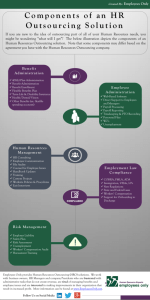
LINKING ITIL WITH OUTSOURCE SERVICES ROKHSAREH MOBARHAN UNIVERSITI TEKNOLOGI MALAYSIA
advertisement

LINKING ITIL WITH OUTSOURCE SERVICES ROKHSAREH MOBARHAN UNIVERSITI TEKNOLOGI MALAYSIA LINKING ITIL WITH OUTSOURCE SERVICES CASE STUDY: CENTER OF INFORMATION COMMUNICATION TECHNOLOGY IN UTM ROKHSAREH MOBARHAN A project report submitted in partial fulfillment of the requirements for the award of the degree of Master of Science (Information Technology – Management) Faculty of Computer Science and Information Systems Universiti Teknologi Malaysia NOVEMBER 2009 iii To my beloved husband and family for their encouragement, support and pray iv ACKNOWLEDGEMENT In the name of Allah, Most Gracious, Most Merciful. First and foremost I am grateful to ALLAH on His blessing in completing this thesis. I wish to express my sincere appreciation to my supervisor, Assoc. Prof. Dr. Azizah Abdul Rahman for encouragement, precious guidance and critics. Without her continued support and interest, this thesis would not have been the same as presented here, and also to the staffs of CICT, for their valuable feedback. I would also like to thank to all my family members for their prayers and all their supports and encouragements. My gratitude also goes to my beloved and wonderful husband, thank you for the encouragement, for being my inspiration, for the understanding you have given to me and most importantly, for your endless love. I thank you all. v ABSTRACT The arrival of the Internet and the rush to e-commerce has seen many companies look to outside vendors to supply necessary skills and competencies, as these are often not available in-house. Many large organizations are increasingly outsourcing their IT functions. Factors like lower costs, improved productivity, higher quality, higher customer satisfaction, and ability to focus on core areas are some of the benefits of outsourcing. However, there are many challenges and problems associated with IT outsourcing. As a strategic resource, outsourcing must be governed accordingly to mitigating the problems. In this project, I identify the main problems and challenges related to IT outsourcing. In addition, we delve into some important issues on IT outsourcing, particularly the challenges along with benefits. IT Infrastructure Library (ITIL®) delivers framework by providing best practices that provide governance on delivering quality, cost effective, and efficient IT services. So ITIL V3 will be used as a solution in this project. ITIL can be served as a framework for managing the relationship with an outsourcing service provider. This study will help the management to identify the problems and take the necessary remedial steps. In this project, a framework will be suggested that is arisen from the ITIL V3 framework for managing the outsourcing projects and there are some activities and suggestion to implementing each process. vi ABSTRAK Kemunculan internet dan e-dagang telah menyebabkan kebanyakan syarikat mencari pembekal luar untuk membekal kemahiran dan kompetensi yang diperlukan, Hal ini demikian kerana ia tidak didapati di rumah. Banyak organisasi besar semakin mengembangkan fungsi IT mereka kepada subkontraktor IT. Faktor-faktor seperti kos yang lebih rendah, produktiviti yang semakin meningkat, kualiti yang lebih tinggi, kepuasan pelanggan yang semakin tinggi, dan kemampuan untuk fokus pada bidang utama adalah beberapa manfaat kepada subkontraktor IT. Namun, terdapat banyak cabaran dan masalah yang berkaitan dengan subkontraktor IT. Sebagai sumber strategi, subkontraktor harus diatur dengan bijak untuk mengurangkan masalah. Dalam projek ini, saya telah mengenalpasti masalah dan cabaran utama yang berkaitan dengan subkontraktor IT. Selain itu, saya juga telah mengkaji beberapa isu penting khususnya cabaran dan faedah subkontraktor IT. IT Infrastructure Library (ITIL ®) menyampaikan rangka kerja dengan menyediakan amalan-amalan terbaik yang memberi kerajaan penyampaian terbaik, kos yang efektif dan perkhidmatan IT yang berkesan. ITIL V3 digunakan sebagai penyelesaian dalam projek ini. ITIL boleh dijadikan sebagai rangka kerja untuk menguruskan hubungan dengan pembekal perkhidmatan subkontraktor. Kajian ini akan membantu bahagian pengurusan untuk mengenalpasti masalah dan mengambil langkah-langkah pembaikan yang diperlukan. Dalam projek ini, sebuah rangka kerja dihasilkan dengan menggunakan ITIL V3 untuk menguruskan projek-projek subkontraktor dan beberapa saranan untuk aktiviti dan cadangan pelaksanaan masing-masing. vii TABLE OF CONTENT CHAPTER 1 TITLE PAGE TITLE i DECLARATION ii DEDICATION iii ACKNOWLEDGEMENT iv ABSTRACT v ABSTRAK vi TABLE OF CONTENTS vii LIST OF TABLES xi LIST OF FIGURES xii LIST OF ABBREVIATIONS xiv LIST OF APPENDICES xv PROJECT OVERVIEW 1 1.1 Introduction 1 1.2 Background of the problem 3 1.3 Statement of the problem 4 1.4 Project Objectives 5 1.5 Scope of the project 5 1.6 Importance of the project 6 1.7 Chapter Summary 7 viii 2 LITERATURE REVIEW 8 2.1 Introduction 8 2.2 Outsourcing 10 2.2.1 Definition of Outsourcing 11 2.2.2 Types of Outsourcing 12 2.2.3 Software Development 14 2.2.3.1 Software development life cycle (SDLC) 2.2.3.1.1 Planning Stage 15 2.2.3.1.2 Requirements definition Stage 16 2.2.3.1.3 Design Stage 17 2.2.3.1.4 Development Stage 19 2.2.3.1.5 Integration and test Stage 20 2.2.3.1.6 Installation and Acceptance Stage 21 2.2.3.2 Software development Outsourcing (SDO) 23 2.2.4 Steps of Outsourcing 24 2.2.5 Advantages of Outsourcing 32 2.2.6 Disadvantages of Outsourcing 35 2.2.7 Case study 37 2.2.7.1 Duct layout industry 37 2.2.7.2 Contact Advocate 40 2.2.8 Outsourcing Governance 42 2.3 IT Governance 14 45 2.3.1 Definition of IT Governance 47 2.3.2 IT Governance Focus Areas 51 2.3.3 IT Governance Frameworks 53 2.4 IT Infrastructure Library 56 2.4.1 ITIL Benefits 58 2.4.2 ITIL Evolution 60 2.4.2.1 ITIL V2 vs. V3 61 2.4.2.2 ITIL V3 books 62 2.4.2.2.1 Service Strategy 65 2.4.2.2.2 Service Design 67 2.4.2.2.3 Service Transition 71 2.4.2.2.4 Service Operation 74 ix 2.4.2.2.5 Continual Service Improvement 3 4 5 77 2.5 Chapter Summary 82 METHODOLOGY 83 3.1 Introduction 83 3.2 Project Methodology 84 3.2.1 Initial Planning Phase 86 3.2.2 Analysis 86 3.2.2.1 Literature Review 86 3.2.2.2 Identifying CICT problems 87 3.2.3 Develop a Proposed Framework 89 3.3 Chapter Summary 89 INITIAL FINDINGS 90 4.1 Introduction 90 4.2 Organizational Analysis 91 4.2.1 CICT Mission, Vision and Objectives 92 4.2.2 CICT Organizational Structure 93 4.3 Questionnaire and Interview Analysis 94 4.4 suitable component of ITIL for outsourcing 99 4.5 general proposed framework 102 4.6 Chapter summary 103 FRAMEWORK REFINEMENT 104 5.1 Introduction 104 5.2 Proposed framework design 105 5.2.1 ITIL Implementation Framework 105 5.2.1.1 Phase 1 106 5.2.1.2 Phase 2 107 5.2.1.3 Phase 3 109 x 5.2.1.4 Phase 4 5.2.2 Framework implementation roadmap 111 5.2.2.1 Incident Management Process 114 5.2.2.2 Problem Management Process 117 5.2.2.3 Financial Management Process 118 5.2.2.4 Service level management 120 5.2.2.5 Change management 122 5.2.2.6 Supplier management 125 5.2.2.7 Information Security Management 127 5.2.2.8 Service Evaluation 129 5.3 OMF Implementation Project Organizational Structure 5.3.1 Implementation team and groups 132 132 5.3.1.1 Steering Group 132 5.3.1.2 ITIL Implementation Project Manager 133 5.3.1.3 Implementation Teams 134 5.3.2 Framework Applying Steps 134 5.4 Framework verification 136 5.5 Framework Finalization 136 5.5.1 Risk Management 6 111 137 5.6 Chapter Summary 141 DISCUSSION AND CONCLUSION 142 6.1 Achievements 142 6.2 Constraints and Challenges 143 6.3 Recommendations 144 6.4 Chapter Summary 145 REFERENCES APPENDICES A-E 146 151-167 xi LIST OF TABLES TABLE NO. TITLE PAGE 2.1 Definitions of IT governance 49 2.2 ITIL V3 processes and sub processes 80 4.1 Summary of interview analyzing 98 4.2 ITIL V3 processes regarding outsourcing 100 5.1 benefits of the framework processes for CICT 130 xii LIST OF FIGURES FIGURE NO. TITLE PAGE 2.1 Literature Review Framework 9 2.2 Outsourcing 12 2.3 SDLC Stages 15 2.4 Input and output of planning stage 16 2.5 Input and output of requirements definition stage 17 2.6 Input and output of Design stage 18 2.7 Input and output of Development stage 19 2.8 Input and output of Integration and Test stage 21 2.9 Input and output of installation and acceptance stage 22 2.10 Steps of Outsourcing 26 2.11 Outsourcing challenges 43 2.12 Key Aspects of Outsourcing Governance 44 2.13 Evolution of the IT Function within organizations 45 2.14 IT Governance objectives 50 2.15 Focus areas of IT Governance 51 2.16 The service lifecycle 62 2.17 Key links, inputs & outputs of the service lifecycle 64 2.18 Service Design 68 2.19 Service Transition 72 2.20 Service Operation 75 xiii 2.21 Continual Service Improvements 78 3.1 Project Methodology Framework 85 4.1 CICT Organizational Chart 94 4.2 general proposed framework 102 5.1 Outsourcing Management Framework 106 5.2 Framework implementation roadmap 112 5.3 suggested Incident/Problem Report Form 116 5.4 Framework implementation Steps 135 5.5 Finalized OM Framework for CICT 139 5.6 OMF for software Development Projects 140 xiv LIST OF ABBREVIATIONS CCTA – Central Computer and Telecommunications Agency CMM – Capability Maturity Model COBIT – Control Objectives for Information and Related Technology CSI – Continual Service Improvement DSL – Definitive Software Library EDA – Exploratory Data Analysis IACEP – Informational and Analytical Centre of Environmental Protection ITGI – Information Technology Governance Institute ITIL – IT Infrastructure Library ITSCM – Information Technology Service Continuity Management OGC – Office of Government Commerce OLA – Operating Level Agreement RFC – Request for Change ROI – Return on Investment SDO – Software Development Outsourcing SLA – Service Level Agreement SLM – Service Level Management SQP – Service Quality Plan OMF _ Outsourcing Management Framework xv LIST OF APPENDICES APPENDIX TITLE PAGE A Interview Questions 151 B Questionnaire 152 C UTM Suggested List 155 D Suggested SLA Template 156 E Acceptance Test for OM Framework 162 CHAPTER 1 PROJECT OVERVIEW 1.1 Introduction In recent years Information Technology has become an inseparable part of every organizations and the existence of an organization crucially depends on the effective application of IT. With the emergence of e-commerce, the use of technology is becoming just an accepted, indeed expected way of conducting business and also a way of creating new opportunities that provide them with a source of competitive advantage [1]. The arrival of the Internet and the rush to e-commerce has seen many companies look to outside vendors to supply necessary skills and competencies, as these are often not available in-house. Because developing e-commerce applications can place great demands on companies, and managers often conclude that the only 2 way to meet short deadlines for new technology projects is to contract for specialist services [1]. However, the challenges for IT managers are to co-ordinate and work in partnership with the business to deliver high quality IT services [43]. Due to enhanced focus on the customer in the planning, development and delivery of information services, IT service management (ITSM) has become increasingly important. ITSM strives to the better alignment of IT efforts to business needs and to manage the efficient providing of IT services with guaranteed quality [54]. There are some mechanisms for implementing Information Technology Governance like COBIT, ITIL, Six Sigma, and CMM, CMMI. In this trend towards embracing principles of organizational IT Service Management, the IT Infrastructure Library (ITIL) has become the worldwide de facto standard in Service Management. It is a set of books describing IT management processes and practices [45]. Globally, most of the IT organizations are currently focused on using ITIL to implement and improving IT Support and Delivery processes. 3 1.2 Background of the problem In today’s global economy, outsourcing has become a very common phenomenon. Many large organizations have outsourced some or all of their IT functions. Factors like lower costs, improved productivity, higher quality, higher customer satisfaction, time to market, and ability to focus on core areas are some of the benefits of outsourcing [2]. However, there are many challenges and risks associated with outsourcing like Management challenges, Cultural/language communication risks, Security risks, Knowledge transfer challenges, loss of flexibility in reacting to changing business conditions, lack of customer focus, contractual misunderstandings, Hidden costs, and maintaining outsourcing relationships[2]. The Centre for Information and Communication Technology (CICT) in UTM is responsible for ensuring that staffs and students have access to teaching, learning and research resources by providing the University's IT infrastructure, acquiring, developing and supporting new and emerging technologies and systems, and providing access to millions of digital resources across the University's campuses. The vision of CICT is to become the source of quality and innovative ICT services towards achieving the University's aspirations. It had and has many programs for achieving these goals and objectives, such as Human Resource System, Finance System, Document Management, Enterprise Portal, Smart Card System, Business Intelligent and others. CICT uses outsourcing for some of these projects. In spite of many advantages that outsourcing brought for them, they are facing some problems like misunderstanding, quality, cost problems. 4 According to the cited problems, it is so important to have a well managed plan for outsourcing actions. Furthermore ITIL is not only an effective tool for managing internal IT processes. It can also serve as a framework for managing the relationship with an outsourcing service provider. 1.3 Statement of the Problem This research attempts to find the answers to some problems related to: i. What is CICT situation and its problem when conducting with the software development outsourcing projects? ii. What are the elements in ITIL v3 framework that are suitable for this case study? iii. How to best manage software development outsourcing projects? iv. How ITIL can be used to manage CICT outsourcing projects? In this research is intended to use a relevant research methodology to analyze the data that will be gathered and arrive with the suggestions for the improvement that can benefit the organization, which would enhance outsourcing management performance. 5 1.4 Project Objectives This project will focus on the following five objectives: i. To identify challenges and problems those arise during outsourcing project. ii. To understand the CICT situation and its problem when conducting with the outsourcing, especially software development outsourcing projects. iii. To analyze of how a manager can manage and supervise outsourcing projects and give some suggestions which arise from ITIL methodology. iv. To determine elements in ITIL v3 those are suitable for adapting to CICT to manage the outsourcing projects. v. To propose a framework towards the adoption or adaptation of ITIL for the Software Development Outsourcing Projects. 1.5 Scope of the project This study will concentrate on the Outsourcing projects, especially software development outsourcing, it’s conducting problems and challenges, and as a case study CICT will be analyzed. In this project, Information Technology Infrastructure Library (ITIL) will be used for solving the problems associated with outsourcing, so it will cover an overall view of ITIL V3 Framework and it component. 6 1.6 Importance of the project When someone decided to use outsourcing services, it is imperative to: • Select the right partner • Identify issues related to outsourced project management. • Improve outsourcing management issues Furthermore, it is important to understand the: • Security during outsourcing • Relationship with the outsourcer • Relevant risks • Process used for development a contract To ensure the success of outsourcing, the client and provider are required to confront some critical challenges. The outsourcings should be govern to control and mitigate the risks and to ensure that the outsourcing deliver value to the organization [63]. So, this research project will significantly focus on find the problems of outsourcing and try to give some solutions using ITIL framework. In other words, it will try to implement the ITIL framework for managing the software development outsourcing projects. The main aim of this project is to propose a framework for governing the Software Development Outsourcing. 7 1.7 Chapter Summary Introduction of the research project, background of the problem, statement of the problem, problem objectives, and scope of the project was identified in this chapter. CHAPTER 2 LITRITURE REVIEW 2.1 Introduction The Literature Review covers all the areas that are of interest to the research study. The purpose of this chapter is to aid the author in having deeper knowledge and understanding on the research areas. Some concepts such as definitions, technologies, best practices and case studies of the current system will be analyzed. For readers, this chapter provides a general view of subject background, problems and some useful solutions. The study areas that shall be discussed are divided into five main themes that are the Outsourcing, IT Governance, ITIL, ITIL V2 overview, ITIL V3 and also CICT problems. Figure 2-1 shows the Literature Review framework of the project. 9 Literature Review 2.2 Outsourcing 2.2.1 Definition of outsourcing 2.2.2 Types of Outsourcing 2.2.3 Software Development 2.2.4 Outsourcing advantages 2.2.5 Outsourcing disadvantages 2.2.6 Steps of Outsourcing 2.2.7 Case Study 2.2.8 Outsourcing Governance 2.3 IT Governance 2.3.1 IT Governance Definition 2.3.2 IT Governance focus Areas 2.3.3 IT Governance Frameworks 2.4 ITIL 2.4.1.1 Benefits 2.4.2 ITIL Evolution 2.4.2.1 ITIL v2 vs. V3 2.4.2.2 ITIL V3 Books 2.4.2.2.1 Service strategy 2.4.2.2.2 Service design 2.4.2.2.3 Service transition 2.4.2.2.4 Service operation 2.4.2.2.5 Continual 2.5 Conclusion Figure 2.1 Literature Review Framework Service Improvements 10 2.2 Outsourcing Due to rapidly Advances in technology, increasingly demand for IT applications and the inadequate supply of IT personnel [1], Managers and senior executives are becoming increasingly aware of challenges and opportunities in order to be more efficient and effective in delivering products and services to customers While the changing nature of competition has placed firms under heavy pressure to rapidly develop and commercialize new innovations to ensure their survival, the successful release of new products undoubtedly brings firms plenty of profits and revenue growth. To remain competitive, firms must also pursue product innovation through both internal and external services [6]. Generally, the term “outsourcing” is used to describe external providing of services. The outsourcing of IT can be traced back to the 1960s when computers were expensive and physically large. During that period, computers required considerable space and controlled environmental conditions so as to operate them successfully. This situation demanded that companies had to make substantial capital investments in order to have their own computing facilities. In order to avoid such expenditure, many organizations contracted out their routine data processing, particularly payroll and accounting, to large data-processing service bureau [1]. In today’s global economy, outsourcing has become a very common phenomenon. Many large organizations have outsourced some or all of their IT functions. Factors like lower costs, improved productivity, higher quality, higher customer satisfaction, time to market, and ability to focus on core areas are some of the benefits of outsourcing. However, there are many challenges and risks associated with IT outsourcing [2]. 11 2.2.1 Definition of Outsourcing In broad terms Outsourcing refers to a company that contracts with another company to provide services that might otherwise be performed by in-house employees [3]. Outsourcing is usually used when a company takes a part of its business and gives that part to another company [4]. In other word, Outsourcing is an approach to task management that involves utilizing resources that are outside the direct control of the company to handle tasks that are relevant to the operation and success of the business [14]. The outside firms that are providing the outsourcing services are third-party providers, or as they are more commonly called, service providers. But as a complete definition, Outsourcing is as an act of delegating or transferring some or all of the IT related decision making rights, business processes, internal activities, and services to external providers, who develop, manage, and administer these activities in accordance with agreed upon deliverables, performance standards and outputs, as set forth in the contractual agreement. Typically, the function being outsourced is considered non-core to the business [24]. Generally, this involves contracting with a service provider to handle the specific function for a specific period of time and with guidelines that are agreeable to both parties. In some cases, the service may be granted limited power to act in the stead of the client, if that is necessary to perform the contracted tasks [14]. The recipients for outsourced activities are generally in the same country. When a company on another country is involved e.g. India, the correct term to use is “offshore outsourcing”. “Nearshore outsourcing” refers to outsourced projects that are outside the country, but on the same continent e.g. a US company outsourcing. 12 In recent times, the Outsourcing has been most commonly used for technology related initiatives such as handing over the IT help-desk to a third-party. But it can also refer to non-technical services such as handing over the telephonebased customer service department [4]. Deliver determined product Client Vendor Payment Figure 2.2 Outsourcing 2.2.2 Types of Outsourcing Whereas Outsourcing has become an increasingly important issue for many organizations, it categorized in different types. this categorization is based on the nature of work being outsourced. • Business Process Outsourcing (BPO): The first type, BPO, is the contracting of a specific business task to a third-party service provider. Originally, this was associated with manufacturing firms, such as Coca Cola that outsourced large segments of its supply chain. In the contemporary context, it is primarily used to refer to the outsourcing of services. It includes call center outsourcing, human 13 resources outsourcing (HRO), finance and accounting outsourcing and payroll and claims processing outsourcing [9, 8]. Many of these BPO efforts involve offshoring -- hiring a company based in another country -- to do the work. India is a popular location for BPO activities [8]. • Information Technology Outsourcing (ITO): The second is Information Technology Outsourcing. It is a company's outsourcing of computer or Internet related work, such as programming, to other companies. It is used in reference to Business Process Outsourcing or BPO, which is the outsourcing of the work that does not require much of technical skills. ITO includes IT services, technical support, software testing, and website management outsourcing [9]. • Software development outsourcing (SDO): The third type is Software R&D or also known as software development outsourcing. It is provision of software development services by an external supplier [7]. I will go details of this part, because my focus is on the SDO projects. • Knowledge Process Outsourcing (KPO): The forth one, KPO, is a form of outsourcing, in which knowledge-related and information-related work is carried out by workers in a different company or by a subsidiary of the same organization. Unlike the outsourcing of manufacturing, this typically involves high-value work carried out by highly skilled staff. KPO firms, in addition to providing expertise in the processes themselves, often make many low level business decisions—typically those that are easily undone if they conflict with higher-level business plans [10]. • Legal process outsourcing (LPO): Finally, LPO is an activity or practice to get legal support services from legal services' firms or corporations. In the 14 beginning, LPO covered mostly low-end transcription work (Data management, Word Processing, Litigation support, Book-keeping and reconciliations etc.) but now it includes a huge range of legal processes, such as patent application drafting, legal research, pre-litigation documentation, advising clients, writing software licensing agreements and drafting distribution agreements[11]. 