Flexible Throughput Management in IEEE 802.11e Wireless LANs
advertisement

Flexible Throughput Management in IEEE 802.11e
Wireless LANs
Shafiqul Karim1, David Green2, Michael Rumsewicz3, Nigel Bean4
1
School of Electrical & Electronic Engineering, 2,3,4School of Mathematical Sciences
University of Adelaide, SA 5005, Australia
{1shafiqul.karim, 2david.green, 3michael.rumsewicz, 4nigel.bean}@adelaide.edu.au
Abstract—The IEEE 802.11e standard has been developed to
provide quality of service (QoS) support to a wireless local area
network (WLAN). The framework for the standard is defined
such that the precise configuration details are left open to allow
a variety of possible implementations. Therefore the challenge
lies in implementing a configuration to provide specific QoS
requirements in a WLAN. In this paper, we propose a control
scheme to provide flexible, throughput management. This scheme
is evaluated using simulations and is shown to perform very well.
I. I NTRODUCTION
The IEEE 802.11 standard [1] is currently the most popular
and widely deployed technology for wireless broadband access
to wired local area network (LAN) services and the Internet.
The IEEE 802.11 standard is similar to Ethernet, in that
only best effort service is provided. Best effort service in
most cases, is sufficient for network traffic based on Internet
services such as web browsing, e-mail, file transfers and peer
to peer (P2P) applications. However, in recent times interest
in providing QoS in WLANs has grown with the introduction
of Voice over Internet Protocol (VoIP) services and other
interactive services such as real-time audio/video streaming
and online games.
In order to satisfy the additional traffic demands and
service requirements placed on WLANs, the IEEE 802.11
Work Group established two clear research directions. Task
Group N was established in order to improve the overall
throughput/bandwidth capabilities of WLANs. The primary
focus has been on developing novel physical layer (PHY) specifications to provide the necessary improvements. Task Group
E was created to take an alternative approach. Their focus
has been on introducing service differentiation mechanisms at
the MAC layer level and as a result it replaces the MAC layer
implementation defined in the IEEE 802.11 standard. The task
group E finalized the IEEE 802.11e standard midway through
2005 and was approved and published in late 2005 [2].
The IEEE 802.11e standard defines the Hybrid Coordination
Function (HCF) for determining access to the transmission
channel. HCF introduces two access mechanisms, the Enhanced Distributed Channel Access (EDCA) and the HCF
Controlled Channel Access (HCCA). The two access mechanisms are extensions to the Distributed Coordination Function
(DCF) and optional Point Coordination Function (PCF) access
1-4244-1230-7/07/$25.00 © 2007 IEEE
mechanisms defined in the IEEE 802.11 standard.
The IEEE 802.11e standard does not define a configuration
for EDCA or HCCA that achieves the QoS goals of providing
flexible, throughput management. As a result, in this paper
we propose a control scheme configuration within the EDCA
framework that achieves these QoS goals.
Our control scheme provides flexible throughput management. The control scheme can be easily configured and
implemented into the EDCA framework. The remainder of
this paper is organized as follows. The DCF and EDCA
mechanisms are briefly reviewed and discussed in Section II
and Section III. The specific throughput service goals and the
required network architecture used to achieve these goals is
described in Section IV. In Section V we describe in the
detail the proposed control scheme. The control scheme is
investigated via simulations and the results are discussed in
Section VI. Finally, we conclude our paper in Section VII.
II. IEEE 802.11 DCF
The DCF access mechanism is a carrier sense multiple
access with collision avoidance (CSMA/CA) and binary exponential back-off system. A station with a data frame ready
to transmit observes the activity of the transmission channel
for an idle period interval equal to a distributed inter-frame
space (DIFS). After observing an idle period equal to a DIFS,
a station is required to wait for a random back-off interval
before commencing transmission.
The back-off interval is represented as a number of integer
slots, a slot refers to a fixed duration of time and the total
number of slots in the interval is referred to as the back-off
counter. The back-off counter is decremented each time the
transmission channel is observed to be idle for a slot duration.
Whenever activity is detected on the transmission channel, the
decrementing process is suspended and the current back-off
counter value is retained. When the transmission channel is
subsequently observed to be idle again for a DIFS interval, the
process of decrementing the back-off counter resumes using
the previously retained value. A station is allowed to transmit
its data frame immediately after its back-off counter reaches
zero.
