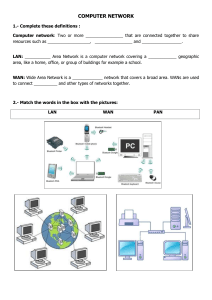
TRANSPORT NETWORK DESIGN UNIT 15 Ahamed Shamil KG-64212 Contents a) What type of network should be deployed in the Main Building and what equipment should be installed and please describe about that devices?.................................................................................3 Types of Network Switches ....................................................................................................................... 6 LAN Switch or Active Hub ................................................................................................................ 6 Unmanaged Network Switches .......................................................................................................... 7 Managed Switches ............................................................................................................................... 7 Core Routers vs. Edge Routers .......................................................................................................... 9 Virtual Router ....................................................................................................................................... 9 Nodes on a LAN ....................................................................................................................................... 10 Types of Local-Area Networks (LANs) ..................................................................................................... 10 b) What type of network should be deployed in the SUB-A Building and what equipment should be installed (describe your answer)? ………………………………………………….10 c)What type of network should be deployed in the SUB-B and what equipment should be installed (describe your answer)??.............................................................................................11 Firewall ........................................................................................................................................................ 13 d) What type of network connections should be used to link the buildings together and where and how should the College’s Internet connection be made? ……………………….15 • BUS Topology ................................................................................................................................ 17 • RING Topology ............................................................................................................................. 18 • STAR Topology ............................................................................................................................. 18 • MESH Topology ............................................................................................................................ 19 • TREE Topology ............................................................................................................................. 19 • HYBRID Topology........................................................................................................................ 20 1. Personal Area Network (PAN)..................................................................................................... 21 2. Local Area Network (LAN) .......................................................................................................... 21 3. Wireless Local Area Network (WLAN) ...................................................................................... 21 4. Campus Area Network (CAN) ..................................................................................................... 21 5. Metropolitan Area Network (MAN) ........................................................................................... 21 6. Wide Area Network (WAN) ......................................................................................................... 22 7. Storage-Area Network (SAN) ...................................................................................................... 22 8. System-Area Network (also known as SAN) .............................................................................. 22 9. Passive Optical Local Area Network (POLAN) ......................................................................... 22 10. Enterprise Private Network (EPN)............................................................................................ 22 1|Page 11. Virtual Private Network (VPN) ................................................................................................. 23 Hierarchical Network Design ........................................................................................................... 23 What does Network Redundancy mean? ............................................................................................... 26 MRP - Media Redundancy Protocol ....................................................................................................... 34 PVST+ and Rapid PVST+ ........................................................................................................................ 44 PVST+ (Per VLAN Spanning Tree Plus)................................................................................................ 44 PVST+ (Per VLAN Spanning Tree Plus) is a Cisco proprietary STP version. It is also the default STP version for Cisco devices. It is the standard named 802.1d. ....................................................................... 44 How WANs Are Connected ..................................................................................................................... 47 Leased Lines and Metro Ethernet ........................................................................................................... 48 Problems With Wide Area Networks ...................................................................................................... 48 Network Management Protocols............................................................................................................ 60 Network management protocols are network protocols................................................................ 60 Be clear about the approach of the protocol........................................................................................ 60 Network management protocols and their architecture................................................................ 61 Network management protocols and the organization of dataAnother fundamental point is the way in which the network administration protocols format and manage the management data. ................... 61 ICMP .................................................................................................................................................. 62 SNMP ................................................................................................................................................. 62 Architecture SNMP........................................................................................................................... 63 1. Duplicate IP Addresses ........................................................................................................................ 64 2. IP Address Exhaustion ......................................................................................................................... 64 3. DNS Problems ..................................................................................................................................... 65 4. Single Workstation Unable to Connect to the Network ..................................................................... 65 5. Unable to Connect to Local File or Printer Shares .............................................................................. 66 6. Local Network is Unable to Connect to the internet .......................................................................... 66 7. Slow Internet Performance ................................................................................................................. 67 According to cisco ................................................................................................................................... 68 Configuration Issues................................................................................................................................ 68 • SSID Mismatch.......................................................................................................................... 68 • Security Mismatch .................................................................................................................... 68 • Disabled WLAN ........................................................................................................................ 68 • Unsupported Data-Rates .......................................................................................................... 68 2|Page LO1 Explore LAN design principles and their application in the network design process. Part 1 a) What type of network should be deployed in the Main Building and what equipment should be installed and please describe about that devices? Network design refers to the planning of the implementation of a computer network infrastructure. Network design is generally performed by network designers, engineers, IT administrators and other related staff. It is done before the implementation of a network infrastructure. Network design involves evaluating, understanding and scoping the network to be implemented. The whole network design is usually represented as a network diagram that serves as the blueprint for implementing the network physically. Typically, network design includes the following: • • • • • Logical map of the network to be designed Cabling structure Quantity, type and location of network devices (router, switches, servers) IP addressing structure Network security architecture and overall network security processes 3|Page Main Building I recommend LAN network should be deployed in the main building based on the scenario, suppose high speed, high bandwidth connectivity. Local area network – LAN • • • • • • • • LAN is a network within a geographical location. Usually within a room/building Will be owned by the same organization Typically, wired LANs run at speeds of 100Mbps to 1Gbps, have low delay, and make very few errors. LANs can be wired or wireless (IEEE 802.11) Initially was a broadcast system IEEE 802.3 popularly called Ethernet is the most popular LAN technology It is also possible to divide one large physical LAN into multiple smaller logical LANs or VLANs 4|Page Repeaters/Hubs A repeater receives a digital signal and re-amplifies or regenerates that signal, and then forwards the digital signal out all active ports without looking at any data. An active HUB does the same thing. Any digital signal received from a segment on a HUB port is regenerated or re-amplified and transmitted out all ports on the HUB. This means all devices plugged into a hub are in same collision domain as well as in same broadcast domain. A hub is really a multiple-port repeater. HUBs, like repeaters, don’t actually examine any of the traffic as it enters and is then transmitted out to the other parts of the physical media. switches By default, switches break up collision domains but are one larger broadcast domain. Switches aren’t used to create internetworks; they’re employed to add functionality to an internetwork LAN. The main purpose of a switch is to make a LAN work better, to optimize its performance, providing more bandwidth for the LAN’s users. Switches forward frames from one port to another within the switched network. 5|Page With a layer 2 switch, an incoming frame from a particular station is switched to the appropriate output line to be delivered to the intended destination. At the same time, other unused lines can be used for switching other traffic. Just like Hub and Bridge, Switch is also used to connect the multiple devices together in a LAN segment. Basically, a Switch is the upgraded version of the Bridge. Besides providing all the functionalities of Bridge, it also offers several additional features. The biggest advantage of Switch is that, it makes switching decisions in hardware by using application specific integrated circuits (ASICs). Unlike the generic processors that we use in our PC, ASICs are the specialized processors built only to perform very few particular tasks. Usually, the ASICs in the Switches have single task and that is the switching the frames as fast as possible. An ASIC occupied switch performs this task blazingly fast. For example, an entry level Catalyst Switch 2960 can process 2.7 million frames per second. Types of Network Switches LAN Switch or Active Hub Also known as the local area network or Ethernet switch, this device is used to connect points on a company’s internal LAN. It blocks the overlap of data packets that run through a network by 6|Page allocating the bandwidth economically. When we say bandwidth, it refers to the amount of data that can be carried from one point to the other under a given period of time. With a LAN switch, it reduces the network traffic by delivering the data only to its intended recipient. The important bandwidth would first be delivered before the subsequent ones. Unmanaged Network Switches Mostly used in home networks and small companies or businesses, this device allows other devices on the network to connect with each other; it could be from one computer to the other, or a computer connected to a printing device. As what the name suggests, this type of device does not need to be watched constantly and it is the easiest and simplest installation, because of its small cable connections. Managed Switches Unlike the unmanaged network switch, this device is customizable; because of this feature, you can enhance the functionality of a certain network. This device has two types – Smart switches and Enterprise switches. Smart switches have limited features, but provide a web interface and accept configurations of basic settings. They are perfect for fast and constant LANs which support gigabit data transfer and allocations. Enterprise switches have a wide range of management features and the capability to fix, copy, and transform and display network configurations. They are usually found in large companies which contain large numbers of connections, nodes, switches, and ports. Having more features than the smart switches, Enterprise switches are usually more expensive. Layer-3 switches The function of a layer-3 switch (multilayer switch) combine L2 switch and some of a router feature. A L2 switch works with MAC addresses only, whereas a L3 switch understands IP address. L3 switches perform routing functions, it can do static routing and dynamic routing. That means, a L3 switch has both MAC address table and IP routing table. It can handle intra-VLAN communication and packets routing between different VLANs as well. L3 switch will consist of multiple broadcast domain. 