Governance, Risk,
and Compliance
Cisco Security Advisory Services
Information Security
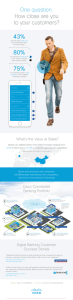
Information is one of the most valuable resources in
business, and the continued expansion of the Internet
of Everything (IoE) is making it increasingly more vital to
secure connections between people, processes, data, and
things. Organizations today need cybersecurity solutions
that work intelligently with your networks, applications, and
infrastructure so you can take advantage of the opportunities
of IoE and related cloud and mobility technologies while
effectively managing security and risk.
Benefits
More Connections, More Threats to Information Security
• Protect Your Data and Infrastructure
Identify and mitigate the most common
infrastructure, application, and operational
vulnerabilities
Many organizations, however, do not have a clear understanding of
what information is most critical, where it is located, or how it should
be managed. Tracking the various applications that support business
processes—including where they are located, which ones are vulnerable,
which ones process regulated information, and how they change over
time—can be difficult.
• Ensure Effective Programs Are in Place
Provide comprehensive application,
network, operations, and organizational
security
• Perform Proactive Threat Management
Prepare for new and evolving threats
• Ensure Organizational Alignment
Allocate security resources and
investments to support business strategies
• Meet Compliance Requirements
Understand and maintain ISO 27001,
PCI DSS, and other certifications and
standards
Improve Protection of Your Business Assets
Cisco® Security Advisory Services for Information Security help
organizations maintain the confidentiality, integrity, and availability of
critical business assets, as well as manage complex risk and compliance
requirements with greater ease and efficiency. Our experts draw on
years of experience, proven methodologies, and advanced tools to help
organizations protect critical business assets and manage security across
the IT infrastructure.
We start by listening to your challenges and goals. Then we collaborate
to customize proven governance frameworks and strategies to meet
each client’s unique needs and provide robust risk and compliance
management, innovative approaches to IoE security, and world-class
threat management. Through our partnership, you uncover new ways to
think about security and its impact on your business. You gain knowledge
that helps your teams anticipate threats, adapt to the changing security
landscape, and develop a strong security posture. With greater knowledge
about security, you’ll think differently about business.
More About Our Services
• Information Security Risk Assessment: Identifies and prioritizes
strategic, operational and systemic information and system risks that
affect the execution of IT strategies and recommends treatment to
reduce or eliminate unacceptable risks.
© 2015 Cisco and/or its affiliates. All rights reserved.
Cisco Security Advisory Services: Information Security
• Information Risk Program Development: Builds a solid
risk management foundation through the creation of a
new information security program, customization of an
existing program, or revamping your strategy to support
new IT initiatives.
• Information Security Program Assessment: Holistically
addresses application, endpoint, and network vulnerabilities
with consolidated processes, policies, and controls to
create a comprehensive and measurable information
security program that protects your business.
• ISO 27001 Advisory Services: Understand the
certification process and determine your current level
of preparedness to gain ISO 27001 certification.
• ISO 27002 Assessment: Determines organizational
alignment to ISO 27002 controls and defines
remediation plans to address gaps.
Cisco Advisory: Seasoned Security Professionals
As strategic and technical advisors, Cisco Security Advisory
Services help leading organizations and executive teams
identify strategic opportunities in information security to
improve performance and create long term and sustainable
business value.
Backed by a superior combination of resources — vast
research and threat intelligence, mature methodologies,
and multidisciplinary experts across security, cloud,
mobility, collaboration, and data center operations—our
clients better manage risk and compliance, develop a
strong security posture, control cost, and achieve strategic
IT and business objectives.
Technology-Enabled Consulting with Cisco
Advisory Accelerator Advisory
Accelerator is our project management, workflow,
and reporting platform for security assessments. It
enables rapid execution of project tasks, integrates with
many of our security assessment tools, and facilitates
efficient report generation and consultant collaboration.
Advisory Accelerator provides large scale efficiencies,
allowing consultants more time on in depth analysis, as
a collaborative extension of the consulting expertise that
Cisco provides.
Key Features
Case Study: Technology Provider
Challenges
• Enable “bring your own device” (BYOD) for
workforce flexibility
• Mitigate information security risk associated
with BYOD
Solution
• Advisory services for development of BYOD policies
• Integrate BYOD with information security policies
• Refine related policies as needed
Outcomes
• Operationalized new policies and standards
to enable BYOD
• Integrated and developed sustainable mobile
workforce security controls and updated
network controls
• Mitigated BYOD-related threats
• Assessment guidance, workflow and reporting
• Trend analysis to support ROI, budget planning
and product selection
• Expert collaboration, brainstorming and strategy support
• Crowd-sourced, quality controlled knowledge engine
Next Steps
• Faster ramp of inexperienced security professionals
Visit www.cisco.com/go/securityservices to connect
with our advisors and protect your business today.
© 2015 Cisco and/or its affiliates. All rights reserved. Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco
trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership
relationship between Cisco and any other company. (1110R) DEC14CS4667 09/15