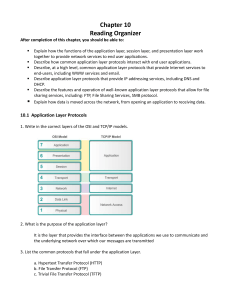
Name _______________________________________________________ Date ________________ Chapter 10 – Application Layer Study Guide Tips for success: While answering the questions read Chapter 9 and review the summary. All answers should be in RED type After completion of this chapter, you should be able to: Explain how the functions of the application layer, session layer, and presentation layer work together to provide network services to end user applications. Describe how common application layer protocols interact with end user applications. Describe, at a high level, common application layer protocols that provide Internet services to end-users, including WWW services and email. Describe application layer protocols that provide IP addressing services, including DNS and DHCP. Describe the features and operation of well-known application layer protocols that allow for file sharing services, including: FTP, File Sharing Services, SMB protocol. Explain how data is moved across the network, from opening an application to receiving data. 10.1 Application Layer Protocols 1. Write in the correct layers of the OSI and TCP/IP models. OSI Model TCP/IP Model 7 Application 6 Presentation 5 Session 4 Transport Transport 3 Network Internet 2 Data Link Application Network Access 1 Physical 2. What is the purpose of the application layer? It is the layer that provides the interface between the applications we use to communicate and the underlying network over which our messages are transmitted. IST 166 – Network Fundamentals Page 1 Luse – Spring 2018 3. List the common protocols that fall under the application Layer. a. Hypertext Transfer Protocol (HTTP) b. File Transfer Protocol (FTP) c. Trivial File Transfer Protocol (TFTP) d. Internet Message Access Protocol (IMAP) e. Domain Name System (DNS) protocol 4. The presentation layer has three primary functions. These are: a. Formats, or presents, data from the source device into a compatible form for receipt by the destination device. b. Compression of the data in a way that can be decompressed by the destination device. c. Encryption of the data for transmission and the decryption of data upon receipt by the destination. 5. List the common protocols that work in the presentation layer. Video: a. QuickTime b. Motion Picture Experts Group (MPEG) Graphic Image Formats: a. Graphics Interchange Format (GIF) b. Joint Photographic Experts Group (JPEG) c. Portable Network Graphics (PNG) 6. Explain in detail the function of the session layer. It functions at the session layer create and maintain dialogs between source and destination applications. The session layer handles the exchange of information to initiate dialogs, keep them active, and to restart sessions that are disrupted or idle for a long period of time. 7. The TCP/IP model Application layer is equal to which three OSI model layers? a. Application b. Presentation c. Session 8. List the protocols that fall under the TCO/IP model Application layer. a. Domain Name System (DNS) b. Telnet c. Simple Mail Transfer Protocol (SMTP) d. Dynamic Host Configuration Protocol (DHCP) e. Hypertext Transfer Protocol (HTTP) f. File Transfer Protocol (FTP) g. Trivial File Transfer Protocol (TFTP) h. Bootstrap Protocol (BOOTP) i. Post Office Protocol (POP) j. Internet Message Access Protocol (IMAP) 9. The P2P network model involves two parts, these are: IST 166 – Network Fundamentals Page 2 Luse – Spring 2018 a. P2P networks b. P2P applications 10. Why is it difficult to enforce security and access policies in networks containing more than just a few computers? P2P networks do not use centralized user accounts or access servers to maintain permissions. 11. A peer to peer (P2P) application allows a device to act as both a client and a server within the same communication. 12. In the client - server model, the device requesting the information is called a client and the device responding to the request is called a server. 13. At what layer of the OSI model is the Client and server processes are considered to be in? Application layer 10.2 Well - Known Application Layer Protocols and Service 14. Three application layer protocols that are involved in everyday work or play are: a. Hypertext Transfer Protocol (HTTP) b. Simple Mail Transfer Protocol (SMTP) c. Post Office Protocol (POP) 15. How does a browser interpret the three parts of the URL? a. http - the protocol or scheme b. www.cisco.com - the server name c. index.html - the specific filename requested 16. HTTP is a request/response protocol. 