7|Page Routers Routers are used to connect networks together and route packets of data from one network to another. Routers, by default, break up a broadcast domain. A router creates & maintains a table of the available routers and their conditions and use this information along with distance and cost algorithms to determine the best route for a given packet. Typically, a packet may travel through number of network points with routers before arriving at its destination. The router connects the different network segments. It switches the data packets between those networks which are either located in the different logical segments or built with the different network layer protocols. When a router receives a data packet on any of its interface, it checks the destination address of that packet and based on that destination address, it forwards that data packet from the interface which is connected with the destination address. To forward a data packet to its destination, router keeps the records of connected networks. These records are maintained in a database table known as the routing table. Routing table can be built statically or dynamically. Basically routers are used: • • • To connect different network segments. To connect different network protocols such as IP and IPX. To connect several smaller networks into a large network (known as the Internetwork) 8|Page • • • • • To break a large network into smaller networks (Known as the Subnets. Usually created to improve the performance or manageability.) To connect two different media types such as UTP and Fiber optical. To connect two different network architectures such as Token Ring and Ethernet. To connect LAN network with Telco company’ office (Known as the DTE device). To access DSL services (known as the DSL Router). Core Routers vs. Edge Routers A core router is a wired or wireless router that distributes Internet data packets within a network, but does not distribute data packets between multiple networks. In contrast, an edge router is a wired or wireless router that distributes Internet data packets between one or more networks, but does not distribute data packets within a network. Virtual Router Unlike a physical wired or wireless router, a virtual router is an abstract, intangible object that acts as a default router for computers sharing a network. The router functions using the Virtual Router Redundancy Protocol (VRRP), which becomes active when a primary, physical router fails or otherwise becomes disabled 9|Page b) What type of network should be deployed in the SUB-A Building and what equipment should be installed (describe your answer)? A local-area network (LAN) is a computer network that spans a relatively small area. Most often, a LAN is confined to a single room, building or group of buildings, however, one LAN can be connected to other LANs over any distance via telephone lines and radio waves. A system of LANs connected in this way is called a wide-area network (WAN). The difference between a LAN and WAN is that the wide-area network spans a relatively large geographical area. Typically, a WAN consists of two or more local-area networks (LANs) and are often connected through public networks. By Vangie Beal Nodes on a LAN Most LANs connect workstations and personal computers. Each node (individual computer) in a LAN has its own CPU with which it executes programs, but it also is able to access data and devices anywhere on the LAN. This means that many users can share expensive devices, such as laser printers, as well as data. Users can also use the LAN to communicate with each other, by sending email or engaging in chat sessions. LANs are capable of transmitting data at very fast rates, much faster than data can be transmitted over a telephone line; but the distances are limited and there is also a limit on the number of computers that can be attached to a single LAN. Recommended Reading: Webopedia's Network Topology Study Guide. • • • Types of Local-Area Networks (LANs) There are many different types of LANs, with Ethernets being the most common for PCs. Most Apple Macintosh networks are based on Apple's AppleTalk network system, which is built into Macintosh computers. The following characteristics differentiate one LAN from another: Topology: The geometric arrangement of devices on the network. For example, devices can be arranged in a ring or in a straight line. Protocols: The rules and encoding specifications for sending data. The protocols also determine whether the network uses a peer-to-peer or client/server architecture. Media: Devices can be connected by twisted-pair wire, coaxial cables, or fiber optic cables. Some networks do without connecting media altogether, communicating instead via radio waves. 10 | P a g e ADSL router Asymmetric digital subscriber line (ADSL) is a type of DSL broadband communications technology used for connecting to the Internet. ADSL allows more data to be sent over existing copper telephone lines (POTS), when compared to traditional modem lines. A special filter, called a microfilter, is installed on a subscriber's telephone line to allow both ADSL and regular voice (telephone) services to be used at the same time. ADSL requires a special ADSL modem and subscribers must be in close geographical locations to the provider's central office to receive ADSL service. Typically this distance is within a radius of 2 to 2.5 miles. ADSL supports data rates of from 1.5 to 9 Mbps when receiving data (known as the downstream rate) and from 16 to 640 Kbps when sending data (known as the upstream rate).( By Vangie Beal) L2 switch A layer 2 switch is a type of network switch or device that works on the data link layer (OSI Layer 2) and utilizes MAC Address to determine the path through where the frames are to be forwarded. It uses hardware based switching techniques to connect and transmit data in a local area network (LAN). Routers Routers are used to connect networks together and route packets of data from one network to another. Routers, by default, break up a broadcast domain. A router creates & maintains a table of the available routers and their conditions and use this information along with distance and cost algorithms to determine the best route for a given packet. Typically, a packet may travel through number of network points with routers before arriving at its destination. 11 | P a g e c)What type of network should be deployed in the SUB-B and what equipment should be installed (describe your answer)?? Access point(wired/wireless) An access point is a device, such as a wireless router, that allows wireless devices to connect to a network. Most access points have built-in routers, while others must be connected to a router in order to provide network access. In either case, access points are typically hardwired to other devices, such as network switches or broadband modems. Access points can be found in many places, including houses, businesses, and public locations. In most houses, the access point is a wireless router, which is connected to a DSL or cable modem. However, some modems may include wireless capabilities, making the modem itself the access point. Large businesses often provide several access points, which allows employees to wirelessly connect to a central network from a wide range of locations. Public access points can be found in stores, coffee shops, restaurants, libraries, and other locations. Some cities provide public access points in the form of wireless transmitters that are connected to streetlights, signs, and other public objects. While access points typically provide wireless access to the Internet, some are intended only to provide access to a closed network. For example, a business may provide secure access points to its employees so they can wirelessly access files from a network server. Also, most access points provide Wi-Fi access, but it is possible for an access point to refer to a Bluetooth device or other type of wireless connection. However, the purpose of most access points is to provide Internet access to connected users. The term "access point" is often used synonymously with base station, though base stations are technically only Wi-Fi devices. It may also be abbreviated AP or WAP (for wireless access point). However, WAP is not as commonly used as AP since WAP is the standard acronym for Wireless Access Protocol. Switch Layer 2 switching (or Data Link layer switching) is the process of using devices’ MAC addresses on a LAN to segment a network. Switches and bridges are used for Layer 2 switching. They break up one large collision domain into multiple smaller ones. In a typical LAN, all hosts are connected to one central device. In the past, the device was usually a hub. But hubs had many disadvantages, such as not being aware of traffic that passes through them, creating one large collision domain, etc. To overcome some of the problems with hubs, the bridges were created. They were better than hubs because they created multiple collision domains, but they had limited number of ports. Finally, switches were created and are still widely used today. Switches have more ports than bridges, can inspect incoming traffic and make forwarding decisions accordingly. Each port on a switch is a separate collision domain. 12 | P a g e Firewall A firewall is a type of cybersecurity tool that is used to filter traffic on a network. Firewalls can be used to separate network nodes from external traffic sources, internal traffic sources, or even specific applications. Firewalls can be software, hardware, or cloud-based, with each type of firewall having its own unique pros and cons. The primary goal of a firewall is to block malicious traffic requests and data packets while allowing legitimate traffic through. Firewall types can be divided into several different categories based on their general structure and method of operation. Here are eight types of firewall: • • • • • • • • Packet-filtering firewalls Circuit-level gateways Stateful inspection firewalls Application-level gateways (a.k.a. proxy firewalls) Next-gen firewalls Software firewalls Hardware firewalls Cloud firewalls 13 | P a g e d) What type of network connections should be used to link the buildings together and where and how should the College’s Internet connection be made? As per the given situation, fiber association is the ideal and viable answer for interconnect fundamental structure and SUB-A structure when separations surpass 100m, which is the time when Ethernet cabling starts to endure debasement. Running fiber cabling gives a far more prominent separation ability. Where there is underground ducting running between the structures, rather than 'pulling' links through, arrange architects will introduce the fiber utilizing their 'link blowing' or ' link streaming' machines. If no such ducting exists, at that point overhead cabling should be considered. Main Building to SUB-B Building A site-to-site VPN allows offices in multiple fixed locations to establish secure connections with each other over a public network such as the internet. Site-to-site VPN extends the company's network, making computer resources from one location available to employees at other locations. An example of a company that needs a site-to-site VPN is a growing corporation with dozens of branch offices around the world. There are two types of site-to-site VPNs: • Intranet-based — If a company has one or more remote locations that they wish to join in a single private network, they can create an intranet VPN to connect each separate LAN to a single WAN. • Extranet-based — When a company has a close relationship with another company (such as a partner, supplier or customer), it can build an extranet VPN that connects those 14 | P a g e companies' LANs. This extranet VPN allows the companies to work together in a secure, shared network environment while preventing access to their separate intranets. Even though the purpose of a site-to-site VPN is different from that of a remote-access VPN, it could use some of the same software and equipment. Ideally, though, a site-to-site VPN should eliminate the need for each computer to run VPN client software as if it were on a remote-access VPN. Dedicated VPN client equipment, described later in this article, can accomplish this goal in a site-to-site VPN. Now that you know the two types of VPNs, let's look at how your data is kept secure as it travels across a VPN. Internet connectivity Will associate web passage to head office firewall by means of Site-to – website VPN Tunnel and control traffic from firewall and Router. Main Building to SUB-A here are many complex fiber optic data transmission systems being employed as per the application requirement. The easiest way to understand a fiber optic link system is by discussing simple point to point fiber optic links. A P2P or point to point fiber optic data link consists of an optical transmitter to transmit the data, optical fiber as the medium, and an optical receiver. There will be splicing points in between the fiber optic link system, there will be fiber optic connectors at transmitter and receiver points. A full duplex fiber optic link is the commonly employed fiber optic application. Such fiber optic links consist of two simple P2P fiber optic links. Duplex fiber optic links transmit in opposite directions between the input and output equipments. Duplex fiber optic links can be configured 15 | P a g e using a single fiber. In such cases, fiber optic splitters are used at each end to couple the transmitted optical signal onto the fiber and receive the optical signal to the detector. Split down to single units, all fiber optic link systems are a sets of P2P fiber optic links. Different fiber optic link system topologies come from the different ways that P2P fiber optic links can be connected between equipments. Note that the word fiber optic topology refers to the configuration of various equipments and the fiber optic components interconnecting them. Equipments used in a fiber optic link system may be computers, workstations, consoles and such related equipments. P2P or Point to point fiber optic links are connected to produce different type of fiber optic link systems. Some of the fiber optic link systems produced with point to point link includes linear bus, ring topology, star topology and tree topology. Thus we can see that Point to point fiber optic links are the basic building units of all fiber optic systems. A fiber-optic cable, also known as an optical-fiber cable, is an assembly similar to an electrical cable, but containing one or more optical fibers that are used to carry light. The optical fiber elements are typically individually coated with plastic layers and contained in a protective tube suitable for the environment where the cable will be deployed. Different types of cable[1] are used for different applications, for example, long distance telecommunication, or providing a high-speed data connection between different parts of a building. Internet connectivity Will interface web door to head office firewall by means of Point to Point Fiber Optic underground conduit Cable Tunnel and control web traffic from firewall and switch. 