Networks and Communications - Course Outline - MS216
advertisement
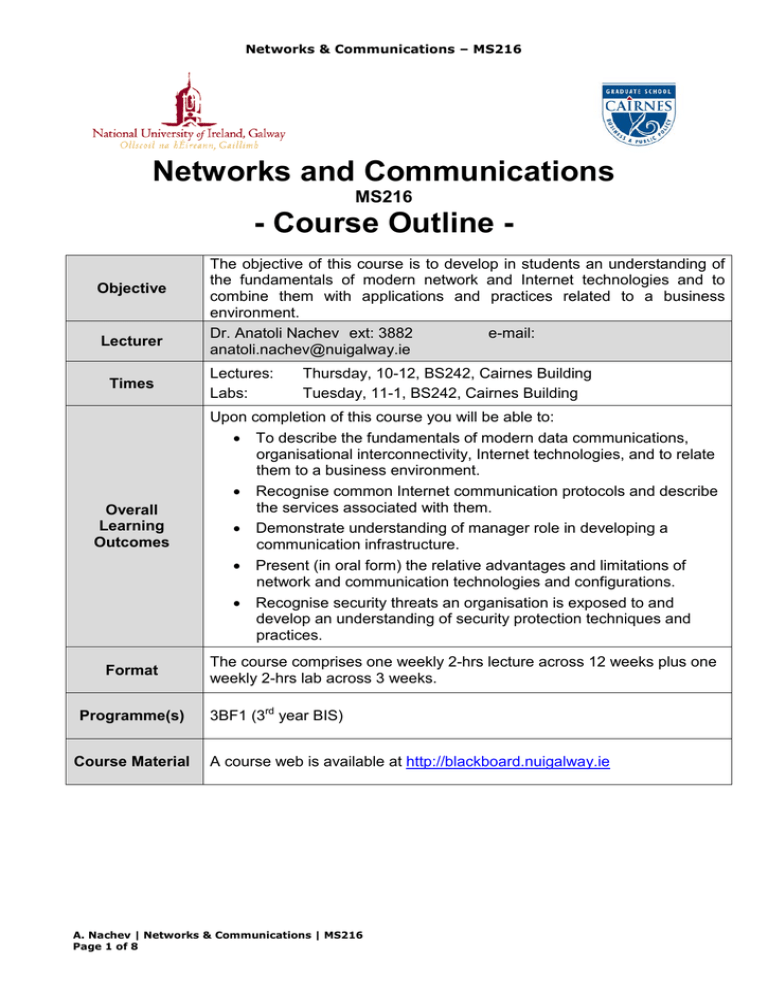
Networks & Communications – MS216 Networks and Communications MS216 - Course Outline Objective Lecturer Times The objective of this course is to develop in students an understanding of the fundamentals of modern network and Internet technologies and to combine them with applications and practices related to a business environment. Dr. Anatoli Nachev ext: 3882 e-mail: anatoli.nachev@nuigalway.ie Lectures: Labs: Thursday, 10-12, BS242, Cairnes Building Tuesday, 11-1, BS242, Cairnes Building Overall Learning Outcomes Upon completion of this course you will be able to: • To describe the fundamentals of modern data communications, organisational interconnectivity, Internet technologies, and to relate them to a business environment. • Recognise common Internet communication protocols and describe the services associated with them. • Demonstrate understanding of manager role in developing a communication infrastructure. • Present (in oral form) the relative advantages and limitations of network and communication technologies and configurations. • Recognise security threats an organisation is exposed to and develop an understanding of security protection techniques and practices. Format The course comprises one weekly 2-hrs lecture across 12 weeks plus one weekly 2-hrs lab across 3 weeks. Programme(s) Course Material 3BF1 (3rd year BIS) A course web is available at http://blackboard.nuigalway.ie A. Nachev | Networks & Communications | MS216 Page 1 of 8 Networks & Communications – MS216 Assessment 1. 2. 3. End of Year Examination Continuous Assessment Mid-term group assignment 65% 15%* 20% * Continuous assessment involves five MCQ tests. Workload Credit weighting: Lecture hours: Computer laboratory hours: Independent assignment work: Independent study: Associated hours: Examination: Total Student Effort: 5 ECT 24 6 25 55 13 2 125 hours Core Text: (Students need their own copy) [1] MS216 Networks & Communications Course Pack. [2] Forouzan, B., 2003, Business Data Communications, McGraw-Hill, 1 ed., ISBN: 0-7112194-3. Supplementary Text(s): [3] Forouzan, B., Data Communications and Networking, 4 ed., McGraw-Hill, 2007. [4] Stallings, W., Business Data Communications, 6 ed., Prentice Hall, 2007. [5] Fitzgerald, J & Dennis, A. Business Data Communications and Networking, 10 ed., John Wiley & Sons, 2010. [6] Forouzan, B. TCP/IP Protocol Suite, McGraw-Hill, 3rd ed., 2006. [7] Panko, R. Business Data Networks and Telecommunications, 7 ed. Prentice Hall, 2009. [8] Stallings, W., Cryptography and Network Security: Principles and Practice, 4 ed., Prentice Hall, 2006. [9] http://httpd.apache.org/docs/misc/FAQ.html [10] Conklin et al. Principles of Computer Security. Security+ and Beyond, McGraw-Hill, 2004. A. Nachev | Networks & Communications | MS216 Page 2 of 8 Networks & Communications – MS216 Agenda Topic Week 1: Internet - Overview • Computer networks - overview. • The Internet history. • Internet administration. • Conceptual view of Internet. o ISPs. • OSI overview. Readings [1] Ch 1 [2] Ch 1, 13 [3] Ch 1,2, App. C [5] Ch 1 [6] Ch 1, 2 [7] Ch 6 Week 1 Outcomes: You will be able to … • • • • • Distinguish between different types of networks. Describe the Internet evolution. Describe Internet authorities and their functions. Explain the Internet structure. Distinguish between network layers. Week 2: Internet Connectivity • • Internet infrastructure. Internet connectivity o Conventional modems. o ISDN. o DSL. o Cable modems. o Leased lines, packet switched WANs. o Fixed wireless Internet. o