Case Studies in Public Private Partnership Click to edit Master text styles
advertisement

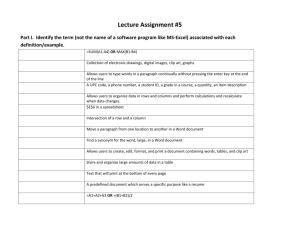
Case Studies in Public Private Partnership Click to edit Master text styles – Second level Third level – Fourth level Fifth level Cheri McGuire Principal Security Strategist Trustworthy Computing Critical Infrastructure Protection Microsoft's Critical Infrastructure Protection Program Click to edit Master text styles – Second level Third level – Fourth level Fifth level Drive strategic ecosystem and internal change that enhances critical infrastructure security and resiliency, builds trust and alignment of action with governments and critical infrastructure providers. Critical Infrastructure Protection The World Today Click to edit Master text styles – Second level Third level – Fourth level Fifth level Instant Messenger traffic – one day in June 2006 Almost 1 billion different sessions with more than 7 billion IM messages sent Aproximately 93 million users logged in with 64 million different users becoming engaged in conversations Approximately 1.5 million new users that were not registered within Microsoft Messenger were invited to join Planetary‐ Planetary‐Scale Views on a Large Instant‐ Scale Views on a Large Instant‐Messaging Network Jure Leskovec Carnegie Mellon University and Erik Horvitz Microsoft Research Jure Leskovec Carnegie Mellon University and Erik Horvitz Microsoft Research Critical Infrastructure Protection Threat Trends Exponential Growth of IDs Increasingly Sophisticated Malware Identity and access management challenging Anti‐ Anti‐malware alone is not sufficient Number of variants from over 7,000 malware families (1H07) Number of Digital IDs B2C styles Click to edit MasterB2Etext – Second level Third level Internet – Fourth level Client/server Fifth level Mainframe B2B Mobility Pre‐ Pre‐1980s 1980s 1990s 2000s Crime On The Rise Attacks Getting More Sophisticated Traditional defenses are inadequate Largest segment by $ spent on defense National Interest Source: Microsoft Security Intelligence Report (January – June 2007) Largest area by $ lost Spy Fastest growing segment Thief Personal Gain GUI Applications Drivers Trespasser Personal Fame User O/S Vandal Curiosity Largest area by Author volume Examples: • Spyware • Rootkits • Application attacks • Phishing/Social engineering Hardware Physical Script‐ Script‐Kiddy Amateur Expert Specialist Critical Infrastructure Protection CIIP Partnership Fundamentals Click to edit Master text styles Embraces – Secondcore levelaspects of terms "public-private" and "partnership" Third Provides the level structure, processes, and environment for "Trusted – Fourth level Collaboration" Fifth Aligns industry and level government requirements, priorities, goals and objectives Flexible and adaptable to address changing risk landscape Provides value for both government and industry members Focuses on continual improvement and assessment of lessons learned Critical Infrastructure Protection International Partnerships International Click to edit Telecommunication Master text styles Union -– Second Member of the ITU’s Development Sector to build cyber security level - capacity and promote effective risk management skills Third level Contributed to report for national administrations with a – Fourth level for addressing cybersecurity at the management framework national level and for organizing and implementing a national Fifth level cybersecurity strategy International Botnet Task Force - - Dedicated to sharing information about botnets, including intelligence, technical details, and strategies in order to combat the botnet problems Includes 130 law enforcement participants from over 30 countries, and 50 industry participants from over 40 private companies Critical Infrastructure Protection National-level Partnerships Japan Japan Computer Emergency Click to edit Master text styles Response Team Coordination Center – Second level National Infrastructure Security Third level Center – Fourth level Fifth level Australia Infrastructure Assurance Advisory Group United Kingdom Centre for the Protection of National Infrastructure Vendor Security Information Exchange United States Critical Infrastructure Partnership Advisory Council Network Security and Information Exchange National Security Telecommunications Advisory Committee Critical Infrastructure Protection Private Sector Partnerships Click to edit Master text styles – Second level Third level – Fourth level Industry Consortium for Fifth level Advancement of Security on the Internet Enhances the global security landscape by driving excellence and innovation in security response practices Enables its members to proactively collaborate to analyze, mitigate, and resolve multi‐vendor, global security challenges Software Assurance Forum for Excellence in Code Dedicated to increasing trust in ICT products and services through the advancement of proven software assurance methods Paper released tomorrow: Fundamental Practices for Secure Software Development: A Guide to the Most Common and Effective Secure Development Practices in Use Today Critical Infrastructure Protection Resources Critical Infrastructure Resiliency Exercise Guide cipteam@microsoft.com Click to edit Master text styles Security Intelligence Report – Second level http://www.microsoft.com/downloads/Search.aspx?displaylang=en# Third level Security Cooperation Program – Fourth level http://www.microsoft.com/Industry/government/scp.mspx Fifth level Microsoft Security Response Center secure@microsoft.com SAFECode www.safecode.org ICASI www.icasi.org My Contact Information: Cheri McGuire – cheri.mcguire@microsoft.com Critical Infrastructure Protection Click to edit Master text styles – Second level Third level – Fourth level Fifth level © 2008 Microsoft Corporation. All rights reserved. Microsoft, Windows, Windows Vista and other product names are or may be registered trademarks and/or trademarks in the U.S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION. Critical Infrastructure Protection