16 | P a g e Part 2 1. An analysis of the network design models and how they contribute to the design of a scalable and reliable network. Totally suitable versatile and dependable system configuration is significant for entrepreneurs. A little system is regularly more helpless to infections and spyware than bigger systems, because of programming vulnerabilities. Modern programming worked to deal with these dangers is similarly as significant as having top notch steering frameworks and equipment. Realizing how to structure a PC arrange isn't in every case simple. Everything from the situation of the switch in a sign chain to the quantity of PCs in the system will influence the progression of data inside an association. • • • • • • • • • Setting up a system for the workplace requires the accompanying: A secure Internet association from the Internet Service Provider (ISP) A switch with a fast Internet association A modem Firewall capacities One or more switches (enables PCs to connection to each other over an inward system) Phone line/link/fiber optic connecting (wired or remote) Ethernet center points Management and security programming For little systems, the essential rationale pursues that the ISP sends data to the modem, which associates with the switch, which at that point interfaces the private company work areas and workstations either wired or remotely. Select a suitable topology to configure nodes together: • BUS Topology Bus topology is a network type in which every computer and network device is connected to single cable. When it has exactly two endpoints, then it is called Linear Bus topology. 17 | P a g e • RING Topology It is called ring topology because it forms a ring as each computer is connected to another computer, with the last one connected to the first. Exactly two neighbours for each device. • STAR Topology In this type of topology all the computers are connected to a single hub through a cable. This hub is the central node and all others nodes are connected to the central node. 18 | P a g e • MESH Topology It is a point-to-point connection to other nodes or devices. All the network nodes are connected to each other. Mesh has n(n-1)/2 physical channels to link n devices. • TREE Topology It has a root node and all other nodes are connected to it forming a hierarchy. It is also called hierarchical topology. It should at least have three levels to the hierarchy. 19 | P a g e • HYBRID Topology It is two different types of topologies which is a mixture of two or more topologies. For example if in an office in one department ring topology is used and in another star topology is used, connecting these topologies will result in Hybrid Topology (ring topology and star topology). 20 | P a g e Choose a network design type which is suitable to organizations behavior 1. Personal Area Network (PAN) The smallest and most basic type of network, a PAN is made up of a wireless modem, a computer or two, phones, printers, tablets, etc., and revolves around one person in one building. These types of networks are typically found in small offices or residences, and are managed by one person or organization from a single device. 2. Local Area Network (LAN) We’re confident that you’ve heard of these types of networks before – LANs are the most frequently discussed networks, one of the most common, one of the most original and one of the simplest types of networks. LANs connect groups of computers and low-voltage devices together across short distances (within a building or between a group of two or three buildings in close proximity to each other) to share information and resources. Enterprises typically manage and maintain LANs. Using routers, LANs can connect to wide area networks (WANs, explained below) to rapidly and safely transfer data. 3. Wireless Local Area Network (WLAN) Functioning like a LAN, WLANs make use of wireless network technology, such as WiFi. Typically seen in the same types of applications as LANs, these types of networks don’t require that devices rely on physical cables to connect to the network. 4. Campus Area Network (CAN) Larger than LANs, but smaller than metropolitan area networks (MANs, explained below), these types of networks are typically seen in universities, large K-12 school districts or small businesses. They can be spread across several buildings that are fairly close to each other so users can share resources. 5. Metropolitan Area Network (MAN) These types of networks are larger than LANs but smaller than WANs – and incorporate elements from both types of networks. MANs span an entire geographic area (typically a town or city, but sometimes a campus). Ownership and maintenance is handled by either a single person or company (a local council, a large company, etc.). 21 | P a g e 6. Wide Area Network (WAN) Slightly more complex than a LAN, a WAN connects computers together across longer physical distances. This allows computers and low-voltage devices to be remotely connected to each other over one large network to communicate even when they’re miles apart. The Internet is the most basic example of a WAN, connecting all computers together around the world. Because of a WAN’s vast reach, it is typically owned and maintained by multiple administrators or the public. 7. Storage-Area Network (SAN) As a dedicated high-speed network that connects shared pools of storage devices to several servers, these types of networks don’t rely on a LAN or WAN. Instead, they move storage resources away from the network and place them into their own high-performance network. SANs can be accessed in the same fashion as a drive attached to a server. Types of storage-area networks include converged, virtual and unified SANs. 8. System-Area Network (also known as SAN) This term is fairly new within the past two decades. It is used to explain a relatively local network that is designed to provide high-speed connection in server-to-server applications (cluster environments), storage area networks (called “SANs” as well) and processor-toprocessor applications. The computers connected on a SAN operate as a single system at very high speeds. 9. Passive Optical Local Area Network (POLAN) As an alternative to traditional switch-based Ethernet LANs, POLAN technology can be integrated into structured cabling to overcome concerns about supporting traditional Ethernet protocols and network applications such as PoE (Power over Ethernet). A point-to-multipoint LAN architecture, POLAN uses optical splitters to split an optical signal from one strand of singlemode optical fiber into multiple signals to serve users and devices. 10. Enterprise Private Network (EPN) These types of networks are built and owned by businesses that want to securely connect its various locations to share computer resources. 22 | P a g e 11. Virtual Private Network (VPN) By extending a private network across the Internet, a VPN lets its users send and receive data as if their devices were connected to the private network – even if they’re not. Through a virtual point-to-point connection, users can access a private network remotely. The recurrence of Wi-Fi associations in business settings has been on the ascent. Emergency clinics, grounds, corporate workplaces, and even retail outlets depend on PC systems administration to give helpful data to their representatives and clients consistently. According to this announcement, Wi-Fi association is significant for Telco and Networking Solutions. Hierarchical Network Design This topic discusses the three functional layers of the hierarchical network model: the access, distribution, and core layers. Network Hierarchy Early networks were deployed in a flat topology as shown Flat Switched Network Hubs and switches were added as more devices needed to be connected. A flat network design provided little opportunity to control broadcasts or to filter undesirable traffic. As more devices and applications were added to a flat network, response times degraded, making the network unusable. A better network design approach was needed. For this reason, organizations now use a hierarchical network design as shown 23 | P a g e Hierarchical Network A hierarchical network design involves dividing the network into discrete layers. Each layer, or tier, in the hierarchy provides specific functions that define its role within the overall network. This helps the network designer and architect to optimize and select the right network hardware, software, and features to perform specific roles for that network layer. Hierarchical models apply to both LAN and WAN design. The benefit of dividing a flat network into smaller, more manageable blocks is that local traffic remains local. Only traffic that is destined for other networks is moved to a higher layer. For example, in the flat network has now been divided into three separate broadcast domains. A typical enterprise hierarchical LAN campus network design includes the following three layers: • • • Access layer: Provides workgroup/user access to the network Distribution layer: Provides policy-based connectivity and controls the boundary between the access and core layers Core layer: Provides fast transport between distribution switches within the enterprise campus Another sample three-layer hierarchical network design is displayed. Notice that each building is using the same hierarchical network model that includes the access, distribution, and core layers. 24 | P a g e Multi Building Enterprise Network Design NOTE There are no absolute rules for the way a campus network is physically built. While it is true that many campus networks are constructed using three physical tiers of switches, this is not a strict requirement. In a smaller campus, the network might have two tiers of switches in which the core and distribution elements are combined in one physical switch. This is referred to as a collapsed core design. 25 | P a g e 2. A detailed explanation of Local Area Network redundancy concepts, network features, such as bandwidth and load and their related issues. The explanations should contain the possible solutions provided at Layer 2 and 3 of the OSI Model. Network redundancy is a key to maintaining network reliability. Multiple physical links between devices provide redundant paths. The network can then continue to operate when a single link or port has failed. Redundant links can also share the traffic load and increase capacity. Multiple paths need to be managed so that Layer 2 loops are not created. The best paths are chosen, and an alternate path is immediately available should a primary path fail. The Spanning Tree Protocols are used to manage Layer 2 redundancy. Redundant devices, such as multilayer switches or routers, provide the capability for a client to use an alternate default gateway should the primary default gateway fail. A client can now have multiple paths to more than one possible default gateway. First Hop Redundancy Protocols are used to manage how a client is assigned a default gateway, and to be able to use an alternate default gateway should the primary default gateway fail. (cisco) What does Network Redundancy mean? Network redundancy is a process through which additional or alternate instances of network devices, equipment and communication mediums are installed within network infrastructure. It is a method for ensuring network availability in case of a network device or path failure and unavailability. As such, it provides a means of network failover. Network redundancy is primarily implemented in enterprise network infrastructure to provide a redundant source of network communications. It serves as a backup mechanism for quickly swapping network operations onto redundant infrastructure in the event of unplanned network outages. Typically, network redundancy is achieved through the addition of alternate network paths, which are implemented through redundant standby routers and switches. When the primary path is unavailable, the alternate path can be instantly deployed to ensure minimal downtime and continuity of network services. https://www.techopedia.com/definition/29305/network-redundancy LAN redundancy concepts Spanning Tree Protocol (STP) The Spanning Tree Protocol (STP) is a network protocol that builds a loop-free logical topology for Ethernet networks. The basic function of STP is to prevent bridge loops and the broadcast radiation that results from them. Spanning tree also allows a network design to include backup links to provide fault tolerance if an active link fails. 26 | P a g e As the name suggests, STP creates a spanning tree within a network of connected layer2 bridges, and disables those links that are not part of the spanning tree, leaving a single active path between any two network nodes. STP is based on an algorithm that was invented by Radia Perlman while she was working for Digital Equipment Corporation. In 2001, the IEEE introduced Rapid Spanning Tree Protocol (RSTP) as 802.1w. RSTP provides significantly faster recovery in response to network changes or failures, introducing new convergence behaviors and bridge port roles to do this. RSTP was designed to be backwardscompatible with standard STP. STP was originally standardized as IEEE 802.1D but the functionality of spanning tree (802.1D), rapid spanning tree (802.1w), and multiple spanning tree (802.1s) has since been incorporated into IEEE 802.1Q-2014. Purpose of Spanning Tree STP provides the mechanism to have redundant links at Layer 2 while avoiding the potential for loops and MAC address database instability. 