Satellite Internet. [1] Ch 2 [2] Ch 8, 9, 12 [3] Ch 9, 18, 20, 21 [5] Ch 7, 8, 9 [6] Ch 3 Week 2 Outcomes: You will be able to … • • • • • Distinguish between different technologies used for connection to the Internet. Identify the role of the manager in selecting correct connections. List advantages and limitations of those connections. Explain what equipment is required for each type of connection. To identify some new and emerging technologies for Internet connection. Weeks 3, 4: Internet Communication Model: Application Layer Services • Communication models and protocol suites: TCP/IP, IPS/SPX, AppleTalk, SNA. • TCP/IP protocols stack. • E-mail components and functioning. o User agents and mail transfer agents. A. Nachev | Networks & Communications | MS216 Page 3 of 8 [1] Ch 3, 4 [2] Ch 2, 13 [3] Ch 26, 27 [4] Ch 4 [5] Ch 2 [6] Ch 18, 19, 20, 22, 23 Networks & Communications – MS216 • • • o E-mail delivery stages. o Push protocol - SMTP, MIME. o Access protocols POP3 and IMAP, proprietary protocols. o Mailing lists. o Spam and anti-spam techniques. FTP. Telnet. World Wide Web. o WWW components. o URL, URN, URI. o Search engines and Google - components and operation. o Browser architecture. o Hyper-Text Transfer Protocol (HTTP). o HTTP request and response messages. o Web documents. Weeks 3, 4 Outcomes: You will be able to … • • • • • Describe fundamentals of the Internet application layer services. Recognise communication protocols HTTP, SMTP, POP, IMAP, MIME, FTP, and Telnet and comment on their correct usage. Identify messages that clients and servers exchange. Take decision on building up an Internet server infrastructure. List anti-spam techniques and policies. Weeks 5, 6: Internet Communication Model: Web Servers • Web server location, outsourcing, collocation. o Server OS • Web server hardware requirements, fault tolerance. • Web server software. • Apache. • IIS: setup and configuration, security settings. • IIS administration tools. o Management Console. o User manager. o Server security. • IIS: Fault tolerance and backup, backup policy. o IIS: Web server logging. A. Nachev | Networks & Communications | MS216 Page 4 of 8 [1] Ch 5 [9] Networks & Communications – MS216 Weeks 5, 6 Outcomes: You will be able to … • • • • • Take decision on selection of o Server location o Hardware o Fault tolerance components o Software Recognise which server components are to be installed. Demonstrate techniques for remote administration. Demonstrate basic server administration activities. Set up intranet / extranet sites. Week 7: IP Addresses and Routing. • Transport layer protocols: TCP and UDP. • Network layer and IP. • IP addresses o IP address classification o Subnetting and supernetting o Masks o Dynamic address configuration, DHCP o IP address registration • Routing techniques. • Static vs. dynamic routing, routing algorithms. [1] Ch 6 [2] Ch 4 [3] Ch 20, 21, 22, 25 [6] Ch 4, 5, 6 Week 7 Outcomes: You will be able to … • • • • • Describe the IP address distribution mechanism and recognise distribution organisations. Distinguish between different classes of IP addresses and their suitability to different sizes of organisations. Explain the DHCP service. Demonstrate work with IP utilities such as PING, TRACERT, IPCONFIG. Distinguish between different routing techniques. Week 8: Domain Name System (DNS) • Domain name space. • Distribution of name space, DNS servers, zones. • DNS and Internet. • DSN resolution, caching. • Domain name registration. • DNS utilities. A. Nachev | Networks & Communications | MS216 Page 5 of 8 [1] Ch 7 [3] Ch 25 [6] Ch 16 Networks & Communications – MS216 