Document 12927713
advertisement

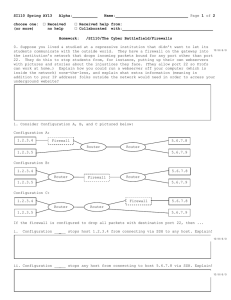
University of Babylon, IT College Information Network Dep., Third Class, Second Semester MTCNA Course MikroTik Certified Network Associate 2015-2016 By M.Sc. I.T Alaa A. Mahdi Firewall Objectives • Firewall principles; • structure; • chains and actions + LAB; • • Firewall Filter in action; • filter actions; • filter chains; • protecting your router (input) + LAB; • protection your customers (forward) + LAB; • RouterOS connection tracking; • impact on router; • connection state + LAB; Firewall principles • Firewall is a system or device that allows network traffic that is considered safe to flow through it and prevent an insecure network. Currently, the term firewall is a common term that refers to the system that regulates communication between two different networks. • The firewall implements packet filtering and thereby provides security functions that are used to manage data flow • to the router, • through the router, and • from the router. • Network firewalls keep outside threats away from sensitive data available inside the network. Whenever different networks are joined together, there is always a threat that someone from outside of your network will break into your LAN. Firewalls are used as a means of preventing or minimizing the security risks inherent in connecting to other networks. Properly configured firewall plays a key role in efficient and secure network infrastructure deployment. Chains • The firewall operates by means of firewall rules. Each rule consists of two parts – • The matcher which matches traffic flow against given conditions and • The action which defines what to do with the matched packet. • Firewall filtering rules are grouped together in chains. It allows a packet to be matched against one common criterion in one chain, and then passed over for processing against some other common criteria to another chain. Firewall Chains • • • • There are three defined chains: Input Forward Output • These three chains cannot be deleted. • Firewall rules are grouped together in chains. Each chain can be considered as a set of rules. • There are three default chains (input, forward, and output), which cannot be deleted. • More chains can be added for grouping together filtering rules. There are three predefined chains, which cannot be deleted: • input - used to process packets entering the router through one of the interfaces with the destination IP address which is one of the router's addresses. Packets passing through the router are not processed against the rules of the input chain • forward - used to process packets passing through the router. • output - used to process packets originated from the router and leaving it through one of the interfaces. Packets passing through the router are not processed against the rules of the output chain. • It is very advantageous, if packets can be matched against one common criterion in one chain, and then passed over for processing against some other common criteria to another chain. • For example, packets must be matched against the IP addresses and ports. Matching against the IP addresses can be done in one chain without specifying the protocol ports. Matching against the protocol ports can be done in a separate chain without specifying the IP addresses. The firewall rules are applied in the following order: • When a packet arrives at an interface, the NAT rules are applied first. The firewall rules of the input chain and routing are applied after the packet has passed the NAT rule set. This is important when setting up firewall rules, since the original packets might be already modified by the NAT. • If the packet should be forwarded through the router, the firewall rules of the forward chain are applied next. • When a packet leaves an interface, firewall rules of the output chain are applied first, then the NAT rules and queuing. • When processing a chain, rules are taken from the chain in the order they are listed there from the top to the bottom. If it matches the criteria of the rule, then the specified action is performed on the packet, and no more rules are processed in that chain. If the packet has not matched any rule within the chain, then the default policy action of the chain is performed. The available policy actions are: • accept - Accept the packet • deny - Silently drop the packet (without sending the ICMP reject message) • reject - Reject the packet and send an ICMP reject message Basic Firewall Setting • Assume we have router that connects a customer's network to the Internet. The basic firewall building principles can be grouped as follows: Protection of the Router from Unauthorized Access • Connections to the addresses assigned to the router itself should be monitored. Only access from certain hosts to certain TCP ports of the router should be allowed. • This can be done by putting rules in the input chain to match packets with the destination address of the router entering the router through all interfaces. Protection of the Customer's hosts • Connections to the addresses assigned to the customer's network should be monitored. Only access to certain hosts and services should be allowed. • This can be done by putting rules in the forward chain to match packets with the destination addresses of customer's network leaving the interface. Enforcing the Internet Usage Policy from the Customer's Network • Connections from the customer's network should be monitored. • This can be done by putting rules in the forward chain. Example of Firewall Filters Router protection • Lets say our private network is 192.168.0.0/24 and public (WAN) interface is ether1. • We will set up firewall to allow connections to router itself only from our local network and drop the rest. • Also we will allow ICMP protocol on any interface so that anyone can ping your router. Router protection Customer protection • To protect the customer's network, we should check all traffic which goes through router and block unwanted. For icmp, tcp, udp traffic we will create chains, where will be droped all unwanted packets: • /ip firewall filter add chain=forward protocol=tcp connection-state=invalid \ action=drop comment="drop invalid connections" • add chain=forward connection-state=established action=accept \ comment="allow already established connections" • add chain=forward connection-state=related action=accept \ comment="allow related connections" Example: To deny acces to the router via Telnet (protocol TCP, port 23) • /ip firewall filter add chain=input protocol=tcp dst-port=23 action=drop Protect your RouterOS router • / ip firewall filter • add chain=input connection-state=invalid action=drop \ comment="Drop Invalid connections" • add chain=input connection-state=established action=accept \ comment="Allow Established connections" • add chain=input protocol=udp action=accept \ comment="Allow UDP" • add chain=input protocol=icmp action=accept \ comment="Allow ICMP" • add chain=input src-address=192.168.0.0/24 action=accept \ comment="Allow access to router from known network" • add chain=input action=drop comment="Drop anything else" Protecting the Customer's Network (forward) • /ip firewall filter • add chain=forward protocol=tcp connectionstate=invalid \ action=drop comment="drop invalid connections" • add chain=forward connection-state=established action=accept \ comment="allow already established connections" • add chain=forward connection-state=related action=accept \ comment="allow related connections" Accept winbox • add chain=input protocol=tcp dst-port=8291 action=accept • add chain=input action=drop HW: • Reject Telnet to router? IP/Firewall/ Connection tracking • There are several ways to see what connections are making their way though the router. • In the Winbox Firewall window, you can switch to the Connections tab, to see current connections to/from/through your router. It looks like this: Connection tracking settings • enabled • Allows to disable or enable connection tracking. Disabling connection tracking will cause several firewall features to stop working. See the list of affected features. • For more info., see the PDF. HW: • What is Tarpit? Surf the internet!!!!