27 | P a g e List of Spanning Tree Protocols Several varieties of spanning tree protocols have emerged since the original IEEE 802.1D. The varieties of spanning tree protocols include • • • • • • STP: This is the original IEEE 802.1D version (802.1D-1998 and earlier) that provides a loop-free topology in a network with redundant links. Common Spanning Tree (CST) assumes one spanning tree instance for the entire bridged network, regardless of the number of VLANs. PVST+: This is a Cisco enhancement of STP that provides a separate 802.1D spanning tree instance for each VLAN configured in the network. The separate instance supports PortFast, UplinkFast, BackboneFast, BPDU guard, BPDU filter, root guard, and loop guard. 802.1D-2004: This is an updated version of the STP standard, incorporating IEEE 802.1w. Rapid Spanning Tree Protocol (RSTP) or IEEE 802.1w: This is an evolution of STP that provides faster convergence than STP. Rapid PVST+: This is a Cisco enhancement of RSTP that uses PVST+. Rapid PVST+ provides a separate instance of 802.1w per VLAN. The separate instance supports PortFast, BPDU guard, BPDU filter, root guard, and loop guard. Multiple Spanning Tree Protocol (MSTP): This is an IEEE standard inspired by the earlier Cisco proprietary Multiple Instance STP (MISTP) implementation. MSTP maps multiple VLANs into the same spanning tree instance. The Cisco implementation of MSTP is MST, which provides up to 16 instances of RSTP and combines many VLANs with the same physical and logical topology into a common RSTP instance. Each instance supports PortFast, BPDU guard, BPDU filter, root guard, and loop guard. Redundancy at OSI Layers 1 and 2 Redundancy at OSI Layers 1 and 2. The three-tier hierarchical network design that uses core, distribution, and access layers with redundancy attempts to eliminate a single point of failure on the network. Multiple cabled paths between switches provide physical redundancy in a switched network. This improves the reliability and availability of the network. Having alternate physical paths for data to traverse the network makes it possible for users to access network resources, despite path disruption. The following steps explain how redundancy works in the topology shown. 1. PC1 is communicating with PC4 over a redundant network topology. 2. When the network link between S1 and S2 is disrupted, the path between PC1 and PC4 is automatically adjusted to compensate for the disruption. 3. When the network connection between S1 and S2 is restored, the path is then readjusted to route traffic directly from S2 to S1 to get to PC4. 28 | P a g e For many organizations, the availability of the network is essential to supporting business needs; therefore, the network infrastructure design is a critical business element. Path redundancy is a solution for providing the necessary availability of multiple network services by eliminating the possibility of a single point of failure. Redundancy is an important part of hierarchical design for preventing disruption of network services to users. Redundant networks require adding physical paths, but logical redundancy must also be part of the design. However, redundant paths in a switched Ethernet network can cause both physical and logical Layer 2 loops. Logical Layer 2 loops can occur because of the natural operation of switches, specifically, the learning and forwarding process. When multiple paths exist between two devices on a network, and there is no spanning tree implementation on the switches, a Layer 2 loop occurs. A Layer 2 loop can result in three primary issues: MAC database instability: Instability in the content of the MAC address table results from copies of the same frame being received on different ports of the switch. Data forwarding can be impaired when the switch consumes the resources that are coping with instability in the MAC address table. Broadcast storms: Without some loop-avoidance process, each switch can flood broadcasts endlessly. This situation is commonly called a broadcast storm. Multiple frame transmission: Multiple copies of unicast frames can be delivered to destination stations. Many protocols expect to receive only a single copy of each transmission. Multiple copies of the same frame can cause unrecoverable errors. 29 | P a g e Issues with Layer 1 Redundancy: MAC Database Instability Ethernet frames do not have a time to live (TTL) attribute, like IP packets. As a result, if there is no mechanism enabled to block continued propagation of these frames on a switched network, they continue to propagate between switches endlessly, or until a link is disrupted and breaks the loop. This continued propagation between switches can result in MAC database instability. This can occur because of broadcast frames forwarding. Broadcast frames are forwarded out all switch ports, except the original ingress port. This ensures that all devices in a broadcast domain are able to receive the frame. If there is more than one path for the frame to be forwarded out, an endless loop can result. When a loop occurs, it is possible for the MAC address table on a switch to constantly change with the updates from the broadcast frames, resulting in MAC database instability. The following steps demonstrate the MAC database instability issue. shows a snapshot during Step 4. 1. PC1 sends out a broadcast frame to S2. S2 receives the broadcast frame on F0/11. When S2 receives the broadcast frame, it updates its MAC address table to record that PC1 is available on port F0/11. 2. Because it is a broadcast frame, S2 forwards the frame out all ports, including Trunk1 and Trunk2. When the broadcast frame arrives at S3 and S1, they update their MAC address tables to indicate that PC1 is available out port F0/1 on S1 and out port F0/2 on S3. 3. Because it is a broadcast frame, S3 and S1 forward the frame out all ports, except the ingress port. S3 sends the broadcast frame from PC1 to S1. S1 sends the broadcast frame from PC1 to S3. Each switch updates its MAC address table with the incorrect port for PC1. 4. Each switch again forwards the broadcast frame out all of its ports, except the ingress port, resulting in both switches forwarding the frame to S2. 30 | P a g e 5. When S2 receives the broadcast frames from S3 and S1, the MAC address table is updated again, this time with the last entry received from the other two switches. This process repeats repeatedly until the loop is broken by physically disconnecting the connections causing the loop or powering down one of the switches in the loop. This creates a high CPU load on all switches caught in the loop. Because the same frames are constantly being forwarded back and forth between all switches in the loop, the CPU of the switch must process a lot of data. This slows down performance on the switch when legitimate traffic arrives. A host caught in a network loop is not accessible to other hosts on the network. Additionally, because of the constant changes in the MAC address table, the switch does not know out of which port to forward unicast frames. In the previous example, the switches will have the incorrect ports listed for PC1. Any unicast frame destined for PC1 loops around the network, just as the broadcast frames do. More and more frames looping around the network eventually create a broadcast storm. Issues with Layer 1 Redundancy: Broadcast Storms A broadcast storm occurs when there are so many broadcast frames caught in a Layer 2 loop that all available bandwidth is consumed. Consequently, no bandwidth is available for legitimate traffic and the network becomes unavailable for data communication. This is an effective denial of service. A broadcast storm is inevitable on a looped network. As more devices send broadcasts over the network, more traffic is caught within the loop, consuming resources. This eventually creates a broadcast storm that causes the network to fail. There are other consequences of broadcast storms. Because broadcast traffic is forwarded out every port on a switch, all connected devices have to process all broadcast traffic that is being flooded endlessly around the looped network. This can cause the end device to malfunction because of the high processing requirements for sustaining such a high traffic load on the NIC. The following steps demonstrate the broadcast storm issue. the result during Step 6. 1. PC1 sends a broadcast frame out onto the looped network. 2. The broadcast frame loops between all the interconnected switches on the network. 3. PC4 also sends a broadcast frame out on to the looped network. 4. The PC4 broadcast frame also gets caught in the loop between all the interconnected switches, just like the PC1 broadcast frame. 5. As more devices send broadcasts over the network, more traffic is caught within the loop, consuming resources. This eventually creates a broadcast storm that causes the network to fail. 31 | P a g e 6. When the network is fully saturated with broadcast traffic that is looping between the switches, new traffic is discarded by the switch because it is unable to process it. In Figure 2-3, S2 is now discarding additional frames. Because devices connected to a network are regularly sending out broadcast frames, such as ARP requests, a broadcast storm can develop in seconds. As a result, when a loop is created, the switched network is quickly brought down. Issues with Layer 1 Redundancy: Duplicate Unicast Frames Broadcast frames are not the only type of frames that are affected by loops. Unicast frames sent onto a looped network can result in duplicate frames arriving at the destination device. The following steps demonstrate the duplicate unicast frames issue. a snapshot during Step 5 and Step 6. 1. PC1 sends a unicast frame destined for PC4. 2. S2 does not have an entry for PC4 in its MAC table, so it floods the unicast frame out all switch ports in an attempt to find PC4. 3. The frame arrives at switches S1 and S3. 4. S1 does have a MAC address entry for PC4, so it forwards the frame out to PC4. 5. S3 also has an entry in its MAC address table for PC4, so it forwards the unicast frame out Trunk3 to S1. 6. S1 receives the duplicate frame and forwards the frame out to PC4. 7. PC4 has now received the same frame twice. 32 | P a g e RSTP The 802.1D Spanning Tree Protocol (STP) standard was designed at a time when the recovery of connectivity after an outage within a minute or so was considered adequate performance. With the advent of Layer 3 switching in LAN environments, bridging now competes with routed solutions where protocols, such as Open Shortest Path First (OSPF) and Enhanced Interior Gateway Routing Protocol (EIGRP), are able to provide an alternate path in less time. Cisco enhanced the original 802.1D specification with features such as Uplink Fast, Backbone Fast, and Port Fast to speed up the convergence time of a bridged network. The drawback is that these mechanisms are proprietary and need additional configuration. Rapid Spanning Tree Protocol (RSTP; IEEE 802.1w) can be seen as an evolution of the 802.1D standard more than a revolution. The 802.1D terminology remains primarily the same. Most parameters have been left unchanged so users familiar with 802.1D can rapidly configure the new protocol comfortably. In most cases, RSTP performs better than proprietary extensions of Cisco without any additional configuration. 802.1w can also revert back to 802.1D in order to interoperate with legacy bridges on a per-port basis. This drops the benefits it introduces. The new edition of the 802.1D standard, IEEE 802.1D-2004, incorporates IEEE 802.1t-2001 and IEEE 802.1w standards. 33 | P a g e First Hop Redundancy Protocol (FHRP) IP routing redundancy is designed to allow for transparent fail-over at the first-hop IP router. Both HSRP and VRRP enable two or more devices to work together in a group, sharing a single IP address, the virtual IP address. The virtual IP address is configured in each end user's workstation as a default gateway address and is cached in the host's Address Resolution Protocol (ARP) cache. In an HSRP or VRRP group, one router is elected to handle all requests sent to the virtual IP address. With HSRP, this is the active router. An HSRP group has one active router, at least one standby router, and perhaps many listening routers. A VRRP group has one master router and one or more backup routers. MRP - Media Redundancy Protocol MRP is an open standard for Ring topologies in industrial networks enabling faster recovery times in switch loop scenarios (10ms or better) than spanning tree protocols. In a ring network each Ethernet switch is connected to two other switches forming a ring. The benefit is that each switch has a redundant connection (links) into the network and may also provide a more cost-effective cabling infrastructure than using an aggregation switch at a central location. For these reasons, ring topology networks are popular within industrial infrastructures. The disadvantage in forming a ring network using switches is that using this topology introduces a “switch loop” condition. The loop creates broadcast storms as broadcasts and multicasts are 34 | P a g e forwarded by switches out of every port. The switch or switches will repeatedly rebroadcast the broadcast messages, flooding the network. Since the Layer 2 header does not support a Time to Live (TTL) value, if a frame is sent into a looped topology, it can loop forever severely consuming all available bandwidth on the loop making the network unusable. One resolution to this problem is to simply break the loop somewhere in the ring. Spanning Tree protocols such as RSTP were developed to detect these switch loop conditions and then intelligently reconfigure the network to provide this break, eliminating the switch loop. Also, if anything happens in the network, a topology change notification is sent out to create a different safe path. Although effective enough for many networks, Spanning Tree protocols take a relatively long time for this re-convergence to complete. RSTP, as an example, can take a few seconds for the network to recover which is not good enough for mission critical industrial Ethernet applications. Specialized Ring protocols have been designed for mission critical industrial networks operating in a ring topology providing a recovery time of 10ms or better, significantly quicker than RSTP. Media Redundancy Protocol (MRP) is a common standards-based protocol (IEC 624392) which provides this capability. The way MRP works is that a “Ring Manager” switch will drop (block) all packet forwarding on one of its two