Week 8 Outcomes: You will be able to … • • • • • Explain the role of the domain name system in a communication infrastructure and a necessity of a DNS server. Use FQDN and PQDN. Distinguish between different types of DNS resolution. Improve efficiency of services by caching. Work with DNS utilities. Week 9: Need for Security: Attacks and Malware • Business needs for information security • Denial-of-service attacks o SYN flooding o Ping of death o Distributed DoS • Backdoors & trapdoors • Sniffing • IP spoofing • Smurf attacks • Man-in-the-middle attack • Reply attack • Password guessing and cracking • Malware o Viruses o Trojans o Worms o Logic bombs [10] Ch 15, also available from http://highered.mcgrawhill.com/sites/dl/free/0072255099/ 172083/SampleChapter.pdf Week 9 Outcomes: You will be able to … • • • • Recognise that organisations have business needs for information security Identify threats posed to information security Describe the most common attacks, including denial-of-service, spoofing, sniffing, password attacks, etc. Describe the different types of malicious software that exist, including viruses, worms, trojans, and logic bombs Weeks 10, 11: Network Security Techniques • Security requirements. • Secret key encryption o Block ciphers: DES, TDES, AES. • Key management, session keys. o Diffie-Hellman protocol. o Key Distribution Center (KDC). o Kerberos. • Public key encryption, RSA algorithm. • Digital signature. A. Nachev | Networks & Communications | MS216 Page 6 of 8 [1] Ch 9 [2] Ch 14 [3] Ch 29, 30, 31 [4] Ch 20 [5] Ch 10 [7] Ch 9, module F [8] Ch 9, 10, 11 Networks & Communications – MS216 • • Digital certificates. Security protocols: o IPsec. o TLS / SSL. o Application layer security. Weeks 10, 11 Outcomes: You will be able to … • • • • • • List security requirements for a secure system over the Internet. Distinguish between secret and private key encryption. Describe the role of digital signature and digital certificates in secure communications. Compare different classes of digital certificates and explain the application process. Describe the strengths and weaknesses of different encryption and key distribution techniques. Explain how a secure connection between browsers and servers is established. Weeks 12: Attack Prevention systems • Firewalls o Packet filters. o Circuit-level gateways. o Application gateways. o Stateful multilayer inspection firewall. o Network address translation (NAT). • Firewall architecture. • Security holes. • Virtual Private Networks (VPNs). [1] Ch 10 [2] Ch 10, 14 [3] Ch 30, 31 [7] Ch 9, module F [8] Ch 16, 18 Week 12 Outcomes: You will be able to … • • • • Distinguish between different types of firewalls and their correct deployment. Discuss how NAT servers enhance security of an organisation. Describe how hacker attacks are usually launched. Explain how VPNs provide cheap solutions for secure connections between branches of a corporate network or between individuals and a network. A. Nachev | Networks & Communications | MS216 Page 7 of 8 Networks & Communications – MS216 Lectures & Labs Schedule: Semester 1 Week Lecture Lab 1 y 2 y 3 y 4 y 5 y 6 y 7 y y 8 y y 9 y y 10 y 11 y 12 y Other Information: Lab sessions will begin in week 7 and persist to week 9 inclusive, providing 3 sessions. Each session is of 2 hours’ duration. Labs use a LAN of servers based on MS Windows 2003 and IIS v.6.0. General: This course is available on the Blackboard in ppt format. Should you have a visual disability and require the document in another format, please contact me and I will oblige. A. Nachev | Networks & Communications | MS216 Page 8 of 8