre ___________ Between Tables What is the purpose of the Switchboard Manager in Microsoft Access 2010? How does a query-based report differ in design to a report based on just one table? How would you include some plain text into a mailing label report? In a Microsoft Access 2010 report, the page numbering would most likely be placed into the: If you wished to present a professionally looking form on screen that would show all the necessar information, which of the following form design tools would you most likely use? An .ACCDE file is a ___________ version of the original .ACCDB file. Which type of the query is used to accept the value from the user while executing the query and f records accordingly To encrypt the databse in Access 2010 must be opened in the __________________. To extract the records based on date field, which of the symbol should be used FIX() is a kind of ____ function in MS-Access 2010. MS-Access 2010 has added new features of ______ to eliminate the need of VBA code Encrypting a database does not restrict access to database objects, but to __________ the database Third Party Encryption Technology can also be applied to the database of Microsoft Access 2010. To create a split database in MS Access 2010 go to which tab? After spliting database,frontend database holds_________________. After spliting database,backend database holds_________________. When an Access database is split, it creates two files_________________. A Data Access Page is a special type of _________ that allows users to interface with database us Internet Explorer. OLAP systems use concept of OLAP cube called a ______________ cube The data which is to be exported from Tally.ERP 9 can be in ________ format. In Tally ERP-9 Remote Access is also known as __________. Accessing data store on a remote location using Internet in Tally.ERP9 is called____________. Tally.ERP9 can be classified user in two categories are___________. Which of the following is not a predefined security level provided by Tally.ERP 9? The business model is represented in the graphical form using ______________ and __________ _______ integrates supply and demand mangement within and across companies. OLAP stands for _________________. __________ includes transportation from Suppliers and receiving inventory. Which of the following is not the service area of SCM? Which step of the ERP implementation involves, educating and recruiting end users throughtout t implementation process? The system ____________ process will address issues such as software configuration, hardware acquisition and software testing. A __________________ review is recommended to ensure that all business objectives established the planning phase are achieved. In _________________ stages, auditors have access to rudimentary ERP tools and capabilities fo security configurations. Immediate posting and updation of books of accounts as soon as the transactions are entered. Thi called as __________ Which of the following ETDS forms are available in Tally.ERP 9? The exported eTDS file from Tally.ERP 9 can be validated through NSDL's freely downloadable called __________________ ERP systems provide an access to the__________ data ________________ is a tool that refers to skills, processes, technologies, applications and practic to facilitate better, accurate and quicker decision making. Business intelligence systems are ________ Decision Support Systems. Data warehousing technology is the process of creating and utilizing the company’s __________ The data in the Warehouse comes from the _________ environment and external sources. In essence, SCM integrates ___________ management within and across companies. _____________ including all fulfillment activities, warehousing and transportation to customers. Customer Relationship Management is a ________________ level strategy. Operational CRM provides support to ___________ business processes. Collaborative ______ ultimate goal is to use information collected by all departments to improve quality of services provided by the company. Tally.ERP 9 follows the DES __________ method to safeguard the data. Immediate posting and updation of books of accounts as soon as the transactions are entered. Thi called as __________ Business Intelligence Systems are data-driven ___________________. Which of the following ETDS forms are available in Tally.ERP 9? The exported eTDS file from Tally.ERP 9 can be validated through NSDL's freely downloadable called __________________ With ______________ technology the characters are reduced in breadth and user is allowed to inp additional characters which would make the account name, entity complete and readable. In Tally.ERP 9 __________________ provides the user with administrator rights and the capabili check the entries made by the authorised users and alter these entries, if necessary. __________________ is an enabling framework which establishes a connection through which th user can access the Client's data without copying/transferring the data. If we want the company to be connected automatically for remote access on load, the property __________ needs to be set it as Yes. ___________________ technology is the process of creating and utilizing the company's historic Is there a fixed qualification for internal auditor_________. Which of the following will not appear in the home page of K-Doc? To change an email header so that the message appears to have originated from someone or some other than the actual source is known as___________. To playfully satirize a website is known as_____________. _________is the complete package to manage the billing requirements of a CA firm on cash syste accounting. Which of the following is not a/an feature of eSecretary? Annual return preparation can be done using ________. ________is correspondence automation & management software that is seamlessly integrated wit Microsoft Office. ________ is an independent,objective assurance and consulting activity designed to add value and an organization's operations. Which of the following is/are the main purpose of the internal audit? As per _____________of the Income tax Act,every person carrying on business or profession is r get his accounts audited by a CA before the "specified date". __________________ refers to use software/applications to automatically perform tasks such as accounting,preparing trial balance, financial statements etc. and electronically transmit data or inf using internet.. FEMA Stands for _______________. Which application helps the management to allocate the revenue to the credit of the right employe identified the opportunity? Who has full privileges in the financial accounting application? _________is the centre point of the financial accounting application as any transactions having fi impact carried out in any other module will reflect in this module. In Financial Accounting Application,the transactions flow from GL (General ledger) to other mod Which of the functionalities is not provided in the purchasing module of Financial Accounting Application. In Financial Accounting Application,automatic sequence number of documents control is not requ which of the following module? Which module of Financial Accounting Application can be used for assigning credit limit to cust Which of these will trigger/alert for timely payment ? We can manage interviews,offers and job vacancies by using which of the application? ________,___________,__________ are commonly