10 CYBER SECURITY GUIDELINES
advertisement
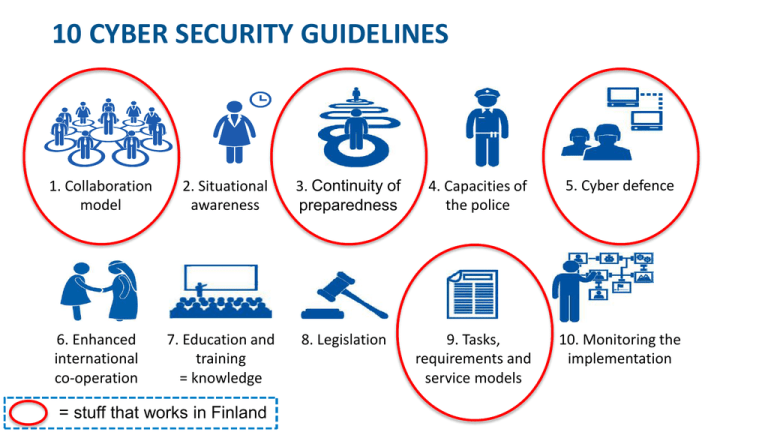
10 CYBER SECURITY GUIDELINES 1. Collaboration model 2. Situational awareness 3. Continuity of preparedness 4. Capacities of the police 5. Cyber defence 6. Enhanced international co-operation 7. Education and training = knowledge 8. Legislation 9. Tasks, requirements and service models 10. Monitoring the implementation = stuff that works in Finland HOW? CYBER DEFENSE CENTER INFORMATION SECURITY MANAGEMENT Public-Private-Partnership 30.5.2016 2 Security Operation Centers Telco SOC Telco TelcoSOC SOC ISP SOC ISP ISPSOC SOC Bank SOC Bank BankSOC SOC Government Ministry Ministry Ministry Agency Agency Agency Law enforcement Critical Infrastructure and Industry Situational Awareness Awareness Campaigns Early Warning Incident Management Reporting & Stats Vulnerability Management Authority Requests Incident Correlation PPP Threat Intelligence <S Energy <S <S <S Health Logistics <S Other Food CERT Collaboration A SOC ecosystem with operative capabilities to collaborate, observe attacks and help recovering. Always confidential, Ref. Finnish HAVARO. 08.0 voluntary for participants and very cost-effective. 3 https://www.viestintavirasto.fi/en/aboutthesector/reviewsandarticles/informationsecurity.html 8.20 PPP CRITICAL INFRASTRUCTURE AND INFORMATION PROCESSES Asset Mapping and Classification Data Privacy Risk Management Compliance Management INFORMATION SECURITY MANAGEMENT Business Continuity Security Awareness Business-driven Security & Privacy An Information Security Management System co-operative practice that is supported by a national body. NIXU CONFIDENTIAL 08.08.2015 4 Ref. Finnish HUOVI http://www.varmuudenvuoksi.fi/vuosikertomus-2013/huovi-portaali ONE-STOP SHOP FOR HIGH-END CYBER SECURITY CONSULTING Solutions for Industrial Internet Solutions for Digital Business Solutions for Corporate and IT Security Risk management Situational awareness Vulnerability management Compliance management Information security management Incident response & forensics Identity management Access management Application security Secure software lifecycle Secure development Infrastructure security Delivery models: 08.08.2015 NIXU CONFIDENTIAL Advisory assignment – Implementation project – Assessment – Continuous Service 5