17. List and explain the three common message types used by HTTP. a. GET – a client request for data b. POST – POST and PUT are used to upload data files to the web server c. PUT – PUT uploads resources or content to the web server 18. Is HTTP a secure protocol? No 19. HTTPS uses the same client request server response process as HTTP. How is the data stream encrypted before being transported across the network? Secure Socket Layer (SSL) 20. Email is a Store and forward method of sending, storing, and retrieving electronic messages across a network. IST 166 – Network Fundamentals Page 3 Luse – Spring 2018 21. An email client does not communicate directly with another email client when sending email. Explain what happens. Both clients rely on the mail server to transport messages. This is true even when both users are in the same domain. 22. Email supports three separate protocols for operation. These are: a. Simple Mail Transfer Protocol (SMTP) b. Post Office Protocol (POP) c. Internet Message Access Protocol (IMAP) 23. Clients only use two application layer protocols to retrieve email. These are: a. POP b. IMAP 24. What is the purpose of SMTP? Simple Mail Transfer Protocol (SMTP) transfers mail reliably and efficiently. 25. Where must SMTP be running in order to operate correctly? On both the client and the server 26. What port number does SMTP use? 25 27. What is the purpose of Post Office Protocol (POP)? It enables a workstation to retrieve mail from a mail server. 28. What port number does POP use? 110 29. What is the purpose of Internet Message Access Protocol (IMAP)? It is another protocol that describes a method to retrieve email messages. 30. Explain in detail how is IMAP different from POP? When the user connects to an IMAP capable server, copies of the messages are downloaded to the client application. The original messages are kept on the server until manually deleted. Users view copies of the messages in their email client software. POP downloads the message to the local account. No copy is kept on the server. 31. On the Internet, domain names, such as http://www.cisco.com, are much easier for people to remember than 198.133.219.25, which is the numeric address for this server. Explain what happens if Cisco decides to change the numeric address of www.cisco.com. It is transparent to the user, because the domain name remains the same. The new address is simply linked to the existing domain name and connectivity is maintained. IST 166 – Network Fundamentals Page 4 Luse – Spring 2018 32. What is the purpose of a Domain Name System (DNS)? DNS uses a distributed set of servers to resolve the names associated with these numbered addresses. 33. Which Microsoft DOS command displays all of the cached DNS entries on a Windows computer system? ipconfig /displaydns 34. The DNS client, sometimes called the DNS resolver 35. Computer operating systems have a utility called nslookup. What does this allow users to do? It allows the user to manually query the name servers to resolve a given hostname. 36. What services does a DNS Server offer? a. assignment of IP addresses b. subnet masks c. gateway d. other IP networking parameters 37. How is DHCP a security risk? DHCP can pose a security risk because any device connected to the network can receive an address. 38. Explain how DHCP operates. The DHCP server maintains a pool of IP addresses and leases an address to any DHCP enabled client when the client is powered on. 39. What is the purpose of FTP? FTP was developed to allow for data transfers between a client and a server. 40. Explain what is a Server Message Block (SMB)? It is a client/server file sharing protocol, developed by IBM in the late 1980s, to describe the structure of shared network resources, such as directories, files, printers, and serial ports. It is a request - response protocol. 41. SMB messages can: a. Start, authenticate, and terminate sessions b. Control file and printer access c. Allow an application to send or receive messages to or from another device 42. SMB file - sharing and print services have become the mainstay of Microsoft networking. 10.3 The Message Heard Around the World IST 166 – Network Fundamentals Page 5 Luse – Spring 2018 43. What is the application layer is responsible for? Directly accessing the underlying processes that manage and deliver communication through the network IST 166 – Network Fundamentals Page 6 Luse – Spring 2018