referred to as CIA in information security pa ___________provides information about updation of project cost based on time spent by employe various projects. Which of the follwing is not a/an functionality provided by PMS? ___________automates the calculation of salary for taking inputs from the timesheet application, from Leave Management System and salary details from the HR master data. Which of the follwing is not a control in Leave Management System? Permanent Audit File are obtained once but updated on __________basis. In Permanent Audit file, _______ is not the key data documented. ________is a type of training in which user logon on the training server with a user ID and passw In some cases, trainee is supposed to appear for the examination/test at the end of the training is____________. ________ are the hardware/infrastructure equipments used in a CA firm. _____________means information available in the organization should not be altered or modified unauthorized personnel. Which of these is/are the standard email program used in an organization? Which of the following is not a characteristics of WAN? _________is protection of information assets from threats to preserve their value. Which types of information assets need to be secured in a CA Office? The extent and level of _________ would depend on the nature of information. __________ of information might be affected due to denial of service attack or some other reason __________means the sender cannot deny having sent a message and receiver cannot deny receiv message. Risk may not be _______ in nature. The process of identifying an individual, usually based on user id and password in an organization called______________. Which of the following is not a software equipment required in a CA's office? Which of the following is not an application arranged by ICAI? PBX stands for ________ ________ is the process of meeting the financial goals through the proper management of finance ___________ can be defined as the process of setting the procedures in the organization for achie predefined goals. ________ shows ability of company to pay back long term loans along with interest or other char generation of profit from its operations. _____________________is the simplest method of comparing different stocks at a point of time t investment decisions. The very first line of code of XML file is_____________. Every bit of data has to start and end with an identical tag Deletion of XML Map is done through __________. Excel works primarily with ________ types of XML files. Method of tax calculations shall change according to _________. ________ is a process used in statistical analysis in which a predetermined number of observation taken from a larger population. In __________, Individuals are selected at regular intervals from a list of the whole population. In ______________ each individual is chosen entirely by chance and each member of the popula an equal chance, or probability, of being selected. Which method is commonly used in social sciences when investigating hard to reach groups? __________ are useful for quick reading and easy understanding, particularly for top managemen Popular methods of capital budgeting include _________ and payback period. _________ is the value of all future cash inflows less future cash outflows as on today. ___________is the process of defining and analyzing the dangers to individuals, businesses and government agencies posed by potential natural and human-caused adverse events. __________ which is used more often, does not involve numerical probabilities or predictions of ________ are generally used to present information in a simple and better way and also be used to the risk in a better way. It is a technique used to determine how different values of an independent variable will impact a p dependent variable under a given set of assumptions. _______ involves computing different reinvestment rates for expected returns that are reinvested the investment horizon. Which function that is used to calculate the payment for specific loan terms ____________ ________helps to break down the Return on Equity _______ is a common method for financing property, facilities, and equipment. Which option can be used to split windows into four in ms excel 2010? How to restrict the values of a cell so that only a list can be entered in a cell? What does the COUNTA() function do in MS Excel 2010 ? If the value in A1 is "ITT" and in B1 is "ICAI ", which function in Excel will return " ITT @ ICA C1? Which of the following function will return a value of 7? A tiny chart embedded in a worksheet cell that provides a visual representation of data is a _____ _________is a graphical equivalent of a pivot table, which is used to visualise PivotTable report s data To frequently print a specific range of cells on a worksheet , the option used is Non-excel files can be opened in MS Excel using the _____is a text concatenation operator. Which of the following is correct? ___ function in MS-Excel returns the remainder after number is divided by divisor. EXCEL Work in ________ Mode In Ms-Excel 2010, ______ is Last Column Name? In Excel 2010, the default criteria setting for AutoFilter in each field is __________. Subtotal option is in __________ group of Data tab in Excel 2010. Which of the following cannot store connection information of an external data source in Excel 2 The default pivot chart type in Excel 2010 is a ________ chart. To consolidate Excel data, ________________________ is used when worksheet data does not ha consistent layout or pattern. In Excel 2010, the __________ function is used to generate a forecast. ______function calculates the payment for a loan (installment) based on constant payments and a interest rate. __________ are easy-to-use filtering components that enable the user to quickly filter the data in PivotTable report in MS-Excel 2010. In Excel 2010, range C3:C6 indicates _______________. Keyboard shortcut to show a shortcut menu in MS Excel 2010 is _______________. To select multiple non-adjacent cells in an Excel 2010 worksheet, click them holding _________ A quick way to return to a specific area of a worksheet in Excel 2010 is to type the cell address or name in the ____________. In MS-Excel 2010, the Name Box shows the ________________________. In Excel 2010, what is represented by the small black square in the lower-right corner of an active range? Suppose we accidentally erased a record in an Excel worksheet. Which command can be used to r immediately? Excel 2010 offers up to____________sort levels. Which feature in Excel 2010 enables us to find the input values needed to achieve a goal or objec The INT function________ Which of the following statements about scenarios is not true? What is a scenario summary report? What does Solver uses in its dialog box? What term describes a feature that gives Excel enhanced capability? What dialog box allows you to change a field name in a PivotTable? Why are PivotTables considered interactive? Identify the need for controls and auditing in a computerised environment. Grand totals calculated for any code on a document in the batch are called….. Control that checks if correct sequence of commands and update parameters are passed from the application software to the database. With respect to data integrity control, when monetary transactions are processed against master fi without a match, we should maintain a …. The system test