The number of slots in a back-off counter is randomly
selected from the range [0, CW-1], where CW is the current
295
ICON 2007
back-off contention window size. The CW used is within
a fixed range defined by CW min and CWmax . The first
transmission attempt for a frame made by a station uses a
CW value set to the minimum value defined by CW min . With
each unsuccessful frame transmission attempt, the CW value
is doubled until the maximum value CW max is reached. A
station will continue attempting to retransmit a frame until a
retransmission counter elapses causing the station to simply
drop the frame.
A successful transmission involves the receiver station acknowledging it has correctly received a data frame from the
transmitter station. The receiver station will transmit an acknowledgment (ACK) frame back to the transmitter station, after an interval equal to a short inter-frame space (SIFS) elapses
from receiving the data frame. If an ACK is not received within
an ACK timeout duration, the transmitter station assumes
the data frame was not received. The transmitter station will
simply reschedule the data frame for retransmission according
to the procedures described above.
DCF also uses beacon frame broadcasts at fixed intervals to
provide management services within a WLAN. Some of the
management services provided include, timing synchronization, broadcasting the network identifier, the network security
information and supported PHY transmission bit rates.
III. IEEE 802.11 E EDCA
EDCA implements four virtual DCF access mechanisms
within the MAC layer of a single station. The DCF access
mechanism is the primary access mechanism used in IEEE
802.11 based wireless networks.
The four virtual DCF entities are referred to as access
categories (ACs), each of which achieves a differentiated
level of access to the transmission channel. Differentiation
is achieved by varying the amount of time each AC must
sense the transmission channel being idle and the size of the
contention window (CW) it uses in the back-off process [2].
The classification terminology for each AC as defined in the
standard is shown in Table I.
SIF S: Short Inter-frame Space interval duration.
SlotT ime: Slot duration.
In order for service differentiation to exist for an arbitrary
AC i and AC j, where 0 ≤ i < j ≤ 3 (AC Priority), at least
one of the following inequalities must be strict, CW min [i] ≥
CW min [j], CW max [i] ≥ CW max [j] and AIFSN[i] ≥ AIFSN[j].
As a result AC j will have a better chance to access the
transmission channel than AC i.
If more than one AC queue in the one station finishes its
back off procedure at the same time, the higher priority AC
is given the right to transmit. While the lower priority AC
assumes a collision has occurred and reschedules a retransmission. This is described as a virtual collision within a station.
EDCA also introduces the idea of a transmission opportunity (TXOP). The TXOP is the maximum period of time a
station can hold the transmission channel while transmitting
frames. A station cannot initiate a frame transmission if the
time it would take to successfully transmit the frame exceeds
the prescribed TXOP duration. Each AC can be assigned a
specific TXOP-Limit.
EDCA extends the use of beacon frames in WLANs to
include broadcasting AC specific parameters. The EDCA
parameter set for each AC which is broadcast includes, the
AIFSN, CW min , CW max and TXOP-Limit. The beacon frame
structure used in the IEEE 802.11e EDCA standard defines
the range and allowable values that can be used for setting
AIFSN, CW min , CW max and TXOP-Limit for each AC. For
further information please refer to [2].
EDCA is able to introduce QoS into the MAC layer primarily through service differentiation. The four ACs are used
to classify higher layer traffic and allows each to receive a
differentiated level of service. The ability of beacon frames to
broadcast the EDCA parameter set allows it be dynamically
changed as required to achieve a desired result. Thus the
challenge lies in determining a specific configuration of the
EDCA mechanism that achieves the desired service result.
IV. S YSTEM A RCHITECTURE AND D ESIRED S ERVICE
G OALS
TABLE I
ACCESS C ATEGORIES
AC Priority
0
1
2
3
AC
AC BK
AC BE
AC VI
AC VO
AC Designation
Background
Best Effort
Video
Voice
Each AC is assigned an interval referred to as an arbitration
inter-frame space (AIFS) and a range for its CW value. The
AIFS value determines the period of time an AC must sense
the transmission channel being idle and the respective CW
value governs the back-off process used [2].