2.2.3 Software development A software development process is a structure imposed on the development of a software product. Synonyms include software life cycle and software process. 2.2.3.1 Software development life cycle (SDLC) SDLC is a process of logical stages taken to develop a software product. The six stages of the SDLC are designed to build on one another, taking the outputs from the previous stage, adding additional effort, and producing results that leverage the previous effort and are directly traceable to the previous stages. This top-down approach is intended to result in a quality product that satisfies the original intentions of the customer [64]. Figure 2.4 illustrates SDLC stages. 15 Project Planning Requirements Definition Design Development Integration & Test Installation &Acceptance Figure 2.3 SDLC Stages 2.2.3.1.1 Planning Stage The planning stage establishes a bird's eye view of the intended software product, and uses this to establish the basic project structure, evaluate feasibility and risks associated with the project, and describe appropriate management and technical approaches. 16 Figure 2.4 Input and output of planning stage [64] The outputs of the project planning stage are the configuration management plan, the quality assurance plan, and the project plan and schedule, with a detailed listing of scheduled activities for the upcoming Requirements stage, and high-level estimates of effort for the out stages. 2.2.3.1.2 Requirements definition Stage The requirements gathering process takes as its input the goals identified in the high-level requirements section of the project plan. Each goal will be refined into a set of one or more requirements. These requirements define the major functions of the intended application, define operational data areas and reference data areas, and define the initial data entities. Major functions include critical processes to be managed, as well as mission 17 critical inputs, outputs and reports. A user class hierarchy is developed and associated with these major functions, data areas, and data entities. Figure 2.5 Input and output of requirements definition stage [64] The outputs of the requirements definition stage include the requirements document, the RTM, and an updated project plan. 2.2.3.1.3 Design Stage The design stage takes as its initial input the requirements identified in the approved requirements document. For each requirement, a set of one or more design elements will be produced as a result of interviews, workshops, and/or prototype efforts. 18 Design elements describe the desired software features in detail, and generally include functional hierarchy diagrams, screen layout diagrams, tables of business rules, business process diagrams, pseudo code, and a complete entityrelationship diagram with a full data dictionary. These design elements are intended to describe the software in sufficient detail that skilled programmers may develop the software with minimal additional input. Figure 2.6 Input and output of Design stage [64] When the design document is finalized and accepted, the RTM is updated to show that each design element is formally associated with a specific requirement. The outputs of the design stage are the design document, an updated RTM, and an updated project plan. 19 2.2.3.1.4 Development Stage The development stage takes as its primary input the design elements described in the approved design document. For each design element, a set of one or more software artifacts will be produced. Software artifacts include but are not limited to menus, dialogs, data management forms, data reporting formats, and specialized procedures and functions. Appropriate test cases will be developed for each set of functionally related software artifacts, and an online help system will be developed to guide users in their interactions with the software. Figure 2.7 Input and output of Development stage [64] The outputs of the development stage include a fully functional set of software that satisfies the requirements and design elements previously documented, an online help system that describes the operation of the software, an implementation map that identifies the primary code entry points for all major system functions, a 20 test plan that describes the test cases to be used to validate the correctness and completeness of the software, an updated RTM, and an updated project plan. 2.2.3.1.5 Integration and test Stage During the integration and test stage, the software artifacts, online help, and test data are migrated from the development environment to a separate test environment. At this point, all test cases are run to verify the correctness and completeness of the software. Successful execution of the test suite confirms a robust and complete migration capability. During this stage, reference data is finalized for production use and production users are identified and linked to their appropriate roles. The final reference data (or links to reference data source files) and production user list are compiled into the Production Initiation Plan. 21 Figure 2.8 Input and output of Integration and Test stage [64] The outputs of the integration and test stage include an integrated set of software, an online help system, an implementation map, a production initiation plan that describes reference data and production users, an acceptance plan which contains the final suite of test cases, and an updated project plan. 2.2.3.1.6 Installation and Acceptance Stage During the installation and acceptance stage, the software artifacts, online help, and initial production data are loaded onto the production server. At this point, all test cases are run to verify the correctness and completeness of the software. Successful execution of the test suite is a prerequisite to acceptance of the software by the customer. 22 After customer personnel have verified that the initial production data load is correct and the test suite has been executed with satisfactory results, the customer formally accepts the delivery of the software. Figure 2.9 Input and output of installation and acceptance stage [64] The primary outputs of the installation and acceptance stage include a production application, a completed acceptance test suite, and a memorandum of customer acceptance of the software. Finally, the PDR enters the last of the actual labor data into the project schedule and locks the project as a permanent project record. At this point the PDR "locks" the project by archiving all software items, the implementation map, the source code, and the documentation for future reference. 23 2.2.3.2 Software development Outsourcing (SDO) Outsourced product development has become the most feasible solution in the IT world for the development of software products. This is because not only is it cost effective but it’s the sure shot means for producing top-quality products. There are very many outsourced product development firms that are ready to undertake this task at a reasonable cost without compromising on quality. Not only that, they also bring in new and innovative ideas in product development. The term software outsourcing has been described as a situation where in a customer contacts a software development company for the part or complete development of a software product or delivering an IT enabled service. The software outsourcing with an external organization can be for development of complete or partial software products, the purchase of packaged or customized software products or involving the vendor in the full software development cycle & also contract with him for maintenance after delivery [65]. Most companies take up the option of outsourcing the development phase of software due to several factors such as to minimize costs, bring in additional resources or channelize their time and resources for core activities. Whatever be the reason, outsourced product development is now making quite a stir in the IT world. The different types of software outsourcing can be broadly described as below: I. In-house software development (no outsourcing): Many organizations have their own IT departments catering to their software needs. These 24 organizations develop the required software and information systems within their own capacity and productivity limits. II. Product Component outsourcing: In product component outsourcing, the developer is contracted to develop one or several parts of a software system. In case of complex systems when the organization does not have the capacity or required skill to develop a particular component such component is outsourced. III. Process Component Outsourcing: In outsourcing parts of software development cycle, the customer organization contracts for an external group to perform all or certain functions of one or more of their process steps or components. IV. Software Acquisition (Total outsourcing): In this type, the organization outsource each and every activity associated with the software which includes design, development, programming, testing and maintenance .The main reason for such type of outsourcing is to focus on the organizations core values. 2.2.4 Steps of Outsourcing With the development of the complex and strategic of outsourcing, IT outsourcing decision becomes more complex [14]. The decision to outsource IT is 25 not an easy one to make. Experience highlights that it demands considerable managerial attention and should not be made without rigorous analysis and discussion [1]. Figuring out whether or not the company should pack up some part of production and ship it to outsourcers can be a difficult choice to make [12]. Each business will have different priorities and concerns, which will drive the outsourcing decision. The selection process needs to be rigorous [15]. Outsourcing needs to be undertaken systematically and handled like any other major business project. Outsourcing is still too often driven by gut feel, promises of short-term gains and response to the smart sales staff of the outsourcing service providers [15]. It can offer definite advantages, but only if it’s done right. To do the job properly a number of steps need to be considered by the business in its considerations of outsourcing strategies and plans. 26 1 Understand Company’s objective, business strategy, mission and vision 2 Plan the RFI 3 4 5 6 Prepare the RFP Vender Selection Contracts and negotiation Ongoing supplier management Figure 2.10 Steps of Outsourcing Step1: Understand Company’s objective, business strategy, mission and vision. The client company needs to understand its mission, vision and business strategy to decide if outsourcing and partnering are viable strategic options. The mission and objectives of the business must be understood together with the critical success factors, in particular in terms of customer and shareholder demands. Outsourcing of complete processes should be the aim, but before that decision is made, the core competencies must be identified and understood [15]. 27 Also company needs to describe the process, service or product that they want outsourced clearly. They should indicate what their goals are through outsourcing [18]. Step2: Find out all you need to know about the vendor (Plan the RFI) This stage of the process begins testing of the market for vendor resources which have the skills, interest, capability and equally as important, the corporate culture and flexibility to become the company’s outsourcing partner. This stage anticipates the preparation and issuance of a Request for Information (RFI) to the specific market sector [19]. The RFI provides material for the first rounds of vendor evaluations. It also spells out the business requirements defined by the core team, so the vendor understands what the company is trying to accomplish [18]. Frequently, candidate vendors are already known by the company through past or existing supplier/vendor relationships. Care should be taken during this Step to test the management philosophy of the vendor with regard to customer care and protection, degree of service level commitment, and overall business philosophy. Other areas for investigation include historical performance as measured by client reference, vendor outsourcing market share & experience, and overall approach to be a partner in the outsourcing program. The RFI provides the outsourcing vendor the opportunity to describe his skills, to show his wares and to reveal his philosophical viewpoints on the conduct of business [19]. 28 Contents of RFI • The type of information usually sought by RFI’s includes things such as: The availability of equipment or needed services. The approximate one time and recurring costs. The differentiating factors between the goods or services proposed and similar offerings from other vendors. • The latter is very useful in providing information to help determine mandatory and desirable characteristics to be included in an RFP. After vendors return the questionnaire, the issuing company matches the vendors’ responses to the company’s requirements and weights the criteria based on importance. Providers that don’t meet stated needs or haven’t responded to the specific questions are eliminated. Eventually, the RFI process helps companies make the "go or no go" decision—that is, the choice to proceed with or walk away from a project. The data solicited identifies the availability and viability of outsourcing, cost estimate ranges, and risks. It also provides detail useful for developing project requirements [18]. Step 3: Prepare the RFP The third step is to develop the RFP; send it to short-listed suppliers; evaluate them; and, finally, select the best ones. 29 The RFI and RFP are complementary. Information collected during the RFI process can prepare the solution requirements section of the related RFP. Leveraging the information-gathering focus of the RFI will lead to a concise RFP that articulates the business needs [18]. But Unlike a Request for Information (RFI), an RFP is designed to get suppliers to provide a creative solution to a business problem or issue. RFPs should be used carefully since they can take a lot of time for both the organization and its suppliers. However, for more complex projects, an RFP may be the most effective way to source the goods or services required [20, 21]. The RFP outlines the engagement’s requirements—relevant skill sets, language skills, intellectual property protection, infrastructure, and quality certifications—and gives prospective vendors the information necessary to prepare a bid. The responsibility of developing the RFP rests with the project’s sourcing leader, but various aspects of the document will require input from other domain experts [18]. A good RFP includes one section that states what the company seeks (business requirements) and four sections that ask about the vendor and what it will be able to provide [18]: • Business requirements. In brief, this section details the company’s project goal, deliverables, performance and fulfillment requirements, and liquidity damages. • Vendor profile. External service providers differ greatly in performance, style, and experience. This part of the RFP details the vendor’s stability, services, and reputation. • Vendor employee information. This section addresses the resources assigned at the project management, middle management, team leader, and task levels, along with the quality of people, their skills, training, 30 compensation, and retention. If the company ranks technical skills highest should look at technical expertise before examining costs. • Vendor methodology. The methodology segment details project management, quality, regulatory compliance and security. • Infrastructure. This part outlines the vendor’s infrastructure stability and disaster-recovery abilities. Step4: Vender Selection After vendors have sent their RFP responses, the evaluation is begun. When vendors respond to an RFP, if the proposal meets the stated requirements, each vendor must then undergo a due diligence review [18]. In depth due diligence takes place s to ensure that the vendors are financially sound and likely to be able to deliver as promised. Activity levels, the impact of changes in activity levels, the performance KPIs and the measurement processes are just some of the factors agreed together with service level agreements (SLAs), all specified in clear, unambiguous, measurable form [15]. The length and formality of the due diligence process varies according to companies’ experience with outsourcing, the timeline for implementing outsourcing, the risk, and familiarity with the vendor [18]. 31 Step5: Contracts and negotiation Negotiations and contracts with an outsource provider are a complex area requiring procurement and negotiation skills as well as legal skills and in-depth knowledge of the subject matter under consideration, i.e. experts who understand the current processes and their scope, strengths and weaknesses [15, 21]. Contracts are about identifying costs and deliverables, sharing of risk, service levels agreements and control processes. Negotiations are a prime opportunity for the outsourcing partner to add income without increasing effort and for the client company to add value without adding cost. This is not a trivial activity and requires much skill and tenacity [15]. Step6: Ongoing supplier management Once the Outsourced programme is implemented, there is an ongoing need for supplier relationship management to ensure that the outsourced process is fully integrated with the business and the process performance is monitored to meet contractual as well as business needs is safeguarded. If critical business processes are outsourced it is paramount that the supplier is integrated into the client's management processes and communications [15]. 32 2.2.5 Advantages of Outsourcing Organizations who are interested in outsourcing are often curious to know more about advantages and disadvantages of outsourcing. By gaining insight about both the good and bad of outsourcing, organizations can decide if outsourcing is right for them. Most organization jump headlong into outsourcing, without actually finding out if outsourcing is good for their business. The advantages and disadvantages of outsourcing can help the organization decide if outsourcing is right for their business [15]. There are several good reasons to consider outsourcing, including: I. Cost Reduction: One of the most common benefits is cost reduction. What this means is that an organization delegates a job to a vendor who can perform the same job at a much lower cost. The comparative cost advantage that a vendor offers forms the basis for outsourcing [1, 2, 13, 15, 22, and 23]. Depending on the function, there is a good chance that choosing to outsource the task will be cheaper than buying necessary equipment, hiring and training personnel, and actually doing the work necessary to successfully complete the task [13]. II. Focus on core business: Another advantage of outsourcing is that it allows company to focus on core business processes and activities [2, 13, 15, 21, and 22] and to improve its competitive advantage to enable organization’s strategic goals, quality and reliability, professional services, and higher customer satisfaction [2]. In other words, the operating principle is to retain the activities that deliver customer value and shareholder value and outsource the rest. On the other hand, Outsourcing system allows companies to contract for services that are not within the scope of their expertise, so that they can focus their time, 33 money and energy on their core competencies instead of wasting valuable resources trying to gain Understanding of areas that are somebody else's expertise [22]. III. Reduce capitalization and their fixed cost base: Some organizations outsource to reduce capitalization and their fixed cost base. In order to flex business volumes and product mix in a business dealing with heavily fluctuating demand, the asset base needs to be kept low. Business assets include all assets of the business such as fixed assets, inventories and human assets (i.e. permanently employed staff). Outsourcing some or all of the asset intensive activities such as manufacturing may be a good way of achieving that [1, 15]. IV. Access to specialist resources: It is sometimes possible to gain access to specialist resources by outsourcing. By outsourcing company can get expert and skilled services Service levels can be increased by appreciating that a company is unlikely to be good at everything and that specialist suppliers can add significant value by applying their specialist skills - and possibly economies of scale - on behalf of their customers [15, 1]. V. Increase productivity: Productivity means getting more accomplished starts outsourcing; it must break down duties into smaller tasks. These tasks become part of an organized process, where each person involved becomes an efficient specialist, as opposed to a generalist who tries to do everything. When workers are able to focus on a limited number of tasks, they will become more efficient in performing their duties. They know what is expected from them and they are not distracted by having new demands put on them. When 34 someone is trying to juggle too many conflicting tasks at once, the person won’t be able to do all of them well [25]. VI. Access better technology at a lower cost: Technology is changing rapidly and it is expensive for companies to keep up with the latest advances. Instead of investing the considerable financial resources necessary to continuously upgrade equipment and train staff, it may make more sense to “borrow” the technology from a company that has already made this investment. When a company enters into an agreement with another company to provide some services involving new technology, both parties benefit. One of them reaps the benefit of the other company’s investment and the company that already bought the equipment gains needed capital [25]. VII. Make faster deliveries to customers: Another benefit of outsourcing is that company can make quicker deliveries to customers. Third-party contractors will be able to provide faster deliverables because the existence of a contract puts pressure on the supplier, compared with internal development, to deliver a quality product on time and within budget, and the company in turn will be able to make quick deliveries to its customer. Faster deliveries can also help them save on time [1]. VIII. Improved customer satisfaction: With timely deliveries and high-quality services you can impress your customers. Outsourcing can help you benefit from increased customer satisfaction and your customers will remain loyal to your organization [26]. 35 IX. Share Risk: Investing in new technology can be a risky proposition for businesses today. Rather than putting up its own funds, it may make more sense for a business to use outsourcing to ensure that the technology available to them is always up to date and relevant to their needs [26]. Apart from the above factors there are other reasons as to why a company would want to outsource. These include: 9 Improving technical expertise. 