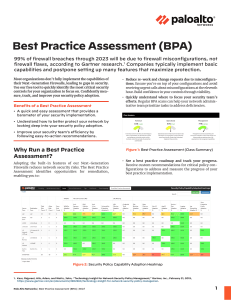
BPA and Security Assurance Implementing Zero trust BPA and Security Assurance Implement Security Minimize the chances of a successful intrusion. Identify the presence of attackers. Protect your valuable data Protect your customers, partners, and employees and thus protect the reputation of your business Help to achieve a Zero Trust security environment. Incident Management Identify and Prioritize Access and Run the BPA Security Assurance Identify and Prioritize Upload a Tech Support File on Customer Support Portal and Run the BPA Identify and prioritize the first area of improvement to begin the transition Use the BPA’s links to technical documentation to configure Best Practice Assessment From the BPA summary page, view Policies, Objects, Network, or Device detailed reports for the selected configuration assessment. From a detailed report, click the circled blue ? for descriptions and rationales for the configuration check and links to technical documentation for the best practice configuration. Access and Run the BPA Access the BPA from the Customer Support Portal Click the pencil icon to edit the Standard User to whom you want to assign BPA permissions.