that tests the top-level modules first and then the lower modules are simulated wi dummy modules to check the interfaces is called …. Identify the audit technique that examines each transaction as it passes through the system. The Core Image Comparison audit technique compares the…. The technique used by an auditor to list unused program instructions is….. The sample data created and used for the purpose of testing the application system is called…. The test data (dummy unit) implemented in the normal processing of the system over a period of known as…. The test data generated with correctness proof, data flow analysis and control flow analysis tools called…. The organisational, management, maintenance and access controls are categories of …… When a real-time system is simulated to generate the same output as the real-time system, the tech called…. When an auditor expands the extent of substantive tests to determine the impact of defects on the attainment of program objectives, the methodology is…. This is an important control in systems that use digital signatures for authentication purposes. Selecting transactions based on a sampling rate is called …. method. The capability of the generalized audit software to read different data coding schemes, different re formats and different file structures is…. The audit software capability of frequency analysis is to…. The audit functions of attributes sampling, variables sampling, stratified sampling are included in functions. Identify the functional limitation of a generalized audit software that enables evidence collection the state of an application system after the fact. The purpose-written audit programs are used for….. Picture of a transaction as it flows through the computer systems is called….. The application controls are …. Identify the type of audit when auditors are members of the systems development team. Identify the field check - "If a set of values is defined, is the input data one of these defined value The field check that conforms if data input for a field is in a particular format. The field check on a processed data that fails if a field is not initialized to zero or errors occur dur calculation is…… The validation checks applied to a field depending on its logical interrelationships with the other the record are called ….. A group of records or transactions that are contiguous constitute ….. …………..is the type of batch check (group of records) for all input records of a particular type is DB2 is an example of __________ ____________is used to Modify/Change Data in Table MS-Access is _________________ Which of the following is not a data type in MS-Access? To make changes in MS-Access form should be opened in __________________ _______layout of a form displays one record at a time In SQL, DML stands for _________ To see more than one record at a time in a form we use _______ The default query invoked by ms-access is __________ software serves as the Intermediary between the user and the database Distributed database have now come to know as a __________ database DDL Stands for -. In DBMS, view level data abstraction is known as __________ In DBMS, Normalization concept responsible for _______________ one 2 one, one 2 many and many 2 many Relationship exist in _________ model Record is also known as ________ in a Relational data base ____________ is extention of ACCESS DATABASE Default length of numeric data type is ____________ Default value option in field property use for ________ Value of Report Header exist on ___________ page of report __________ is an action or set of actions that you can use to automate tasks SQL is a _________ Language Which one is the Second Level of Data Abstraction? Memo data type store _________ number of characters. __________ data type field can't be updated A Record is also commonly called as a _________ Most database operations that we do manually can be automated by using _________ are what we use to summarize and present data in the table A database tabel is similar in appearance to a _______ SQL is considered to be a _______ SQL is considered to as an ideal Language for _______ DBMS that supports a database located at a single site is called a _____ DBMS that supports a database distributed across several different site is called a _____ The _________key does not accept Duplicate and Null values in Field. ______ is often implemented as an array of records In MS-Access 2010,the ________ control in the form lets the user insert a picture into it. Which query should be used to retrieve the following information from table of databases "Which employees earn more than Rs.30,000 a month?" Queries in MS-Access 2010 can be used as ________________________. What is a form in MS-Access? Which of the following degree of relationship cannot be applied in MS-Access 2010? In an ER model, a/an ___________ is any object, place, person, event or concept about which an enterprise records data. The process of arranging data in a logical sequence is called ____________. If some chunk of data is stored at two places in a database, then ___________. In MS-Access, what data type can be used for a phone number field in a database? E-R Diagram is ________________ Model. Which of the following can be a primary key in an employee database? Which of the following is a Database Management System? Which of the following is not a data type in MS-Access 2010? Which of the following is a New data type in MS-Access 2010? In MS-Access 2010, __________ queries are best suitable to summarize information and looking trends. Which of the following is not a section in Report Design view in MS-Access 2010? Which of the following is not an action query in MS-Access 2010? In MS-Access 2010, which data type is best suitable for storing the price of a commodity? In MS-Access 2010, which of the following data type creates a field that allows the user to choos from another table or from a list of values by using a list box or combo box? In a table, _____________ uniquely identifies each record that is stored in the table. _________ is used to insert values in Table directly. DCL provides commands to perform actions like _________. A database _______ presents summarized information retrieved from a table in a preformatted, at manner. In MS-Access 2010, which type of query extracts the data from one or more existing tables and p into separate table? In an MS-Access report, in which section we can keep the count[Sales] to calculate the total sales month? What is the first step in creating a form or report using the Form Wizard or the Report Wizard in M Access 2010? Which of the following is not an advantage of using a DBMS? ___________ provides in Access 2010 is used to convert database tables to the normalized form. Which Ribbon command tab includes the Table Analyzer Wizard in MS Access 2010 ? A Junction Table creates a _______________ relationship between two tables. The Primary key of one table and the matching column in another table is known as ___________ In SQL, having clause is used for _________ To compact the database in MS Access 2010, the database must be opened in the ___________. In MS Access 2010,_________ help protect a database from system failures and against mistakes Undo command cannot fix. Improving the performance of a database in MS Access 2010 used______________ tool. The _________ can be used to create reports on database objects for planning and modifying data design. Use _____________ to grant or revoke permissions or to change the owner of database objects. _____________ commands are used to enforce database security in a multiple user database envi Which SQL clause is used to retrieve data from database? The __________clause is used to filter records in database. DCL(Data Control Language) used for __________is Example of DBMS What are the features of the Payroll Software provide by the ICAI. Which are the transaction supported by the Billing and Accounting software ? The software provide creating,printing and sending bulk individual mail is___________________ The feature Archive is available in K-DOC application for the purpose of____________. Employee Information Portal feature in Payroll Application provide employee to view their________________. Which is not a feature of ICAI-ROC application ? The Payroll application supports three methods of salary disbursement are________________. Which Tools and Utilities is not supported by Payroll Application ? The software provide the facility to generate bills,receipts,vouchers and clients outstanding etc is______________. A software which provide the structured file management and knowledge mamnagement is_____________________. The software provides a complete package to manage secretarial requirements & generates forms MCA21 requirements The ICAI-ROC provides the facility to prepare________________. The software which provide the Contact Management,Correspondence Management, simplified Mail/Email etc. Correspondence feature of eSecretary application provide facilities are______________. To create New Contact and access Contact features are available in which application ? _____________________ is comprehensive package that combines Income Tax,Service Tax,e-TD etc. The financial transactions are to be …………. leading to different steps in Accounts Compilation The methods LIFO, FIFO, Moving Average are used to …. The report prepared taking the asset and liability type accounts from the Trial Balance is called… The report that depicts operating profit/loss for a period is ….. The day book contains transactions relating to ……… The Bills Receivable details are maintained in a …….. Creditors ledger has details of your dues to …….. The sundry debtors are placed in the Balance sheet on the …… The first step in Tally before any transaction is entered or saved is creating a ……… To configure country specific details use the function key…… Identify the security mechanism used in Tally. The basic document where transactions are entered chronologically is…. After selecting a company in Tally, you will be in the…… Tally software is based on ……… accounting system. Identify the primary group of capital nature that uses bank account and cash in hand as sub group All financial entries in Tally are done using……. The Direct expenses, Purchase account, Direct income are primary groups of ….. The option to delete a sub-group is admissible through the menu…… The behavioural attributes of this group cannot be changed. Credit limits for personal accounts and branches can be done in the ledger mode…… We are not allowed to delete a ledger from this mode. All account heads except Cash and Bank are placed in the…… These are the basis for analysis by potential investors, banks etc. Identify the primary group of capital nature that has the sub-groups: Bank OD Account, Bank OC Account. The primary document for recording all financial transactions in Tally is the…… You can customize the voucher entry screen using the function key……. Identify the voucher type that records fund transfers between cash and bank accounts. This voucher type records adjustments between ledgers. The use of classes for payment, receipt and contra vouchers enables data input in …… The details of a voucher entry can be given in the ……. The credit note voucher can hold account types: …….. The suffix and prefix details for the voucher type can be made applicable only from the ……. The voucher used to record all bank and cash payments is ….. The accounts that the business owns is called …. Tally's age-wise analysis considers the voucher's …… Arrange the steps in generating the books of accounts. 1. Create Trial balance 2. Create new ledgers 3. Generate Day Books 4. Update journals for financial transactions For day-to-day transactions the voucher types used are Say for example a payment is made to a creditor ABC - Rs.10000 by cash, it can be entered into t voucher type….. Identify the purchase voucher type, the transaction for purchase of 10 CPUs,10 monitors by credi Identify the voucher type to be chosen for the sale of computers to Anand by cash @ Rs.210000 p A bank overdraft repaid by cheque at Rs.25000 can be made in the voucher….. The financial statement that consolidates ledger balances is ….. The F9 function key in the left side of the Gateway of Tally screen displays the…… The option on the Gateway of Tally that will generate the P&L account statement is….. The expenditure for running the business for a period is ….. This displays the balance daywise for a selected voucher type. The feature in Tally to analyze accounts of a company is….. The age-wise statement is displayed based on…… The ratio analysis of receivables can be done based on…… Name the statement that helps the management in the decision making process. Identify the budget type which is chosen where transaction amounts are to be monitored. Choose the budget type to be used where bank accounts balances are to be monitored. The management that needs to consolidate the accounts of its various enterprises uses ……. in Ta Identify the user who can access audit trails in Tally. Identify the accounting feature in tally that facilitates splitting financial years for a company data. Identify the account type by the rule: "Debit the receiver and credit the giver". The tracking of changes in vouchers and ledger masters is done by….. Tally can import data from other programs and creates a log about the activity in the file….. Import and export of data between Tally and other programs is possible with the help of….. The manual option of voucher numbering leads to….. The Tally audit trail tracks changes made to vouchers that are ….. The ratio analysis of Bills Receivables or Bills Payables can be displayed with the function key… The test data generated with correctness proof, data flow analysis and control flow analysis tools called…. When a real-time system is simulated to generate the same output as the real-time system, the tech called…. When an auditor expands the extent of substantive tests to determine the impact of defects on the attainment of program objectives, the methodology is…. This is an important control in systems that use digital signatures for authentication purposes. The first document where the transaction is entered is called a ….. Selecting transactions based on a sampling rate is called …. method. The capability of the generalized audit software to read different data coding schemes, different re formats and different file structures is…. The audit software capability of frequency analysis is to…. The audit functions of attributes sampling, variables sampling, stratified sampling are included in functions. Identify the functional limitation of a generalized audit software that enables evidence collection the state of an application system after the fact. The purpose-written audit programs are used for….. Picture of a transaction as it flows through the computer systems