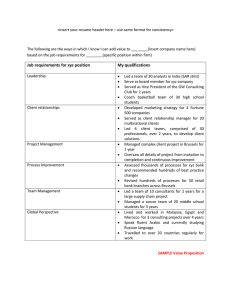
Assignment Task 2: BYOD Acceptable Use Policy & Procedure This policy of XYZ Group of Companies (hereinafter the “Company”) outlines the Company’s provisions for the appropriate use of personal mobile devices in the workplace. This is intended to protect the security and integrity of the Company’s data and technology infrastructure. The Company grants its employees the privilege of bringing and using smartphones and tablets of their choosing at work for their convenience. The Company reserves the right to revoke this privilege if users do not abide by the policies and procedures outlined below. The Company’s employees must agree to the terms and conditions set forth in this policy in order to be able to connect their devices to the company network. The policy applies to any hardware and related software that is not organizationally owned or supplied, but could be used to access organizational resources. That is, devices employees have acquired for personal use but also wish to use in the business environment. OBJECTIVE This policy establishes the Company’s guidelines for employee use of personally owned electronic devices for work-related purposes. Employees of the Company may have the opportunity to use their personal electronic devices for work purposes when authorized in writing, in advance, by the management and the Head of the IT Department. The use of personal devices may be limited based on compatibility of technology. Contact the IT department for more details. SCOPE The purpose of this policy is to define standards, procedures and restrictions for end users who are connecting a personally-owned device to the Company’s organization network for business purposes. This device policy applies, but is not limited to all devices and accompanying media (e.g. USB and external hard drives) that fit the following classifications: ● Smartphones ● Other mobile/cellular phones ● Tablet computers ● Portable media devices ● PDAs ● Ultra-mobile PCs (UMPCs) ● Laptop/notebook computers, including home desktops ● Any personallyowned device capable of storing organizational data and connecting to a network The overriding goal of this policy is to protect the integrity and business data that resides within the Company’s technology infrastructure. This policy intends to prevent this data from being deliberately or inadvertently stored insecurely on a device or carried over an insecure network where it could potentially be accessed by unsanctioned resources. A breach of this type could result in loss of information, damage to critical applications, loss of revenue, and damage to the company’s public image. Therefore, all users employing a personally-owned device connected to [the Company’s organizational network, and/or capable of backing up, storing, or otherwise accessing organizational data of any type, must adhere to company-defined processes for doing so. APPLICABILITY This policy applies to all XYZ Group of Companies employees, including full and part-time staff, contractors, freelancers, and other agents who use a personally-owned device to access, store, back up, or relocate any organization or client-specific data. Such access to this confidential data is a privilege, not a right, and forms the basis of the trust the Company has built with its clients, partners, and other constituents. Consequently, employment at XYZ Group of Companies does not automatically guarantee the initial or on-going ability to use these devices to gain access to organizational networks and information. PROCEDURE Device protocols To ensure the security of the Company, authorized employees are required to have anti-virus and mobile device management (MDM) software installed on their personal mobile devices. This MDM software will store all company-related information, including calendars, e-mails and other applications in one area that is password-protected and secure. The Company’s IT department must install this software prior to using the personal device for work purposes. Employees may store company-related information only in this area. Employees may not use cloud-based apps or backup that allows company-related data to be transferred to unsecure parties. Due to security issues, personal devices may not be synchronized with other devices in employees’ homes. Making any modifications to the device hardware or software beyond authorized and routine installation updates is prohibited unless approved by IT. Employees may not use unsecure Internet sites. All employees must use a pre-set ringtone and alert for company-related messages and calls. Personal calls and messages should be turned off or set to silent or vibrate mode during meetings and conferences and in other locations where incoming calls may disrupt normal workflow. Excessive personal calls, e-mails or text messaging during the workday, regardless of the device used, can interfere with employee productivity and be distracting to others. Employees must handle personal matters out of work time and ensure that