So, AC[i] (i = 0,1,2,3), has the following parameters defined,
AIFSN[i] to determine the AIFS[i] duration, initial contention
window size CW min [i] and a maximum allowable contention
window size CW max [i]. AIFS[i] is computed as
AIF S[i] = SIF S + (AIF SN [i] × SlotT ime),
(1)
In this paper our goal is to develop a specific configuration
to implement within the EDCA framework that provides
flexible, throughput management. We restrict our configuration
only to an infrastructure based WLAN.
An infrastructure based WLAN is chosen since an access
point (AP) is present in this form of network. The AP is a central device in the network with the responsibility for relaying
frame transmissions and broadcasting beacon frames. These
two characteristics are exploited in our proposed configuration.
The proposed configuration controls the network behaviour
to achieve a set of specified throughput proportions amongst
the ACs. In addition, the control can be configured to maximize the combined total throughput of all ACs, while maintaining the required throughput proportions.
The next section discusses our proposed configuration used
to achieve these goals.
296
V. P ROPOSED C ONTROL S CHEME C ONFIGURATION
The EDCA mechanism allows the parameter set for each
AC to be modified. Numerous papers [3], [4], [5], [6], [7],
[8], [9], [10], [11], [12], [13], [14] have developed methods for
analytically estimating the throughput performance and MAC
delay characteristics for each AC. These are determined as a
function of the EDCA parameter set information for each AC,
the number of active stations transmitting and the transmitted
frame sizes. A fundamental assumption in most of the methods
is that the network is operating under saturation load with each
active station always attempting to transmit a frame.
Clearly, the network performance for an AC can be dynamically altered through clever selection of the EDCA parameters
[15]. Extending this idea, we can overlay specific constraints
for the throughput performance of an AC under saturation load
through appropriate EDCA parameter settings.
We demonstrate the strength of our approach by manipulating only the CWmin value in order to achieve a specified
throughput proportion for each AC. We assume the AIFS
value used for each AC is the same and the TXOP-Limit is
set only to allow single frame transmissions. In this paper,
purely for simplicity, we limit the system to a two AC
configuration, however the theory described can easily be
extended to encompass a full four AC configuration system.
We arbitrarily select AC3 and AC2 as the two access
categories used in the system. The AIFS value for both ACs is
a DIFS interval and the CW min value is set according to our
control scheme in each beacon frame broadcast. This value is
then manipulated by the exponential back-off procedure under
a collision scenario up to the default DCF value of CWmax
= 1023. In the case of the control scheme selecting a CWmin
> 1023, we set CW max = CW min .
We achieve the desired throughput proportion for AC3 and
AC2 by appealing to the relationship shown in equation (2).
This is analogous to applying weighted-round-robin (WRR)
across the access categories.
3
[ CWnmin3
]
2
[ CWnmin2
]
≈
T hrpt3
AC3access
≈
.
AC2access
T hrpt2
(2)
n3 : total number of stations transmitting AC3 traffic.
n2 : total number of stations transmitting AC2 traffic.
CWmin3 : AC3 access category value for CWmin .
CWmin2 : AC2 access category value for CWmin .
AC3access : transmission access probability for AC3.
AC2access : transmission access probability for AC2.
T hrpt3 : throughput for AC3 access category.
T hrpt2 : throughput for AC2 access category.
to determine the required relationship between CWmin3 and
CWmin2 , which should achieve the desired throughput proportions for given values for n3 and n2 .
This principle applies elegantly to a homogeneous traffic
profile for AC3 and AC2. For a heterogeneous traffic profile
with different frame sizes for AC3 and AC2, the proportional
transmission access theory is still valid. However, the equation
for the throughput proportions must include additional factors
and constraints related to the frame sizes for AC3 and AC2.
This modification is a relatively simple extension to equation
(2), but purely for simplicity in this paper, we assume a
homogeneous traffic profile for AC3 and AC2.
We verified that equation (2) is valid using the analytical
method described in [13]. This particular analytical method is
selected since it is one of the more recent methods describing
the behavior of the EDCA mechanism.