9 Gaining access to technical talent and technical expertise not available inhouse. 9 Gaining access to new technologies. 9 Improve efficiency 9 Save on manpower and training costs 9 Increase flexibility 2.2.6 Disadvantages of outsourcing While the benefits of outsourcing can be obvious and immediate, there are still a few potential disadvantages to keep in mind. Often, these are minor, and may not even be issues at all in some situations. However, every organization can and should consider them before choosing to outsource any company function. Disadvantages of outsourcing are: 36 I. Loss of real-time control: When any given business function is conducted inhouse, it is a simple task to step in and order some type of a change if necessary. For example, when billing is done in-house, it is very easy to apply a credit to a customer invoice when the product or service did not live up to the promises made to the client. If the billing process is outsourced, there may be several steps to go through in order to submit a credit. Even then, if the invoice is already generated, there may be no way to apply the credit in real time, or there may be an extra charge for the service [13]. II. Threat to Security and Confidentiality: It is possible that since data is moved around, leakages or even misuse of information can happen especially in sensitive industries such as those in the technology sectors. Also the knowledge obtained by the supplier from the company may be transferred to competitors [54]. III. Hidden Costs: Anything not covered in the contract will be the basis for the company to pay additional charges. Additionally, it will experience legal fees to retain a lawyer to review the contacts will be signed. This is the outsourcing company's business. They have done this before and they are the ones that write the contract. Therefore, you will be at a disadvantage when negotiations start [55]. IV. Communication is very crucial: Working miles away, may lead to loss of data or inappropriate data if not handled wisely which may lead to misunderstanding [56]. 37 V. Loss of internally generated talent: It may hamper the growth of an employee by depriving him from the experience he would have gained by handling the business issue himself [56]. Also it has some other disadvantages like: 9 Possible loss of flexibility in reacting to changing business conditions. 9 Maybe some Quality problems 2.2.7 Case study 2.2.7.1 Duct layout industry The client is a leading US-based player in the global duct layout industry space. They needed a partner who could handle their outsourcing services that included duct design and drafting, duct Layout, financial, software development and website analytics services. In the Ducting design arena, the partner would need to understand the ducting industry, interact with both the development team at the customer’s engineering department and the customer’s dealers, and design duct layouts for specific industries all over USA. Down the line, the partner would need to generate invoices from drawings produced, handle online updating of the customer’s product lines, and expand services to the customer’s overseas offices in UK. 38 The Challenge The number of drawings that the customer needed to provide its dealers was growing at an enormous rate, and they needed drawings with a quick turnaround time. Outsource2india was approached by the company with the task of learning about their line of products, and using both commercial software as well as software developed by them to design duct layouts. The challenge lay in the fact that drawings had to be professionally drawn with a high degree of accuracy, and should easily be modifiable. The bigger challenge was that the turnaround time would need to steeply increase with time to meet the high demands from growing demands from the customer’s side. Demands have since grown by a factor of 10. The Solution Outsource2india quickly started the process at a small size and quickly ramped up the quality and turnaround time by which the drawings were delivered. A team was set up to manage key CTQs (Critical To Quality parameters). In three months, their ability to deliver drawings had increased threefold. Given the volume of the drawings, they shifted to the FTE model and had engineers from Outsource2india serving as part of the customer’s team in the US. 39 Within another month, orders had grown almost 10- fold. Maintaining the highest level of quality, the output was matching demand. The illustration shows how the demand for drawings grew over 7 months, all the demand being met by engineers at Outsource2india. The Results Quality: Accuracy of the drawings produced at O2I was so high that inventory planning and invoicing started to be carried out based on these drawings. Value: Use of automation through programming is delivering not only productivity but also increasing accuracy of work carried out every day.. So far, Outsource2india has crossed over 330 projects in 10 months. A highly satisfied client has decided to extend his requirements to other services. Soon, they started developing software, providing Data management solutions, financial 40 services, and Website optimization services. So it brings them cost saving and high quality product. 2.2.7.2 Contact Advocate Contact Advocate is into offering event planning and management services to various industries. Business meetings, conferences of companies is handled efficiently may it be at a national or local level. The Challenges With a ever growing business, Contact Advocate wanted a secure event planning system that would help the company meet its requirements on a real time basis. Company could not have offered a big sum to any service provider. So what Contact Advocate wanted was a cost effective, innovative and a user-friendly system. Solution MachroTech had utmost faith in what CA was doing, hence decided to partner with it. Machrotech decided to develop the system in coordination with its outsourcing development center in India, knowing that budget was a constraint for Contact Advocate. Contact Advocate provides tools for organizations through which they can manage their events like meetings, easily and effectively. MachroTech’s outsourcing development team developed some really exclusive features within the system. This system provides proprietary event matching engine, which would match 41 the events, to the users profile given in the database. The system also has a unique system of automatically sending mails to users, which would match their interests. Another feature is the InfiNet Network. This system intelligently finds the common link in the users address book and determines the best path through which the desired individual would be contacted. Everything was done securely. The users had total freedom and control over whom they wanted to help make business connections. Results MachroTech's Global Software Delivery model enabled CA to take the software to market in less than 10 weeks. One event that CA promoted recently,in Stamford, Connecticut drew over 200 attendees and 30 walk-ups despite a snowstorm! That is because the event leveraged online registration and email marketing to promote and manage the event. Ultimately, the cancellation rates were extremely low and the satisfaction rates high because of the user-friendliness of the system and its tools. Some interesting statistics gathered from management personnel: • Attendance expectations were surpassed by 100% using the Contact Advocate tools • Actual revenue surpassed expected revenue by 75% • The cancellation rate was less than 2% • Walk-up represented an additional 30% • Overall satisfaction of the online registration process was high 42 2.2.8 Outsourcing Governance Outsourcing is the mechanism that allows organizations to transfer the delivery of services to third parties. Fundamental to outsourcing is accepting that, while service delivery is transferred, accountability remains firmly with the remit of the client organization, which must ensure that the risks are managed and there is continued delivery of value from the service provider. Transparency and ownership of the decision-making process must reside within the purview of the client [58]. In outsourcing relationships there is an emerging interest in IT governance [1, 59, and 60]. IT governance is specifying the decision rights and accountability framework to encourage desirable behavior in using IT [61]. As a strategic resource, outsourcing must be governed accordingly. This is not just about purchasing but about effective management and ensuring that both parties benefit. Governance of outsourcing is the set of responsibilities, roles, objectives, interfaces and controls required to anticipate change and manage the introduction, maintenance, performance, costs and control of third-party provided services. It is an active process that the client and service provider must adopt to provide a common, consistent and effective approach that identifies the necessary information, relationships, controls and exchanges among many stakeholders across both parties [58]. To ensure the success of outsourcing, the client and provider are required to confront some critical challenges, which are illustrated in Figure 2.11. When the client transfers an internal capability to an outside party, they lose some control over that capability [62]. 43 Figure 2.11 outsourcing challenges [62] The organizational and technical challenges brought by outsourcing force the client and the provider to establish or redesign corresponding governance mechanisms such as processes to deal with the changes. All of these should be governed in a consistent and effective way. The issues addressed by governance are mainly in two categories [63]: (1) To ensure that outsourcing delivers value to organization. Pursuit for long–term business needs and competitive advantage has driven the need of strategic outsourcing, which has become an important consideration in the strategy making process in every business. Two issues should be explored to reach the ideal state: Is the company getting the outsourced done well? Is the company getting benefits from outsourcing? They are related to outsourcing performance and benefits. (2) To control and minimize the risks. The risks of outsourcing highlight the need both to outsource the right things and to outsource them in the right way. They are related to outsourcing decision and processes. Mitigation of risks is also 44 driven by embedding accountability into the business. Therefore, the ownership and accountability for outsourcing decisions should be assigned appropriately. Therefore, the five aspects of outsourcing including outsourcing decisions, processes, benefits, performance, and accountability should be governed effectively. The loop of outsourcing governance is illustrated in Figure 2.12. Outsourcing Decisions Do right things Outsourcing Processes Outsourcing Accountability Do things right Clear accountability Outsourcing Benefits Get benefits from things Outsourcing Performance Do things well Figure 2.12 Key Aspects of Outsourcing Governance 45 2.3 IT Governance Information Technology (IT) plays a vital role in managing transactions, information & knowledge that is necessary to initiate and support economic and social activities. In many organizations, IT is essential and an integral part of the business to support, sustain and grow the business [27, 28]. Over the years, IT has become the backbone of businesses to the point where it would be impossible for many to function (never mind succeed) without it. IT is no longer separate from but is an essential element of the enterprise [32]. As a result of its increasing role in the enterprise, the IT function is changing. Figure 2.13 Evolution of the IT Function within organizations [33] When evolving from technology providers into strategic partners, IT organizations typically follow a three-stage approach as depicted in Figure 2.13. Each evolutionary stage builds upon the others beginning with IT infrastructure 46 management (ITIM). During this stage, the IT organizations focus on improving the management of the enterprise infrastructure. Effective infrastructure management means maximizing return on computing assets and taking control of the infrastructure, the devices it contains and the data it generates. The next stage, IT service management (ITSM), sees the IT organizations actively identifying the services its customers need and focusing on planning and delivering those services to meet availability, performance, and security requirements. In addition, IT is managing service-level agreements, both internally and externally, to meet agreedupon quality and cost targets. Ultimately, when IT organizations evolve to IT business value management (IT Governance), they are transformed into true business partners enabling new business opportunities. In that stage, IT processes are fully integrated with the complete lifecycle of business processes improving service quality and business agility [33]. IT without governance is reactive, unable to plan, acquire or develop the correct skills or understand priorities. For instance, without a structured process, all projects are number-one priorities. With budgets being flat or minimally increasing, it is difficult to know where to focus. IT governance processes allow IT to understand and manage IT-enabled business change. The business determines priorities and defines investments, allowing IT to identify their staffing requirements and make investments in the correct skill sets or training at the correct time, ensuring value to the organization [28]. Boards and executive management need to extend governance to IT and provide the leadership, organizational structures and processes that ensure that the enterprise’s IT sustains and extends the enterprise’s strategies and objectives. IT governance is not an isolated discipline. It is an integral part of overall enterprise governance. The need to integrate IT governance with overall governance is similar to the need for IT to be an integral part of the enterprise rather than something practiced in remote corners or ivory towers [27]. 47 With the huge growth of IT spending in organizations and the strong evidence toward better IT decision making, it is time to make IT governance more professional[30].Every organization, large and small, public and private, needs a way to ensure that the IT function sustains the organization’s strategies and objectives. The level of sophistication that the company applies to IT governance, however, may vary according to size, industry or applicable regulations. In general, the larger and more regulated the organization, the more detailed the IT governance structure should be [29]. 2.3.1 Definition of IT Governance At its basic definition, “IT governance is the process by which decisions are made around IT investments. How decisions are made, who makes the decisions, who is held accountable, and how the results of decisions are measured and monitored are all parts of IT governance” [34]. Gembergene [35] defines IT governance as “the organizational capacity exercised by the board, executive management and IT management to control the formulation and implementation of IT strategy and in this way ensure the fusion of business and IT”. In 2001, the IT Governance Institute (ITGI) suggested that the “IT Governance is the responsibility of the Board of Directors and executive management. It is an integral part of enterprise governance and consists of the leadership and organizational structures and processes that ensure that the 48 organization’s IT sustains and extends the organization’s strategy and objectives”. Key to this definition is the notion of alignment of the IT with the Business also referred to as Strategic Alignment [27, 32]. IT governance also defined as the strategic alignment of IT with the business such that maximum business value is achieved though the development and maintenance of effective IT control and accountability, performance management, and risk management [36]. Governance is used to describe many different aspects of IT change. At the low level, it is sometimes used to describe project management and control. More often it is used to describe the management and controls of a portfolio of projects. It is used to make sure that IT change processes comply to regulatory requirements. Sometimes it covers the deployment of IT staff. Governance aligns IT change and expenditure to business change and expenditure [31]. Governance is also used to describe the management and control of IT services. Service Level Agreements (SLAs) are used to define levels of service that are acceptable to business, and then used as a basis for monitoring services. Governance makes sure that day-to-day problem fixing and support are aligned to business needs [31]. Table 2.1 shows different definitions of IT Governance. 49 Table 2.1 Definitions of IT governance Researchers IT governance definitions Brown and Magill (1994) IT governance describes the locus of responsibility for IT functions. Luftman (1996) IT governance is the degree to which the authority for making IT decisions is defined and shared among management, and the processes managers in both IT and business organizations apply in setting IT priorities and the allocation of IT resources. Sambamurthy and Zmud (1999) IT governance refers to the patterns of authority for key IT activities. Van Grembergen (2002) IT governance is the organizational capacity by the board, executive management and IT management to control the formulation and implementation of IT strategy and in this way ensure the fusion of business and IT. Weill and Vitale (2002) IT governance describes a firm’s overall process for sharing decision rights about IT and monitoring the performance of IT investments. Schwarz and Hirschheim (2003) IT governance consists of IT-related structures or architectures (and associated authority patterns), implemented to successfully accomplish (IT-imperative) activities in response to an enterprise’s environment and strategic imperatives. IT Governance Institute (2004) IT governance is the responsibility of the board of directors and executive management. It is an integral part of enterprise governance and consists of the leadership and organizational structures and processes that ensure that the organization’s IT sustains and extends the organization’s strategies and objectives. Weill and Ross (2004) IT governance is specifying the decision rights and accountability framework to encourage desirable behavior in using IT. 50 Besides three major components of IT Governance (structure, process and communication) there are four objectives that drive IT governance (Figure 2.5) and must be covered in IT Governance processes: IT value and alignment, accountability, performance measurement, and risk management [34]: • IT value and alignment. One of the primary goals of IT governance to ensure alignment between the business units and IT and delivering value for them. • Risk management. Managing IT risk is important and includes security risks, privacy risks, recovery, resiliency systems and the risks associated to project failures. • Accountability. IT governance insures IT management for the return on its investment in IT. • Performance measurement. IT governance requires some metrics and measurement for evaluating and controlling three other dimensions (IT value and alignment, Risk management and Accountability). Figure2.14 IT Governance objectives [34] 51 2.3.2 IT Governance Focus Areas Fundamentally, IT governance is concerned about two things: IT’s delivery of value to the business and mitigation of IT risks. The first is driven by strategic alignment of IT with the business. The second is driven by embedding accountability into the enterprise. Both need to be supported by adequate resources and measured to ensure that the results are obtained. This leads to the five main focus areas for IT governance, all driven by stakeholder value. Two of them are outcomes: value delivery and risk management. Three of them are drivers: strategic alignment, resource management (which overlays them all) and performance measurement [27]. Figure2.15 Focus areas of IT Governance [27] I. Strategic alignment: Linking business and IT so they work well together. Typically, the lightning rod is the planning process, and true alignment can occur only when the corporate side of the business communicates effectively 52 with line-of-business leaders and IT leaders about costs, reporting and impacts. II. Value delivery: Making sure that the IT department does what’s necessary to deliver the benefits promised at the beginning of a project or investment. The best way to get a handle on everything is by developing a process to ensure that certain functions are accelerated when the value proposition is growing, and eliminating functions when the value decreases. III. Resource management: One way to manage resources more effectively is to organize your staff more efficiently—for example, by skills instead of by line of business. This allows organizations to deploy employees to various lines of business on a demand basis. IV. Risk management: Instituting a formal risk framework that puts some rigor around how IT measures, accepts and manages risk, as well as reporting on what IT is managing in terms of risk. V. Performance measures: Putting structure around measuring business performance. One popular method involves instituting an IT Balanced Scorecard, which examines where IT makes a contribution in terms of achieving business goals, being a responsible user of resources and developing people. It uses both qualitative and quantitative measures to get those answers [27, 29]. 