is called….. Identify the type of audit when auditors are members of the systems development team. The document used for posting of accounting transactions is …….... When the debit total is greater than credit total, the amount appears in the …….. column. uestion at http://caknowledge.in/itt-question-bank-ca-students/ Option A Numeric Data FALSE Analysis ACL Equation Editor Option B Date Data TRUE Data IDEA function Editor Option C Both A and B Relation Unix Calculation Editor Items of audit interest Data Analysis File Definition Stratification System validation Print Preiview Review Programming standards Detection Numeric Data Primary Key Understand program specifications Exclude Date Data Unique Key Formulate flaw hypotheses Sequence checking Character Data Secondary Key Random Systematic All of the above Random TRUE Field check Systematic FALSE Filter check All of the above NEFT, RTGS Beneficiary bank NEFT UTN RTGS,NEFT Central bank(RBI) RTGS UTE EFT,RTGS Remitting bank EFT UTR Straight Through Processing VLAN Straight Temporary Processing LAN Strict Through Processing WAN Control Management System Cash Management System Core Management System Systems audit are Audit of internal important for the controls is not needed verification of the at all internal controls Compare check Audit of controls in any banking environment is performed using software audit Managing of Assets Formulating a security Developing a business policy continuity planning Firewall Internet banking Core Banking Solution ATM Data centre Middleware Web centre ATM Server Central Application Server Database Server System version Application Version Client version Virtual Local Area Network Data base server LAN Local Area Network ATM DATA Server Virtual Networks Wide Area Network Domain Name Server MAN Application Development Software Development Server Development Review Management LANs RTGS VLANs Log management WANs Consalidation Password Policy protection Positive Balance File Militarised zone Web server Application Server City Zone IBAS Centralised Data base security State zone IBDS Hacking Method Push-pull method Both A &B Sytem software utility software Application Software local line Leased line Broadband 16 digit number Personal Identification Number Net transaction ID NO Output Control Input control Process Control Letter of Credit Letter of Tax Letter of Payable Business Recovery Planning Programmer testing Infosys Business Continuity Planning User testing HCL Technologies Disaster Recovery Planning (a) & (b) both TCS Pin No - offset value Offset value - Pin No Pin No - Natural Pin Soft copy of Electronic Hard copy of Electronic journal Journal Cash register Offset value Pin sent to customer Natural Pin Expression Elements Operator Button Expression Box Will match all text starting from B Will match all text ending from B Will match all text having second character as B Select query Crosstab query Action query Alphabetical Order Form only FALSE At the end of the table Any where in the table Form but not in table Table but not in Form TRUE ActiveX control Caption Inner-Report Unbounded Controls Background Sub-Report Graphics Control Record Source Inside-Report Table or query,InnerReport Table or query,MainReport Table or query,SubReport Data Definition Language Detailed Definition Data Defined Language Language Pie Chart Pie Chart .ACCDB Area Chart Line Chart .ACCDE Bar Chart Bar Chart .MDW Front-end database Back-end database Both of them HTML and InfoPath Access Forms Visual Basic Application Export to Outlook Text Options in Tool menu of Access Number To add table To store objects created in other programs For long text entries Manage replies Date/time Those records that match an entity in a field Records based on a criterion you specify Records that meet any of several criteria you specify Detailed Maintaining Language Data Maintaining Language Data Manipulation Language The Visual Basic 1.0 editor Notepad The QuickBasic editor Save your changes, close the workbook, and then reopen it. Click the report, and on Select the Pivot Table the Pivot Table toolbar, worksheet and press F9 click the refresh data on the keyboard button Datasheet View Ole Object Form DCL Design View Hyperlink Query DML Pivote Table & Pivot Chart View Memo Macro DDL Insert, Update Or Change The Structure Delete Records And Of Tables Data Values Authorizing Access And Other Control Over Database Network Database Model Memo Relational Database Model Number Object Oriented Database Model Date/time Data Definition Data Refinement Establishing Relationship Not update update automatically have to update manually Relationship Join Query To build a main switchboard form that Creates the macros used To allow the user to controls all other to program an switch from one database forms. automatic application. file to another. The reports are restricted in size. It doesn’t It doesn't have as many design options. Type the text directly into the label. Report Footer Use the > button. Section Header Use the Mailing label wizard text option. Page Footer Pivot Table Fixed-down Pivot Chart Locked-down All The tools of the form design control gallery. Open-down Make Table Query Open Secure mode $ Math Macro Update Query Open Inclusive mode # Date Form Delete Query Open Exclusive mode () Text Report Open Modify Read TRUE Create Tab Forms Tables FALSE External Tab Query Forms File tab Report Query A back-end database & A new database & Old primary database & front-end database database. secondary database XML page single dimensional XML Networking Local Data Local User Owner HTML Page hyper dimensional HTML VB.Net Remote Data Remote User Public User Web page multi dimensional ASCII Tally.Net Internet Data Both A & B Data Entry charts, pictures BPM smart art, clip art SCM flowcharts, flow diagrams PLM Online Analysis Processing Inbound Operations Online Analytical Processing Outbound Operations Online Analytical Programming Sourcing planning Logistics Asset Management PLM Step 1 Step 2 Step 3 implementation upgradation installation pre implementation under process review post implementation post implementation pre implementation Both A & B Interactive Processing Immediate Processing Real Time Processing Form 26, Annexure to Form 27, Annexure to 26 27 Form 26Q, Annexure to 26Q File Validation Program integrated File Validation Utility distributed File Valuation Program isolated Data Warehousing data-driven general data operational supply and demand Data Modeling information driven historical data backup supply and chain Business Modeling resource driven operational data data supply and sortage Inbound operations business front office outbound operations corporate back office hybridbound operations strategic staff CRM's encryption ERP decryption SCM cryptography Interactive Processing Immediate Processing Information Systems Real Time Processing Integrated Information Decision Support Systems Systems Form 26, Annexure to Form 27, Annexure to 26 27 Form 26Q, Annexure to 26Q File Validation Program File Valuation Program File Validation Utility Tally Fix Tally Adjust Tally Fit HTTP-XML based data Unlimited multi-user User-defined Security interchange support Direct Web Browser Access Web Publishing Tally.NET Allow to Connect Company Contact On Load Either A or B Data Warehousing TRUE Powerpoint Data Modeling FALSE Word Business Modeling Email middle attack. Web tapping Email Spoofing. Web Interception Email hacking. Web spoofing