friends and family members are aware of the policy. Exceptions may be made for emergency situations and as approved in advance by management. BOYD DEVICES AND SUPPORT The following devices are approved for employee BOYD use and connection to the Company’s network: OnePlus 7T Plus Pro Samsung Galaxy Note 10 Apple iPhone 11 Pro Apple iPhone 11 Apple iPhone XR Apple iPhone XS Max Samsung Galaxy Note 9 Samsung Galaxy S9 Plus Google Pixel 4 XL Google Pixel 3A XL Motorola Moto G7 Power Nokia 7.1 Huawei P30 Pro Huawei P20 Pro Huawei P10 LG G8 ThinQ Xiaomi Mi 9 Oppo Reno 10x Zoom Honor Magic 2 VivoIQOO ZTE Axon 10 Pro 5G Moto G7 Power LG G8X ThinQ Dual Screen Nexus 6P Sony XPERIA XZ3 Devices must be presented to IT for proper job provisioning and configuration of standard apps, such as browsers, office productivity software and security tools, before they can access the network. REIMBURSEMENT The company will reimburse the employee a percentage (5%) of the cost of the device. The company will reimburse the employee for the following charges: roaming, plan overages and monthly service charges. PRIVACY XYZ Group of Companies will respect the privacy of your device and will only request access to the device by IT technicians to implement security controls, as outlined below, or to respond to legitimate requests arising from administrative, civil or criminal proceedings. The Company has the right, at any time, to monitor and preserve any communications that use the Company’s networks in any way, including data, voice mail, telephone logs, Internet use and network traffic, to determine proper use. Management reserves the right to review or retain personal and company-related data on personal devices or to release the data to government agencies or third parties during an investigation or litigation. Management may review the activity and analyse use patterns and may choose to publicise these data to ensure that the Company’s resources in these areas are being used according to this policy. Furthermore, no employee may knowingly disable any network software or system identified as a monitoring tool. RESTRICTIONS ON AUTORIZED USE Employees whose personal devices have camera, video or recording capability are restricted from using those functions anywhere in the building or on company property at any time unless authorized in advance by management. While at work, employees are expected to exercise the same discretion in using their personal devices as is expected for the use of company devices. Company policies pertaining to equality, discrimination, retaliation, Social Media, Intellectual Property, confidential information and ethics apply to employee use of personal devices for work-related activities. Employees may not use their personal devices for work purposes during periods of unpaid leave without authorization from management. XYZ Group of Companies reserves the right to deactivate the company’s application and access on the employee’s personal device during periods of unpaid leave. An employee may not store information from or related to former employment on the company’s application. Family and friends should not use personal devices that are used for company and work-related purposes. Devices may not be used at any time to: Store or transmit illicit materials Store or transmit proprietary information belonging to another company Harass others Engage in outside business activities All employees will be blocked from accessing certain websites or downloading applications during work hours while connected to the corporate network at the discretion of the Company. Such websites include but are not limited to: Facebook Instagram Twitter Snapchat Typito Reddit Tumblr Flickr Pinterest Netflix Google Play ACCEPTABLE USE SAFETY The company defines acceptable business use as activities that directly or indirectly support the business of Company XYZ. The company defines acceptable personal use on company time as reasonable and limited personal communication or recreation, such as reading, checking messages or calling. Devices’ camera and/or video capabilities are disabled while on-site. The following apps are allowed: o The Guardian and any other foreign newspaper app o Weather App o Any local newspaper app o Whatsapp o Waze o BBC News o Any local bank app (HSBC, BOV mobile, etc) o Spotify o Dictionary Apps o Any local taxi apps Employees are expected to follow the National Traffic regulation laws and regulations regarding the use of electronic devices at all times. For further clarification follow the link: https://www.transport.gov.mt/Land-Licence-obtaining-your-driving-licence-Highway-code-eng.pdf-f911 Employees whose job responsibilities include regular or occasional driving are expected to refrain from using their personal devices while driving. Regardless of the circumstances, including slow or stopped traffic, employees are required to pull off to the side of the road and safely stop the vehicle before placing or accepting a call or texting. Special care should be taken in situations involving traffic, inclement weather or unfamiliar areas. Company XYZ has a zero-tolerance policy for texting or emailing while driving and only hands-free talking while driving is permitted. Employees who are charged with traffic violations resulting from the use of their personal devices while driving will be solely responsible for all liabilities that result from such actions. Employees who work in hazardous areas must refrain from using personal devices while at work in those areas, as such use can potentially be a major safety hazard. SECURITY ON USE OF DEVICE IT manages device security policies, network, application and data access centrally using whatever technology solutions it deems suitable. Any attempt to contravene or bypass that security implementation will be deemed an intrusion attempt and will be dealt with in accordance with the Company’s security policy. IT reserves the right, through policy enforcement and any other means it deems necessary, to limit the ability of end users to transfer data to and from specific resources on the Company network. In order to prevent unauthorized access, devices must be password protected using the features of the device and a strong password is required to access the company network. All data stored on the device must be encrypted using strong encryption and complex passwords. Passwords must be at least six characters and a combination of upper- and lower-case letters, numbers and symbols. Passwords will be rotated every 90 days and the new password cannot be one of 15 previous passwords. The device must lock itself with a password or PIN if it’s idle for five minutes. After five failed login attempts, the device will lock. Contact IT to regain access. Rooted (Android) or jailbroken (iOS) devices are strictly forbidden from accessing the network. Employees are automatically prevented from downloading, installing and using any app that does not appear on the company’s list of approved apps. Smartphones and tablets that are not on the company’s list of supported devices are not allowed to connect to the network. Employees’ access to company data is limited based on user profiles defined by IT and automatically enforced. Employees, contractors and temporary staff will follow all Company-sanctioned data removal procedures to permanently erase Company-specific data from such devices once its use is no longer required. LOST, STOLEN, DAMAGED OR HACKED EQUIPMENT Employees are expected to protect personal devices used for work-related purposes from loss, damage or theft. In the event of a lost, stolen, damaged or hacked device, it is incumbent on the user to report the incident to IT immediately. The device will be remotely wiped of all data and locked to prevent access by anyone other than IT. If the device is recovered, it can be submitted to IT for re-provisioning. Appropriate steps will be taken to ensure that company data on or accessible from the device is secured - including remote wiping of the device where appropriate. The remote wipe will destroy all data on the device, whether it is related to company business or personal. RISKS/LIABILITIES/DISCLAIMERS While IT will take every precaution to prevent the employee’s personal data from being lost in the event it must remote wipe a device, it is the employee’s responsibility to take additional precautions, such as backing up email, contacts, etc. The company reserves the right to disconnect devices or disable services without notification. Lost or stolen devices must be reported to the company within 24 hours. Employees are responsible for notifying their mobile service provider immediately upon loss of a device. The employee is expected to use his or her devices in an ethical manner at all times and adhere to the company’s acceptable use policy as outlined above. The employee assumes full liability for risks including, but not limited to, the partial or complete loss of company and personal data due to an operating system crash, errors, bugs, viruses, malware, and/or other software or hardware failures, or programming errors that render the device unusable. Company XYZ reserves the right to take appropriate disciplinary action up to and including termination for noncompliance with this policy. By signing this policy, employees acknowledge that they fully understand the risks and responsibilities of the BYOD policy and procedure. Any questions relating to this policy should be directed to the Head of IT on lawrence.ciantar@xyzcompany.com.mt or the Head of Human Resources on fanina.sciberras@xyzcompany.com.mt A copy of this policy, and related policies and procedures, can be found in the internal drive, Office files, Policies and Procedures. Employee Declaration I,____________________________________, have read and understand the above BYOD Policy, and consent to adhere to the rules outlined therein. ___________________________________ Employee Signature _______________________________ Date ___________________________________ ______________________________ Head of Human Resources Date