53 2.3.3 IT Governance Frameworks Implementing good IT governance requires a framework based on three major elements [34]: • Structure. The framework must answer this questions: ”Who makes the decisions? What structural organizations will be created, who will take part in these organizations, and what responsibilities will they assume? “ • Process. In the process aspect, these questions must be answered: “How are IT investment decisions made? What are the decision-making processes for proposing investments, reviewing investments, approving investments, and prioritizing investments? “ • Communication. Communication deals with of how the results of these processes and decisions will be monitored, measured, and communicated. Also it needs some mechanisms to communicate IT investment decisions to the board of directors, executive management, business management, IT management, employees, and shareholders. Over the years, a number of frameworks have emerged, each with their own strengths and weaknesses, but also, each with their own focus and purpose. Some of the major frameworks are currently as below: 54 • IT Infrastructure Library (ITIL): is a customizable framework of best practices that promote quality computing services in the information technology (IT) sector. ITIL addresses the organizational structure and skill requirements for an IT organization by presenting a comprehensive set of management procedures with which an organization can manage its IT operations. • Control Objectives for Information and Related Technology (COBIT): is a set of best practices (framework) for information technology management created by the Information Systems Audit and Control Association (ISACA), and the It is a framework for information security that provides managers, auditors, and IT users with a set of generally accepted measures, indicators, processes and best practices to assist them in maximizing the benefits derived through the use of information technology and developing appropriate IT governance and control in a company [37]. It is comprised of 34 high-level control objectives and 318 detailed control objectives that have been designed to help businesses maintain effective control over IT [38]. • Six Sigma: is a data-driven quality control standard that was originated by the Motorola Company in the 1980s and was designed to help eliminate the rate of defects perceived to be caused by manufacturing variation. An organization that achieves Six Sigma is required to have, at the most, 3.4 defects for every one million customer requirements. Sigma is a term used in statistics to represent standard deviation, an indicator of the degree of variation in a set of measurements or a process [39]. • The Capability Maturity Model (CMM): is a method for evaluating and measuring the maturity of the software development process in organizations on a scale of 0 to 5. Its rating scale was developed by the Software Engineering Institute at Carnegie Mellon University. A revised version, the 55 Capability Maturity Model Integration (CMMI), provides guidance for improving an organization’s processes and a way to manage the development, acquisition and maintenance of products or services [40]. If your goal is improving the quality and measurability of IT governance across the entire networked application implementation life cycle or implementing a control system for improved regulatory compliance, COBIT probably would be a more effective choice [41]. If your organization is ready for a company-wide, team-focused approach to quality, also it has a serious commitment to employee education and on the other hand it wants to develop and maintain structured business improvement skills, Six Sigma is the best choice [42]. If the objective is to continuously improve IT operations efficiency and IT customer service quality, ITIL would probably be the better bet [41]. All of these Frameworks provide methodologies that can be used to improve the processes that company has in place. However, these methodologies provide little or no guidance about which processes are required for IT to function well. The ITIL framework is a source of good practice in service management. ITIL provides a guide to the framework of processes required to run IT as a Business for the Business and the relationship between those processes [48]. 56 2.4 IT Infrastructure Library The Information Technology Infrastructure Library (ITIL) is a English language set of documents consisting of several volumes of IT management concepts, processes and methods. The guidance, documented in a set of books, describe an integrated, process based, best practice framework for managing IT services [44]. ITIL has been published in Great Britain by the Central Computer and Telecommunications Agency (CCTA) under the IT Infrastructure Library label since the late 1980’s. The CCTA has now become a part of the Office of Government Commerce (OGC), which took over ownership of ITIL. For the further development of ITIL, the OGC is cooperating with the BSI, the itSMF (IT Service Management Forum), an increasingly influential association of ITIL users, and also with the two IT Service Management examination institutes, the Dutch EXIN (Exameninstitut voor Informatica) and the British ISEB (Information Systems Examination Board). The OGC is still coordinating office [45]. ITIL is a public framework that describes Best Practice in IT service management. It provides a framework for the governance of IT, the ‘service wrap’, and focuses on the continual measurement and improvement of the quality of IT service delivered, from both a business and a customer perspective. This focus is a major factor in ITIL’s worldwide success and has contributed to its prolific usage and to the key benefits obtained by those organizations deploying the techniques and processes throughout their organizations. 57 ITIL provides “best practice” guidelines and architectures to ensure that IT processes are closely aligned to business processes and that IT delivers the correct and appropriate business solutions [43]. ITIL is intended to assist organizations in optimizing their own IT service management practices. Worldwide, ITIL is the most widely used best practice for IT Service Management. ITIL is a top-down, business driven approach to the management of IT Services that specifically addresses the strategic business value generated by the IT organization and the delivery of high quality IT services. ITIL is designed to focus on the people, processes and technology issues that IT organizations face. ITIL is aimed at: • IT service providers • IT directors and managers • Chief Information officers It will also inform: • Business managers • Customers and end-users involved in building good relationships with their IT service providers plus any organization that depends on IT Services. ITIL provides the foundation for quality IT service management. The widespread adoption of ITIL guidance has encouraged organizations worldwide, both commercial and non-profit, to develop supporting products as part of a shared 'ITIL philosophy'. The Information Technology Service Management Forum (itSMF) is a global consortium of more than 400 international corporations and 4,000 individual members responsible for advancing IT best practices through the 58 utilization of the IT Infrastructure Library (ITIL), which provides a structured framework consisting of systematic and professional road maps for managing complex IT environments [47]. 2.4.1 ITIL Benefits One of the main objectives of ITIL is to assist IT service provider organizations “to improve IT efficiency and effectiveness whilst improving the overall quality of service to the business within imposed cost constraints” [49]. ITIL offers a systematic, professional approach to the management of IT service provision. Benefits realized by many IT organizations through implementing ITIL and processes based on “best practice” guidelines are [43, 44, and 49]: • Increasing customer satisfaction with IT services • Better communication and information flows between IT staff and customers • Continuous improvement in the delivery of quality IT services • Reduced long term costs through improved ROI or reduced TCO through process improvement • Greater productivity and better use of skills and experience • Demonstrable VFM to the business, the board and stakeholders, through greater efficiency Standards and guidance for IT staff • Reduced risk of not meeting business objectives, through the delivery of rapidly recoverable, consistent services 59 • Improved communication and better working relationships between IT and the business • The ability to absorb a higher rate of Change with an improved, measurable rate of success • Processes and procedures that can be audited for compliance to “best practice” guidelines • Improved ability to counter take-over, mergers and outsourcing. There are also benefits to the customer of IT services, such as: • Reassurance that IT services are provided in accordance with documented procedures that can be audited • The ability to depend upon IT services, enabling the customer to meet business objectives • The identification of contact points for enquiries or discussions about changing requirements • The knowledge that information is produced to justify charges for IT services and to provide feedback from monitoring of service level agreements ITIL emphasizes the importance of providing IT services to satisfy business needs in a cost effective manner. Many IT organizations are attempting to become more customer oriented to demonstrate their contribution to the business. The library can help IT organizations achieve this. Organizations are encouraged to adapt the guidance to suit their needs. They are however, cautioned against omitting activities without due consideration, since IT Service Management is a set of integrated and coordinated functions. 60 Organizations are likely to gain most benefit – in the longer term– from implementing all of the functions rather than some discrete functions. ITIL provides a consistent and comprehensive approach to service management ranging from software products to consultancy, training and qualifications. The common approach brings with it a common language of ITIL terms, which permits better communication between IT and suppliers [44]. 2.4.2 ITIL Evolution The first version of ITIL was initially developed in the 1980’s by the forerunner to the OGC (CCTA) and was used mainly by government agencies. It consisted of a variety of booklets based on work done by the UK Government Information Infrastructure Management Forum [46]. It consisted of a library of 31 associated books covering all aspects of IT service provision [43]. This initial version was then revised and replaced by seven, more closely connected and consistent books (ITIL V2) consolidated within an overall framework. The two most widely read focused on service delivery and service support. These two books present the foundation for IT service management (ITSM), which is a set of 10 management processes that provide guidance and best practices on managing assets, bugs, changes, disasters, efficiency, and finances. The model shows the goals, general activities, inputs, and outputs of the various processes and facilitates communication and cooperation among various functions in IT [43, 46]. 61 In 2007, ITIL V2 was superseded by an enhanced and consolidated third version of ITIL, consisting of five core books covering the service lifecycle, together with the Official Introduction [43]. The newest version, is fundamentally different from previous versions. ITIL v3 focuses on the entire service life cycle, taking the ultimate consumer of the services — the business — into consideration [46]. 2.4.2.1 ITIL V2 vs. V3 There is a greater focus on the strategy of IT within an organization and on continual improvement. The emphasis in the new books is that processes alone are not enough to guarantee business success. Processes have to form part of the overall strategy of the business, and have to be directly linked to business outcomes, to be effective. The lifecycle in the new books shows how this can be achieved In addition, there are some significant differences in the format. The previous eight books are being replaced with 5 new books covering an ITSM Lifecycle [67]. However any changes to the basic processes are not very radical. Problem Management has been streamlined, Request Fulfillment has been pulled out from Incident Management and given more prominence and more has been added on Event Management. Most of the best practices from previous versions of ITIL remain intact and still valid [67]. Overall V3 will provide generic guidance for any type of Service Provider, increase the scope of Service Management and provide more depth over V2. 62 2.4.2.2 ITIL V3 books ITIL version 3 is a set of five new books, the ITIL Service Lifecycle, replaced the previous Service Support and Service Delivery books, and other related volumes. The main development is that V3 takes a lifecycle approach to guidance, as opposed to organizing according to IT delivery sectors [43]. Figure2.16 The service lifecycle [43] The five core books cover each stage of the service lifecycle (Figure 2.18), from the initial definition and analysis of business requirements in Service Strategy and 63 Service Design, through migration into the live environment within Service Transition, to live operation and improvement in Service Operation and Continual Service Improvement. The core books are the starting point for ITIL V3. It is intended that the content of these core books will be enhanced by additional complementary publications and by a set of supporting web services [43]. The ITIL V3 books are as below: I. Service Strategy: focusing on providing guidance on how to leverage service management capabilities that effectively deliver value to customers. II. III. Service Design: translates plans and objectives into action items. Service Transition—looks at how the design delivers the intended strategy, and whether it can be effectively executed. Change management is an important component. IV. Service Operation: this is the day-to-day service management guidance. V. Continual Service Improvement: performance measurement and improvement through the life of the service. The figure 2.17, illustrates how the service lifecycle is initiated from a change in requirements in the business. 64 Figure2.17 Key links, inputs & outputs of the service lifecycle stages [43] These requirements are identified and agreed within the Service Strategy stage within a Service Level Package (SLP) and a defined set of business outcomes. This passes to the Service Design stage where a service solution is produced together with a Service Design Package (SDP) containing everything necessary to take this service through the remaining stages of the lifecycle. The SDP passes to the Service Transition stage, where the service is evaluated, tested and validated, the Service Knowledge Management System (SKMS) is updated, and the service is transitioned into the live environment, where it enters the Service Operation stage. 65 Wherever possible, Continual Service Improvement identifies opportunities for the improvement of weaknesses or failures anywhere within any of the lifecycle stages [43]. 2.4.2.2.1 Service Strategy The IT Infrastructure Library (ITIL) version 3 Service Strategies book sits at the core of the ITIL V3 lifecycle and provides senior leadership with guidance on how to leverage service management capabilities to effectively deliver value to customers and capture value for service providers. Achieving a deep understanding of customer needs, in terms of what these needs are, and when and why they occur, also requires a clear understanding of exactly who is an existing or potential customer of that service provider. This, in turn, requires the service provider to understand the wider context of the current and potential market places that the service provider operates in, or may wish to operate in [43]. “The Service Strategy volume provides guidance on how to design, develop, and implement service management not only as an organizational capability but also as a strategic asset. Guidance is provided on the principles underpinning the practice of service management that are useful for developing service management policies, guidelines and processes across the ITIL Service Lifecycle”[50]. There are many topics covered in Service Strategy volume. The development of markets, internal and external, service assets, Service Catalogue, and implementation of strategy through the Service Lifecycle, Financial Management, Service Portfolio Management, Organizational Development, and Strategic Risks are major topics which included in Service Strategy [50]. 66 Organizations can use the guidance to set objectives and expectations of performance, also to identify, select, and prioritize opportunities. Service Strategy help organizations to handle the costs and risks associated with their Service Portfolios. [50] It sets out guidance to all IT service providers and their customers, to help them operate and thrive in the long term by building a clear service strategy. Some questions that can be answered with this guidance are of the following kind [43]: • What services should we offer and to whom? • How do we truly create value for our customers? • How do we capture value for our stakeholders? • How can we make a case for strategic investments? • How can Financial Management provide visibility and control over value creation? • How should we define service quality? There are three sub processes including: I. Financial Management: Financial Management covers the function and processes responsible for managing an IT service provider’s budgeting, accounting and charging requirements. It provides the business and IT with the quantification, in financial terms, of the value of IT services, the value of the assets underlying the provisioning of those services, and the qualification of operational forecasting. 67 II. Service Portfolio Management (SPM): SPM involves proactive management of the investment across the service lifecycle, including those services in the concept, design and transition pipeline, as well as live services defined in the various service catalogues and retired services. III. Demand Management (DM): Demand management is a critical aspect of service management. The purpose of Demand Management is to understand and influence customer demand for services and the provision of capacity to meet these demands. At a strategic level this can involve analysis of patterns of business activity and user profiles. At a tactical level it can involve use of differential charging to encourage customers to use IT services at less busy times. 2.4.2.2.2 Service Design Service Design is a stage within the overall service lifecycle and an important element within the business change process. The role of Service Design within the business change process can be defined as [43, 55]: “The design of appropriate and innovative IT services, including their architectures, processes, policies and documentation, to meet current and future agreed business requirements.” 68 Service Catalogue Management Supplier Management Service Level Management Capacity Management Availability Management IT Service Continuity Management Information Security Management Figure 2.18 Service Design The main goals and objectives of Service Design are to [43, 50]: • Design services to meet agreed business outcomes • Design processes to support the service lifecycle • Identify and manage risks 69 • Design secure and resilient IT infrastructures, environments, applications and data/information resources and capability • Design measurement methods and metrics • Produce and maintain plans, processes, policies, standards, architectures, frameworks and documents to support the design of quality IT solutions • Develop skills and capability within IT • Contribute to the overall improvement in IT service quality. There are some processes and activities associated with Service Design [50]: I. Service Catalogue Management (SCM): provides a central source of information on the IT services delivered to the business by the service provider organization, ensuring that business areas can view an accurate, consistent picture of the IT services available, their details and status. The purpose of Service Catalogue Management (SCM) is to provide a single, consistent source of information on all of the agreed services, and ensure that it is widely available to those who are approved to access it. II. Service Level Management (SLM): negotiates, agrees and documents appropriate IT service targets with the business, and then monitors and produces reports on delivery against the agreed level of service. The purpose of the SLM process is to ensure that all operational services and their performance are measured in a consistent, professional manner throughout the IT organization, and that the services and the reports produced meet the needs of the business and customers. 70 III. Capacity Management: includes business, service and component capacity management across the service lifecycle. A key success factor in managing capacity is ensuring that it is considered during the design stage. The purpose of Capacity Management is to provide a point of focus and management for all capacity and performance-related issues, relating to both services and resources, and to match the capacity of IT to the agreed business demands. IV. Availability Management: The purpose of Availability Management is to provide a point of focus and management for all availability-related issues, relating to services, components and resources, ensuring that availability targets in all areas are measured and achieved, and that they match or exceed the current and future agreed needs of the business in a cost-effective manner. V. IT Service Continuity Management (ITSCM): The purpose of ITSCM is to maintain the appropriate on-going recovery capability within IT services to match the agreed needs, requirements and timescales of the business. ITSCM includes a series of activities throughout the lifecycle to ensure that, once service continuity and recovery plans have been developed, they are kept aligned with Business Continuity Plans and business priorities. VI. Information Security Management (ISM): ISM needs to be considered within the overall corporate governance framework. Corporate governance is the set of responsibilities and practices exercised by the board and executive management with the goal of providing strategic direction, ensuring that the objectives are achieved, ascertaining that the risks are being managed appropriately, and verifying that the enterprise’s resources are used effectively. The purpose of the ISM process is to align IT security with business security and ensure that information security is effectively managed in all service and Service Management activities 71 VII. Supplier Management: this process ensures that suppliers and the services they provide are managed to support IT service targets and business expectations. The purpose of the Supplier Management process is to obtain value for money from suppliers and to ensure that suppliers perform to the targets contained within their contracts and agreements, while conforming to all of the terms and conditions. 2.4.2.2.3 Service Transition The role of Service Transition is to deliver services that are required by the business into operational use. Service Transition delivers this by receiving the Service Design Package from the Service Design stage and delivering into the Operational stage every necessary element required for ongoing operation and support of that service. If business circumstances, assumptions or requirements have changed since design, then modifications may well be required during the Service Transition stage in order to deliver the required service. Service Transition focuses on implementing all aspects of the service, not just the application and how it is used in ‘normal’ circumstances. It needs to ensure that the service can operate in foreseeable extreme or abnormal circumstances, and that support for failure or errors is available. As you can see in the figure 2.11, there are seven processes and activities in the service transition. 72 Figure 2.19 Service Transition I. Transition Planning and Support: The goals of Transition Planning and Support are to: 73 • plan and coordinate resources to ensure that the requirements of Service Strategy encoded in Service Design are effectively realized in Service Operations • Identify, manage and control the risks of failure and disruption across transition activities. II. Change Management: ensures that changes are recorded, evaluated, authorized, prioritized, planned, tested, implemented, documented and reviewed in a controlled manner. The purpose of the Change Management process is to ensure that standardized methods are used for the efficient and prompt handling of all changes. III. Service Validation and Testing: The key purpose of service validation and testing is to provide objective evidence that the new/changed service supports the business requirements, including the agreed SLAs. IV. Release and Deployment Management: The goal of the Release and Deployment Management process is to assemble and position all aspects of services into production and establish effective use of new or changed services. It covers the whole assembly and implementation of new/changed services for operational use, from release planning through to early life support. V. Application Development and Customization: This process focuses on the performance of a new or changed service. The purpose of this process is to provide standard means of determining whether the actual performance of a new or changed service compares favorably to predicted performance, and whether it operates acceptably by providing value to the customer. 