International Journal of Application or Innovation in Engineering & Management... Web Site: www.ijaiem.org Email: , Volume 2, Issue 6, June 2013
advertisement

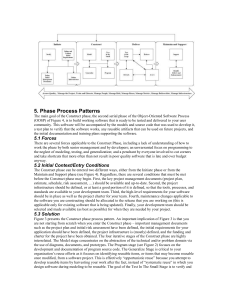
International Journal of Application or Innovation in Engineering & Management (IJAIEM) Web Site: www.ijaiem.org Email: editor@ijaiem.org, editorijaiem@gmail.com Volume 2, Issue 6, June 2013 ISSN 2319 - 4847 Development of Reuse Repository and Software Component Performance Analysis P.Niranjan1, Dr.P.Shireesha2, M.Venugopal Reddy3 1, 2, 3 Department of Computer Science &Engineering, Kakatiya Institute of Technology & Science, Warangal, India ABSTRACT Software engineering is a profession dedicated to the creation and maintenance of software applications by applying technologies and practices from computer science. Software Reuse is the process of implementing or updating software systems using existing software assets. Software Reusability modelling is helpful to appraising the quality of developed or developing reusable software components and in identification of reusable components from existing systems. This can reduce the cost of developing the software from scratch. In this paper developing software repository with structural attributes of software components are represented quantifiably with help of software metrics and performance of hierarchical clustering based approach is investigated to identify the reusable object oriented software systems. That the performance of hierarchical clustering based approach is satisfactory enough for the identification of the object based reusable modules from the existing software reuse repository. Keywords— Software Reuse, Software Architecture, Reusability, Clustering 1. INTRODUCTION The Software metrics are useful in helping software developers to develop large and complex software systems. The aim of metrics is to forebode the quality of the software merchandises. Effective software reuse requires that the users of the system have access to appropriate components. The user must access these components accurately and quickly, and be able to modify them if necessary. Various attributes, which ascertain the quality of the software, include maintainability, defect density, fault proneness, normalized rework, Comprehensibility, reusability etc. Today the requirement is to associate the reusability attributes with the metrics and how these metrics collectively ascertain the reusability of the software component to find. Software architecture is thus important for software development, but architectures do not have an explicit representation in most general aim programming languages. Another problem is that successful software applications are doomed to continually evolve and grow. Architecture the conceptual architecture often becomes inaccurate with regard to the implemented. Several approaches and techniques have been proposed in the literature to support software architecture reconstruction (SAR). First raw and simple classification of SAR environments based on a few typical scenarios (filter outing and clustering, compliance checking, this consequences in architectural erosion, drift, mismatch, or chasm analysers generators, program understanding, and architecture acknowledgment). This paper presents a state of the art of software architecture reconstruction approaches to construct reuse repositories. While it is a re-examine on the research in SAR, we organized it from the perspective of a change by reversal applied scientist who desires to reconstruct the architecture of an existing application and would like to cognise which approaches to consider. We structure the field around the following axes: the goals, the process, the inputs, the techniques, and the end points of SAR approaches. Map of research field or in each axis, we class both the most influential approaches and the original ones, with the goal to create a structured mention. 2. PREVIOUS WORK Organizations implementing systematic software reuse programs must be able to measure their progress and identify the most effective reuse strategies. Architecture is a critical issue in the development of any complex software system. Software system architecture has become an important subfield of software technology in both academic and industrial community. Software architecture describes the gross structure of a software system with a collection of elements, connectors and constraints. Carrying out and furnishes a blue print for system construction and composition software architecture acts as a bridge between requirements. It assists to understand large systems, support reprocess at both component and architecture level. Architecture intends to the major components to be developed and their relationships and constraints, expose changeability of the system, verify and validate the target system at a high degree and so on. Recently, software architecture is used to aid maintenance and evolution to cut down their complexity and cost that mainly upshot from the difficulty of understanding the large-graduatedtable and complex software. Since that software architecture aids to understand large-graduated table software systems is well recognized, it is a natural idea to understand the system to be kept and evolved through its architecture. [2] Volume 2, Issue 6, June 2013 Page 473 International Journal of Application or Innovation in Engineering & Management (IJAIEM) Web Site: www.ijaiem.org Email: editor@ijaiem.org, editorijaiem@gmail.com Volume 2, Issue 6, June 2013 ISSN 2319 - 4847 Software architecture produced at contrive phase (called designed software architecture) seems able to be directly used in maintenance and evolution. Unfortunately, it cannot work well for three reasons. Firstly, the contrived software architecture may be not available because the system is developed without an explicit architectonic phase or the documents are lost. Secondly, the contrived software architecture may have some differences or mismatch with the actual software architecture built in the target system. Ideally, Maintainers always obey the strict principles of software engineering, and ideally, if the