Payroll eSecretary Billing and Accounting software Contact Management Greeting Management Email Management Paste Document ICAI-ROC application K-DOC application ICAI XBRL Software K-DOC application eSecretary ICAI XBRL Software Statutory audit Tax audit Internal auditiing Financial reporting Operations of the organization Both A and B Section 45 Section 44AD Section 43B ERP Office automation Either A or B Foreign Exports Management Act Financial Enterprise Management Act Foreign Exchange Managament Act Resource allocation and scheduling Knowledge management Document Management Systems Database administrator Account administrator System administrator AP module GL module TRUE FALSE AR module Receipts of goods or Evaluation of Vendors service Invite and analyze quotations from vendors Purchasing Accounts Payable Expense Management Purchasing Accounts Payable Sales Accounts Receivable Accounts Payable Expense Management Resource allocation and scheduling HR and Payroll applications Knowledge management Confidentiality,Integrit Confidentiality,Integrity Confidentiality,Integrity y and Availability and Authentication and Access rights Performance management system HR management system Payroll Capture the Key Employee designation Automated alerts for Performance Indicators and reporting structure pending appraisals Timesheet System HR management System Reduce administrative burden on HR Excess leave half-yearly yearly Payroll System Error free capture of leave details monthy Organization chart Client’s accounting manual Copies of clients’ incorporation documents like MoC Internal Training E-Learning Classroom Training Classroom Training PC E-Learning Application Server Virtual Learning WAN Confidentiality Integrity Availability Microsoft Exchange Lotus Notes Both A and B Most WANs are owned by only one organization. Confidentiality Client data Availability Compared to LAN, its transmission speed is low Integrity Own data Confidentiality WAN uses only private networks. Information Security Own documents Integrity Integrity Authentication Confidentiality Non-Repudiation reputational Integrity financial Authentication operational Availability Authentication Confidentiality Resource allocation and scheduling ICAI-XBRL suite Client management K-DOC HR and Payroll Billing and Accounting Private Exchange Branch Public Exchange Branch Private Branch exchange Corporate planning Monte Carlo simulation Financial planning Monte Carlo Simulation Corporate Planning Debt Assets Ratio Interest Coverage Ratio Total Fund Ration Earnings Per share Fixed Asset Over ratio Price Earnings Multiple Decision Tree Analysis <?xml version="3.0" <?xml version="2.0" <?xml version="1.0" encoding="ISO-8859- encoding="ISO-8859- encoding="ISO-88591"?> 1"?> 1"?> <TagName>Data</Tag </TagName>Data<Tag </TagName>Data</TagN Name> Name> ame> Directally Delete Command 3 Annual Income Delete Button 2 DOB XML Maps Dialog Box 1 status of assess Snowball sampling Sampling Systematic sampling Clustered sampling Sampling Systematic sampling Snowball sampling Convenience sampling Systematic sampling Quota Sampling Sampling Snowball sampling Balance sheet discounted cash flow Net present value Summary reports internal rate of return Working capital IRR net present value IRR Sensitivity analysis Risk analysis Qualitative risk analysis Sensitivity analysis Risk analysis Qualitative risk analysis Graphs Sparklines Both A& B Decision Tree analysis Sensitivity analysis Both A& B Scenario analysis SUMIF() Du Point Analysis Mortagage Sensitivity analysis PMT Return on Investment Leasing Decision Tree Analysis COUNTIF() Profitability Ration Rent Format -> Window Window -> Split View -> Window -> Split Settings Tab under the Settings Tab under the Settings Tab under the tab Data -> Filter Tab Format -> Cells tab Data -> Validation ->Advanced Filter Counts cells having alphabets Counts empty cells Counts cells having number A1+ "@" + B1 A1 # "@" # B1 A1 & "@" & B1 ROUNDDOWN(7.4999 ROUNDUP(7.4999,0) ,0) ROUND(7.4999,0) Bar Chart Sparkline Pivot Chart Bar Chart Pivot Chart Sparklines Pagelayout -> Page Setup -> Print Area Add Ins # Pagelayout -> Print Area Developer Tab $ AVERAGE(4,5,6,7) MOD() 3 XWE Top10 Sort & Filter AVERAGE(A1:A6,B1:B AVERAGE(A1,B1,C1) 6) INT() DIV() 5 7 XFD XAA Bottom10 Top half Outline Data Tools Workbook Column .odc file Line .htm file Scatter Consolidation by position TREND Consolidation by category STANDARDIZE Consolidation using 3-D formulas CORREL PV NPV IRR Sparklines Cells C3 through C6 Shift + F10 Slicers Cell C3 and Cell C6 Shift + F1 Macros Cell C4 and Cell C5 Shift + F11 Ctrl Alt Shift Name Box Formula Bar Zoom Box Page Setup -> Print Area Text Import wizard & Name of the workbook Name of the worksheet Name of the cell or range currently working on currently working on currently working on Copy handle Fill handle Insert handle Insert 32 Replace 64 Paste 60 Goal Seek Consolidate Data Validation Rounds a number to a Rounds a number down desired multiple to the nearest integer Rounds a number up A scenario is a set of values saved with the workbook. Scenarios provide a way A workbook can have to see different solutions one scenario per sheet. for worksheet formulas. A formatted description of each scenario on a separate worksheet Arguments Trendlining Field Options A formatted defined range of Solver and Goal Seek solutions Limitations Enhancement bit Field Pane A worksheet with a separate thumbnail for each formula Constraints Thumbnail Field Settings They allow you to They allow you to add rearrange row and dynamic data. column data. They allow you to generate e-mail enabled reports. Absence of input documents Financial totals Lack of visible transaction trail Record totals Accessibility of data and computer programs Document totals Table level Data Integrity Batch check Sequence account Data account Suspense account Bottom up test Embedded code Hybrid test Program code Stub test Database Analyzers Database with master table Modelling Test data Executable program with master copy Analyzing Table data Transaction data with master transaction Mapping Item data Integrated Test Facility Black box Test Facility Graph testing Test item block Application controls Test data pack General controls Test program pack Check controls Parallel trailing Tracing parallel Parallel coding Cross reference lister Public audit trails Formulate flaw hypotheses Random audit trails Correct lister Sample audit trails Transaction sampling Systematic sampling Simple sampling File size File data File access Sort and merge files Sampling nth item Formatting output Stratification Selection Statistical Limited ability to determine Propensity for Ex Post Auditing Only Analytical review only Error Sorting, creating, and printing files Program Input controls General audit Data retrieval, code comparison Track Processing controls Post audit Reading data, selecting and analyzing information Snapshot Both A and B System audit List Format mask Range Data mask Slab Field mask Range Sign Overflow Field checks Physical batches Record checks Logical batches Batch checks Block batches Control totals ODBMS Update Query DBMS Number Form view Tabular Serial number RDBMS Process Query RDBMS Character Form Design columnar Transaction type DBMS Insert Query ODBMS Memo Change Form Datasheet Data manipulation language Tabular Update Query DATABASE Client data base Data mathematical language columnar Select Query DBMS Server data base both