74 VI. Service asset and configuration management: The configuration management part of this process provides a logical model of the IT infrastructure, consisting of configuration items, their attributes, and their relationships. This process manages the service assets in order to support the other service management processes. VII. Knowledge Management: The purpose of Knowledge Management is to ensure that the right person has the right knowledge, at the right time to deliver and support the services required by the business. 2.4.2.2.4 Service Operation The purpose of Service Operation is to deliver agreed levels of service to users and customers, and to manage the applications, technology and infrastructure that support delivery of the services. It is only during this stage of the lifecycle that services actually deliver value to the business, and it is the responsibility of Service Operation staff to ensure that this value is delivered. 75 Figure 2.20 Service Operation Service Operation has some processes as follow: I. Request Fulfillment Process: The purpose of Request Fulfillment is to enable users to request and receive standard services; to source and deliver these services; to provide information to users and customers about services and procedures for obtaining them; and to assist with general information, complaints and comments. 76 II. Access management: The purpose of the this process is to provide the rights for users to be able to access a service or group of services, while preventing access to non-authorized users. The process includes verifying identity and entitlement, granting access to services, logging and tracking access, and removing or modifying rights when status or roles change. III. Event Management: According to definition of event, “An event is a change of state that has significance for the management of a configuration item or IT service”, Event Management is the process that monitors all events that occur through the IT Infrastructure to allow for normal operation and also to detect and escalate exception conditions. IV. Incident Management: According to definition of incident, “An incident is an unplanned interruption to an IT service, or a reduction in the quality of an IT service. Failure of a configuration item that has not yet impacted service is also an incident”, Incident management concentrates on restoring the service to users as quickly as possible, in order to minimize business impact. After the incident has been investigated and diagnosed, and the resolution has been tested, the Service Desk should ensure that the user is satisfied before the incident is closed. V. Problem Management: The key objectives of Problem Management are to prevent problems and resulting incidents from happening, to eliminate recurring incidents and to minimize the impact of incidents that cannot be prevented. VI. IT Operations Management: is the function responsible for the daily operational activities needed to manage the IT Infrastructure. This is done according to the Performance Standards defined during Service Design. 77 VII. IT Facilities Management: is responsible for managing the physical environment where the IT infrastructure is located. Facilities Management includes all aspects of managing the physical environment, for example power and cooling, building access management, and environmental monitoring. 2.4.2.2.5 Continual Service Improvement Continual Service Improvement (CSI) is concerned with maintaining value for customers through the continual evaluation and improvement of the quality of services and the overall maturity of the ITSM service lifecycle and underlying processes. The primary purpose of CSI is to continually align and re-align IT services to the changing business needs by identifying and implementing improvements to IT services that support business processes. These improvement activities support the lifecycle approach through Service Strategy, Service Design, service Transition and Service Operation. In effect, CSI is about looking for ways to improve process effectiveness, efficiency as well as cost effectiveness. 78 Figure 2.21 Continual Service Improvements Following processes are associated with Continual Service Improvement: I. Service Evaluation: The objective of Service Evaluation is to evaluate service quality on a regular basis. This includes identifying areas where the targeted service levels are not reached and holding regular talks with business to make sure that the agreed service levels are still in line with business needs. II. Process Evaluation: This process objective is To evaluate processes on a regular basis. This includes identifying areas where the targeted process metrics are not reached, and holding regular benchmarking, audits, maturity assessments and reviews. 79 III. Definition of Improvement Initiatives: The main goal of this process is definition specific initiatives aimed at improving services and processes, based on the results of service and process evaluation. The resulting initiatives are either internal initiatives pursued by the service provider on his own behalf, or initiatives which require the customer’s cooperation. IV. Continual Service Improvement Monitoring: verifies if improvement initiatives are proceeding according to plan, and to introduce corrective measures where necessary. Table 2.2 ITIL V3 processes and sub processes 80 81 82 2.5 Chapter Summary This chapter discussed outsourcing, IT Governance and its different frameworks. In more detail ITIL Framework, its versions and processes, the best practices are described. This literature review is expected to be the elements on doing the next phases of the study. CHAPTER 3 METHODOLOGY 3.1 Introduction Methodology is a organized, documented set of procedures, rules, principles and guidelines that describes how something will be done. It includes the frameworks, techniques, methods, patterns and procedures used to accomplish a set of goals and objectives. This chapter provides a clear guideline on how the project goals and objectives shall be achieved. Three main phases should be completed regarding to accomplish the goals of this research. Each of these phases will be discussed by details in this chapter. 84 3.2 Project Methodology Project methodology is the guidelines to ensure that project is conducted in a disciplined and well-managed manner. By the implementation of mythologies, programs, documents and data can be achieved as a result of activities and tasks that are included in the methodology. In order to get some information about the outsourcing problems and challenges, some analyses were carried out. The required methodology for this study started from initial planning, an analysis of the general outsourcing problems, study about ITIL Framework and its component, and at the final phase we are going to develop a proposed framework for managing software development outsourcing project. Figure 3.1 shows the project methodology framework. 85 Phase 1: Initial Planning • Project objectives • Project scopes • Project methodology Phase 2: Analysis Literature Review Identifying CICT problems • Definitions • Identify outsourcing and challenges • Analysis the ITIL framework and its component • Interview • questionnaire Phase 3: Develop a Proposed Framework • • • • Identify components of framework Framework development Framework implementation Framework acceptance Figure 3.1 Project Methodology Framework 86 3.2.1 Phase 1: Initial Planning Phase The project starts with the first phase that is Initial Planning. The main purpose of this phase is to define the goals, scope and methodology of the project. First of all, the title of the project is discussed with the supervisor. The objective of the study is analyzed and identified according to the problem statement. Project scope is identified to draw the boundary of this study. Finally, some researches on the background of the study are done in order to decide on the methodology of the study. 3.2.2 Phase 2: Analysis Data analysis is the process of looking at and summarizing data with the intent to extract useful information and develop conclusions. In this phase, few activities are carried out such as literature review, identify problems of outsourcing projects and as a case study software development outsourcing projects of CICT are studied. At this phase, the aim is to gain an in-depth understanding of outsourcing and ITIL framework. 3.2.2.1 Literature Review The literature review is an essential stage in conducting a research project. Reading and appraising what other people have written about the subject area are 87 also very important. According to Naoum (1998), it can be both descriptive and analytical. It is descriptive in that it describes the work of previous writers and it is analytical in that it critically analyzes the contribution of others with the view of identifying similarities and contradictions made by previous writers. A review of the literature has the following purposes: • To justify choice of research question, theoretical or conceptual framework, and method; • To establish the importance of the topic; • To provide background information needed to understand the study; • To show familiarity with significant and/or up-to-date research relevant to the topic; • To establish study as one link in a chain of research that is developing knowledge in related field. In this stage, essential things such as the definitions, types of outsourcing, way of outsourcing, its benefits and disadvantages, also ITIL, its evolution and benefits and other related studies were identified and analyzed. 3.2.2.2 Identifying CICT problems The purpose of this part is to identify CICT’s problems with outsourcing projects, so data collection is very important. Establishing a data collection process should be seen as a fundamental step at the start of any improvement activity. 88 A data collection process ensures that a project can efficiently and accurately collate data enabling to measure and establish a baseline of current performance whilst quantifying later improvements. Without accurate and timely information, improvement projects can flounder, change agents may guess at fixes and resultant solutions be inappropriate. Research methods for data collection can be classified in various ways. However, one of the most common distinctions is between qualitative and quantitative research methods. Quantitative data collection methods are used to study natural phenomena. They rely on random sampling and structured data collection instruments that fit diverse experiences into predetermined response categories. They produce results that are easy to summarize, compare, and generalize. Examples of quantitative methods include survey methods, laboratory experiments, formal methods such as econometrics, and numerical methods for instance mathematical modeling. Qualitative data collection methods are used to study social and cultural phenomena. They play an important role in impact evaluation by providing information useful to understand the processes behind observed results and assess changes in people’s perceptions of their well-being There are different ways for collecting data such as questionnaire and interview. Qualitative data sources include observation and participant observation (fieldwork), interviews and questionnaires, documents and texts, and the researcher’s impressions and reactions. 89 In this project, for collecting data about the CICT, we use qualitative data collection, interview and questionnaire. The interview questions are attached in Appendix A and the questionnaire is attached in Appendix B. 3.2.3 Phase 3: Develop a Proposed Framework In this phase, researcher after analyzing of collected data about CICT and general information should propose proper framework or list of suggestions for the CICT based on the best practices. After developing the framework, it should implement in CICT and if it has some problem, it should be solved after getting comment from the CICT manager. 3.3 Chapter Summary This chapter discussed various aspects of the study related to the research design, including the method, data collection processes and data analysis techniques. CHAPTER 4 INITIAL FINDINGS 4.1 Introduction This chapter covers the analysis of current situation of the case study. The case study for this project is Center of Information Communication Technology (CICT). Findings from this analysis provide the researcher with a solid ground in implementing the framework 91 4.2 Organizational Analysis Before proceeding with any analysis, it is very important to understand about the case study which is CICT, UTM. CICT or the Center of Information and Communication Technology was established in 1975 by the name of Computer Center or ‘Pusat Komputer’. The aim was to assist the University's administrative computing as well as to provide consultancy in government agencies computerization such as the Teachers' Training Division, the Malaysian Examinations Council and the Public Services Department. In 1981, the Department of Computer Science was established to offer Computer Science courses. The Computer Center then merged with this department in order to combine all ICT expertise in UTM. In 1991, a decision has been made to launch the Faculty of Computer Science and Information Technology and reestablish the Computer Center so that both entities can fully concentrate on their own functions. On 19 January 2004, the Computer Center was upgraded to CICT or the Center of Information and Communication Technology. Now, CICT is responsible for ensuring that staffs and students have access to teaching, learning and research resources by providing the University's IT infrastructure, acquiring, developing and supporting new and emerging technologies and systems, and providing access to millions of digital resources across the University's campuses. 92 CICT is continually developing and delivering the new initiatives by extending access to the University's network, CICT services and support digital resources, and by developing and supporting the delivery of e-learning. 4.2.1 CICT Mission, Vision and Objectives The vision of CICT is “to become the source of quality and innovative ICT services towards achieving the University's aspirations”. The missions of CICT are “We are committed to fulfill the University's ICT requirements through activities in administrative and academic computing, providing ICT infrastructure, training, ICT research and consultation based on quality”. CICT aims: • To become a leader in excellence and innovative information technology services • To provide centralized and integrated ICT service • To be the reference center for ICT • To explore new technology in ICT services and implementation. The objectives of CICT are: • To increase the adoption of information technology in all University activities 93 • To provide guaranteed ICT infrastructure and facilities • To become the reference center in ICT service and deployment in the University • To become the center of software / application development in the University • To explore new technologies in ICT services and implementation • To increase the ICT competencies of the University community 4.2.2 CICT Organizational Structure The functions of CICT are divided in six divisions. The divisions are academic computing, service and infrastructure, administrative computing, corporate planning, and training and consultancy. Figure 4.1 illustrates the organizational structure of CICT. 94 Figure 4.1 CICT Organizational Chart 4.3 Questionnaire and Interview Analysis The goal of interview is to understand the CICT challenges and problem with the software development outsourcing projects. The interview was held with Mr. Helmee Yaacob -manager of the development team at CICT and IT officer for HR system-. The interview questions are attached to the project (Appendix A). 95 A questionnaire is a series of questions asked to individuals to obtain statistically useful information about a given topic. In this project, the questionnaire was given to the user of HRFIN project to find the other problems from the user’s viewpoint the questionnaire has been attached in appendix B. Through the interview and questionnaire CICT reasons for outsourcing a project, outsourcing problems, CICT Satisfaction of outsourcing providers, service quality and others can be determined. Also this interview can help us in gathering essential information to give suggestions to CICT for solving their problems. CICT uses IT for doing most of their works such as data collection, data analyzing, collaboration and so on. They use some software related to their work, and for the software development project they use NetBeans and Oracle. Being the only center of ICT in UTM cause to having a lot of programs, but they can’t do all of those projects inside. Sometimes they outsource their software development projects. The type of CICT software development outsourcing is Software Development Outsourcing and software Acquisition (Total outsourcing). It means all the software development stages such as design, development, programming, and testing is outsourced. CICT started outsourcing from 2005. Their reasons for using outsourcing are the lack of related technology and lack of adequate staffs. If their project is big, they don’t have enough staff to handling the project, or the staffs don’t have related knowledge, so they have to outsource their projects. 96 Their fist outsourcing project was Human Resource and Finance System. This project was very big and complex, and they hadn’t enough and adequate staffs, so outsourcing was the only way to get work done more efficiently and effectively This project took one and half year to completing. CICT has problems when conducting with outsourcing such as deliverable quality problems, misunderstanding and time problems, because developing mutual understanding between client and outsourcer takes more time. Also because of lack of a managed relationship and clear contract content, the outsourcer can’t understand what CICT exactly expects. Most of their problems for the software development projects are: • Misunderstandings of the contract content and services. The software development projects need to have more details about the project. User needs, requirements and other things should be identified with details. On the other hand mutual understanding of the project between CICT and Third-Party Company takes a lot of time. Sometimes some of the requirement can’t be understand by the vender. Sometime the contract content is not very clear, so misunderstanding it cause to misunderstanding. • Time consuming. For development project, the analysis and requirement definition stage takes more time, because if the requirement identify carefully, problems decrease. But Most of the time, first meeting is not enough for gathering all data. For developing HRFIN project, outsider came to CICT several times and collects their needed information, but after starting the project again they came here for more information. So it cause to taking more time. As you can see, the misunderstanding added more problems to project. 97 • Frequently changing of the requirement. When their projects take a long time, the requirements change during that time, so applying the changes has additional cost for them. For example HRFIN project took one and half year. That was long time. During that time something such as the university policies and staffs needs changed. So they have to add new functionality or change some part of the program according to their new requirement. Therefore it had additional cost and time. • Poor relationship management. They lose their direct management on the project; also they cannot manage and govern their relationship. HRFIN was their first outsourcing project and they hadn’t any experience on the outsourcing. They hadn’t any plan for conducting with outsource providers. So they didn’t have any control on the project. There are some benefits they get from outsourcing, including: • They Gain new technology in programming. Using HRFIN outsourcing brought new technology in java development using NetBeans with 12 layer • Using outsourcing the project, reduced issues for handling the staffs. • After completing the project, staffs can be terminate, because they are not permanent staffs, so the cost increase. After implementing the outsource project, if a problem occurs, they try to solve them internally but if they can’t, they inform the outsource company via sending email, calling or sometimes visiting. Then it takes four days to one week for solving their problems. It is very important for them, because if the software problem cause to stopping the work, it must be solve immediately. In this case one week is too much. 98 They try to use more meetings and dissections for solving their problems, but they couldn’t find an appropriate solution. These reasons cause CICT to not satisfy using outsourcing a lot. As you can see, table 4.1 shows the summary of analyzing. Table 4.1 summary of interview and questionnaire analyzing Topic Interviewee kinds of CICT outsourcing projects Reasons of outsourcing the project Type of CICT SDO CICT information • Mr. Helmee Yaacob, manager of the development team at CICT and IT officer for HR system • Software development project • Lack of adequate staffs • Lack of related technology and programming skills inside • Software Development Outsourcing and software Acquisition (Total outsourcing) • Gain new technology of netbean programming with 12 layers Benefits gain by outsourcing • Project outsourcing, reduced issues for handling the staffs during the project. • After completing the project, staffs can be terminate, because they are not permanent staffs, so the cost increase. 99 Problems of using outsourcing • Misunderstanding of the contract content and services • Time consuming • Frequently requirement changes that caused to additional cost • Outsourcing relationship management treating with • Most of the time internally problem After • Inform outsider via Email, fax, calling or visiting • For externally, 4 days to one week installation time taken to solve the problem CICT satisfaction of • Because of cited problem, CICT is not satisfying outsourcing outsourcing too much. 4.4 Suitable Component of ITIL for Managing the Outsourcing According to the outsourcing problem of CICT and the problems mentioned in Literature Review, there are some component of ITIL related to them. These components help to better managing the outsourcing projects. In the next project we’re going to explain how these components can solve the CICT outsourcing problems. Table 4.2 shows the ITIL processes related to outsourcing. 100 Table 4.2 ITIL V3 processes regarding outsourcing ITIL V3 Processes Specific benefits to General Benefits CICT book Service Strategy Financial Management • To the • defines determines required financial resources over the structures necessary for the the management of financial planning period, and to planning data of the allocate CICT those for optimum benefits. Service • To the • To defines provide thorough boundaries of the project assessment of service- Management in terms of the functions level and services that the insight that helps CICT service provider will give eliminate to company, the volume features of work that will be from contracts, and it accepted and delivered, ensures that they don't and acceptance criteria pay outside vendors for for responsiveness and service levels they don't the really need. Service Design Level quality of requirements unneeded and • To deliverables. options Mitigate misunderstanding Supplier management • To ensure that suppliers • To ensure that perform to the targets outsourcing contained their perform all conditions and and term of contract within contracts agreements, while conforming to all of the terms and conditions between vendor provider CICT and 101 Service Operation Problem management • To facilitate root-cause analysis to eliminate recurring incidents by • To help in finding the cause of incident , so it can identifying and resolving remove underlying problems. immediately The is result CICT problem fewer disruptions of project. Change management • The risk of disrupting critical systems through of undocumented especially and unplanned changes drops Service transition • To manage the changes dramatically. systems the project, when the requirement changes. Critical are available when people need them and IT support personnel spend less time chasing down and fixing outages that could've been Service Evaluation Improvement Continual Service avoided. • To assess project outage and to corrective instigate action if required. And to ensure the vendors processes is align with SLA • To ensure about quality of service delivered by vendors. 