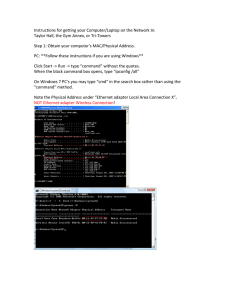
11/16
advertisement

COS 109 Monday November 16 • Housekeeping – Lab 6 and Problem Set 7 available now Lab 6 is due by midnight on Friday November 27 Problem Set 7 is due by 5 PM on Monday November 30 – Because these deadlines have been extended, there will be no further extensions • Today’s class – Finishing up software – Beginning a discussion of how networks (leading up to the internet) work Problem set 5 35 30 25 20 15 10 5 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 Average score 23.67 Two classmates turned in Pset 6; we’ll look forward to PSet5 today Are these pictures the same or different? Remember a picture is just a stream of (R,G,B) byte triples starting from the upper left and moving across each row in scan order. These pictures are 320x240 and so include 76,800 pixels and 230,400 bytes. Very first pixel on left picture is (244,244,234) Very first pixel on right picture is (244,245,234) NB 244 = 11110100 and 245 = 11110101 in binary A color exercise Same or different? One color or multiple colors? Colors of the top block R 61 60 56 48 G 236 236 232 224 B 230 228 224 224 Divisible by 1 4 8 16 What is going on here? Very first pixel on left picture is (244,244,234) Very first pixel on right picture is (244,245,234) NB 244 = 11110100 and 245 = 11110101 in binary • Human perception is limited and we are unlikely to be able to see small changes in color • We can take the LSB (least significant bit) and use it to encode a message • Steps • Set all LSB to 0 (some colors will change but imperceptible so) • You now have 230,400 bits in which to encode a message • Write you message and convert to ASCII • You can now encode 28,800 bytes (or characters in ASCII) • Almost 20 copies of the Gettysburg address This process is called steganography • A decade ago it was a popular means of communication among terrorists • Another example -- Same or different?? Message has been encoded; could start anywhere From http://news.engineering.iastate.edu/2010/04/09/unhidden-mathematician-works-to-combat-child-pornography/ An example Image size 500x320pixels With 24 bits of Color per pixel Total of 480,000 bytes Saint Olga planting Christianity in Russia, symbolized as a tree From www.textscience.com/images/steganographic.jpg Details In the image on the right the least significant bit for each color of some number of pixels was used to encode a hidden message “ The Gospel of Judas in its English translation by Kasser, Meyer, and Wurst.. These 480,000 bits allow the encoding of 60,000 bytes far more than enough for the short text of 17,845 bytes. The human eye cannot detect any difference between the full 24-bit color of the image on the left from the slightly modified image on the right. Special purpose systems • not all computers run a general-purpose operating system • game machines, cell phones, digital cameras, camcorders, e-book readers, … – may run a single program specialized to a single task – but increasingly these use versions of standard operating systems, most often Linux • it's often easier to build a new product if you can use offthe-shelf software as a controller – much less work to get started – easier to add new features Why software instead of hardware? • general-purpose software instead of special-purpose hardware: • software is – more flexible – easier to change in the field – cheaper to manufacture (though often costly to create originally) • hardware is – faster, more efficient – more reliable, more robust – more secure against intrusion, theft, reverse engineering • dividing line is not always clear – flash memory, etc. – plug-in cards, game cartridges Fundamental Software Ideas • algorithm: sequence of precise, unambiguous steps – performs some task and terminates – based on defined basic / primitive operations – describes a computation independent of implementation details • programming language: – grammar, syntax, and semantics for expressing computation notation is important • program: algorithms implemented in a programming language • compilers, interpreters: programs that convert from the high level language used by people to a lower level – a compiler is a program that writes a program – an interpreter also acts as a computer so the program can be run • libraries and components: programs written by others – packaged in a form that can be used in a new program • abstraction, layers, interfaces, virtualization – hiding details, pretending to be something else • bugs: the need for absolute precision – cover all cases, cope with failures and misuse Course high level outline • hardware (3-4 weeks) – how computers represent and process information – what's inside a computer, how it works, how it's built – the universality of a computer • software (3-4 weeks) • networks and the impact of internetworking (3-4 weeks) • along the way Course high level outline • hardware (3-4 weeks) • software (3-4 weeks) – – – – how we tell computers how to do things algorithms as recipes for computations a very gentle introduction to programming in Javascript programs that make us able to write programs, run apps, … • networks and the impact of internetworking (3-4 weeks) • along the way Survey (part 2) • Have you heard of • Have you held – – – – – – – – – – Random access memory Moore’s Law NP completeness Javascript Net neutrality Spambots The Cloud The internet TCP/IP Malware/ransomware – – – – – A transistor An integrated circuit A disk drive Memory A CPU Survey (part 2) • Have you heard of • Have you held – – – – – – – – – – Random access memory Moore’s Law NP completeness Javascript Net neutrality Spambots The Cloud The internet TCP/IP Malware/ransomware – – – – – A transistor An integrated circuit A disk drive Memory A CPU Survey (part 2) • Have you heard of • Have you held – – – – – – – – – – Random access memory Moore’s Law NP completeness Javascript Net neutrality Spambots The Cloud The internet TCP/IP Malware/ransomware – – – – – A transistor An integrated circuit A disk drive Memory A CPU Website of the day • How often are you seen? • How unique are you? • Prof or hobo Communications and networking • history and background – telephone system – local area networks, wide area networks (LANs and WANs) • Internet – architecture: what the pieces are and how they fit together – names and addresses: what's your name and number? Domain Name System, IP addresses – routing: how to get from here to there traceroute, ping – fundamental protocols and layers IP, TCP – higher level protocols and services: HTTP, SSH, SMTP, IMAP, ...; web, email, instant messaging, peer to peer, ... • Web – what makes it work: URL, HTTP, HTML, browser Early Communications (Technology?) • Runners (The Battle of Marathon) Phidippides was again called upon to run to Athens (26 miles away) to carry the news of the victory and the warning about the approaching Persian ships. Despite his fatigue after his recent run to Sparta and back and having fought all morning in heavy armor, Phidippides rose to the challenge. Pushing himself past normal limits of human endurance, the reached Athens in perhaps 3 hours, delivered his message and then died shortly thereafter from exhaustion. (From http://www.lakepowell.net/marathon.html) • Smoke signals In Ancient China, soldiers stationed along the Great Wall would alert each other of impending enemy attack by signaling from tower to tower. In this way, they were able to transmit a message as far away as 750 kilometres (470 mi) in just a few hours. (From https://en.wikipedia.org/wiki/Smoke_signal) • Carrier pigeons The sport of flying homing pigeons was well-established as early as 3000 years ago. They were used to proclaim the winner of the Olympics. Messenger pigeons were used as early as 1150 in Baghdad and also later by Genghis Khan. By 1167 a regular service between Baghdad and Syria had been established by Sultan NourEddin (From https://en.wikipedia.org/wiki/Homing_pigeon) More recent technology • signal lights ("1 if by land and 2 if by sea") "Old North Church Boston 1882". Licensed under Public Domain via Commons - https://commons.wikimedia.org/wiki/File:Old_North_Church_Boston_1882.jpg More recent technology • Town criers Pony Express True technology • Optical telegraph (Chappe, 1792) – – – – – faced many of the problems of modern networks protocols: rules by which independent parties exchange info bandwidth limitations: how to send information faster error detection and recovery security and privacy: protecting info from eavesdroppers & imposters Gerard Holzmann, The Early History of Data Networks • Telegraph (Morse, 1850's) – similar issues (and a new technology that killed the old one) Tom Standage, The Victorian Internet Telephone system (Alexander Graham Bell, 1876) • organizing principles, all based on voice traffic: – – – – – – – • • • • voice calls need only a narrow bandwidth channel a call uses a dedicated circuit, with long setup and hold times telephone number is a unique identifier fixed routing for a specific call parallel signaling network; data separated from control simple user interface: all intelligence inside network guarantees on quality of service; high reliability running out of some