We observed through the verification procedure that the
relationship in equation (2), breaks down when the values of
CWmin3 and CWmin2 used are relatively small in comparison
to the values for n3 and n2 . The collision probability for an
AC is directly related to the number of stations transmitting
and the contention window size used. Therefore, small values
for CWmin3 and CWmin2 cause the collision probability to
be significant enough to cause a degradation in throughput
for AC3 and AC2, thus leading to different throughput
proportions being obtained. Therefore equation (2) holds when
we assume the values for CWmin3 and CWmin2 selected are
large enough to cause AC3access , AC2access << 1, for the
given n3 and n2 .
Achieving the service goal described in Section IV is
relatively straightforward. The set of CWmin3 and CWmin2
that achieve the target throughput proportions for a given n3
and n2 according to equation (2) are analyzed more deeply
using the analytical method [13]. The appropriate CWmin3
and CWmin2 value can now be selected to also achieve the
secondary goal of maximizing the combined total throughput
for AC3 and AC2.
An important detail omitted in the above discussions, is
the restriction imposed on the allowable range and values for
CWmin and CWmax for each AC. Beacon frames transmit
the parameters defined as ECWmin and ECWmax which are
used to calculate the values for CWmin and CWmax [2] by
CWmin = 2ECWmin − 1,
(3)
CWmax = 2ECWmax − 1.
(4)
Note that ECWmin , ECWmax {0, 1, ...., 15}.
The simple intuition behind the relationship is that the
selected values for CWmin3 and CWmin2 , should distribute
the proportion of access to the transmission channel according
to the required throughput proportion, given n3 and n2 .
Effectively, the proportional access to the transmission channel
leads to a similar proportional throughput performance for
AC3 and AC2. As a result, equation (2) can be rearranged
To keep within the standard framework, we firstly determine
the required CWmin3 and CWmin2 independent of the restriction mentioned above. Once the values have been calculated,
we simply choose the best combination of the nearest allowable exponentially encoded CWmin3 and CWmin2 values.
The entire scheme relies on knowing a priori the correct
values for n3 and n2 , so how can we accurately observe the
values of n3 and n2 from the WLAN?
297
TABLE II
MAC AND PHY PARAMETERS FOR IEEE 802.11 B
The AP in a WLAN acts as a relay device for all frame
transmissions performed by client stations and we utilize this
useful property in our proposed control scheme to determine
the value for n3 and n2 . The control scheme monitors all
successfully relayed frame transmissions within a beacon
frame period. For each successfully relayed frame, the control
scheme catalogues the size of the frame, the AC label used
(either AC3 or AC2) and which client station invoked the
transmission. Thus the control scheme can easily identify the
number of transmitting stations in each AC per beacon frame
period.
We extend this process further by using a sliding window
approach over two consecutive beacon frame periods. The
control scheme then determines the number of transmitting
stations, which successfully transmitted data frames of type
AC3 or AC2 over the two beacon frame periods. This is used
as an estimate for the value of n3 and n2 in the WLAN. Using
the estimated value of n3 and n2 , the control scheme computes
the CWmin3 and CWmin2 that achieves the required service
goals. The next beacon frame following the observation period,
is updated by the control scheme with the computed CWmin3
and CWmin2 values and is broadcast to all the client stations.
To implement this control scheme into the EDCA mechanism is quite simple. We can make use of the existing ability
within the AP to observe transmissions and broadcast beacon
frames to update the CWmin and CWmax values. The control
scheme remains within the framework defined by the standard
and no changes are needed in the client stations. The next
section discusses the simulation results obtained using our
proposed control scheme configuration.
VI. P ERFORMANCE E VALUATION OF S IMULATION
R ESULTS
Parameter
SIFS
DIFS
SlotTime
AIFSN3
AIFSN2
PHY header
MAC header
ACK frame
FCS (frame checksum)
Data Rate
Control Rate
Standard EDCA Settings
CWmax3 proposed settings
CWmax2 proposed settings
Retry Limit
TXOP-Limit
Beacon frame Period
RT S/CT S Mode
Value
10 μs
50 μs
20 μs
2
2
192 bits
256 bits
112 bits
32 bits
11 Mbps
1 Mbps
CWmin3 = 7, CWmax3 = 15
CWmin2 = 15, CWmax2 = 31
max {1023, CWmin3 }
max {1023, CWmin2 }
7
0 (single frame transmissions only)
100 ms
OFF
TABLE III
N UMBER OF ACTIVE STATIONS OVER T IME
n3
2
5
3
7
10
6
1
6
1
1
n2
8
6
1
7
4
9
1
7
4
5
Time Duration (sec)
25 - 35
35 - 45
45 - 55
55 - 65
65 - 75
75 - 85
85 - 95
95 - 105
105 - 115
115 - 125
A. Test 1 - Standard EDCA Configuration
In this section, we investigate the simulation results obtained from our proposed control scheme. The simulation
tool used is N S-2 (version 2.29) [16], combined with the
EDCA implementation in N S-2 developed by the TKN group
in Technical University of Berlin [17]. We have modified
the EDCA implementation to include our proposed control
scheme. The MAC and Physical layer parameters used are
shown in Table II. The actual number of active stations n3 and
n2 are changed according to Table III within the simulation
period.
