CS475 – Networks Assignments Lecture 8 Chapter 3 – Internetworking
CS475 – Networks
Lecture 8
Chapter 3 – Internetworking
Assignments
• Reading for Lecture 9: Section 3.3
3.2 Basic Internetworking (IP)
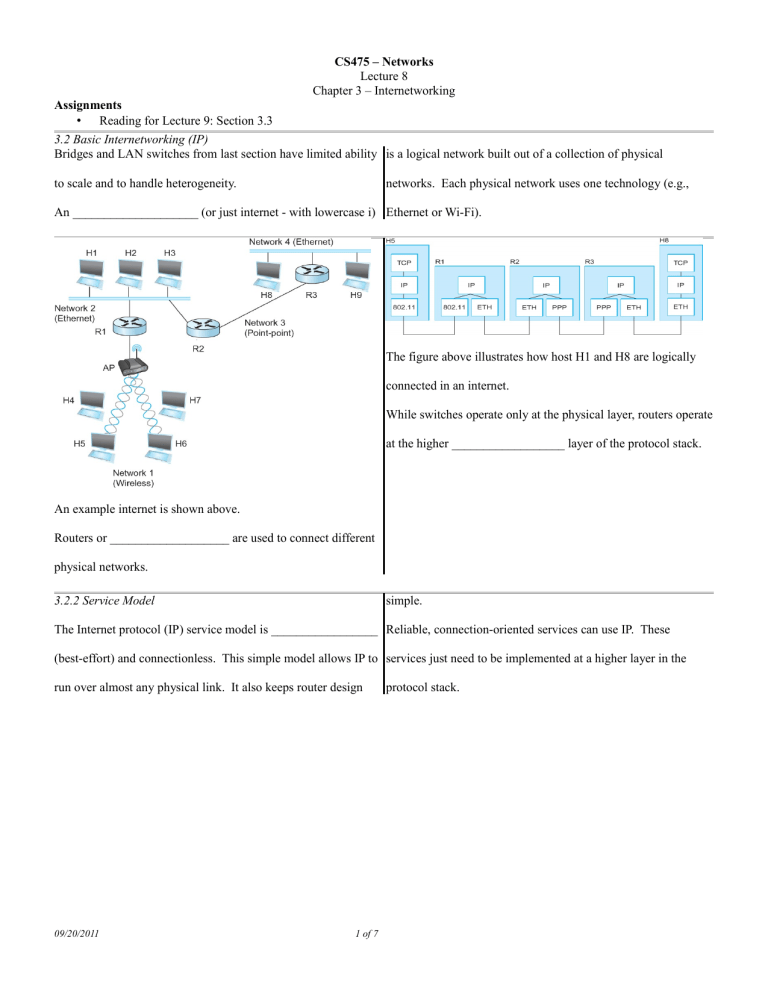
Bridges and LAN switches from last section have limited ability is a logical network built out of a collection of physical to scale and to handle heterogeneity.
networks. Each physical network uses one technology (e.g.,
An ____________________ (or just internet - with lowercase i) Ethernet or Wi-Fi).
The figure above illustrates how host H1 and H8 are logically connected in an internet.
While switches operate only at the physical layer, routers operate at the higher __________________ layer of the protocol stack.
An example internet is shown above.
Routers or ___________________ are used to connect different physical networks.
3.2.2 Service Model simple.
The Internet protocol (IP) service model is _________________ Reliable, connection-oriented services can use IP. These
(best-effort) and connectionless. This simple model allows IP to services just need to be implemented at a higher layer in the run over almost any physical link. It also keeps router design protocol stack.
09/20/2011 1 of 7
3.2.2 Service Model - Packet Format
The IP packet is treated as a collection of 32 byte words.
The IP Version 4 packet format is shown at right. The HLen field is the size of the header (number of 32 bit words). The
Type Of Service ( TOS ) field allows for
__________________________ service.
The Length fields contains the entire packet size in bytes (up to
65.535 bytes). The Ident , Flags and Offset support
_______________ and reassembly and will be discussed shortly.
The Time To Live ( TTL ) field is decremented at each router.