developers e.g., update the contrived documents when any alteration is did in carried out or maintenance, the designed software architecture should correctly describe software architecture of the target system. Target system is too trivial and but in practice, such work to keep the consistency among the documents, tedious and error-prone to be done seriously. Then, the differences or mismatch between the designed software architecture and the actual software architecture constructed in the system appear and become more when time elapses. Thirdly and finally, May not accommodate for maintenance and evolution and since different stakeholders have different requirements, the designed software architecture is for development. Typically, the maintainers necessitate much more details about the system than the developers, e.g., internal structure of a component, details of a connector, and so on. Then, architecture-based maintenance and evolution should use software architecture recovered from the target system, instead of the designed software architecture. [2] Software architecture used in maintenance and evolution is usually recovered from the source code and other documents of the target system based on program comprehension. Such retrieved software architecture cannot capture some special information seeming at runtime, which are important to maintenance and evolution. For examples, the number of togs, size of buffers, number of network connections, apply charge per unit of CPU and memory, number of component instances, total number of invocations to a given component or its method, and other information related to workload are critical to tune performance. The exceptions come about at runtime aid to correct errors. the maximum, minimal and average response time of a gave method may identify that the algorithm in this method has to be reimplemented. Though these runtime details may be available in some special management tools, they are hard to incorporate into software architecture recovered from the documents. Consequently, the maintainers cannot acquire all of their required information from the recovered software architecture. Software reuse classification and retrieval approaches have been classified with minor differences based on available software reuse systems and also based on researcher’s criteria. Various methods to classify software reusable components have been proposed and implemented. Attribute classification scheme is well suited to develop the software reuse repositories. 3. PROPOSED SYSTEM The proposed system ‘development of software reusable repository’ is required to implement a classification scheme to build a library and to provide an interface for browsing and retrieving components. The main requirement is to develop a classification scheme which is used for classifying components. The system should support three operations uploading components, downloading components and search for software components. Fig.1 Proposed system to develop software reuse repository Non Architectural Inputs The origin code is an omnipresent trustworthy origin of information that most approaches consider. Some of the approaches directly query the origin code applying regular expressions. However, most of them represent origin code using meta frame works. With the paradigm of the analysed software these Meta frame works cope. For instance, the language-independent meta frame works is used to reversal applied scientist object-oriented applications. Its conceptions include classes, methods, calls, or accesses. The additional fashion is the symbolic textual information. Some approaches apply the symbolic information available in the comments or in the method name calling as well as origin file name calling. Dynamic information is also used to identify features, or coactions. The physical organization of applications in footing of files and architectural information folders often brings out. Clustering Conventions Purely automated software architecture extraction techniques do not exist. Reverse engineers must still channelize the most automated approaches. Approaches in this area often combine concept, dominance, and bunch analysis Volume 2, Issue 6, June 2013 Page 474 International Journal of Application or Innovation in Engineering & Management (IJAIEM) Web Site: www.ijaiem.org Email: editor@ijaiem.org, editorijaiem@gmail.com Volume 2, Issue 6, June 2013 ISSN 2319 - 4847 techniques. Formal concept analysis is a branch of theory used to identify contrive patterns, features, or modules. Clustering algorithms identify groups of objects whose members are similar in some way. Software perspectives of applications they have been used to produce. To identify subsystems, cluster files applying designation conventions. Some approaches automatically partition software merchandises into cohesive clusters that are loosely interconnected. Clustering algorithms are also used to extract features from object interactions. In directed graph, a node D dominates a node N if all paths from a given root to N go through D. In software maintenance, dominance analysis identifies the related parts in an application. In the context of software architecture extraction, unifies cluster and dominance analysis techniques to merges architectural components in object-oriented systems. Component Clustering In this module there are two main methods of hierarchical clustering algorithm. First method is agglomerative approach, where we begin from the bottom where all the objects are and going up through merging of objects. We begin with each individual objects and merge the two closest objects. The process is iterated until all objects are aggregated into a single group. Second method is divisive approach, where we start with assumption that all objects are group into a single group and then we split the group into two recursively until each group consists of a single object. One possible way to perform is recursively or iteratively split by the largest distance. Step by step algorithm of agglomerative approach to compute hierarchical clustering is as follow. Convert object features to distance matrix. Software Components