102 4.5 General Proposed Framework I proposed a general framework for managing the outsourcing project. On the next project the framework should be tested and maybe some changes will be necessary. Also we exactly identified which processes of ITIL are associated with which stages of software development outsourcing project. Initialing • Problem management Development • Service Level Management Closing • Service Evaluation • Financial management • Supplier management • Change management Figure 4.2 General Proposed Framework 103 4.6 Chapter Summary This chapter describes organizational structure of the CICT and its functions. CICT interview was analyzed. It helps to understand current situation in the organization and identify necessary processes that should be implemented. We found some of ITIL processes regarding CICT, and finally just proposed a general framework. CHAPTER 5 FRAMEWORK REFINEMENT 5.1 Introduction One of the main objectives of this project is to develop a framework for managing the outsourcing projects. This framework is arrived from the ITIL V3 framework. The OM Framework will provide guidelines for the outsourcing services to achieve good outsourcing relationship management by implementing it. Through the researcher analysis of outsourcing and ITIL V3, the framework was developed by integrating all the important and suitable components. The framework design will be discussed in details in this chapter. 105 5.2 Proposed framework design In developing the proposed framework, it is vital to incorporate methodologies and concepts to ensure a successful delivery service that achieves business goals. The development of the proposed framework for managing the outsourcing projects involves the related components of ITIL V3 framework. These components have been determined by the researcher during literature review and analysis phase as described in chapter 2 and 4. The components are discussed in the following sections. 5.2.1 ITIL Implementation Framework A phased approach needs to be taken to the ITIL implementation for CICT outsourcing projects. This recognizes the limitations of staffing resources that can be allocated to the project, and acknowledges that staff will still be required to complete their normal activities. According results of the questionnaire and interviews, the implementation phases of framework is divided into 4 phases (Figure 5.1). These phases should be implemented according to their importance for the CICT and also based on the simplicity to implementation. 106 Figure 5.1 Outsourcing Management Framework (OM Framework) 5.2.1.1 Phase 1 Service support processes, such as incident management and problem management, are among the first ITIL processes that organizations start to implement. Many IT organizations start the implementation of IT service management processes from incident management [68]. Incident Management is a sub process in ITIL that need to be implemented in every company for better IT operation. Incident Management is the process for dealing with all incidents; this can include failures, questions or queries reported by the users of HRFIN project or by technical staff. The primary goal of the Incident Management process is to restore normal service operation as quickly as possible [53]. 107 Incident Management is strongly linked to Problem Management, which is charged with determining the root cause of an incident. So after implementing Incident management process, when all possible incidents are stored, Problem management should be implemented. The next process in phase1 is problem management. Problem Management investigates the underlying cause of incidents, and aims to prevent incidents of a similar nature from recurring. By removing errors, which often requires a structural change to the IT infrastructure in the CICT, the number of incidents can be reduced over time [53]. Although Incident and Problem Management are separate processes, they are closely related and will typically use the same tools, and may use similar categorization, impact and priority coding systems. This will ensure effective communication when dealing with related incidents and problems [53]. Above mentioned processes is recommended first, because they are fairly easy processes and able to gain early benefits. It is usually better to start with something easier and something that will show immediate benefit with minimum effort. It will motivate implementation team to continue ITIL implementation project. 5.2.1.2 Phase 2 The first process in phase 2 that is important to implement is financial management. Financial management helps CICT to account for expenditure, identify 108 costs, improve the budgeting process, identify costs that were higher than expected, identify areas for possible cost reduction, identify the cause of costs, and implement the way of cost control. The Financial Management is responsible for enabling the CICT to account fully for the spend on outsourcing services and to attribute these costs to the services delivered to CICT, and to control and manage the overall IT outsourcing budget and enable the fair and equitable recovery of costs (by charging) for the provision of IT services. The financial management output is an input for the Service Level Management, so it should be implement before SLM. Implementing financial management can also help CICT to decide if the outsourcing is more cost effective than in sourcing or not. So it should be implemented before the other processes to find the better solution for the organization. After deciding about the outsourcing and find all the outsourcing cost it’s time to implement Service Level Management that is one of the most important processes of IT Service Management and is a vital process for every outsourcing project in that it is responsible for agreeing and documenting service level targets and responsibilities within SLAs, for every activity within IT [51]. SLA also receives input from the incident and problem management. Because the experience from the last projects can help them to define a better SLA that is very clear. And also they can find the problems that happened before in the projects and find their solutions and mention them in the new SLA. 109 The objective of the Service Level Management process is to manage and maintain the quality of IT services delivered to the CICT. The process also seeks to improve on the quality of service delivered to the CICT outsourcing projects. The purpose of the SLM process is to ensure that all operational services and their performance are measured in a consistent, professional manner throughout the IT organization, and that the services and the reports produced meet the needs of the business and customers. 5.2.1.3 Phase 3 There are three other processes, supplier management, change management and security management that should be implemented in the phase 3. The first important process to manage the outsourcing projects is the managing supplier. After implementing a good Service Level Agreement, it’s very important that the supplier should be monitored. It’s for ensuring that the supplier performs all the SLA statements and agreements. The goal of the Supplier Management process is to manage suppliers and the services they supply, to provide seamless quality of IT service to the business and to ensure that suppliers perform to the targets contained within their contracts and agreements, while conforming to all of the terms and conditions. [51]. 110 It is essential that Supplier Management processes and planning are involved in all stages of the project. Next important process to implement is change management. Gartner reports that 80% of project failures are caused by changes. So, if all changes are under control as soon as possible, a lot of these failures will be prevented. That is definitely a quick win and quick wins is what ITIL implementation project manager wants to keep the motivation of support teams up and keep upper management committed to the project. It may be a while to realize the benefits of Service Level Management. Any changes can happen for the software development project, so CICT needs to have a good plan for every changes to reduce the additional time and cost. So Change Management has an important role in these kinds of projects, especially for CICT that they don’t have any special plan when the changes occur. Information security management is the last processes of this phase. Information security is a management activity within the corporate governance framework, which provides the strategic direction for security activities and ensures objectives are achieved. When a company outsources their activities, the security finds an important role. So this process should be implemented to ensuring that security of the information are implemented, as the purpose of information security is to ensure that information security is effectively managed in all services and to provide a focus for all aspects of IT security and manage all IT security activities. 111 5.2.1.4 Phase 4 After implementing all the necessary process in the previous phases, in this phase, service evaluation should be implemented. When the whole processes were implemented, service evaluation is needed to understand whether the performance and value of a service is acceptable and to evaluate service quality on a regular basis. Service Evaluation is a final process that helps CICT to recognize that the outsourcer has delivered the predefined services with all accepted features. 5.2.2 Framework Implementation Roadmap for Software Development Projects After proposing the framework, the road map can help to follow each process inside the each phase. Figure 5.2 shows that each process should be applied in each phases. 112 processes Phase1: Phase2: Phase3: Phase4: Phase5: Phase6: Planning Requirement Design Development Testing Installation Definition Incident Management Problem Management Financial Management Service Level Management Supplier Management Change Management Information Security Management Service Evaluation Figure5.2 Framework implementation roadmap for software development outsourcing Incident management is a process that should be applied in the whole phases of the project from planning to installation, because the incidents may happen in every phases of the project, and all of them should be recorded. Problem management is a process to find the cause of an incident, so it should be applied after incident management and also it should be carried on the whole software development life cycle. 113 After these two processes, financial management should be applied from the planning phase, because it helps CICT to realize if outsourcing is a cost effective option for CICT or not. During the project, any changes may happen and for each change, the related cost should be identified. Therefore financial management should be continued on the other phases. The next important process is Service Level Management. A Service Level Agreement should be prepared in the requirement definition phase and two parties should agree to its statements. After agreeing on SLA, the supplier management process should be started. It is an ongoing process from design phase to installation to monitoring the outsourcers. It checks supplier to ensure that they are doing each phases according to the agreements. During the software development project any changes can happen. So a change management is required to managing them in a good manner with low cost and time. And also change management should be kept until the installation phase. After managing the changes, the important process that should be implemented is Information Security Management. This process helps CICT to ensure that the information is used by the authorized people. So it started from design phase to testing phase. The final process is service evaluation that should be applied in the last two phases, testing and installation phases. 114 Now, all identified processes are described in more detail and the suggestion and activities for implementing them are explained: 5.2.2.1 Incident Management Process The ITIL definition of an incident is “an incident is any event which is not part of the standard operation of a service and which cause an interruption to, or a reduction in, the quality of that service.” This includes bugs, outages, and even user interface problems. Note that incident management does not include root cause analysis or correction. It is all about restoring service [53]. The incidents database is an important asset for software development projects. Learning from past experience in service management, allows shifting from a reactive approach to a more proactive one [69]. So the CICT related staffs should create a database for recording the incidents. Incident management process is consisted of following activities [71]: 115 • CICT should define Incident manager for managing the incident which occurs during software development outsourcing projects. • Incident manager should define required training of the staff for detecting the incident and how to resolve it if they can. • They should identify what documentation and forms will be used in incident management. • So they need to create Incident management forms. Suggested form is illustrated in figure 5.3. This form can complete the CICT forms in Appendix C. • They must ensure that the staffs know how to use the forms. • Documentation the process for incident management is necessary. • Ensuring that the technician can understand and follow the incident process is important. Output from the incident management process should be following: • Request for change • Incident resolution and closure • Updated incident record • Management information (reports) • Input to the Problem Management process 116 Incident Report Form Reporter Information Date of Report: Reporter Name: His / Her Job Title: Department: Signature: Incident Information Date of Incident: BPPO Very Critical HCM High Urgency Location of HCD Medium Incident Keselamatan Low If others, please specify: Attachments: YES Describe how incident occurred Fixed Further action required: Not fixed Resolution No action Follow up Incident/problem Solution Information The cause of incident/problem what action has been done to solving it Resolve Time and Date Resolver name: Her/ His job title: Signature: Tester Engineer Name: Date: Signature: Figure 5.3 suggested Incident/Problem Report Form NO 117 5.2.2.2 Problem Management Process ITIL defines a ‘problem’ as the cause of one or more incidents. Problem Management involves root-cause analysis to determine and resolve the cause of incidents, proactive activities to detect and prevent future problems/incidents and a Known Error sub-process to allow quicker diagnosis and resolution if further incidents do occur [53]. Recurring incidents can be identified as Problems that require correction. This is the job of the Problem management process. Problem management depends on the output of Incident process. Ideally Incident management produces consistent record classification and data for trending in support of problem identification. Once Incident management can reliably produce this level of output, the data can be trusted to support the implementation of Problem management [74]. • One of the first activities associated with the Problem management process that CICT should implement it is the “Major Incident Review” process, often referred to as a postmortem activity. The premise of this activity is to review high impact incidents to determine root cause and implement measures to avoid a reoccurrence. This activity will implement under the management of the incident restoration process and led by the incident manager. This can be considered as reactive Problem management. • The next activity is the realization that Problem management is a distinct process that requires its own process models, policies and resources and is supported by incident reporting. While at this point the process is 118 implemented at a level of maturity that has significant benefits, the majority of activity is still focused on reactive problem identification and elimination. • The third level of implementation will include the identification or proactive issues for the explicit purpose of incident avoidance of the CICT outsourcing projects. Known Error record will open for the purpose of impact analysis and assessment before the incident occurs [74]. Problem management implementation process is also consisted of following activities [73]: • CICT should assign the role of problem manager to their analyzer or developer. • Then train the other staffs to detect the problem. • Problem manager and incident manager should design the documentation forms. • After designing, they should create the forms (suggested form is illustrated in figure 5.3). • The process of problem management should be documented inside the forms. 5.2.2.3 Financial Management Process Financial Management is the sound stewardship of the monetary resources of the organization. It supports the organization in planning and executing its business objectives and requires consistent application throughout the organization to achieve maximum efficiency and minimum conflict. It is an iterative cycle of budgeting and accounting [76]. 119 The purpose of Financial Management is to ensure that the cost of outsourcing services is justifiable and it also helps to identify particularly costly areas that CICT may want to examine to see if doing the project in sourcing might reduce costs or outsourcing is better. Financial Management links closely to Service Level Management. There may be a difference between desirable and affordable service levels and it is the Service Level Management process that enables a balance to be struck between what the outsourcer would like and what is possible with the funds available. Financial Management is an input to the Service Level Management process as it provides budget and cost information to work with when negotiating service level agreements [75]. In order for the budgets to be realistic and to serve as a reference for the CICT, it is necessary to first identify all the cost items. Estimating the cost associated with these items is not always a simple task and external factors that are not under the direct control of the CICT often have an influence, such as an increase in the cost of software licenses, etc. It is essential that budgets take these uncertainties into account and care is taken to avoid their rendered obsolete by the slightest change in the requirements. The Financial Management process is typically implemented along the following activities: 120 • CICT financial manager should provide a list of all outsourcing expenditures to decide if outsourcing is more cost effective than doing in source. • They should ensure that funds are available for planned events. • They should provide detailed financial information for proposed initiatives • They should Track current expenditures against the budget. • Financial manager should record all expenditure using spreadsheet software or something else. • For it to be of value, the expenditure record must be kept up to date. 5.2.2.4 Service level management Service levels and their associated agreements are great tools for enabling managers to measure and guide their outsourcing relationships. When developed and used correctly, service levels can help ensure successful outsourcing engagements. Developed and used incorrectly, however, they can lead to poor results, dissatisfied customers, competitive disadvantage and ultimately failure to achieve good results in a deal [70]. The main goal of Service Level Management is to define, negotiate and monitor the quality of the project services that are accepted by two parties. The results of interaction/negotiation should be incorporated in the Service Level Requirements document (SLR) [77]. So they should have a SLR that is about the CICT Requirement for an aspect of an IT Service. This document should reflect the CICT needs and expectations regarding: 121 • The functionality and characteristics of the service. • The availability of the service. • The continuity of the service. • Service implementation time and procedures. The next step in implementation must be the preparation and acceptance of the agreements necessary for the services. A detailed description of the service must be included in the SLAs. They should talk about everything from the more general aspects to the most specific details of the service [77]. The suggested SLA for CICT is included the following important parts (see Appendix D): • Service description: describes the services and scope of services • Roles and responsibilities definition: specify the responsibilities of the both parties, CICT and the outsourcer. • Requesting service: describes how CICT can contact to outsourcer. • Service Maintenance: describes the maintenance related work. • Pricing: identify how they calculate the cost and calculate the amount of cost. • Reporting and reviewing: determines the periodic review and service level reporting. The Service Level Management process is typically implemented along the following activities: 122 • CICT should prepare SLR first to know about their needed functionality of the software development projects. • Also they need to have a SLA template, to have a managed and monitored relationship with the outsourcers. • Two parties should define the responsibilities and the functions and services in detail and with very clear statements. • The SLA should be reviewed and monitor frequently by the project manager. • Frequently report of the project progress should be prepared by outsourcer. 