When it reaches 0 the packet can be dropped. It is intended to prevent an endlessly circulating packet. An initial value of 64 is the default.
The Protocol field is a demux key (TCP is 6, UDP is 17). The
Checksum is a 16 bit checksum over the header. Packets with checksum errors are dropped.
The SourceAddr and DestinationAddr
3.2.2 Service Model - Fragmentation and Reassembly
To allow sending IP packets over links with different Maximum fragment (it is the same as in the
Transmission Units (_________________) IP allows packets to original packet). The M bit in the be fragmented while in route to the destination.
Flags field is 1 except in the
____________ fragment. The Offset is the byte offset divided by 8.
(Fragmentation is on an 8 byte
Fig 3.17 IP packet fragmentation boundary only.)
Notice that the fragments are not reassembled until they reach the destination.
The Ident field is the same in each
are 32 bit
___________________________ (not MAC addresses!)
There may be any number of Options . These are rarely used.
09/20/2011 2 of 7
3.2.3 Global Addresses
IP addresses are globally unique. Each host has a unique IP
(actually each interface has a unique IP, hosts with multiple
NICs and routers will have multiple IP addresses.
IP addresses are __________________________. They consist
Fig 3.19 IP Addresses
(a) class A address
(b) class B address
(c) class C address of a network part and a host part.
The network and host parts of the IP address are not fixed-size.
3.2.4 Datagram Forwarding in IP
Hosts or routers that have the same network part are on the same Conceptually the forwarding table for router R2 could appear as
____________________ network.
Every physical network connected to the Internet contains at shown below. least one router.
The network part uniquely identifies a single physical network on the Internet.
Every IP datagram contains the IP address of the destination.
Every node in the path (including the source) looks at the network part of the destination address to determine if it is on the same physical network as the destination.
Router R2 Forwarding Table
• If the node is on the same physical network it sends it directly to the destination
• If not, it sends the packet to the next _______________ by consulting its forwarding table.
2
3
Network NextHop
1 R1
4
Int 1
Int 0
R3
A network may have multiple routers. If the forwarding table does not contain an entry for a desired network, the packet can be sent to the _____________ router (or gateway).
The forwarding table for many end nodes (hosts) may contain only an entry for a single default router.
Note that forwarding tables used in routers contain entries for network addresses, not individual hosts.
09/20/2011 3 of 7
3.2.5 Subnetting and Classless Addressing
The original IP classes (A, B, C) resulted in a lot of wasted IP In the example below a subnet mask with 24 leading 1s allows a address. Every network, no matter how small, required at least a Class B address to be subnetted into 256 subnets with 255 hosts class C network address with up to 255 hosts.
on each subnet.
A fairly large network of 1000 hosts would require a class B network address leaving 64000 IP addresses unusable.
All hosts on the same subnet have the same subnet address and subnet mask.
__________________________ allows for much more efficient Externally the subnetted network still appears as a single Class B use of the IP address space by allowing a network number to be network.
split and the pieces assigned to different subnets.
Subnetting works by using a portion of the host number as a subnet ID. The subnet ID and network number together form a subnet number (address).
A subnet _____________ is used to define which bits of an address are part of the subnet address and which bits are used to identify a host on the subnet.
An example subnetted network is shown at right. The top two networks can have up to 127 hosts. The bottom network can have up to 255 hosts.
Subnet # SubnetMask Next
128.96.34.0
255.255.255.128 intf0
128.96.34.128 255.255.255.128 intf1
128.96.33.0
255.255.255.0
R2
Forwarding table for Router R1
Forwarding tables for the internal routers must also include a subnet mask.
A host now ____________ a destination IP with its own subnet is not, the packet is sent to the default router.
mask to see if the destination subnet is the same as the sources Note that it is not necessary that the 1s in the subnet mask be subnet. If it is the packet is sent directly to the destination. If it contiguous, but this is highly recommended.
09/20/2011 4 of 7
Classless ______________________ Routing (CIDR) drops the The ISP advertises a 21 bit CIDR address that is used externally classful addresses discussed previously and allows the network for routing. Routers within the ISP route traffic to 8 different part of an IP address to be any length. In CIDR, network networks.
addresses are represented using a /X after the network prefix.