designated ring ports (Fig 2), in effect “breaking” the switch loop. All the traffic from devices connected to all the switches in the loop will still have a path to each other, with redundant links, but without the harmful switch loop. 35 | P a g e The Ring Manager is in constant communication with its MRP peers. If one of the two links on any of the other ring nodes detects a failure, the client node will send a message to the Ring Manager which will then unblock its blocked port enabling communication again between all of the switches. Special poll packets which can traverse blocked ports, are sent around the ring and monitored by the Ring Manager. If the Ring Manager does not see its poll packets come back around the ring, it knows that one of the switch nodes, or even a switch/hub that does not support MRP, has failed. The Ring Manager will then unblock its port and resume the forwarding of packets on both of its ring ports. All devices on switches, except the failed node, will again have a path to each other. During these topology change events, the various switches on the ring will be informed to clear the MAC tables that they have built-up so they can re-learn the port to destination MAC addresses of the devices connected to the ring. Given the intelligence behind the protocol, it is strongly recommended that each switch node in the ring supports MRP. 36 | P a g e 3. Provide a detailed account of how redundancy protocols support scalable networks. What should be considered As a basis for functional and purposeful network, design is of paramount importance and directly contributes to the successful operation or failure of the network. For a well-designed network following criteria must be met: • • • Designing the network with resiliency in mind Using technology to identify and eliminate single points of failure Having processes in place to reduce the risk of human error In addition to these three basic criteria that must be considered when building an efficient network and which must complement each other, one needs to take into account elements that will ensure the successful implementation of the design. • • • • • • • Physical infrastructure Topological/protocol hierarchy Scaling and Redundancy Addressing aggregation (IGP and BGP) Policy implementation (core/edge) Management/maintenance/operations Cost There are different ways in which network can be designed. The network can be designed on the basis of three-layer hierarchical model or collapsed core model or any other model, which is now considered best practice. However, it should be remembered that no matter which model is used, one needs to take into account the specificities of the organization for which the network is designed for. DESIGN In the case of Small and Medium Enterprise networks one can choose a collapsed core design, slightly altered using stackable switches instead of two separate core switches. In this case, stackable switches can provide maximum redundancy in the network. In the case of smaller networks generally it is not justified to use the full three-layer hierarchical model with the access, distribution and core layers. The reasons for this are the additional costs for the distribution layer equipment that generally is not required, additional network complexity, higher maintenance costs and so on. Since there are no distribution layers there is fewer points of potential failures in the network. Also, if the funds intended for the distribution layer are re-directed to other equipment, organization can get better and more reliable equipment which in turn contributes to the resilience of the network. 37 | P a g e In order to make core of the network redundant and fast, perhaps the best solution is the use of stackable switches which has the benefit of eliminating STP protocol. If stackable switches are used as L3 devices FHRP can also be eliminated with maintaining adequate level of reliability. Although it is possible and even simpler and cheaper to use L3 stackable switches as routers this is not a good solution. The reason is that besides routing the traffic one need to have various security elements implemented in the network, such as filtering traffic based on UDP / TCP ports or applications, anti-virus protection and so on. For the purposes of security, one should certainly use Firewalls, and today more and more so-called Next-Generation Firewalls. In this case it would be better to use two firewalls and configure them to work together using one of the FHRP protocol or if the budget permits configure them to work in HA (High Availability) mode, and thus ensure minimal downtime in the event of failure of one of the firewalls or links to the Internet. Ultimately the topology for this network will resemble a star topology, but without the single points of failure in the core network. Also, to keep the benefit of collapsed core design every VLAN should be restricted to one access layer switch stack. For VLAN communication all the VLANs can be terminated at the core stack but this can be complex because routing has to be used for communication with the rest of the network and the Internet. Another simpler solution is to terminate all the VLANs at the firewall and have all the benefits of traffic filtering to have more secure network. If firewalls are used in HA mode than it is even simpler and more reliable solution, but as it is mentioned before it is more expensive because this kind of feature is generally licensed or comes with higher models of firewalls. TECHNOLOGIES USED FOR REDUNDANCY Technologies that can be used to provide redundancy in the network are different and depending on the combination of these technologies’ different convergence times after a failure of a link or device will be achieved. When choosing the technology, one needs to be careful, because after implementation, it can be very difficult and dangerous for the company’s business to make changes in the production network. Redundancy in the network can be implemented using a combination of the four technologies that will be briefly described below in this document. These are STP (Spanning Tree Protocol), Link Aggregation, FHRP (First Hop Redundancy Protocols) and switch stacking. STP Today it is pointless to talk about the original IEEE 802.1D STP version or CST (Common Spanning Tree) when talking about network redundancy. The reason is very slow convergence after failure of a link that takes 30-50 seconds, depending on the size of network and it can even cause problems in the convergence. In the case of smaller networks CST would also do its part, but it would be quite inefficient. For larger networks with more complex patterns of network traffic and applications sensitive to disruption of communication CST should be avoided. In addition to the slow convergence problem is also the fact that the CST does not recognize 38 | P a g e VLANs, in fact CST treat the entire network as one VLAN and thus a large number of links in the network is blocked which is certainly not something one would want in a network. The problem of slow convergence can be solved by implementing the IEEE’s RSTP (Rapid STP), but less than optimal forwarding of traffic remains as RSTP still builds one STP tree for the entire network. A better version of STP is Cisco PVST + (Per VLAN Spanning Tree Plus), which has the same slow convergence time as STP, but enables better use of links in the network. This is because of the ability to share traffic according to VLANs by making a link that is blocked for one VLAN, to be in forwarding state for another VLAN. This is also useful in the event of link failure, because in this case negative impact on the network is much smaller than in the case when STP is used. Since the convergence is per VLAN link failure affects only VLANs whose forwarding link has failed. In addition, one can configure protection against network attacks using STP BPDU Filter, Root Guard, BPDU guard, loop guard functionality as well as port fast option allowing us to have stable STP topology, which is essential for a functional network. These mechanisms are beyond the scope of this paper but should be considered when implementing PVST+. The problem that can occur is when there is many VLANs configured on a switch. In this situation switch CPU could be overloaded which can cause other problems in the network even inability to converge. If the goal is to have short convergence times, and at the same time have more STP instances Cisco’s PVRST + (Per VLAN Rapid Spanning Tree Plus) can be used which is sort of a combination of IEEEs RSTP and Cisco’s PVST + protocol. PVRST + allows us to have a short convergence and the possibility of an independent convergence of the network for each VLAN, which allows us more flexibility. With all the additional functionality that are listed under PVST + this would be a good choice for a stable STP topology. The problem that can occur is also linked to the number of instances of STP. Because PVRST + supports a separate instance of STP for each VLAN, and also has shorter convergence time, the CPU is significantly burdened, and switch can be easily led to overloading. Recommendations for implementation of PVRST + is never to configure more VLANs than required in a network, otherwise it could lead to 100% CPU load and ultimately bring down the network. However, if one want redundancy based on STP and one have lot of VLANs (hundreds), the solution is the use of IEEEs MST protocol (Multiple Spanning Tree) that allows single instance of spanning tree protocol for a group of VLANs which ultimately results in fewer instances of spanning tree protocol in a network and still have the ability to use all links. Though it may seem that STP is something that should be used in a network, sometimes it is not the case. STP should not be excluded completely, but redundancy in a network should not be based on STP. Depending on the complexity of the network STP can be a valid solution, but for example, in data center networks STP should not be used at all. Some of the reasons are inefficient use of links and slow convergence for such environments with very complex topologies that are 39 | P a g e difficult to troubleshoot. STP could be used as failback mechanism in the event of a loop, but everything should be done in order to prevent the occurrence of loops. Also one should implement redundancy in the network using other mechanisms like switch stacking and link aggregation. LINK AGGREGATION Large amounts of traffic that is circulating through the network is not uncommon even in smaller networks, and one way to increase throughput of the network is to use link aggregation. Although it seems that the main benefit of link aggregation is higher bandwidth, the primary thing that is accomplished is in fact link redundancy between switches in a network. Link aggregation can also be used for computers or servers (NIC teaming), which certainly adds to the total resilience of the network. There are different ways of performing link aggregation, some of which are standard, such as LACP (Link Aggregation Control Protocol), and some are owned by a variety of manufacturers such as Cisco, Juniper, Avaya, Huawei etc. No matter which protocol is used, one needs to know the capabilities of the solution and whether aggregated links will be able to take the burden of network traffic in the event of failure of critical elements such as links or devices. If aggregated link has insufficient bandwidth with respect to the traffic it does not fulfill the purpose for which it was designed, because in case of failure of the main link the impact will be similar to a situation where there is no link redundancy. This effect is amplified if there is no QoS (Quality of Service) mechanisms in the network which means no prioritization of traffic, which is especially problematic for real-time applications and essential communications. GATEWAY REDUNDANCY The gateway is one of the most important elements of any network and therefore it is necessary to ensure maximum availability of such devices. A way in which availability of the Gateway is ensured is to make it redundant, which means that there are at least two devices which simultaneously perform the function of the gateway in a network. Protocols that can be used for this purpose are HSRP (Host Standby Router Protocol) from Cisco and VRRP (Virtual Router redundancy protocol) which is standard and is supported by other manufacturers of networking equipment. With these protocols one can configure at least two devices to work as a single gateway, without the need to change anything on the user computers. The idea is that all computers, according to their VLAN, are configured with the same IP address for gateway. This IP address is configured on two or more routers at the edge of the network and these routers are responsible for forwarding traffic coming to that IP address. At any time, one of the routers is primary gateway, responsible for forwarding traffic, and the other serves as a backup. If a router that is the primary gateway fails, the role of the primary gateway is assumed by another router that is configured to be his backup. 