a and b both a and b Delete Query O.S Client-Server database Data Definition Data Design Language Define Data Language Language Internal Schema Conceptual Schema External Schema Increase data duplication Reduce Redundancy Increase Efficiency Hierachical Attribute .mdb 255 char FLAT FILE SYSTEM Entity .dbf 16 chra Relational model Tuple .accdb text enter a value automatically every program Programming Physical level 256 YES/NO column Program Report MS-WORD 3 GL Java Multiuser DBMS for checking first check Non-Procedural Logical Level 1000 HYPERLINK field query Query Excel/spreadsheet 4GL Internet Distributed DBMS for validation check last macro Application View Level 16536 MEMO tuple form Form Powerpoint 5GL Database Centralized DBMS Client-Server database key field Record Title Distributed DBMS Primary key Tuple Logo Multiuser DBMS Reference Key Tabel Picture Search Query Make Table Query Aggregate Query View, change and analyze data in different ways A source of records for forms and reports Both A and B It is a Data Entry Screen to make It is a printed page viewing, entering and where users will enter editing data in the data database table One-to-One One-to-Many It is a part of database used by the analysts to draw conclusions Many-to-Many Entity Classifying Relationship Sorting Attribute Filtering Changing the data at one place only will cause data Storage space is wasted inconsistency Number Text Conceptual Model Structural Model Employee Code Employee Name Java Oracle Memo Yes/No Memo Yes/No It can be more easily accessed Memo Object Model Date of Birth Lotus 1-2-3 Image Calculated Field Crosstab Action Parameter Report Header Section Page Header Section Select Delete Text Number Detail Section Make Table Currency OLE Object Unique Key Query Hyperlink Primary Key Form Memo Foreign Key Report Changing the structure Creating views and of tables indexes Authorizing access and other control over database Form Query Macro Parameter query Update query Crosstab query In the Report Header Section In the Report Footer Section In the Page Footer Section Selecting the underlying table or Reading several screens Selecting the fields that query on which we of mostly useless we want to appear in want to base the form or information and clicking the form or report report next Data independence Data integrity and security Decentralized data Database Analyzer Table Analyzer Wizard Wizard Create External Data One-to-One One-to-Many Form Analyzer Wizard Home Many-to-Many Matching Key Foreign Key Index key For ordering records specifying conditions with group by clause updating records Inclusive Mode Exclusive Mode Normal Mode Backups Save Database Save As Databse Performance Analyzer Hi-tech Analyzer Online Analyzer Table Documenter Database Documenter Query & Report Documenter User and Group Accounts User-level Security Wizard User and Group Permissions Security SELECT SELECT Grant and revoke WHERE WHERE Select FROM FROM Entering Data Word Defining Data Excel Controlling/Accessing Data Access Recruitment Management salary Process Time & attendance Billing Previous years pending bills Cash receipt eSecretary software To create new file Personal profile Contact Management software Template Management software To save file To cut & paste the completed and old document. PAN Number PF No,online submission of loan etc Generation of forms as per formats and requirement of MCA Maintain Minutes Book Calculate the filing fee Salary Paid in Cash Salar paid by Cheque/DD MIS Export Journal Voucher TCS Salary credited to Bank Billing & Accounting softwatre Payroll Software K-DOC application ICAI-File management application K-DOC application Knowledge Management Software Billing & Accounting softwatre Payroll Software K-DOC application Shares Auto filing of eForms Records/Certificates Annual Returs forms eSecretary software Templates Contact Management software Blank document Template Management software Outside document eSecretary software Contact Management software Template Management software Tax Application K-DOC application Tax Suite Application Collected and computed Value closing stock P & L statement Trial balance Grouped and Sampled and stratified summarized Value clearing stock Value expense stock Income statement Balance sheet Trading account P & L statement Income or expenditure Sales or purchase Journal sheet Voucher debtors Customers Assets Asset or liability Sundry debtors Liabilities Income side File F10 Tally Secure Ledger Accounts of Tally Sales Assets side Company F2 Tally Pack Journal Gateway of Tally Production Expense side Project F12 Tally Group Voucher Entry of Tally Mercantile Fixed assets Vouchers Capital nature Alter Sub-group Single Single Current assets Groups Expense nature Delete Ledger-group Multiple Sub-group Loan assets Journal Revenue nature Display Primary-group Sub-group Alter-group Sub Ledger master Group Ledger master General Ledger master Journal and Ledger P & L Account and Journal P & L Account and Balance Sheet Expenses Journal F13 Credit Note Sales Double entry mode Comment Income Trial sheet F12 Payment Receipt List entry mode Memo Assets Voucher F10 Receipt Payment Choice entry mode File Sales account, Sales tax account End of a month Credit Note Liability Previous date Ledger account, Bank account First of a year Contra Income Effective date Suppliers account, Purchases account First of a month Sales Note Sales Current year 1, 2, 3, 4 Credit purchase 1, 3, 4, 2 Cash purchase 2, 4, 3, 1 Both A and B Loan Payment Receipt Credit Purchases Cash Purchases Expense Purchases Cash Ledger Payment Sale Sheet Receipt Stock Journal Debit Balance sheet Accounting reports Net Loss Expense Record book Ratio analysis Income Bill date Data flow On closing balance On closing balance Profit & Loss statement Inventory reports Net Income Example Ledger book Account analysis Payables Effective date Funds flow On net credit flow On net credit flow Trial balance P & L reports Net Profit Taxes Journal book Data analysis Expenses Voucher date Stock flow On net transactions On net transactions Consolidate company Group company Owner Data Entry operator Month-less accounting Real accounts Tally Vault Tally.imp OLE Auto numbers Set company Accountant Yearly-entry accounting Period-less accounting Personal accounts Nominal accounts Tally Audit Tally Report Tally.cfg Tally.exp DBMS ODBC Duplicate number Sequence number more than 30 Days old less than 30 Days old F5 F8 more than a day old F12 Test item block Test data pack Test program pack Parallel trailing Tracing parallel Parallel coding Cross reference lister Public audit trails Formulate flaw hypotheses Random audit trails Correct lister Sample audit trails Ledger Liability Voucher Transaction sampling Systematic sampling Simple sampling File size File data File access Sort and merge files Sampling nth item Formatting output Stratification Selection Statistical Limited ability to determine Propensity for Ex Post Auditing Only Analytical review only Error Reading data, selecting and analyzing information Snapshot System audit Sorting, creating, and printing files Program General audit Data retrieval, code comparison Track Post audit Voucher and journal Income Balance sheet and trial Ledger and trial balance balance Debit Credit k-ca-students/ Option D None of the above Sampling SOFTCAAT Testing Editor Answer C B D C A All of the above Append D B All of the above Filter All of the above Composite Key D A D B