5.2.2.5 Change management The main aim of Change Management is to evaluate and plan the change process to ensure that, if a change is made, it is done in the most efficient way possible [77]. Before implementing Change management process in CICT, a Change manager should be defined, the one person who is most responsible and accountable for change management. The change manager is more of a role, depending on the size, complexity and structure of the organization, there may be more than one person playing the role of change manager for assisting with several activities. The change manager plays a leading role in many of the major activities of change management as follows [78]: • Receive and filter requests for change (RFCs). There must be a single point of collection for RFCs. The change manager will review new RFCs and filter out those that are impractical or duplicates of existing requests. The change 123 manager will serve as the gatekeeper to the activities of the change management process. • Coordinate the activities of the change advisory board (CAB). The change manager will serve as leader and facilitator for the change advisory board and its emergency committee. The change manager will convene the CAB. The change manager and the CAB will make recommendations for implementation, further analysis, deferment or cancellation of an RFC. • Issue and maintain the forward schedule of changes (FSC). The change manager is the keeper of the FSC. When the change advisory board approves changes, the change manager will add the change to the FSC and will give it to outsourcer to implementation. • Close RFC. The authority to declare a change complete and closed should be limited to the change manager. A change should be removed from open status only when it has been verified that the change has been successfully implemented and accepted by the CICT. Change management implementation includes some cost such as expenditure and people. In expenditure terms, the cost is about the any purchases of software designed to aid the creation and processing of request for change. But CICT can reduce this cost by using the suggested templates. In people terms, CICT should assign the roles and responsibilities to existing members of staffs, such as analyzer or developer. So the activities for change management are: • CICT should allocate on person as a change manager, he/ she can be the outsourcing project manager. • Also CICT need to Change Advisory Board that is a group consist of analyzer and developer to help the change manager in assessment of changes. 124 • After assigning the roles and responsibilities, it is important to ensure that those participating in the implementation and subsequent operation of the process understand what is required of them. That means required training should be defined • CICT should use some forms to creating request for changes. • The request for change should be reviewed by CAB and accepted by change manager. • Also the change and its budget for its implementation should be considered. The outputs from the change management process are [77]: • Forward schedule of changes (FSC) – A forward schedule of changes is a listing of upcoming changes which are be scheduled and communicated to other IT service management processes and to the rest of the CICT. The forward schedule of changes shows the changes that have been approved and given a date for implementation. • Updated Requests For Changes • Change advisory board decisions - The discussions of the change advisory board provide the basis for the change manager's decisions to approve or reject proposed changes. The members of the CAB help to determine if changes make sense from technical, financial, and business viewpoints. • Change management reports - Change management reports allow managers to evaluate the effectiveness of the process in the past and its direction in the future. 125 5.2.2.6 Supplier management The purpose of Supplier Management is to plan, manage and review suppliers of outsourcing services and to monitor the agreed service levels. Organizations that establish a formal supplier management program can work more effectively with outsourcers to achieve better business, service and cost outcomes, according to Gartner. Even the best developed and structured contract and service-level agreement (SLA) aren't enough to effectively manage vendor relationships. So If CICT implements supplier management can better manage information flow, and have more comprehensive and relevant information about the outsourcer, which places them in a stronger position during negotiations. "Vendor Management: 2009 Research Agenda Survey" indicates that commercial and government organizations are showing a growing interest in SM to improve spending controls, visibility, governance and regulatory compliance. Outsourcer relationship management is about ensuring that the outsourcer's goals and CICT's goals remain aligned, and that the outsourcer delivers the services the CICT expects. Before doing any activities, CICT needs a supplier manager. His/ Her roles is to ensure that the CICT goals are met, outsourcer services are scoped, documented and aligned with SLAs, documents roles and responsibilities between lead and subcontracted suppliers, assesses the impact of changes, attends CAB meeting, performs contract or SLA reviews at the determined time. 126 There are some activities and suggestions to helping CICT to better supplier management: • First CICT should choose outsourcers with standardized processes. • Then categorize outsourcers and choose the best one. • CICT should define roles and responsibilities of the staffs. • Regular meetings and scorecards can help CICT to increase supplier performance. • Defined service-level agreement measurements and metric reporting (for example, response time) • Outsourcer summary reports that distill information from performance surveys are provided quarterly to the CICT senior management team for review. • Outsourcer should prepare regular reports on results of the each phase of project • Monthly/bi-weekly review can help CICT to focus on reviewing service levels and identifying areas that require management attention. The agenda for these meetings can include milestone review, quality review, performance and assessment. • Also they can have weekly meeting between both project managers and developers for successful service delivery. These meetings will ensure identification of issues early so that they can be addressed. The agenda for these meetings can include project review, issue resolution, and team discussion. The day-to-day interactions must be focused on resolving any issues as they arise. The CICT teams should understand when issues should be escalated, and the outsourcer team should make a commitment to take ownership of issues related to application services. 127 5.2.2.7 Information Security Management The purpose of information security management is to ensure that the information is correct and complete, that it is always available for the development purposes and that it is only used by the outsourcer people who are authorized to do so [77]. About 60% of companies fail to do security risk mitigation when outsourcing software development, according to Gartner. Perfect security is impossible, but CICT should aim to provide a level of security appropriate to their objectives and operation needs. However, security is one of the most essential factors for successful outsourcing. Security issues may result in terrific expenses on re-establishing damaged reputation, leaving aside correcting mistakes or even re-doing all the work. To ensure that outsourcing arrangements meet the needed standard of security, an outsourcing security expert, highlighted lately four necessary stages, including knowing requirements, specifying expectations of the outsourcer, ensuring that the outsourcer can meet those requirements, and staying up-to-date. Successful security management is a must for successful outsourcing. Companies applying for software development outsourcing should ensure that their security management requirements are well defined and indicated in the agreements and contracts that control outsourcing relationships. Security Management is a continuous process and the Security Plan and security-related sections of the SLAs should be kept up-to-date 128 CICT should develop security policy and define: • The relationship with the general CICT policy. • Coordination with other IT processes. • The protocols for access to information. • The risk assessment procedures. • Training programmes. • The level of monitoring of security. • What reports need to be issued periodically. • The scope of the Security Plan. • The structure and people responsible for the Security Management process. • The processes and procedures employed. There are some ways to control the security, such as: • CICT should define a security policy that is align with the CICT goals. • CICT should ensure the outsourcer clearly understands and implements the security strategy they demand, including data protection and intellectual property protection within the outsourced service. • The security requirements are based on such factors as the nature of the CICT business, regulatory considerations, sensitivity of the data, and the consequences of loss or misuse. • Thoroughly examine the level and the approach to IT security the outsourcing provider employs: access control, monitoring the integrity of outsourced operations, etc. And have all CICT security needs reflected in the contract. • There should be ongoing IT security management in the CICT, as new security threats and challenges evolve. Making security a regular item at 129 the management meetings with the outsourcing provider is a best practice to provide for security issues. • It is also important that Security Management is up-to-date regarding new risks and vulnerabilities caused by viruses, spyware, denial of service attacks, and that the necessary hardware and software upgrades are made. 5.2.2.8 Service Evaluation The process of service evaluation is to consider whether the performance and value of a service is acceptable and to evaluate service quality on a regular basis. This includes identifying areas where the targeted service levels are not reached and holding regular talks with outsourcer to make sure that the agreed service levels are still in line with CICT needs. Service evaluation goal is to assess project outage and to instigate corrective action if required. And to ensure the outsourcer processes is align with SLA. There are activities as follow to evaluate the final services: • CICT tester of the project should test the program to ensure that all the objectives are achieved. • CICT should define some measurements that help them to measure the quality of final services, such as user satisfaction. Customer satisfaction on IT outsourcing service is significant in the direction to outsourcing performance. 130 • CICT should ask staffs and users about reporting every dissatisfaction of the project • Have a regular meeting during the outsourcing project. Have a good Service level management and supplier management can help to ensure that the services are aligned with the CICT goals and requirements. Table 5.1 shows the benefits of each processes of framework for CICT. It means that according to the CICT problems, these processes have some benefits for CICT that help them to mitigate or remove the problems. Table 5.1 benefits of the framework processes for CICT CICT Problems Framewor k Related Benefits for CICT Processes • Downtime problem Incident Management • Ensures that all the incidents are addressed in the CICT. • Finds a solution for each happened incidents. • Recurring same problem. Problem Management • Reduces the downtime of the project. • Downtime • Finds a permanent solution for the problems. problem • Cost problem • Eliminate of recurring of the same problems. Financial Management • Makes sure that outsourcing is the best options for CIC according to their budget. • Ensures that funds are available for planned modules. • Helps to track current expenditures against the budget. 131 • Misunderstanding of Service contract Level the Management statement. • Misunderstanding of • Understand the CICT requirements through an open process by creating Service Level Requirement (SLR). • The CICT expectations are managed and met by the outsourcers. • Eliminates misunderstandings. requirements. • Service levels can be measured against agreed targets. • Ensure that all services and conditions necessary for the CICT are mentioned in the agreement. • By declaring all condition and requirements in a clear statement, they can solve the time and cost problem (see 4.3 for more information about the CICT problems). • Not having effective plan an Supplier to Management manage their relationship with • Ensures that outsourcing provider perform all conditions and term of contracts. • The weekly and monthly reports can help CICT to control the project from far distance. outsourcer. • Helps CICT to manage the relationship between two parties by providing the meetings and reports. • How to manage Change when Management project the requirement changes. • Applying the necessary changes with the cost and requirement change. time control. • Reduce additional cost • Manages the changes of the project, especially when and when • By preparing a Request for Change (RFC), CICT time can filter, prioritize, and manage any changes and changes also the cost and expenditure of the changes is occur. determined. • It helps CICT to reduce the additional cost that is related to any changes. • Security when problem Information conducting Security with outsourcers Management • By defining the Information Security policy, they can monitor the security of their information. • Ensures that just authorized people access to the information. 132 • How to ensure about the service quality Service Evaluation • Ensures about quality of service delivered by outsource providers. • Defines measurements to evaluate the outsourcer functionality. 5.3 OM Framework Implementation Project Organizational Structure 5.3.1 Implementation team and groups For the purpose of implementing the OM framework in CICT several teams and groups should be identified. Members of this group should be selected from the employees of the CICT software project team and CIO. 5.3.1.1 Steering Group A steering committee is necessary to lead the team through the ITIL adoption. This role sets project direction, makes key decisions and provides final approval of Program deliverables. 133 The Implementation Project Manager should act as a steering group for this project, bringing in other parties as required to make sound decisions. He can be the CIO of CICT. Key activities for this role include: • Champions process solutions across the CICT • Conducts periodic meetings to monitor Program progress and issues • Provides final review and approval of program deliverables • Identifies and appoints key Program team members • Coordinates major program decisions that have been escalated to the Steering Group on a timely basis to meet program objectives. 5.3.1.2 ITIL Implementation Project Manager Project manager should be proposed among Heads of the CICT (for example CIO). Project manager should be familiar with process in project and has to know concept of the ITIL Framework. This role provides project management oversight and expertise to assist Core Teams in accomplishing their objectives. Key activities for this role include: • Co-ordinates activities with other project managers when necessary. • Provides status of work in progress and/or issues 134 • Develops project work plans, schedules and staffing requirements for projects assigned. • Conducts weekly change, issues and status meetings to track progress and risks with Core Teams assigned to. • Ensures that outstanding project management, process implementation and design requirements and/or issues are being addressed for projects assigned. • Schedules workshops and meetings as required. • Provides overall leadership and management for the projects assigned. 5.3.1.3 Implementation Teams Implementation teams should consist of staffs of the CICT who familiar with processes in working area. Implementation Teams for each specific process within the ITIL framework should incorporate selected members of the Service Management Project Team and key staff members of the software development team. Heads of Departments and employees of the CICT will need to be included as changes recommended will affect staff under their control. 5.3.2 Framework Applying Steps The researcher recommends 5 steps that CICT should undertake to demonstrate adherence to the Outsourcing Management Framework. The steps detailed are as depicted in figure 5.4. 135 1 2 3 4 5 Figure 5.4 Framework implementation Steps 136 5.4 Framework verification OM framework verification was conducted with the Mr. Helmee Yaacob, development team manager and outsourcing manager and also their team members. They commented on the framework and then acknowledged the framework comprehensiveness and clarified that it will be a good guidance for CICT to managing the outsourcing relationship and outsourcing projects (see Appendix E). And also they approved the incident report form and other forms and acknowledge that these are so useful for CICT. The Acceptance Test for OM Framework Questionnaire has been attached in appendix D. 5.5 Framework Finalization After developing the framework, it was shown to the CICT development team and they gave some comments and suggestion on the OM Framework. ITIL V3 doesn’t have any special process as a risk management, but Mr. Helmee Yaacob suggested adding this process to the framework. Because risk management is an important process in whole the software development outsourcing. So I considered it in my Framework. 137 Risk refers to future conditions or circumstances that exist outside of the control of the project team that will have an adverse impact on the project if they occur. A risk is a potential future problem that has not yet occurred. So it should be implemented in phase 2. Because before making an agreement, the organization should be considered any related risks and the suggested solution for them. Also it should be continued in all the phases to attention to all the risk during the projects. So I should add another part in section 5.2 as Risk Management: 5.5.1 Risk Management The main goal of risk management is to identify, assess and control risks. This includes analyzing the value of assets to the business, identifying threats to those assets, and evaluating how vulnerable each asset is to those threats. In organizations almost every decision has an upside and a downside involving some degree of risk. Effective risk management structure supports better decision-making through a good understanding of risks and their likely impact. Ensuring CICT makes cost effective use of risk management first involves creating an approach built up of well defined steps and then embedding them [79]. 138 CICT can achieve some benefit of risk management implementation. The key benefit is the achievement of CICT objectives. The others are better focus on business priorities, strengthening of the planning process and the means to help management identify opportunities, a cultural change that supports open discussion about risks and potentially damaging information; improved financial and operational management by ensuring that risks are adequately considered in the decision-making process; and increased accountability of management. Risk assessment and risk management are important contributors to the success of an IT outsourcing projects. There are some activities for managing the risk of project: • First CICT should identify all possible risks if they outsourced their software development project, and create a risk management plan. • They should analyze the risks to find the potential and important risk, and response to the important risk first. • The most important thing CICT can apply in the risk management is to create contingency plan for high risks. • They should control the risk during the project and look for the new risks. • Also, they should ensure that outsource company have a high degree of understanding of the project. • The project manager can be a risk manager as well. After applying all comments, my Framework is changed to the figure 5.5 and its road map finalized as the figure 5.6. 139 Figure 5.5 Finalized OM Framework for CICT Figure 5.6 Roadmap of Outsourcing Management Framework for software Development Projects 140 141 5.6 Chapter Summary This chapter identified process maturity level that is necessary for effective framework design of the ITIL implementation project. And based on the gathered information about current IT infrastructure of CICT outsourcing projects, implementation framework is developed. Also this chapter describes project organizational structure and expected deliverables of the CICT projects after deployment. CHAPTER 6 DISCUSSION AND CONCLUSION 6.1 Achievements Throughout the process of doing literature review and analysis of the case study, tremendous achievement, knowledge and experience were collected. A good understanding of current situation of CICT is obtained and referring to the objectives of the project, a research of ITIL framework have been carried out with a thorough case study. With all the information in hand, suitable processes of ITIL framework for Outsourcing project were identified. Based on these elements, the Framework was developed. Upon the completion of the framework, framework verification was conducted with CICT development team. Here are the achievements during the investigation and review: 143 • From the analysis, organizational structure of the CICT and its responsibilities were determined. • Form interviews and questionnaires, CICT outsourcing project problems and issues during outsourcing were identified. • According to literature review and CICT analyzes the suitable processes of ITIL Framework were identified and the Outsourcing Management Framework was developed, • Researcher gave some suggestion to implement and apply the ITIL processes in the CICT. 6.2 Constraints and Challenges One the project constraint is to gathering the information about HRFIN problems after outsourcing. Because it’s the first software development outsourcing project of CICT. Interview and questionnaire are used to find the HRFIN users problems. HRFIN project is implementing phase by phase, and some of its phases are not implemented yet, so the documentation about problems is not full. Another objective is to propose a framework that its elements raised from ITIL framework. This objective is achieved, but there are some problems in the way of development. Because I’ve used new version of ITIL that is V3 and the documents and papers about it are not so much. So it was difficult to answering this question” How to apply it to CICT? ”. 144 6.3 Recommendations The objectives of the project are to determine set of standard ITIL processes, operational management procedures and practices which will allow the CICT to manage a software development outsourcing projects. The pursuance of the research has determined some areas that can be enhanced for further studies, such as: • Measuring the level of Service Quality after OM Framework implementation • Comparison of Customer satisfaction level before and after OM Framework implementation in CICT. • Developing post implementation strategy for the CICT. • Information that is presented in the project can be use by organizations that have outsourced their IT service. • The ITIL implementation framework will be useful for other department of UTM. The researcher hopes that the OM Framework will be useful piece of information for CICT and other department that use outsourcing especially those in the higher education institute that wish to embark on ITIL implementation. This project has certainly brought great achievement for the researcher in understanding the corrections between human skills, management and IT. 145 6.4 Chapter Summary This chapter have three sections and stated in detail on the project achievement, constraint, challenges and future recommendations related to current project. From the outcome of the case study, findings were purpose of ITIL processes in Outsourcing Projects. The first section is discussed achievements that were obtained during research and analysis. The second section is described constraints and challenges that were faced by researcher during doing this project. Last section of this chapter has recommendations for future research based on the findings and conclusions of the study. 146 REFERENCES 1. John Ward and Joe Peppard, ‘Strategic Planning for Information Systems’, John Willey & Sons, third edition, Oct: 2007. 2. Subhankar Dhar and Bindu Balakrishnan, ‘Risks, Benefits, and Challenges in Global IT Outsourcing: Perspectives and Practices’, IEEE International Conference, 2006. 