40 | P a g e These protocols do not protect only against failures of the entire device, but they can be configured to track certain links or availability of services so that in case of their unavailability backup device can take the role of the primary gateway and communication can continue. Potential problem with these two protocols is that basically only one device is active at a given time, and the other serves as a backup. Of course, a manual traffic load balance can be configured so that one router is the primary gateway for one part of VLANs, and the other router is the primary gateway for another part of VLANs, which is like manual load balancing in case of STP protocol. But if the goal is to have real load balancing there is another protocol called GLBP (Gateway Load balancing Protocol) which can solve this problem. GLBP is cisco proprietary protocol which allows us to simultaneously use all the routers that act as gateway so that the traffic between them is load balanced. This is especially useful solution in large networks that have multiple exits to the Internet. Otherwise, in most cases it is enough to use HSRP or VRRP. STACKABLE AND MODULAR DEVICES Using stackable switches is a very interesting and viable option in achieving redundant network, even though equipment that supports this type of features can be significantly more expensive than conventional switches. Stacking is the idea that two or more devices can be configured to operate as a single device by connecting backplanes of these devices using special stack cables or in some cases, using fiber optic connections. The advantage of using fiber optic connection is that stacking can be achieved between devices over distances of many kilometers, for example fiber ring around the city which is composed of stackable devices all working as one. In addition to stacking devices for the purpose of network redundancy it is possible to stack their power supply, which further increases network resilience. In networks that are not large and can implement collapsed core network design it can be a very profitable long-term investment which has the advantage of eliminating STP which is relatively slow and can cause problems for network convergence after a failure. Networks using stacking technology combined with link aggregation can achieve more stable and predictable failover in case of failure of any device or any link. Moreover, these networks are easy to expand and maintain and offer greater performance. Although in certain specific situations stack could ultimately cause some negative effects, mainly it is very flexible, resilient, easy to deploy and scalable solution, especially for a relatively small network. For stacking devices, technologies that are used are mainly owned by individual vendors, such as Stack Wise and VSS (Virtual Switching System) from Cisco or IRF (Intelligent Resilient Framework) from HP, which makes sense because these technologies are optimized for specific operating system and hardware which ensures maximum stability and reliability as well as performance. Ultimately when selecting stackable solution, devices price will be the key factor because requirements for performance in smaller networks are generally met using equipment of any manufacturer. An alternative to using stackable devices is the use of modular devices. 41 | P a g e Part 3 1. Design and implement a network prototype using a network simulator (or lab devices), which incorporates redundancy at Layer 2 and 3 and link aggregation features with the following requirements: 2. Include at least three Layer 2 switches. 3. Provide redundant link between all the switches. 4. Use Rapid PVST+ (Per-VLAN Spanning Tree) as spanning tree protocol. 5. Use link aggregation in the main active link. 42 | P a g e 43 | P a g e PVST+ and Rapid PVST+ PVST+ (Per VLAN Spanning Tree Plus) PVST+ (Per VLAN Spanning Tree Plus) is a Cisco proprietary STP version. It is also the default STP version for Cisco devices. It is the standard named 802.1d. In normal STP, CST (Common Spanning Tree), only one instance can be used for the whoşe network. There are no specific instances per VLAN. PVST+ (Per VLAN Spanning Tree Plus) creates an instance for each VLAN and in each instance, a different STP process occurs, a different Root bridge is selected, different port roles are used etc. 44 | P a g e There are some advantages and disadvantages of PVST+ if we compare it with normal STP (CST). What are these advantages and disadvantages? Let’s check. For the network performance, PVST+ is a better selection than STP. Because, in PVST+, STP process is done for a small group of devices, for the devices in the same VLAN. Not for the whole devices in that network. The performance is better in PVST+ than normal STP (CST), but, here the CPU and memory usage are more. This is one of the disadvantages of PVST+. Beside, the convergence time is also higher than CST in PVST+. Another important advantage of PVST+ is providing a good load balancing. Rapid PVST+ (Rapid Per VLAN Spanning Tree Plus) Rapid PVST+ (Rapid Per VLAN Spanning Tree Plus) is also a Cisco proprietary STP version. Again, it has an instance for each VLAN and each VLAN has a separate STP process. 45 | P a g e It has a faster convergence advantage if we compare it with PVST+. Beside, PVST+ (Rapid Per VLAN Spanning Tree Plus) need more CPU and memory resources than PVST+. RPVST+ has four states. These states are also the states of MST (Multiple Spanning Tree) that we will discuss later. RPVST+ States are given below: ▪ ▪ ▪ ▪ Blocking Learning Forwarding Disabled 46 | P a g e Part 4 Task: 1.1 Discuss the Wide Area Networking (WAN) concerns and make recommendations to sustain network security, reliability and performance A WAN (wide area network) is a communications network that spans a large geographic area such as across cities, states, or countries. They can be private to connect parts of a business or they can be more public to connect smaller networks together.The easiest way to understand what a WAN is to think of the internet as a whole, which is the world's largest WAN. The internet is a WAN because, through the use of ISPs, it connects lots of smaller local area networks (LANs) or metro area networks (MANs).On a smaller scale, a business may have a WAN that's comprised of cloud services, its headquarters, and smaller branch offices. The WAN, in this case, would be used to connect all of those sections of the business together.No matter what the WAN joins together or how far apart the networks are, the end result is always intended to allow different smaller networks from different locations to communicate with one another. How WANs Are Connected Since WANs, by definition, cover a larger distance than LANs, it makes sense to connect the various parts of the WAN using a virtual private network (VPN). This provides protected communications between sites, which is necessary given that the data transfers are happening over the internet. Although VPNs provide reasonable levels of security for business uses, a public internet connection does not always provide the predictable levels of performance that a dedicated WAN link can. This is why fiber optic cables are sometimes used to facilitate communication between the WAN links. X.25, Frame Relay, and MPLS Since the 1970s, many WANs were built using a technology standard called X.25. These types of networks supported automated teller machines, credit card transaction systems, and some of the early online information services such as CompuServe. Older X.25 networks ran using 56 Kbps dial-up modem connections. Frame Relay technology was created to simplify X.25 protocols and provide a less expensive solution for wide area networks that needed to run at higher speeds. Frame Relay became a popular choice for telecommunications companies in the United States during the 1990s, particularly AT&T. 47 | P a g e Multiprotocol Label Switching (MPLS) was built to replace Frame Relay by improving protocol support for handling voice and video traffic in addition to normal data traffic. The Quality of Service (QoS) features of MPLS was key to its success. So-called "triple play" network services built on MPLS increased in popularity during the 2000s and eventually replaced Frame Relay. Leased Lines and Metro Ethernet Many businesses started using leased line WANs in the mid-1990s as the web and internet exploded in popularity. T1 and T3 lines are often used to support MPLS or internet VPN communications. Long-distance, point-to-point Ethernet links can also be used to build dedicated wide area networks. While much more expensive than internet VPNs or MPLS solutions, private Ethernet WANs offer very high performance, with links typically rated at 1 Gbps compared to the 45 Mbps of a traditional T1. If a WAN combines two or more connection types like if it uses MPLS circuits as well as T3 lines, it can be considered a hybrid WAN. These are useful if the organization wants to provide a cost-effective method to connect their branches together but also have a faster method of transferring important data if needed. Problems With Wide Area Networks WAN networks are much more expensive than home or corporate intranets. WANs that cross international and other territorial boundaries fall under different legal jurisdictions. Disputes can arise between governments over ownership rights and network usage restrictions. Global WANs require the use of undersea network cables to communicate across continents. Undersea cables are subject to sabotage and also unintentional breaks from ships and weather conditions. Compared to underground landlines, undersea cables tend to take much longer and cost much more to repair. Distinctive WAN innovations can be utilized to conquer arrange security and dependability gives that are depicted as pursues: MD5: It is a generally utilized cryptographic hash capacity and it gives some affirmation that a moved document and client can coordinate checksum of downloaded record with previously existing documents. Just as it additionally gives mistake registration usefulness and helps client to perceive a degenerate or deficient download almost certain when downloading huge 48 | P a g e document. In MD process input message is separated into pieces of 512-piece square and ordinarily it used to check the respectability of records. MD5 is generally used to store passwords. In advanced mark it is utilized for giving assurance consistency on exchange. The calculation filling in as depicts as pursues: The exchange procedure begins when sender makes input message (M) and registers it with message digests (sMD). On the opposite side recipient gets the message (M-esMD) and concentrates encoded message digest (esMD). Further recipient registers possess message digest (rMD) with got message (M).Message was not adjusted during the information transmission, when both message digests are equivalent. • • • • • Broadcast reduction system is a logical domain of computer network which is use in noise reduction. By using broadcast each node is connecting with each other at data linked layer. Filters are Analog circuits which perform signal processing functions and commonly it is used in removing unwanted frequency components from the signal. Different types of digital filters can use by organizations such as active, passive, high pass, linear and non-linear etc. Firewall is a network security system that is monitoring over incoming and outgoing messages. It is working as a software solution and as a hardware appliance. Firewall protects computer or network from unauthorized users by acting as a gate through which all data must pass. System performance can also affect by it because it verifies every packets and lot of time is taken in verification process. Access control lists can be used to assign permission to non-existent nodes and stores permission safely separately from the content in an appropriate manner. VPN tunnels allow remote clients to tunnel into our network that the underlying network does not support or provide directly. It enables one network to send its data via other network connections. It can be used to carry the packets that actually provide the service not normally provided by the network. Major drawbacks of tunnels are that they are not easily moved (Jason and Thomas, 2012). 49 | P a g e 1.2 Design the Wide Area Networking (WAN) infrastructure to meet given requirement As per the requirement we have organization CBS services (PVT)Ltd based in United Kingdom and there are users in the company. They will be using CBS services application which is hosted in data center located on London there are two branches in New York, USA and Colombo, Sri Lankan. All sites have connected each other. As per CBS service bandwidth is required 100 kbps per user. To fulfil this recruitment planning we need 5 Mbps link from two ISPs. We have procured below devices. Details are as follows • • • • Two Routers (each location) Two firewalls (each location Two 3560 core switches (each location) One 3750 switch (each location) We are using WAN routing protocol (Network Technology) EIGRP. Based on technology we have applied routing policy for the load balancing. Load balancing is required when there are two ISP link and we need utilize both. Load balancing is very good technology nowadays. Every organization is using the for-load sharing. We are using IPsec tunnel as security provide to make our data traffic secure and encrypted. MD5 and 3 des algorithm has been used for data encryption. 50 | P a g e 1.3 Critically evaluate the suitability of the Wide Area Networking (WAN) Components The principle segments for a WAN are Routers, switches and modems. These parts are depicted beneath in the equipment area. CPE In telecommunications, a customer-premises equipment or customer-provided equipment (CPE) is any terminal and associated equipment located at a subscriber's premises and connected with a carrier's telecommunication circuit at the demarcation point ("demarc"). The demarc is a point established in a building or complex to separate customer equipment from the equipment located in either the distribution infrastructure or central office of the communications service provider. CPE generally refers to devices such as telephones, routers, network switches, residential gateways (RG), set-top boxes, fixed mobile convergence products, home networking adapters and Internet access gateways that enable consumers to access providers' communication services and distribute them in a residence or enterprise with a local area network (LAN). Routers A router is hardware device designed to receive, analyze and move incoming packets to another network. It may also be used to convert the packets to another network interface, drop them, and perform other actions relating to a network. CME routers A Cisco Unified CME system consists of a router that serves as a gateway and one or more VLANs that connect IP phones and phone devices to the router. ... Each phone can have multiple extensions associated with it and a single extension can be assigned to multiple phones. Switch A switch, in the context of networking is a high-speed device that receives incoming data packets and redirects them to their destination on a local area network (LAN). A LAN switch operates at the data link layer (Layer 2) or the network layer of the OSI Model and, as such it can support all types of packet protocols. Firewall 51 | P a g e A firewall is a network security device, either hardware or software-based, which monitors all incoming and outgoing traffic and based on a defined set of security rules it accepts, rejects or drops that specific traffic. Accept: allow the traffic Reject: block the traffic but reply with an “unreachable error” Drop: block the traffic with no reply A firewall establishes a barrier between secured internal networks and outside untrusted network, such as the Internet. IP telephony IP telephony (Internet Protocol telephony) is a general term for the technologies that use the Internet Protocol's packet-switched connections to exchange voice, fax, and other forms of information that have traditionally been carried over the dedicated circuit-switched connections of the public switched telephone network (PSTN). Using the Internet, calls travel as packets of data on shared lines, avoiding the tolls of the PSTN. The challenge in IP telephony is to deliver the voice, fax, or video packets in a dependable flow to the user. Much of IP telephony focuses on that challenge. Gateways In computer networking and telecommunications, a gateway is a component that is part of two networks, which use different protocols. The gateway will translate one protocol into the other. A router is a special case of a gateway. Gateways, also called protocol converters, can operate at any network layer. The activities of a gateway are more complex than that of the router or switch as it communicates using more than one protocol. 