The simulation tests we perform are the following:
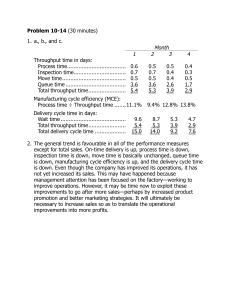
Figure 1 shows the simulation results when using the
standard EDCA configuration. The results show the value
obtained for the AC3 throughput proportion fluctuates as the
number of n3 and n2 change over the simulation period. When
the number of stations n2 is greater than n3 , the throughput
of the system begins to favor AC2 over AC3. As result the
standard EDCA configuration is unable to maintain a specific
level of throughput proportion for AC3 and AC2, as the
number of stations n3 and n2 change.
Test 1: Employ the standard EDCA configuration parameters for AC3 and AC2.
Test 2: Optimize the network to maximize the throughput
of AC3 and AC2, while maintaining the AC3 throughput
proportion at 80%, 67% and 50% respectively.
The overall throughput performance of the standard EDCA
configuration also varies when the number of stations n3 and
n2 change. In particular the overall throughput performance
reduces when the value for n3 and n2 are relatively large.
This is attributed to the small fixed values of CWmin and
CWmax used for AC3 and AC2, thus causing an increase in
the probability of collisions occurring.
We simulate the traffic for AC3 and AC2 using a UDP flow
with packets of size 1000 bytes. The throughputs (for AC3
and AC2) and the proportion of throughput that is from AC3
are measured over one and ten second intervals respectively.
Therefore the standard EDCA configuration is unable to
maintain a consistent overall throughput performance with
varying n3 and n2 and does not provide any means of controlling the throughput proportions achieved in the network.
•
•
298
B. Test 2 - Controlled Proportion under Maximizing Throughput Constraint
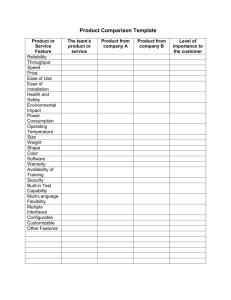
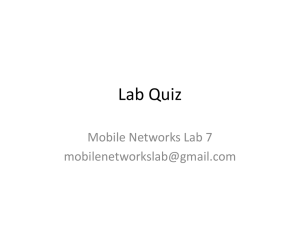
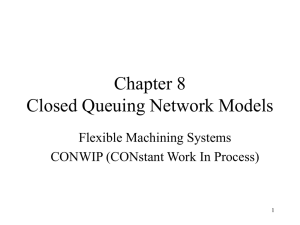
Figures 2 to 4, show the simulation results coincide relatively well with the target throughput proportions. The results
fit quite well to the analytic throughput values calculated from
[13].
However, at certain points in the simulation results, noticeable changes in the achieved throughput proportion occur. This
is attributed to the restriction placed on the allowable CWmin
values that can used. The required throughput proportions
can not be perfectly achieved due to the restrictions on the
allowable CWmin values.
Another observation for all the results is, at certain points
in the simulation period, there are noticeable spikes in the
throughput plots. The spikes coincide with events when a
change in the value for n3 and n2 is initiated.
The control scheme requires a period of time to estimate
the new set of values for n3 and n2 . Therefore, during this
period, the corresponding parameters calculated for the previous estimates of n3 and n2 are used. By applying equation
(2), the values for CWmin3 and CWmin2 remain unchanged
during this period, while the value of n3 and n2 has changed.