resources (area codes, 800/888/877/866, ...) traffic model changing rapidly (cell phones, data, ...) technology changing rapidly (wireless, Internet, ...) worldwide evolution from highly regulated and/or governmentoperated to deregulated / private – highly competitive – incumbent carriers threatened by Internet The Internet (a simple view) his computer your computer their computers her computer Amazon Google Princeton Local Area Networks ("LAN") his computer your computer her computer their computers network network Amazon Google Princeton Simple view of how Ethernet works • Messages are encoded • Messages are converted to bytes • Bytes are group together in packets of fixed size • Packets also contain header information • Source • Destination • Type of data • … • A single wire connects all devices • A message is put on the wire • Every device sees the message • Its destination receives the message Original drawings of Ethernet (Local Area Network) A complication • The Ethernet operates in a CSMA/CD mode • Carrier-sense multiple access with collision detection • Carrier-sense means listen to the wire until there is a lull in conversation • A collision can still happen if 2 machines try to put packets down at the same time (so need collision detection) • In case of collision, each machine backs off for a random amount of time Local Area Networks; Ethernet • a LAN connects computers ("hosts") in a small geographical area • Ethernet is the most widely used LAN technology – developed by Bob Metcalfe & David Boggs at Xerox PARC, 1973 – each host has a unique 48-bit identification number – data sent from one host to another in "packets" of 100-1500 bytes including source and destination address and error checking bits typical data rate 10-1000 Mbits/sec; limits on cable length packet: hdr src 8 6 dest 6 type 2 data 46-1500 bytes • wireless Ethernet uses radio to carry signals – logical behavior is exactly like a wired Ethernet check 4 My LAN at the moment I am writing this • IPV4 Address 192.168.0.8IPV6 Address MAC Address 78.E4.00.90.C7.C3Comments • Reserved IP-44 dBm Unique addresses (MAC addresses) • A media access control address (MAC address), also called physical address, is a unique identifier assigned to network interfaces for communications on the physical network segment. MAC addresses are used as a network address for most IEEE 802 network technologies, including Ethernet and WiFi. (from https://en.wikipedia.org/wiki/MAC_address) • MAC addresses are 6 bytes long (so 2566 possibilities ~ 280 trillion) • LAN assigns IP addresses that exist locally (local router is 192.168.0.1 and it owns the addresses 192.168.0.2 – 192.168.0.254 to assign) (more on this later) My LAN at the moment I am writing this • IPV4 Address 192.168.0.8IPV6 Address MAC Address 78.E4.00.90.C7.C3Comments • Reserved IP-44 dBm Details for dof-h87d0m1 IPV4 Address 192.168.0.8 IPV6 Address MAC Address 78.E4.00.90.C7.C3 Connecting networks (wide area networks / WAN) • how do we connect LANs to each other? – LANs may have different properties – may be far away • names & addresses now needed to find other networks and hosts • routing needed to find a path if multiple networks are involved – can't have each network connected directly to all others • protocols to agree on format of information and how it is exchanged – especially if networks are different kinds that use different format for packets different physical and electrical properties different names and addresses themselves • how do we handle errors, delays, overload, etc.? • how does it scale as the number of networks gets really big? Gateways and Routers his computer your computer their computers Router her computer network network Router Router Amazon Google Princeton My WAN connection The Internet • a huge number of independent networks that are connected – NOT a giant computer or a single network – each network may serve many host computers • nearby computers are connected by a local area network – most often Ethernet (including wireless) • information travels through networks in small "packets" – each packet independent of all others like individual envelopes through the mail – all packets have the same format – standard protocols for format of info and behavior • networks connected by specialized gateway computers (routers) – route packets of information from one network to the next – gateways continuously exchange routing information • each packet passes through multiple gateways – gateway passes packet to gateway that is closer to ultimate destination – gateways usually operated by different companies