52 | P a g e 1.4 Build and configure the Wide Area Networking (WAN) (including services) to meet a given requirement 1.5 Implement network security on a the Wide Area Networking (WAN) IP Allocation 10.10.1.0 10.10.2.0 10.10.3.0 53 | P a g e Site Location London, United Kingdom New York, USA Colombo, Srilanka Subnet mask /24 /24 /24 Configuration IOS command Line Interface 54 | P a g e London, United Kingdom location configuration • Step by step process of implementation on WAN network Router-configuration Router-London>configure terminal Router- London (config)#interface se Router- London (config)#interface serial 0/0/0 Router- London (config)#IP address 10.10.1.2 255.255.255.0 Router- London (config)# no shut down • next we have configuration firewall port that direct connected to router Firewall configuration FW-London>configure terminal FW- London (config)#interface gig0/0 FW- London (config)#IP address 10.10.1.3 255.255.255.0 FW- London (config)# no shut down Ping IP address from firewall to router • C:\ >ping 10.10.1.2 Pinging 10.10.1.2 with 32 bytes of data: Reply from 10.10.1.2: bytes=32 time=1ms TTL=255 Reply from 10.10.1.2: bytes=32 time=1ms TTL=255 Reply from 10.10.1.2: bytes=32 time=1ms TTL=255 Reply from 10.99.1.2: bytes=32 time=1ms TTL=255 Ping statistics 10.99.1.2: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 0ms, Maximum = 0ms, Average = 0ms • next we have configuration access switch port that direct connected to FW switch- London >configure terminal switch- London (config-if)# vlan 10 switch- London(config-if)# name server switch- London (config-if)# exitswitch-Dallas(config)#intraange fa0/10-22 switch- London (config-if)# switchport mode access switch- London (config-if)# switchport mode access vlan 55 | P a g e New York location configuration • Step by step process of implementation on WAN network Router configuration Router-New York>configure terminal Router-New York(config)#interface se Router-New York(config)#interface serial 0/0/1 Router-New York(config)#ip address 10.10.2.2 255.255.255.0 Router-New York(config)# no shut down next we have configuration firewall port that direct connected to router • Firewall configuration FW-New York>configure terminal FW-New York(config)#interface gig0/1 FW-New York(config)#ip address 10.10.2.3 255.255.255.0 FW-New York(config)# no shut down next we have configuration access switch port that direct connected to FW switch-New York>configure terminal switch-New York(config-if)# vlan 12 switch-New York(config-if)# name New Yorkserver switch-New York(config-if)# exit switch-New York(config)#intraange fa0/10-21 switch-New York(config-if)# switchport mode access switch -New York(config-if)# switchport mode access vlan 20 • After configuration of New York location we are able to ping London ip address from New York PC Ping ip address from firewall to router C:\ >ping 10.10.1.2 Pinging 10.10.1.2 with 32 bytes of data: Reply from 10.10.1.2: bytes=32 time=47ms TTL=255 Reply from 10.10.1.2: bytes=32 time=44ms TTL=255 Reply from 10.10.1.2: bytes=32 time=46ms TTL=255 Reply from 10.10.1.2: bytes=32 time=48ms TTL=255 Ping statistics 10.10.1.2: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 44ms, Maximum = 48ms, Average = 46ms 56 | P a g e Colombo location configuration • Step by step process of implementation on WAN network Router configuration Router-Colombo>configure terminal Router- Colombo (config)#interface se Router- Colombo (config)#interface serial 0/0/1 Router- Colombo (config)#ip address 10.10.3.2 255.255.255.0 Router- Colombo (config)# no shut down • next we have configuration firewall port that direct connected to router Firewall configuration FW- Colombo >configure terminal FW- Colombo (config)#interface gig0/1 FW- Colombo (config)#ip address 10.10.3.3 255.255.255.0 FW- Colombo (config)# no shut down next we have configuration access switch port that direct connected to FW switch- Colombo >configure terminal switch- Colombo (config-if)# vlan 12 switch- Colombo (config-if)# name Colombo server switch- Colombo (config-if)# exit switch- Colombo (config)#intraange fa0/10-21 switch- Colombo (config-if)# switchport mode access switch - Colombo (config-if)# switchport mode access vlan 20 • After configuration of Colombo location we are able to ping London and New York ip addressfrom Colombo PC Ping ip address from firewall to router C:\ >ping 10.10.1.2 Pinging 10.10.1.2 with 32 bytes of data: Reply from 10.10.1.2: bytes=32 time=47ms TTL=255 Reply from 10.10.1.2: bytes=32 time=44ms TTL=255 Reply from 10.10.1.2: bytes=32 time=46ms TTL=255 Reply from 10.10.1.2: bytes=32 time=48ms TTL=255 Ping statistics 10.10.1.2: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), 57 | P a g e Approximate round trip times in milli-seconds: Minimum = 44ms, Maximum = 48ms, Average = 46ms Ping ip address from firewall to router C:\ >ping 10.10.2.2 Pinging 10.10.2.2 with 32 bytes of data: Reply from 10.10.2.2: bytes=32 time=47ms TTL=255 Reply from 10.10.2.2: bytes=32 time=44ms TTL=255 Reply from 10.10.2.2: bytes=32 time=46ms TTL=255 Reply from 10.10.2.2: bytes=32 time=48ms TTL=255 Ping statistics 10.10.2.2: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 44ms, Maximum = 48ms, Average = 46ms 58 | P a g e 1.6 Monitor and troubleshoot a the Wide Area Networking We have taken one work area and introduced checking application (i.e. Eheath and MRTG for traffic observing). From Ehealth we get the data like CPU, RAM and basic logs of the gadgets. Furthermore, from MRTG we get data like connection usage and transmission capacity use. At whatever point client face any issue like inactivity and gradualness of the application we utilize this checking application to break down the issues. For the security, we have introduced syslog application which screen the Firewall traffic. On the off chance that any undesirable solicitation, Trojan and so forth hits on the Firewall, we get alert quickly on syslogs. In view of cautions, we investigate the logs and execute the new rules on the firewall which increment the unwavering quality and execution of the system. 1.7 Resolve the Wide Area Networking (WAN) issues to improve security, reliability and performance To determine the WAN system working framework issue, we login to the WAN gadgets and check the CPU, RAM and Link usage. on the off chance that we see any mistakes and variation from the norm on WAN Links, we investigate the issue by putting the directions (show interface WANPort). In view of that we check whether it is issue on specialist co-op or our end. With the assistance of observing devices if mistakes and issue happens, we get auto produced sends which help us to investigate the issue before client reports. It limits personal time and creation loss of the organization. 1.8 Critically evaluate the performance of a the Wide Area Networking (WAN) Reason for this task and structure to arrangement system of an association with the goal that client sitting in HQ and branches can get to citrix application facilitated in Datacenter. We have conveyed best supplies and great design with security estimation. There are five suggestion which can at present improve our system underneath are those: • • • • • We can introduce IPS for assessment on bundle level. We can introduce riverbed to advance WAN traffic. QOS can be applied to organize the traffic. We can make separate zone on Firewall to isolate the server and client traffic because of security reason. We can likewise do NAT to shroud our association subnet to course it on open system. 59 | P a g e Part 5 A) Based on the case study provided, evaluate at least two (2) Network Management Protocols and apply the most suitable protocol on current wireless network for analysis of traffic pattern. Network Management Protocols Understanding network management protocols can be an arduous task. It is easy to miss the technical term, the different procedures, the different ways of formatting the data, the multiple options, etc. To facilitate this task, we propose you to follow this simple guide. Network management protocols are network protocols The network administration protocols work in the field of networks and therefore are network protocols. Now, it is important to differentiate them from those network protocols that allow the transfer of data between two devices, such as TCP, UDP, SMTP, CSMA / CD, etc. In a network both data transfer protocols and administration protocols will coexist, sharing resources such as CPU and link bandwidth. It is therefore interesting to keep in mind that network management protocols also influence the overall performance of the platform. Be clear about the approach of the protocol It is easy to understand that the more complex and heterogeneous the platform, the greater difficulty we will find in its administration. Network administration has faced this complexity from three angles: • • • Faults: in this area the idea is to have procedures to detect faults and a scheme to report them. Performance: here the idea is to obtain data on the behavior of the platform that allows us to make inferences about the performance of it. Actions: Many management protocols include the ability to execute actions on managed items. When we try to understand a protocol it is important to stop for a moment and think about what angle the protocol proposes or with what angle we want to use it. 60 | P a g e Network management protocols and their architecture All management protocols propose an architecture and procedures to extract, collect, transfer, store and report management information from the managed elements. It is important to understand the architecture and procedures when it comes to understanding a management protocol, and indispensable when implementing a solution based on this protocol. Network management protocols and the organization of dataAnother fundamental point is the way in which the network administration protocols format and manage the management data. The basis is how they define and identify the elements to be administered. It is always interesting to mention: What element can I administer with this protocol? Only hardware or does it also cover applications, for example? Then it is about defining what information I can extract from the managed elements and what actions I can execute, if I can execute any. What format is used to handle the data? And how it is stored, if it is stored. Finally, what are the options I have to access this information? Now, in the rest of this article we will review three of the most popular administration protocols, trying to concentrate on the aforementioned points: focus, architecture and data organization. For this review we will take the following diagram as a guide: 61 | P a g e ICMP ICMP (Internet Control Message Protocol) is a network layer protocol that is part of the group of sub-protocols associated with the IP protocol. ICMP works in the field of fault validation and allows the calculation of certain performance metrics. The reader can read about the detailed specifications of the protocol in RFC792. The procedure proposed by ICMP is based on the detection of an error condition and the sending of a message reporting said condition. Thus, the key element is the messages contemplated by ICMP, which are usually classified in two categories: • • Error messages: Used to report an error in the packet transmission. Control messages: Used to report on the status of devices. The architecture with which ICMP works is very flexible, since any device in the network can send, receive or process ICMP messages. In practice it is used for routers and switches to report to the host that originates a packet that the packet cannot be delivered due to a network error. In addition, ICMP is also used to perform calculations of metrics on performance, such as levels of latency, response time or packet loss, among others. SNMP SNMP (Simple Network Management Protocol) is an application layer protocol that covers the areas of failures, performance and actions. SNMP offers a scheme to gather, organize and communicate management information between the devices that make up a network. This scheme manages to be common to a large number of hardware components, supporting: • • Diversity of devices: from network devices such as routers, switches, firewalls or access points to end user devices such as printers, scanners, stations or servers. Diversity of marks: most brands, when presenting a product, make sure that this product has support for SNMP included. The reader interested in reading the formal SNMP specifications should review several RFC documents, but we recommend that you start with RFC 1157. 62 | P a g e Architecture SNMP The SNMP architecture is based on two basic components: the SNMP Agents and the SNMP Administrators. In the following diagram we present a basic outline of this SNMP architecture: SNMP agents are pieces of software that run on the elements to be managed. They are responsible for collecting data on the device. Then, when SNMP administrators request such data through queries, the agent will send the corresponding. The SNMP agents can also send the SNMP Manager information that does not correspond to a query but that part of an event that occurs in the device and that requires to be notified. Then, it is said that the SNMP agent proactively sends a notification TRAP. The SNMP Administrators are found as part of a management or monitoring tool and are designed to function as consoles where all the data captured and sent by the SNMP agents is centralized. 