This causes the obtained throughput proportions to change
and leads to the visible spikes in the throughput plots. The
more prominent spikes occur when a significant change in the
values of n3 and n2 occurs from the previous interval. After
the control scheme determines the new estimate for n3 and
n2 , the network begins to operate again at the required level.
VII. C ONCLUSION
In this paper, we proposed a control scheme capable of providing flexible, throughput management. The control scheme
is described in detail and the implementation is studied and
verified through simulation. The results have demonstrated the
flexibility and effectiveness of the control scheme. In addition,
we have further enhanced the control to be able to limit the
total throughput to a target level, while maintaining the target
throughput proportions. We could not present this work in this
paper due to the space limitations.
As part of our current and future work, we plan to:
• investigate other techniques that can be used to improve
the estimate of the number of active client stations in
each AC.
• investigate how to allow an individual station to achieve
its own throughput requirements. This is of particular
importance since the base station is regarded as an
ordinary station in IEEE 802.11.
• include the use of additional modifiable parameters from
the EDCA parameter set.
•
investigate the possibility of providing client station based
guaranteed throughput using admission control.
ACKNOWLEDGMENT
The authors would like to thank the Australian Research
Council, and industry partner Tenix Australia, for funding this
research through Linkage Project LP0453508.
R EFERENCES
[1] IEEE, IEEE 802.11 Part 11: Wireless LAN Medium Access Control
(MAC) and Physical Layer (PHY) Specifications, 1999 (R2003).
[2] IEEE, IEEE 802.11 Part 11: Wireless LAN Medium Access Control
(MAC) and Physical Layer (PHY) Specifications, Amendment 8: Medium
Access Control (MAC) Quality of Service Enhancments, 2005.
[3] J. W. Robinson and T. S. Randhawa, “Saturation Throughput Analysis
of IEEE 802.11e Enhanced Distributed Coordination Function,” IEEE
J. Sel. Areas Commun., vol. 22, no. 5, pp. 917–928, Jun. 2004.
[4] Z. Kong, D. H. K. Tsang, and B. Bensaou, “Performance Analysis of
IEEE 802.11e Contention-Based Channel Access,” IEEE J. Sel. Areas
Commun., vol. 22, no. 10, pp. 2095–2106, Dec. 2004.
[5] J.-D. Kim and C.-K. Kim, “Performance analysis and evaluation of IEEE
802.11e EDCF,” Wirel. Commun. Mob. Comput., vol. 4, no. 1, pp. 55–
74, Feb. 2004.
[6] A. Banchs and L. Vollero, “A Delay Model for IEEE 802.11e EDCA,”
IEEE Commun. Letters., vol. 9, no. 6, pp. 508–510, Jun. 2005.
[7] Y. Xiao, “Performance Analysis of Priority Schemes for IEEE 802.11
and IEEE 802.11e Wireless LANs,” IEEE Trans. on Wirel. Commun.,
vol. 4, no. 4, pp. 1506–1515, Jul. 2005.
[8] P. E. Engelstad and O. N. Osterbo, “Delay and Throughput Analysis of
IEEE 802.11e EDCA with Starvation Prediction,” in Proc. IEEE Conf.
on Local Comp. Net., 2005, pp. 647–655.
[9] X. Chen, H. Zhai, and Y. Fang, “Enhancing the IEEE 802.11 in QoS
Support: Analysis and Mechanisms*,” in Proc. Qual. of Serv. in Hetro.
Wired/Wirel. Net., 2005, p. 23.
[10] H. Zhu and I. Chlamtac, “Performance Analysis for IEEE 802.11e EDCF
Service Differentiation,” IEEE Trans. on Wirel. Commun., vol. 4, no. 4,
pp. 1779–1788, Jul. 2005.
[11] J. Hui and M. Devetsikiotis, “A Unified Model for the Performance
Analysis of IEEE 802.11e EDCA,” IEEE Trans. on Commun., vol. 53,
no. 9, pp. 1498–1510, Sept. 2005.
[12] Z. Tao and S. Panwar, “Throughput and Delay Analysis for the IEEE
802.11e Enhanced Distributed Channel Access,” IEEE Trans. on Commun., vol. 54, no. 4, pp. 596–603, Apr. 2006.