Outputs In this module a framework is present to appraise software visual images around key areas such as static representation, dynamic representation, perspectives, navigation, project back up, carrying out, and visualization. A good deal of approaches offer (architectural) perspectives or applyvisual images as end product. Tools are present to be used to envision graph representations of software perspectives. Classifying the end products of the various visual images approaches is difficult. Visual image approaches present and group origin code entities as boxes applying the tools. Some tools focus on source code visual images or abstractions. These tools furnish developers with multiple, highdegree capital punishment architectural visualisations. To offer multiple perspectives of an application, it is interesting to combine static and dynamic analysis. Program explorer backups navigation of contrive pattern elements applying execution traces information. 4. RESULTS The concept of this paper is implemented and different results are presented in this section. The proposed work concepts show efficient results and has been efficiently tested on different Datasets. The figure 2 presents the comparisons of precision values of both key word and attribute classifications. Figure 3, 4, 5 and 6 shows the performance results and comparisons. Fig. 2 Precision of keyword and attribute classification schemes. Fig.3 Proposed system displaying component clustering. Volume 2, Issue 6, June 2013 Page 475 International Journal of Application or Innovation in Engineering & Management (IJAIEM) Web Site: www.ijaiem.org Email: editor@ijaiem.org, editorijaiem@gmail.com Volume 2, Issue 6, June 2013 ISSN 2319 - 4847 Fig.4 Proposed system displaying component clustering Fig. 5 Proposed system displaying component clustering Fig. 6 Proposed system displaying associations between classes 5. CONCLUSIONS In this paper a software reuse repository is developed by using data mining approach hierarchical clustering, and is evaluated for reusability prediction of object oriented software systems. In this metric based approach is used for prediction. Reusability value is expressed in the two linguistic values. Five input metrics are used as input and clusters are formed using hierarchical clustering. With these clusters performance of the system is recorded. As deduced from the results it is clear that precision value of the reusable class is the more than non-reusable class, it means the system is able to detect the reusable components precisely. Recall value of the non reusable class is the better than reusable class. Precision values of keyword and attribute classification schemes are compared for accuracy. The proposed technique is showing accuracy value satisfactory enough to use the hierarchical clustering based technique for the identification of the object based reusable modules from the existing reservoir of software components. REFERENCES [1] R. S. Pressman, Software Engineering: A Practitioner’s Approach, 5thedn. (McGraw-Hill, 2005). [2] Parvinder Singh Sandhu and Hardeep Singh, “Software Reusability Model for Procedure Based Domain-Specific Software Components”, International Journal of Software Engineering & Knowledge Engineering (IJSEKE), Vol. 18, No. 7, 2008, pp. 1–19. [3] Capers Jones, “Software Challenges: Economics of Software Reuse”, Computer, Vol.27, No.7, July 1994, pp.106107. [4] Parvinder Singh Sandhu and Hardeep Singh, "A Reusability Evaluation Model for OO-Based Software Components", International Journal of Computer Science, vol. 1, no. 4, 2006, pp. 259-264. [5] Frakes.W.B, Isoda.S, “Success Factors of Systematic Software Reuse”, IEEE, Vol.12, Issue:1, September 1994, pp.15-19. [6] Martin-Bautista, M.J.et.al. “An Approach to An Adaptive Information Retrieval Agent using Genetic Algorithms with Fuzzy Set Genes”, In Proceeding of the Sixth International Conference on Fuzzy Systems, New York, IEEE Press, 1997, pp.1227-1232. Volume 2, Issue 6, June 2013 Page 476 International Journal of Application or Innovation in Engineering & Management (IJAIEM) Web Site: www.ijaiem.org Email: editor@ijaiem.org, editorijaiem@gmail.com Volume 2, Issue 6, June 2013 ISSN 2319 - 4847 [7] Navneet Kaur, Jaspreet Singh Budwayl, “Hybrid Approach to Retrieval of Reusable Component from a Repository Using Genetic Algorithm and Ant Colony”, International Conference on Genetic and Evolutionary Methods, 2008, pp.147-152. [8] Parvinder S. Sandhu and Hardeep Singh, “A Neuro-Fuzzy Based Software Reusability Evaluation System with Optimized Rule Selection”, IEEE 2nd International Conference on Emerging Technologies (IEEE ICET 2006), Peshawar, Pakistan, Nov. 13-14, 2006, pp. 664-669. [9] Prieto-Diaz.R, Freeman.P. “Classifying Software for Reusability”, IEEE Software, Vol.4, Issue:1, January 1987, pp.06-16. [10] Mukhopadhyay Debajyoti, RanbirSingh Sanasam, “An Algorithm for Automatic Web-Page Clustering using Link Structures”, IEEE INDICON Proceedings, IIT Kharagpur, India, 20-22 December 2004, pp.472-477. [11] Parvinder S. Sandhu, PavelBlecharz and Hardeep Singh, “A Taguchi Approach to Investigate Impact of Factors for Reusability of Software Components”, Transactions on Engineering, Computing and Technology, vol. 19, Jan. 2007, ISSN 1305-5313, pp. 135-140. [12] McClure.C, “Software Reuse: A Standards-Based Guide”, Wiley-IEEE Computer Society Press, June 2001. [13] Rym.Mili, Ali.Mili, Roland.T.Mittermeir, “Storing and Retrieving Software Components: A Refinement Based System”, IEEE Transactions on Software Engineering, Vol. 23, Issue: 7, pp. 445-460, July 1997. [14] Xie Binhong, Ren Yaopeng, Zhang Yingjun, Chen Lichao, “Research on the Clustering Algorithm of Component Based on the Grade Strategy”, International Conference on Computer Application and System Modeling, (ICCASM), E-ISBN: 978-1-4244-7237-6, Vol. 6, pp. 500-503, IEEE 20l0. [15] Vitharana.P, Zahedi.F.M., Jain.H., “Knowledge Based Repository Scheme for Storing and Retrieving Business Components: A Theoretical Design and an Empirical Analysis”, IEEE Transactions on Software Engineering, Vol. 29, Issue: 7, pp. 649-664, July 2003. Volume 2, Issue 6, June 2013 Page 477