3. http://www.wisegeek.com/what-is-outsourcing.htm, [online] 4. http://www.mariosalexandrou.com/definition/outsourcing.asp, [online] 5. Federal Financial Institutions Examination Council, “Outsourcing Technology Services”, June: 2004. 6. Yu-An Huanga, Hsien-Jui Chungb and Chad Linc, “ R&D sourcing strategies: Determinants and consequences”,2008. 7. http://www.outsourceit2philippines.com/blog/?p=157, [online] 8. http://www.sourcingmag.com/content/what_is_bpo.asp, [online] 9. Tas, J. & Sunder, “Financial Services Business Process Outsourcing”, Communications of the ACM, 2004. 10. http://archwayconsultancy.com/, [online] 11. Forest Peterson, “Legal Offshoring: India's Pie”, [online] 12. Ian del Carmen, “Simple Steps to Rock-Solid Outsourcing Deals”, [online] 13. Ian del Carmen, “What You Need to Know About Outsourcing: Is Outsourcing Really For You?”. 14. Zhang Pei, Zeng Zhen-xiang, Huang Chun-ping, “A Framework for IT Outsourcing Decision Process”, 2005 147 15. Gunther Kruse and Christine Berry, “OUTSOURCING: The ‘how to’ Guide”, 2007 16. “MODERN TRENDS IN INFORMATION SYSTEM”. [online] 17. Ben Stevens, “Maintenance Outsourcing”, Aryana Group – IPAMC, 2006. 18. Outsourcing Factory Incorporated, “Steps to Select the Right Outsourcing Vendor”, 2008. 19. Gerry Kennedy, “The ACCESS Precept: Roadmap to Outsourcing Success”, 2007 20. Glenn Wheaton,”Request For Proposal (RFP)”, 2008. 21. Warren S. Reid, “Outsourcing: The 20 Steps to Success”, [online] 22. Priyesh Goyal and Rajat Chamria, “Business Process Outsourcing: An Introduction to BPO Industry”, sep: 2007. 23. Ernst & Young, European outsourcing survey, “Outsourcing: the rise of fragmentation”, 2008. 24. Dhar, S., Gangurde, R., & Sridar, R., “Global information technology outsourcing: From a risk management perspective”, 2004. 25. “Advantages of outsourcing”, http://jobs.lovetoknow.com/, [online] 26. JC Redmond, “Reasons for Outsourcing”, [online] 27. IT Governance Institute, “board briefing on IT Governance”, [online] 28. Ann All, “IT Governance: Taking It from the Top”, Feb:2008 29. Karen D. Schwartz ,”IT Governance Definition and Solutions”, may:2007 30. Peter Weill and Jeanne W. Ross, “IT governance”, 2007 31. Andrew Clifford, “What is IT governance?”, [online] 32. W.Van Grembergen, "Strategies for Information Technology Governance", Idea Group Publishing, 2004. 33. HP, "HP IT Service Management (ITSM), Transforming IT organizations into service providers", 2003. 34. Symons Craig, Mark Cecere, G. Oliver Young, and Natalie Lambert, “IT Governance Framework: Structures, Processes, And Communication”, White Paper, Forester Research, March: 2005. 35. Van Grembergen, W., “Introduction to the mini track IT governance and its mechanisms”, Proceedings of the 35th Hawaii International Conference on System Sciences, 2002. 148 36. Webb, P., Pollard, C., and Ridley, G. “Attempting to define IT Governance: Wisdom or Folly”, Proceedings of the 39th Hawaii International Conference on system Sciences, 2006. 37. Shamsul Sahibudin, Mohammad Sharifi Masarat, Ayat, “Combining ITIL, COBIT and ISO/IEC 27002 in Order to Design a Comprehensive IT Framework in Organizations”, 2008. 38. George Spafford, “The Benefits of Standard IT Governance Frameworks”, 2003. 39. Jim Long, “what is Six Sigma?”, [online] 40. David L. Cannon, Timothy S. Bergmann, Brady Pamplin “CISA - Certified Information Systems Auditor”, [online] 41. John Morency, “COBIT vs. ITIL”, 2005 42. Lou Hunnebeck, “ISO 9000 vs. ITIL vs. Six Sigma”, 2004. 43. Alison Cartlidge, Ashley Hanna, Colin Rudd, Ivor Macfarlane , John Windebank, Stuart Rance, “An Introductory Overview of ITIL® V3”, The UK Chapter of the itSMF. 2007. 44. Pink Elephant, ‘The ITIL® Story’ White Paper, September, 2004 45. Michael Brenner, “Classifying ITIL Processes , A Taxonomy under Tool Support Aspects”, 2006 46. Evelyn Hubbert, Simon Yates, Rachel A. Dines, ‘The Evolution From Process To Service Model’, October 2007 47. Tim Young , “Optimizing ITIL Service Delivery”, nov:2003 48. Hank Marquis, “ITIL® v3: What It Is and Why You Should Care”, 2008 49. IBM Corporation, “Introduction to the IT Infrastructure Library”, 2004 50. Office of Government Commerce (OGC), ITIL Core Books , Service Strategy, TSO, UK, 2007 51. Office of Government Commerce (OGC), ITIL Core Books , Service Design, TSO, UK, 2007 52. Office of Government Commerce (OGC), ITIL Core Books , Service Transition, TSO, UK, 2007 53. Office of Government Commerce (OGC), ITIL Core Books , Service operation, TSO, UK, 2007 54. Steven M. Bragg, “Outsourcing”, [online] 55. James Bucki, “Top 6 Outsourcing Disadvantages”, [online] 149 56. Outsourcing : Pros vs. Cons, http://www.squidoo.com/ProsandConsofOutsourcing, [online] 57. Axel Hochstein, Dr. Rüdiger Zarnekow, Prof. Dr. Walter Brenner, “ITIL as Common Practice Reference Model for IT Service Management: Formal Assessment and Implications for Practice”, 58. IT Governance Institute, “Governance of Outsourcing”, [online] 59. Sankar, C. et al. “Global Information Architectures: Alternatives and Tradeoffs”, International Journal of Information Management, 13, 2 (April, 1993), 84–93. 60. Weill, P. and Ross, J. IT governance, Boston, Massachusetts, Harvard Business School Press, 2004. 61. Weill P. and Vitale M. Place to space, “migrating to eBusienss models”, Harvard Business School Press. Boston, Massachusetts, 2002. 62. J.C., Henderson, “Plugging into Strategic Partnerships: The Critical IS Connection”, Sloan Management Review, Spring, 1990, pp. 7–18. 63. Fan Jing Meng, Xiao Yang He, Shun Xiang Yang, Peng Ji, “A Unified Framework for Outsourcing Governance”, IEEE International Conference on ECommerce, 2007 64. “The Software Development Life Cycle (SDLC) For Small To Medium Database Applications”, [online] 65. http://www.e-isn.com/software-outsourcing-types.htm, [online] 66. Pravesh Mehra, “A comprehensive talent strategy for services outsourcing” 67. HP, “ITIL Version 3 Frequently Asked Questions HP Services”, march: 2007 68. Marko Jäntti, “Lessons Learnt from the Improvement of Customer Support Processes: A Case Study on Incident Management”, c_Springer-Verlag Berlin Heidelberg 2009. 69. João Caldeira and Fernando Brito e Abreu, “Influential Factors on Incident Management: Lessons Learned from a Large Sample of Products in Operation”, 2008 70. William Maurer and Richard T. Matlus, “How to Develop and Apply SLAs in Outsourcing”, Gartner, 7 Feb. 2007 71. British Educational Communications and Technology Agency, “incident management”, 2004 72. Troy DuMoulin, “ITIL Implementation Roadmap (incident Management), 2007 150 73. British Educational Communications and Technology Agency, “problem management”, 2004 74. Troy DuMoulin, “ITIL Implementation Roadmap (Problem Management), 2007 75. British Educational Communications and Technology Agency, “financial management”, 2004 76. Troy DuMoulin, “ITIL Implementation Roadmap (financial Management), 2007 77. http://itil.osiatis.es/ITIL_course/it_service_management, [online] 78. http://www.anticlue.net/archives/000840.htm, [online] 79. OGC website, “Risk Management”, http://www.best-management- practice.com/Knowledge-Centre/Best-Practice-Guidance/Management-of-Risk/, [online] 151 Appendix A Interview questions 1. Do you give some of your IT projects to outside providers? 2. What kinds of your IT services are outsourced? If “Other”, please explain your answer. 3. Do these service (what you give to outsiders) cover all your job? 4. Why do you use outsourcing services? Please explain your answer. 5. What kinds of problems do you have when conducting with outsourcing? 6. Which types of software development outsourcing do you have? 7. What kinds of problems do you face with software development projects? 8. Have the problems ever canceled your contract? Why? 9. What benefits do you get from outsourcing? 10. How do you inform the outsource providers about application outage? 11. How long do you need to wait for specialist for elimination of problem and how often does same problem arise? 12. Do you use any ways to solving these problems? 13. How much dose Using those way help you? 14. Do you satisfy using outsourcing? 15. Any suggestions for better work and solving the problems. 152 Appendix B Questionnaire Thank you for taking the time to help us with this survey. 16. How important is using IT in doing your work? Not important at all Somewhat important Not very important Very important 17. What kind of work do you do using IT? Data collection Collaboration Data analyzing Communication Forecasting Other If “Other”, please explain your answer: .............................................................................................................................................. .............................................................................................................................................. 18. What kind of software do you use in your job? .............................................................................................................................................. .............................................................................................................................................. 19. What kind of your IT services are outsourced? Software programming help desk Networks supportive Others …………………………………………………………………….. 20. Why do you use outsourcing services? Please explain your answer. Reducing the cost lack of related technology 153 Lack of adequate staff enabling to focus on your core business Getting work done more efficiently or effectively Others…………………………………………………………………… …………………………………………………………………………… 21. What kind of problem do you have when conducting with outsourcing? Please explain your answer. Time misunderstanding Maintaining relationship quality Cost others …………………………………………………………………………………… …………………………………………………………………………………… 22. What kind of outages usually do you have after implementing the outsourced project? Please explain your answers. …………………………………………………………………………………… …………………………………………………………………………………… 23. How often does same problem arise? Very often Never Often Seldom Very seldom 24. How do you inform the outsourcer department about application outage? Call Send email/ fax/ voice message Visit Other 154 If “other”, please explain your answer: .............................................................................................................................................. .............................................................................................................................................. 25. How long do you need to wait for specialist for elimination of problem? More than 1 week 1 day 4-7 days during day 2-4 days do not need to wait 26. Do you satisfy using outsourcing? Why? Yes No …………………………………………………………………………………… …………………………………………………………………………………… 27. Have you think about any way to eliminating these problems? …………………………………………………………………………………… …………………………………………………………………………………… 28. Do you have any suggestions for better communication and better working with outsourcers? .................................................................................................................................... .................................................................................................................................... .................................................................................................................................... 155 Appendix C UTM – IUMIS, Suggestion List Component: Rekod 7P Version: OR#: UTA_SL_HRMS_PKP_009 CR#, if any: Test Case#: Test Level: UTA(Session 2) Date: 26/06/2009 Attachment: YES NO Severity: 3 1 2 Observation Description: Sumber manusia > Perkhidmatan > Maklumat Peribadi > Rekod 7P Screen: Perincian Sumbangan Sepanjang Tempoh Perkhidmatam Currently, the contents Penyelidikan is used as default screen of Perincian Sumbangan Sepanjang Tempoh Perkhidmatam. Please change it to put the contents of Pengajaran dan Penyeliaan as the default screen. Raised By: Khairul Azmi Ishak/ Helmee Yaakob OR Status Signature: Date Open Closed Date: Regression Component affected: Reviewed by (Team Leader) Comments: Resolution: Resolved by: Verified by: Developer: Date: QA (XYBASE) Date: Test Engineer Date: 156 Appendix D Suggested SLA Template Service Level Agreement (SLA) For CICT outsourcing projects By CICT Effective Date: 157 1. General Agreement Overview This Agreement represents a Service Level Agreement (“SLA” or “Agreement”) between Outsourcer and CICT for the provisioning of Software development project. This Agreement remains valid until superseded by a revised agreement mutually endorsed by two parties. Changes will be recorded in an Amendments section of this Agreement and are effective upon mutual endorsement by them. This Agreement outlines the parameters of all services covered as they are mutually understood by them. The purpose of this Agreement is to ensure that resources are in place to provide consistent service support and delivery to the CICT by the Service Provider(s). 2. Service Description 2.1 Service Scope Place the CICT project focused service description here. 2.2 Assumptions • Services provided by outsourcer are clearly documented in the service catalog. • Funding for major updates will be negotiated on a service-by-service basis. • Changes to services will be communicated and documented. • Service will be provided in adherence to any related policies, processes and procedures 158 • Scheduling of all service related requests will be conducted in accordance with service descriptions. 3. Roles and Responsibilities 3.1 Parties List all relevant contact persons, for example: The following service owner(s) will be used as the basis of the Agreement Service Owner Title/ Role Contact Information 3.2 Service Scope The following Services are covered by this Agreement; Reference No. Service 1001 Provides staffs with a understandable interface 3.3 Service Provider Responsibilities Service Provider responsibilities and/or requirements in support of this Agreement include: • Provide outsourcer with helpdesk services 159 • Maintain and update of the project for a period of time until an extension is made (if required.) • Provide the ability for an extension to the contract (if required) • Meet response times associated with the priority assigned to incidents and service requests. • Generating quarterly reports on service level performance. 3.4 CICT Responsibilities CICT responsibilities and/or requirements in support of this Agreement include: • CICT is a middle man to communicate between stakeholders and vendors. • Provide outsourcer with any information required for project to be completed • Provide real estate agents for interviews required.. • Communicate specific service availability requirements 4. Requesting Service Clear and unambiguous definitions of how long it will take the parties to respond. For example this section might include the definition of initial response to inquiry. For the CICT response time is more important to know, so we consider the distance in KM and then according to this distance the response time will be evaluated Distance of outsourcer organization to UTM: ……………………………….. 1. Web / IT Request: ………………………………………………………..... 2. Contact person Phone: ……………………………………………………... 160 3. Contact person Email: ………………………………………………………. 5. Maintenance and Service Changes All services and/or related components require regularly scheduled maintenance (“Maintenance Window”) in order to meet established service levels. These activities will render systems and/or applications unavailable for normal user interaction as published in the maintenance calendar. • General statement on Change Management process • Communication about emergency maintenance Additional locations and timeframes as required should be added. For example, standard maintenance, major upgrades/changes, 6 Pricing 6.1 Charges It depends on how big the scope is which is depending on the amount of the modules of the project. 7 Reporting, Reviewing and Auditing 7.1 Periodic Review This Agreement is valid from the Effective Date outlined herein and is valid until the Date of Termination. The Outsourcer Relationship Manager is responsible for regular reviews of this document. Contents of this document may be amended as required, provided mutual agreement is obtained from both parties and communicated to all affected 161 parties. The Outsourcer Relationship Manager will incorporate all subsequent revisions and obtain mutual agreements / approvals as required. Designated Review Owner: [Document Owner] Review Period: [Review Period] e.g. “Annually” or “Quarterly” Previous Review Date: [Last or Previous Review Date] Next Review Date: [Next Review Date] 7.2 Service Level Reporting The Service Provider will supply the CICT with the following reports on the intervals indicated: The report should be presented in three ways: 1. Discussions: every two weeks 2. Monthly 3. Meeting on high level committee, 3 or 4 times in a year. Report Name Interval Initial Report 14th June 2010 Contract Extension Report 21st June 2010 14th October 2010 Quarter Report 8 Contract Agreement Accorder Job Title Agreement Date 162 Appendix E Acceptance Test for OM Framework Purpose of Framework: To develop a framework that implements ITIL concepts Immediate Goal: To solve the software development outsourcing problems Long-Term Goal: To improve the outsourcing relationship management and improve quality of services Name: Faculty: Position: Date: How do you rate the OM Framework at this time? (Please mark √ at the respective boxes) 5 Perceived Usefulness: 4 3 2 1 Very Useful Not Useful The degree to which a user believes that using the OM Framework will enhance performance. 5 4 3 2 1 Very Easy Perceived Ease of Use: Very Hard The degree to which a user believes that using the OM Framework will be free from effort. 5 Attitude towards Using: Favorable 4 3 2 1 Very Favorable Not Feeling favorable or unfavorable towards using the OM Framework. Behavioral Intention to use: Will Use Will Not Use The Strength’s of one’s intentions to use the OM Framework in the future. Meets its Purpose: Yes No Achievement of Immediate Goal: Yes No Achievement of Long-Term Goal: Will Achieve Will Fail Suggestions:…………………………………………………………………………………… ……………………………………………………….………………………………………… 163 Participant 1 Acceptance Test for OM Framework Purpose of Framework: To develop a framework that implements ITIL concepts Immediate Goal: To solve the software development outsourcing problems Long-Term Goal: To improve the outsourcing relationship management and improve quality of services Name: Helmee Yaacob Faculty: CICT Position: System Analysis and manager of the development team at CICT Date: 7 October 2009 How do you rate the OM Framework at this time? (Please mark √ at the respective boxes) Very Useful Perceived Usefulness: 5 4 3 2 1 Not Useful The degree to which a user believes that using the OM Framework will enhance performance. 5 4 3 2 1 Very Easy Perceived Ease of Use: Very Hard The degree to which a user believes that using the OM Framework will be free from effort. 5 Attitude towards Using: Favorable 4 3 2 1 Very Favorable Not Feeling favorable or unfavorable towards using the OM Framework. Behavioral Intention to use: Will Use Will Not Use The Strength’s of one’s intentions to use the OM Framework in the future. Meets its Purpose: Yes No Achievement of Immediate Goal: Yes No Achievement of Long-Term Goal: Will Achieve Will Fail Suggestions: you should put on Risk Management during project. Because it‘s very important to project outsourcing. 164 Participant 2 Acceptance Test for OM Framework Purpose of Framework: To develop a framework that implements ITIL concepts Immediate Goal: To solve the software development outsourcing problems Long-Term Goal: To improve the outsourcing relationship management and improve quality of services Name: Fazilah Seren Faculty: CICT Position: Developer Date: 7 October 2009 How do you rate the OM Framework at this time? (Please mark √ at the respective boxes) Very Useful Perceived Usefulness: 5 4 3 2 1 Not Useful The degree to which a user believes that using the OM Framework will enhance performance. 5 4 3 2 1 Very Easy Perceived Ease of Use: Very Hard The degree to which a user believes that using the OM Framework will be free from effort. 5 Attitude towards Using: Favorable 4 3 2 1 Very Favorable Not Feeling favorable or unfavorable towards using the OM Framework. Behavioral Intention to use: Will Use Will Not Use The Strength’s of one’s intentions to use the OM Framework in the future. Meets its Purpose: Yes No Achievement of Immediate Goal: Yes No Achievement of Long-Term Goal: Will Achieve Will Fail Suggestions: 165 Participant 3 Acceptance Test for OM Framework Purpose of Framework: To develop a framework that implements ITIL concepts Immediate Goal: To solve the software development outsourcing problems Long-Term Goal: To improve the outsourcing relationship management and improve quality of services Name: Shahral Amir Faculty: CICT Position: Programmer Date: 7 October 2009 How do you rate the OM Framework at this time? (Please mark √ at the respective boxes) Very Useful Perceived Usefulness: 5 4 3 2 1 Not Useful The degree to which a user believes that using the OM Framework will enhance performance. 5 4 3 2 1 Very Easy Perceived Ease of Use: Very Hard The degree to which a user believes that using the OM Framework will be free from effort. 5 Attitude towards Using: Favorable 4 3 2 1 Very Favorable Not Feeling favorable or unfavorable towards using the OM Framework. Behavioral Intention to use: Will Use Will Not Use The Strength’s of one’s intentions to use the OM Framework in the future. Meets its Purpose: Yes No Achievement of Immediate Goal: Yes No Achievement of Long-Term Goal: Will Achieve Will Fail Suggestions: 166 Participant 4 Acceptance Test for OM Framework Purpose of Framework: To develop a framework that implements ITIL concepts Immediate Goal: To solve the software development outsourcing problems Long-Term Goal: To improve the outsourcing relationship management and improve quality of services Name: Zaman Faculty: CICT Position: PPPM Date: 7 October 2009 How do you rate the OM Framework at this time? (Please mark √ at the respective boxes) Very Useful Perceived Usefulness: 5 4 3 2 1 Not Useful The degree to which a user believes that using the OM Framework will enhance performance. 5 4 3 2 1 Very Easy Perceived Ease of Use: Very Hard The degree to which a user believes that using the OM Framework will be free from effort. 5 Attitude towards Using: Favorable 4 3 2 1 Very Favorable Not Feeling favorable or unfavorable towards using the OM Framework. Behavioral Intention to use: Will Use Will Not Use The Strength’s of one’s intentions to use the OM Framework in the future. Meets its Purpose: Yes No Achievement of Immediate Goal: Yes No Achievement of Long-Term Goal: Will Achieve Will Fail Suggestions: 167 Participant 5 Acceptance Test for OM Framework Purpose of Framework: To develop a framework that implements ITIL concepts Immediate Goal: To solve the software development outsourcing problems Long-Term Goal: To improve the outsourcing relationship management and improve quality of services Name: Suzana Faculty: CICT Position: Developer Date: 7 October 2009 How do you rate the OM Framework at this time? (Please mark √ at the respective boxes) Very Useful Perceived Usefulness: 5 4 3 2 1 Not Useful The degree to which a user believes that using the OM Framework will enhance performance. 5 4 3 2 1 Very Easy Perceived Ease of Use: Very Hard The degree to which a user believes that using the OM Framework will be free from effort. 5 Attitude towards Using: Favorable 4 3 2 1 Very Favorable Not Feeling favorable or unfavorable towards using the OM Framework. Behavioral Intention to use: Will Use Will Not Use The Strength’s of one’s intentions to use the OM Framework in the future. Meets its Purpose: Yes No Achievement of Immediate Goal: Yes No Achievement of Long-Term Goal: Will Achieve Will Fail Suggestions: