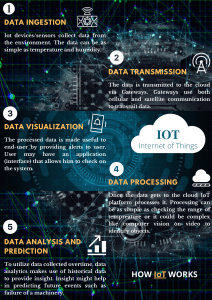
Module 3: Simulation Scenarios Models to Simulate Real-World Scenarios Application of the Models Stages of Data Lifecycle Reuse Existing IoT Solutions Reusability Plan Models to Simulate Real-World Scenarios Application of the Models Reference: 1. Arshdeep Bahga, Vijay Madisetti, “Internet of Things: A hands-on Approach”, University Press, 2015. 2. https://cocoa.ethz.ch/downloads/2014/01/1524_D1.3_Architectural_Reference_Model_update.pdf Functional Model The functional model is an abstract framework for understanding the main functionality groups of the IoT architecture environment and their relationships. Longitudinal Functionality Groups Application IoT Business Process Management Virtual Entity & IoT Service Service Organisation Communication Devices Transversal Functionality Groups Management Security Functional Model The functional model contains seven longitudinal functionality groups complemented by two transversal functionality groups. These transversal groups provide functionalities that are required by the longitudinal groups. The policies governing the transversal groups will not only be applied to the groups themselves, but do also pertain to the longitudinal groups. As an example: for a security policy to be effective, it must ensure that there is no functionality provided by a component that would circumvent the policy and provide an unauthorized access. The functional model is a layered model and the main communication flows between the FGs. Since the transversal FGs (Management & Security) interface with most of the other FGs, their relationships are not explicitly depicted. Functional Model Longitudinal Functionality groups IoT Business Process Management The IoT Business Process Management Functionality Group (BPM FG) relates to the integration of traditional business process management systems, as they are common in the enterprise world, with the IoT. Virtual Entity & IoT Service Service Organisation: It is the central functional group that acts as a communication hub between several other functional groups. Functional Model Longitudinal Functionality groups Communication The CFG ensures reliable communication and flow control. The CFG enables bridging among different networks, allowing Devices to perform as a network entry point implementing forwarding, filtering, connection tracking and packets aggregation functions. All those functionalities are as well supported by an error detection and correction infrastructure implemented by this FG. Transversal Functionality Groups Management The Management Functionality Group (Management FG) is responsible for the composition and tracking of actions that involve one or more other FGs. Example: Turning the entire IoT system into a sleep mode during an energy-harvesting cycle. Tracking of other FGs Security The Security Functionality Group (Security FG) is responsible for ensuring the security and privacy of the IoT system The Security FG is also in charge of protecting the user's private parameters IoT Design Methodology Steps IoT Design Methodology Steps for Home Automation System Purpose & Requirements Specification To identify the system purpose, behavior and requirements. Purpose: A home automation system that allows controlling of the lights in a home remotely using a web application. Behavior: The home automation system should have auto and manual modes. In auto mode, the system measures the light level in the room and switches on the light when it gets dark. In manual mode, the system provides the option of manually and remotely switching on/off the light. The requirements can be like data collection requirements, data analysis requirements, system management requirements, data privacy and security requirements, user interface requirements. • System Management Requirement: The system should provide remote monitoring and control functions. • Data Analysis Requirement: The system should perform local analysis of the data. • Application Deployment Requirement: The application should be deployed locally on the device, but should be accessible remotely. • Security Requirement: The system should have basic user authentication capability. Process Model Specification It formally describes the use cases of the IoT system based on the purpose and requirement specifications. Domain Model Specification The domain model describes the main concepts, entities and objects in the domain of IoT system to be designed. It defines the attributes of the objects and relationships between objects. It provides an abstract representation of the concepts, objects and entities in the IoT domain, independent of any specific technology or platform. The entities, objects and concepts include: Physical entity Virtual entity Device Resource Service Information Model Specification The Information Model defines the structure of all the information in the IoT system and adds more details to the Virtual Entities by defining their attributes and relations. But it does not describe the specifics of how the information is represented or stored. 0..* 0..* Service Specifications Service specifications define the services in the IoT system Service types Service inputs/output Service endpoints Service schedules 0..* 0..* IoT Level Specification Highlights the deployment level for IoT system Functional View Specification • It defines the functions of the IoT systems grouped into various functional groups. • The functional groups included in a functional view are: • Device • Communication • Services • Management • Security • Application Functional View Specification Operational View Specification In this step, various options pertaining to the IoT system deployment and operation are defined, such as, service hosting options, storage options, device options, application hosting options, etc Device & Component Integration The devices and components used here are: Raspberry Pi mini computer LDR sensor Relay switch actuator Application Development Auto Controls the light appliance automatically based on the lighting conditions in the room. Light When Auto mode is off, it is used for manually controlling the light appliance. When Auto mode is on, it reflects the current state of the light appliance. Stages of Data Life cycle The data life cycle is the sequence of stages that a particular unit of data goes through from its initial generation or capture to its eventual archival and/or deletion at the end of its useful life. The various phases of a typical data lifecycle are illustrated in the figures. Generation Creation Purging Capture Storage Archival Action Collection Analysis Storage Maintenance Usage Publication Synthesis Archival Usage Destruction Visualization Stages of Data life cycle Data Creation Data can be created in different forms like PDF, image, Word document or SQL database data and in any organization, data is created in one of the 3 ways: Data Acquisition: acquiring already existing data which has been produced outside the organization. Data Entry: manual entry of new data by personnel within the organization. Data Capture: capture of data generated by devices used in various processes in the organization. Storage Once data has been created, it needs to be stored and protected, with the appropriate level of security. A robust backup and recovery process should also be implemented to ensure retention of the data during the lifecycle. Usage During the usage phase of the data lifecycle, data is used to support activities in the organization. Data can be viewed, processed, modified and saved. An audit trail should be maintained for all critical data to ensure that all modifications to data are fully traceable. Data may also be made available to share with others outside the organization. Archival Data archival is the copying and removal of data from all active production environments where it is stored in case it is needed again, but where no maintenance or general usage occurs. If necessary, the data can be restored to an environment where it can be used. Destruction Data destruction or purging is the removal of every copy of a data item from an organization and is typically done from an archive storage location. The challenge of this phase is to ensure that the data has been properly destroyed. It is important to ensure before destroying data that the data items have exceeded their required regulatory retention period. Data lifecycle and its analysis Fundamental steps of a data analytics project plan(AI, Machine Learning and Big DATA) Define the Goal Get the Data Clean the Data Find Insights and Visualize Enrich the Data Iterate Deploy Machine Learning These seven data science steps ensure realization of business value from each unique project and mitigate the risk of error. Data lifecycle and its analysis Define the Goal Understand the business or activity of the data project Identify a clear objectives of what you want to do with data Get your Data Once the objectives are identified, collect and aggregate the data from different sources Ways to collect the data Query database(using technical skills like MySQL to process the data) Scrape from the websites Connect to Web APIs Obtain data directly from files (downloading it from Kaggle or existing corporate data which are stored in CSV) Data lifecycle and its analysis Explore and Clean the Data Clean the Data: Process of organizing and tidying up the data, removing what is no longer needed, replacing what is missing and standardizing the format of the collected data. Steps Involved Convert the data from one format to another and consolidate everything into one standardized format Filter the data Extracting and Replacing values(missing data sets or they could appear to be non-values, this is the time to replace them accordingly) Split, Merge and Extract data (For example, the place of origin, contains both “City” and “State”. Depending on the requirements, the data can be either merged or split) Data lifecycle and its analysis Explore the Data Once the data is ready to be used, and before processing using AI and Machine Learning, the data need to be examined figure out the business question and transform them into a data science question inspect the data and its properties compute descriptive statistics to extract features and test significant variables. Testing significant variables often is done with correlation. (e.g. exploring the risk of someone getting high blood pressure in relations to their height and weight) Enrich the Dataset Process of enhancing, refining, and improving raw data. Data lifecycle and its analysis Build Helpful Visualizations Visualization is the best way to explore and communicate the findings and is the next phase of data analytics project. Graphs are also another way to enrich the dataset and develop more interesting features Data visualization to helps to identify significant patterns and trends of the data. A better picture of the data can be obtained through simple charts like line charts or bar charts further to understand the importance of the data. Get Predictive Machine learning algorithms help in getting insights and predicting future trends Reduce the dimensionality of the data set and select the relevant ones which contribute to the prediction of results. Data lifecycle and its analysis Interpret models and data. The predictive power of a model lies in its ability to generalize i.e. the ability to generalize unseen future data Interpreting data refers to the presentation of data to a non-technical layman. This results in answering to the business questions stated in objective together with the actionable insights that is found through the data science process. Actionable insight is a key outcome of the data science process i.e. predictive analytics and later on prescriptive analytics(i.e. to repeat a positive result, or prevent a negative outcome). Iterate To make the data useful and accurate, need to constantly reevaluate, retrain it, and develop new features Reuse existing IoT solutions & Reusability Plan Reusing of existing components establish development of new technologies in less time and effort One of the main functionalities that can be reused is related to Device Management layer and the Blackbox reuse Steps Involved Identify the reusable asset Integrate the reusable asset Ways to integrate the reusable asset to the new system Black-box reuse - The assets are integrated in the new system simply as they are White-box reuse - new functionalities are implemented on the existing components for integrating them In IoT development, due to the large scale of operations when building applications it is important to know from the beginning the reuse strategy for integrating components based on the types of functionalities that can be reused. Reuse existing IoT solutions & Reusability Plan Evaluate the reusable asset: It is necessary to ensure that the quality of the reusable components does not compromise the overall quality of the application and they do not deteriorate the quality of the new system. Extendible - to handle the variability of heterogeneous devices and technologies Flexible - to easily adapt to changes caused by the external environment and implement new requirements, Reusable - to allow further reuse in future IoT applications, saving time and effort Functional - to offer several functionalities through APIs. Understandable and Effective What functionalities can be reused from IoT frameworks? Which reuse strategy should be adopted with respect to the functionality reused? What is the quality of the reused components with respect to the functionality reused? Reuse existing IoT solutions & Reusability Plan Re-usable Components Some of the reusable components are Cloud data storage Cloud service Sensors Controllers IoT platform Computing devices