63 | P a g e B) To resolve the problem of wireless local area network (WLAN) IP address allocation with the knowledge of troubleshooting methodology, apply appropriate steps to troubleshoot the failure of IP address allocation. At least six (6) to be discussed. Networks are networks. Despite best efforts to keep things smooth all the time every day, things happen. Here’s a look at some common network issues, some tips for quickly resolving them, and even better, how to prevent them from occurring again. 1. Duplicate IP Addresses When two devices attempt to share a single IP, you see the dreaded “Address Already in Use” error — with no ability to access the network. The Quick Fix: The blame for this often rests with your router’s default DHCP configuration. DHCP is probably trying to assign your new device an address at the beginning of your subnet, and another device may already occupy these low-numbered addresses with static IPs. If you’ve just introduced a new device or server to your network, it may have its own DHCP server. Simply disable the DHCP server on that device to restore sanity to your network. The Preventive Measure: You can take one simple step to avoid IP conflicts by modifying your router’s configuration to begin assigning DHCP addresses near the top end of your subnet, leaving the lower addresses available for devices that require static IPs. 2. IP Address Exhaustion To troubleshoot this issue, use the ipconfig command. If the workstation has assigned itself an IP address that begins with 169.x.x.x, it means that no IP address was available from the DHCP server. The Quick Fix: Some users on cable internet might not have a local router, in which case IP addresses are assigned on a limited basis directly from your ISP. You have probably run out of allowed IP addresses from your ISP. The solution to this is to purchase either a standalone router or WIFI access point with an integrated router. This creates your own local pool of internal addresses, ensuring you won’t run out. If you already have a local router with DHCP, the default address pool might be too small for your network. By accessing the DHCP settings on the router, you can adjust the size of the address pool to meet your network’s needs. The Preventive Measure: It’s important that any internet-connected network have a local router in operation with NAT and DHCP, both for security reasons and to prevent IP address 64 | P a g e exhaustion. The router needs to be the only device connected to the modem, with all other devices connecting through the router. 3. DNS Problems Errors such as The Network Path Cannot Be Found, IP Address Could Not Be Found, or DNS Name Does Not Exist, can usually be traced to a DNS configuration issue. The command line utility nslookup can be used to quickly show a workstation’s DNS settings. The Quick Fix: Workstations and other network devices can be configured to use their own DNS servers, ignoring the server assigned by DHCP. Checking the ‘Internet Protocol Version 4 (TCP/IP)’ settings for your adapter will show if an incorrect DNS server is specified, so just select “Obtain DNS server address automatically” instead. The Prevention Measure: Your local router might be configured to operate as a DNS Server, creating a DNS pass-through to your ISPs servers. On busy networks, this may overload the capabilities of the router. Change your network’s DHCP settings to directly access your DNS servers. 4. Single Workstation Unable to Connect to the Network If only a single workstation is displaying the “No internet” message when opening a web browser, we can usually assume that the rest of the network is healthy and turn our attention to any hardware and software that is particular to this system. The Quick Fix: To resolve this network issue, start by eliminating the obvious communication barriers such as a bad cable, poor WiFi signal, failing network card or incorrect drivers. Ensure that the workstation’s network adapter is configured with the correct IP, subnet, and DNS servers. If that doesn’t solve the problem, check any firewall software on the device to ensure that necessary ports are open to the external network. Common ports include 80 and 443 for web traffic, plus 25, 587, 465, 110, and 995 for email. The Preventive Measure: It’s usually best to leave all workstation TCP/IP settings to “Automatically assigned.” Use a DHCP server to hand out a uniform configuration to all devices on the network. If a static IP is needed on a particular workstation or server, most DHCP servers allow the ability to create static IP mappings. 65 | P a g e 5. Unable to Connect to Local File or Printer Shares Sharing problems are among the most difficult network problems to solve, due to the number of components that need to be configured properly. Most commonly, sharing problems arise due to conflicts between mixed security environments. Even different versions of the same operating system sometimes use slightly different security models, which can make interconnection of workstations difficult. The Quick Fix: We can cure sharing problems most efficiently by drilling down through the possibilities in this order: 1. Ensure that the required services are running. On Windows systems, the server, TCP/IP NetBIOS Helper, workstation, and computer browser services all need to be running. On Linux machines, Samba is the primary component required to share with Windows systems. 2. Check your firewall(s). It’s very common for a workstation’s firewall to be configured to block file and printer sharing traffic, especially if a new antivirus package is installed that introduces its own firewall. Firewall issues can also exist at the hardware level, so ensure that routers or managed switches are passing share traffic within the subnet. Speaking of subnet…. 3. Ensure all workstations are on the same subnet. This problem typically only appears on complex networks, however, even simple networks sometimes have static-IP equipment with an improperly configured subnet. The result is that external traffic will move about just fine, while internal traffic will hit unexpected roadblocks. 4. All Windows network adapters will need File and Printer Sharing for Microsoft Networks, Client for Microsoft Networks, and NetBIOS over TCP/IP enabled. 5. Once the above checks have passed, it’s finally time to check the most likely culprit, permissions. There are multiple layers of access required, each with their own interface within the OS. Check for: • • • • Systems configured with the wrong workgroup or domain. Incorrectly configured HomeGroup. Network type set to Public. Incorrect NTFS permissions. 6. Local Network is Unable to Connect to the internet This situation can either be intermittent or persistent. Often times, the most difficult aspect of dealing with any external network problem is finding the company responsible. And then tasking them to solve the issue, particularly with intermittent failures that are difficult to trace. It can 66 | P a g e sometimes be such a problem that organizations will have to switch internet providers in order to solve the issue. The Quick Fix: A router and modem reboot is the first order of business. The tracert then utility can be used to identify communication breaks. It will clearly hiccup on the particular router hop that is causing the problem. Contact your ISP with your findings, providing screenshots as necessary. The Preventive Measure: To avoid the finger-pointing that can prevent rapid resolution of external issues, do some research to ensure that you procure connectivity only from local Tier 1 providers. Other ISPs are more than happy to sell you service, however, they are simply piggybacking the Tier 1 connection, since they don’t actually own the infrastructure in your area. The goal is to remove as many middle-men as possible, so that when (not if) you experience a problem, one phone call is all that is required to identify the issue and get technicians to work on it. 7. Slow Internet Performance Slow performance is typically due to congestion, or sometimes poor quality connections that have corroded or otherwise deteriorated. Congestion may not be directly related to bandwidth exhaustion, as a single overloaded port on a switch or router can diminish network performance. This can be especially true on leased lines where dedicated bandwidth is to be expected, but speed tests indicate the network is not reaching it’s rated potential. The Quick Fix: Use speed test websites, conducting tests from geographically remote servers. This can pinpoint areas of congestion on the ISP’s network. In the case of cable internet, the local network is shared amongst your neighbors, committing your ISP to a costly bandwidth upgrade when saturation occurs. Report your findings to your ISP so that they can take steps to resolve the issue. DNS servers are an often overlooked aspect of internet performance. Using incorrect DNS servers can result in routing congestion or load balancing problems. While you should typically use your ISP’s DNS settings whenever possible, they may actually be routing traffic through overloaded web caches. You can temporarily adjust your DNS settings to use OpenDNS instead. The Preventive Measure: if internet performance is critical, you’ll need to procure adequate connectivity. While cable internet may be inexpensive, you could be setting yourself up for frequent jeers from employees. A local DSL operator may offer improved reliability for a slightly higher cost, but for the most consistent performance, you may find that an expensive leased line is a requirement for your organization. 67 | P a g e According to cisco Configuration Issues For a successful wireless connection, it is essential that configuration on the WLC is done correctly. This section describes some of the most commonly seen configuration issues. • SSID Mismatch The client uses its SSID to identify and associate to the wireless network, so ensure that the SSID is configured identically on the WLC and the client. In order to check the SSID configured on the WLC, click the WLANs page. Click the appropriate WLAN, and check the SSID configured under the General tab. Note: SSID is case sensitive. It might help the wireless client to associate to the WLAN if you delete and recreate the WLAN. • Security Mismatch Security configurations must match between the WLC and the client. If the authentication type is Static WEP, check if the appropriate encryption key/key index on the WLC matches that of the client. If the authentication type is 802.1x or WPA, ensure that the authentication type/encryption key size matches between the client and the WLC. For more information on how to configure the WLC and the client for various security solutions, refer to Authentication on Wireless LAN Controllers Configuration Examples. Note: Layer 2 security solutions, such as WPA or 802.1x, cannot be used for a WLAN configured with Layer 3 security solutions, such as web authentication or passthrough. For more information on compatible security solutions refer to Wireless LAN Controller Layer 2 and Layer 3 Security Compatibility Matrix. • Disabled WLAN For a successful wireless connection, the corresponding WLAN must be active on the WLC. By default, the status of the WLAN is not enabled on the WLC. In order to activate the WLAN, click the WLANs menu in the WLC. A list of WLANs configured on the WLC displays. Click the WLAN that is configured with the SSID to which the client wants to associate. Under the General tab of the WLANs > Edit page, check the status box. • Unsupported Data-Rates For a particular standard, either 802.11b/g or 802.11a, you can optionally set certain data rates as mandatory and other data rates as supported or disabled on the WLC. For a successful association, a wireless client must support the data rates that are configured as mandatory on the WLC. In order to check the data rates configured on the WLC, click the Wireless menu on the WLC GUI, and check the data rates configured under the 802.11b/g/n > Network or 802.11a/n > Network option that appears on the left-hand side of the page. Check the support page of the client vendor to determine this. If you upgrade the client driver, it can help the client to support the required data rates. Note: For better connectivity, set the lowest data rate to mandatory on the WLC and other data rates to supported. 68 | P a g e IP Address Issues Wireless clients need valid IP addresses to communicate with the rest of the network. The controller behaves like a router with an IP helper address. That is, it fills in the gateway IP address and unicasts it to the DHCP server via the dynamic interface on which the client is installed. So be aware that DHCP snooping on switches will, by default, block these DHCP packets on untrusted ports. When the DHCP offer comes back to the controller, it changes the DHCP server IP address to its virtual IP address. The reason it does this is because when Windows roams between APs, the first thing it does is try to contact the DHCP server and renew its address. 69 | P a g e C) The monitoring of the inter-campus the Wide Area Networking (WAN) links is crucial to ensure smooth network operations. Analyse at least three (3) reasons for the links failure and suggest most suitable solution. Please describe your answer? following problems are the best candidates for interconnection failure: • • • • • • • • Cabling problem to the switch or to the LAN Wrong applique (must be data terminal equipment [DTE] for CSU/DSU connectivity) Router hardware problem Disabled port on the X.25 switch Bad T1 digital link Mismatched Ethernet version configurations Misconfigured hosts Misconfigured router Next, eliminate each potential cause as a problem source and then test the network to determine whether it is operational. The following discussion works through the problem isolation process. 70 | P a g e References Carol, X,,2013. Computer?mediated communication and social networking tools at work. Information Technology and People. 26 (2). PP.172 – 190. Morten H. A., 2011, Sensemaking in Networks: Using Network Pictures to Understand Network Dynamics, in Roger Baxter, Arch G. Woodside (ed.) Interfirm Networks: Theory, Strategy, and Behavior.17. Emerald Group Publishing Limited. PP.1 – 197. Jason B. F. And Thomas L. M., 2012. Tools for interdisciplinary design of pervasive computing. International Journal of Pervasive Computing and Communications. 8. PP.112 – 132. Sheynblat, L., Krasner, N. F., 2004. U.S. Patent No. 6,677,894. Washington, DC: U.S. Patent and Trademark Office. 71 | P a g e