[13] L. Xiong and G. Mao, “Saturated Throughput Analysis of IEEE 802.11e
Using Two-Dimensional Markov Chain Model,” in Proc. ACM int. conf.
on Qual. of Serv. in Hetro. Wired/Wirel. Net., vol. 191, no. 10, Aug. 2006.
[14] D. Xu, T. Sukurai, and H. L. Vu, “MAC access Delay in IEEE 802.11e
EDCA,” in Proc. IEEE Veh. Technol. Conf., Sept. 2006, pp. 1–5.
[15] S. Karim, N. Bean, D. Green, and M. Rumsewicz, “Adaptive Throughput
Management and Quality of Service Provisioning in IEEE 802.11e,” in
Proc. ITC Spec. Semin. on Teletraf. Eng. Chal. for Next Gen. Mob. Net.,
May. 2006.
[16] “The
Network
Simulator
ns-2.”
[Online].
Available:
http://www.isi.edu/nsnam/ns/
[17] S. Wietholter and C. Hoene, “An IEEE 802.11e EDCA
and CFB Simulation Model for ns-2.” [Online]. Available:
http://www.tkn.tu-berlin.de/research/802.11e_ns2/
Other avenues for further investigation include:
• investigate the impact of the control scheme in a WLAN
with unsaturated load.
• employ additional optimization constraints for MAC delay along with existing throughput constraints.
299
6
x 10
6
x 10
Simulated AC3 Throughput Proportion
Simulated AC3 Throughput Proportion
Required AC3 Throughput Proportion
80
100
80
60
Simulated AC3 Throughput
Simulated AC2 Throughput
Simulated Total Throughput
0
5
4
3
7
6
0
4
3
2
1
1
30
40
50
60
70
80
90
100
110
0
120
30
40
50
60
Fig. 1. Standard EDCA configuration. AC3 Throughput Proportion results
shown in the upper half of the graph using the right y − axis and common
x − axis. Throughput results shown in the lower half of the graph, using the
left y −axis and common x−axis. Legends for AC3 Throughput Proportion
and Simulated Throughput results shown in the upper-right and the center-left
position respectively. Simulated Throughput results shown from top to bottom
are Total Throughput, AC3 Throughput and AC2 Throughput.
110
120
80
60
60
20
0
4
3
40
6
0
4
3
1
1
60
70
80
90
100
110
20
5
2
50
Simulated AC3 Throughput
Simulated AC2 Throughput
Simulated Total Throughput
Model AC3 Throughput
Model AC2 Throughput
Model Total Throughput
7
2
40
100
80
40
5
Simulated AC3 Throughput Proportion
Required AC3 Throughput Proportion
Throughput (bits/sec)
Throughput (bits/sec)
100
x 10
100
AC3 Throughput Proportion (Percentage)
Simulated AC3 Throughput
Simulated AC2 Throughput
Simulated Total Throughput
Model AC3 Throughput
Model AC2 Throughput
Model Total Throughput
30
90
6
Simulated AC3 Throughput Proportion
Required AC3 Throughput Proportion
0
80
Fig. 3. Maximizing Throughput while maintaining an AC3 throughput proportion of 67%. Throughput results shown below are Simulated Throughput
overlapped against Model results. Graph to be interpreted as described in Fig.
1.
6
x 10
6
70
Time (seconds)
Time (seconds)
7
20
5
2
0
40
0
120
Time (seconds)
30
40
50
60
70
80
90
100
110
AC3 Throughput Proportion (Percentage)
6
Simulated AC3 Throughput
Simulated AC2 Throughput
Simulated Total Throughput
Model AC3 Throughput
Model AC2 Throughput
Model Total Throughput
AC3 Throughput Proportion (Percentage)
20
Throughput (bits/sec)
Throughput (bits/sec)
7
AC3 Throughput Proportion (Percentage)
60
40
120
Time (seconds)
Fig. 2. Maximizing Throughput while maintaining an AC3 throughput proportion of 80%. Throughput results shown below are Simulated Throughput
overlapped against Model results. Graph to be interpreted as described in Fig.
1.
Fig. 4. Maximizing Throughput while maintaining an AC3 throughput proportion of 50%. Throughput results shown below are Simulated Throughput
overlapped against Model results. Graph to be interpreted as described in Fig.
1.
300