With CIDR the network portion of an IP address may match
192.4.16/24 would include all IP addresses in the range multiple entries in a router's forwarding table. Forwarding is
192.4.16.0 – 192.4.16.255 (256 IP numbers), while 192.4.16/20 then based on the “________________________”.
would include all IP addresses in the range 192.4.16.0 –
192.4.31.255 (4096 IP numbers).
Entries for both 171.69/16 and 171.69.10/24 match an IP destination of 171.69.10.100. The second entry is the longest, so the packet would be routed to 171.69.10/24.
A packet addressed to 171.69.12.5 would be routed to 171.69/16
(assuming that there are no other matching entries).
Fig. 3.22 Route Aggegration
3.2.6 Address Translation (ARP)
The Address Resolution Protocol (ARP) enables a host to the target IP, the source IP and source link-layer address.
dynamically construct a table (known as the ARP table or cache) The target adds or refreshes its ARP cache with a source entry of IP address to physical address mappings.
and then sends an ARP __________________ to the source.
Since the mappings may change over time (NIC card replacement) the entries time-out and are removed periodically
(15 min is typ.).
ARP relies on the fact that most link-level technologies support
_________________________.
If a host wants to send an IP datagram to a node on the same
The ARP packet format used on Ethernet is shown above. HLen network it first checks its ARP cache for a mapping. If there is and PLen are the lengths of the hardware and protocol addresses no entry the host broadcasts an ARP query. The query contains in bits. Operation is 1 for a query and 0 for a reply.
09/20/2011 5 of 7
3.2.7 Host Configuration (DHCP)
Ethernet addresses are hardwired into the adaptor. IP addresses A DHCP server sends out IP addresses to hosts when they can not be hardwired since all hosts on the same physical __________________. The server can be configured to always network must have a common network address.
give the same IP address to the same interface (based on its
Most operating systems allow the IP address and the IP address MAC address) or the server can hand out IP addresses from a of the default router/ gateway to be manually configured.
Manual configuration is time consuming and error prone. The primary method of automatic configuration is known as pool of IP addresses.
The DHCP server might be a standard computer server or a router. The DHCP server might also be setup to provide other
Dynamic Host Configuration Protocol (__________________).
network services (DNS, email, etc).
When a host on the network boots it sends a DHCPDISCOVER message to the IP broadcast address (255.255.255.255). Routers will pass IP broadcasts to other subnetworks (subnets) but not to other networks. The DCHP server replys with an IP address that can be used by the hosts.
It is possible to use DHCP ______________________ so that one DHCP server can provide IP addresses to multiple networks.
A DHCP relay agent receives a broadcast DHCPDISCOVER message and sends a unicast to a DHCP server on another network.
DHCP packet format
(See the text for details.)
4.1.7 Error Reporting (ICMP)
IP networks support a companion protocol – Internet Control
Message Protocol (ICMP) - that is used for reporting
(destination host unreachable, failed reassembly, TTL decremented to 0, checksum error, etc.)
__________________ back to the source host whenever a router An ICMP-Redirect control message can be used to send a better
(or host) is unable to process a datagram successfully route back to a host so that it can update its forwarding table.
09/20/2011 6 of 7
3.2.9 Virtual Networks and Tunnels
Virtual circuit networks can be used to create virtual private networks (_____________________) that act very much like separate private networks.
VPNs use a shared network to create private networks.
The Internet can be used to create VPNs via the use of an IP If router R1 receives a packet containing an address in network tunnel. An IP tunnel is a virtual point-to-point link between two 2, it encapsulates the packet in an IP packet destined for router
_______________________ routers.
R2. R2 strips the added header and forwards the packet to network 2.
VPNs can be used for __________________ or to carry non-IP packets across an IP network. Tunnels can also be used to connect two routers that may have special capabilities.
In Class Exercises
Explore the following Unix commands:
1) arp
2) route
3) ping and traceroute/tracert
09/20/2011 7 of 7