None of the above B None of the above Data check A A A None of the above None of the above All of the above UTS B B B C None of the above MAN A A Centre Management System B None of the above B Laying down procedures for system development A Web centre C Central Office Data Centre. D Domain Name Server B Firewall C Personnal Area Network Application Server WAN A A B System Development D Authorized Controller C MANs B Validation D Central Office Data Centre. demilitarised zone All the above A D D None of the Above B Application Server C None B ATM No B Data Control C Letter of Receible A None None of above I-Flex B C A Offset Value - Natural Pin C (a) and (b) both A Card Number C Expression Builder window C Will match all text starting with a digit A Parameter query B Beginning of the table B Form & Table D B Bound Controls Picture Insert-Report B D C None of the above C Data Detailed Language A Column Chart Column Chart .ACCDT D B B None of them B Excel attachment A All of the above AutoNumber C D For shout text entries of no more than 255 characters C All of above A Detailed Manipulation Language C All of above B All of the above C All Of Above Lookup Wizard Report None Of Above D D B A None Of Above C Structureed Database Model D Hyperlink C None Of The Above A never update B None Of These A To allow changing from one report to another. A The only report type available is the Design Report. B Use the >> button. Page Header C C Form Wizard Columnar None of the above C B Parameter Query Open Read Mode "" None of the above None of the above D C B A A Write A Database Tools All of the above Report A D D A None of the above A None of the above none ALL None of the above None of the above None of the above Tally.NET User C C D C B C B graphs, shapes CRM C B None of the above Production planning B A CRM D Step 4 B migration C None of the above C Either A Or B A Business Processing C All of the above D File Valuation Utility B de-centralized A Business Intelligence none none none none D A B A A none none none B B A none none A A Business Processing C Non-Isolated Information Systems C All of the above D File Valuation Utility B Tally AutoFit C Audit Feature D Email facility C None of the above B Business Intelligence A B My Templates C Email tracking Web threating B C K-DOC application C Share certificate printing D Payroll A ICAI-ROC application B None of the Above C Either A or B C Section 44AB D None of the Above B None of the Above C Client management D User Administrator C FA module B B Comparison with budgets D Fixed assets C Accounts Receivable B Bank Reconcilations C None of the Above B Confidentiality,Integra tion and Authentication A Timesheet application D Prepare summary or bell curve analysis of all employees B Knowledge management System C Approval workflow quarterly C B Copies of important contracts or long term lease agreements C E-Training B All the Above All the Above B D Authentication B None of the Above C Switches are used to connect LAN and WAN None of the above All the above Authentication B C D B Availability D Confidentiality vulnerable A D Integrity B None of the Above ICAI-TOC D D Public Branch exchange C Personal Finance planning C Corporate Planning & Analysis B None of the above B Gross Profit Ratio C <?xml version="0.0" encoding="ISO-88591"?> C <TagName>Data<Tag Name> A None of the above 4 All of the above. C B D Simple random sampling B Simple random sampling C Simple random sampling D Simple random sampling C NPV All the above PMT B D A Scenario analysis B Scenario analysis C Charts D Neither A &B B None None of the above None of the above All the above A B A B View -> Split B All of the above B Counts non-empty cells D A1 $ "@" $ B1 C Only B & C D Pie Chart B None of the above B Print Area Analysis Tool Pak * A C C All of the above REMAINDER() 11 AAA All Calculation D A A B D B .udcx file Bubble C A Any of the above GROWTH C A PMT D Data Forms None of the above Shift + F12 B A A Ctrl + Shift A Sheet Tab A Formula in the cell currently working on C Border B Undo 80 D B Subtotal A Calculates interest B Scenarios help to perform what-if analysis. B A worksheet with separate macros for each scenario Parameters Add-in Field Structure A D D C They allow you to print the reports with various settings. B All of the above Hash totals D D System test B Update account C Top down test Database code D A Module programs with snapshots B Tracing C Record data A Whitebox testing A Test record pack Input controls B B Parallel simulation D Formulate correct hypotheses Data audit trails B A Demographic sampling B File reorganisation C Classify data on a criteria D Reporting C Limited ability to Verify Processing logic A Specific tasks with original or modified programs Picture Neither A nor B Concurrent audit D C C D Digit Input mask C A Serial C File checks Transact batches B A Sequence check None None None Date None None C C A A B B B None None None None None A A B B C None None C C All B None None None long Integer C C C D None None All None None 63999 AUTONUMBER None macro Macro None None Visual Basic Database A B C B B D D C D A B B C C Centralized DBMS None Attribute Graphic B B B B Select Query D Neither A nor B C None of the above Many-to-One B D None of the above Summarizing A C Both A and B Any of the above Interface Joining Date MS-Outlook AutoNumber AutoNumber D B A A B C C None of the above A Summary Section Update AutoNumber D A C Lookup Wizard Record Key None D C A Inserting, updating or deleting records C Report D Make Table query D In the Month Group Footer Section D Selecting how the form or report should be formatted B Reduced application development time C None of the above Database Tools None of the above A D C None of the above B None B Save Mode B None of the above A None of the above A None of the above B None of the above C Create INSERT INSERT B A B All None C C All of the above D All of the above D All of the above A None of the above C All of the above D Bank Receipt D All of the above D Backup utilities C ICAI-ROC application A None of the above B ICAI-ROC application D All of the above D All of the above All of the above A D All of the above A All of the above C Assets and liability Value income stock Asset sheet Suspense accounts C A C C Profit or loss Original entry Suppliers B C D Payable side Application F11 Tally Vault Trial Balance Groups of Tally Manufacture B B C D B B C Capital assets Ledgers Income nature Shift Alter-group Alter-group Multiple B D C A C B D Journal Ledger master C Voucher Account and Balance Sheet C Loans File F11 Contra Journals File entry mode Narration D C B D D B D Buyer's account, Cash account End of a month Payment Asset Configured date A C D D B 3, 4, 2, 1 Contra purchase C C Sales B Debit Purchases A Purchase Voucher Contra C D Journal Expense reports Net Account Income Day book Transaction analysis Loans Previous date Cheque flow On net cash flow On net cash flow C B C A D A B A B C A Alter company Administrator B D Transaction-number accounting Expense accounts Tally Group Tally.ole MS-XLS Range number C B B A C B more than a week old A F6 D Test record pack B Parallel simulation D Formulate correct hypotheses Data audit trails B A Expense C Demographic sampling B File reorganisation C Classify data on a criteria D Reporting C Limited ability to Verify Processing logic A Specific tasks with original or modified programs Picture Concurrent audit D C D Journal and ledger Expense D B