Slotted Aloha in High Speed Bidirectional ... March, 1992 Research Supported By: LIDS-
advertisement

March, 1992
LIDS-
P 2097
Research Supported By:
DARPA contract N00014-84-K-0357
NSF contract ECS-7919880
ARO contract DAAL03-86-K-0171
Slotted Aloha in High Speed Bidirectional Bus Networks*
Lee, W.C.
Humblet, P.A.
March 1992
LIDS-P-2097
SLOTTED ALOHA IN HIGH SPEED BIDIRECTIONAL BUS NETWORKS
Whay Chiou Lee
Pierre
Codex Corporation
Mansfield, MIA
Humblet
Massachusetts Institute of Technology
Cambridge, MA
Abstract
We study the performance of the slotted ALOIH A
multiple access protocol in a high speed bidirectional
passive bus network, where transmissions are in the
form of packets of constant length. Slotted ALOHA
generally
considered to have better throughp i
generallyfcornsdere
to ALOHA,
have better
performance than unslottcd
whose throughput
maximum
throughput is known to be 1/(2e), independent of
station
We
station configuration.
configuration.
We show
show that,
that, with
with aa
probabilistic station configuration, the throughput of
~slotted
can
ALOHA to
slotted ALOHA
can~ de~rade~
degrade
to 11/(3e) when the end-toend propagation delay is significantly larger than the
packet
Nevertheless,
packet transmission
transmission time.
time.
Nevertheless, in
in some
some very
ver
high speed bidirectional bus networks with a
deterministic station configuration, the throughput
of slotted ALOHA can be as high as 1/2.
The speed of a bus network is often specified by the
parameter
a,
which
denotes
the
end-to-end
propagation delay normalized with respect to the
average packet transmission time.
With current
technology and cost trends, typical values of a in most
isting bus networks range between zero and one.
Advances
in
the
technology
of
optical
communications
and the inc reasing demand for
transmissions of relatively short packets promise
future bidirectional bus networks with normalized
end-to-end propagation delay exceeding one.
The fundamental limits of random access protocols
have been widely studied [61. It is common knoledge
that
in many contention-based
multiple access
p
protocols
with
carrier
sensing,
throughput
performance degrades with a because the overhead
for monitoring channel activities increases with a [7].
In our analysis of the slotted ALOHA protocol, we
assume that there is no carrier sensing.
Manv random access strategies for unidirectional bus
networks operating at high speeds have been studied
1
Introduction
by Maxemchuk, who shows that for unidirectional bus
networks, slotted protocols are always more eff.cicnt
than
Our analysis
that
The slotted ALOHA multiple access protocol has been
this isunslotted
not theprotocols
ease in[8].bidirectional
bus shows
networks.
studied by many
researchers.
For broadcast
this is not the case in bidirectional bus necworks.
studied by many
researchers.
For broadcast
With a probabilistic
station configuration, the
communications,
each
transmission
must
be
thn
ra
receivable by all stations, and the success of aslotted
LOH r can d
de lo
c)
when
the
end-to-end
propagation
is
transmission normally requires that there is no othern
the
pact
ta delor on
transmission within the same slot. The maximum
significantly larger than the packet trans m ssion
broadcast throughput for slotted ALOHA is well known
time, whereas the throughput of unslotcd
known to remain as 1/(2e).
to be l/e [1]. In practice, the slotted ALOHA protocol
may
actually
be
used
for
point-to-poin:
The effect of propagation delay on the stcadv state
communications.
Each transmission is designated for
behavior in the ALOHA systems has been inves:!ate d
only one station, and the success of a transmission
behavior in the ALOHo systems has been invpo:aion
depends on its being free of collision only where and
when
Due
when the
the rccctrion
reception is
is intcndcd.
intended.
Due to
to propagation
propagation
delay
in
bidirectional
bus
nc~tworlks,
pa-cktcs
transmitted within the same slot may overlap nondestructively.
When this occurs, we say that there is
channel reuse [2], [3].
In Figure 1. we make use of
space-time
diagrams
to
show
how
channel
reuse
is
possible in a high speed bidirectional bus network.
Space-time
have
diagrams
b
widel
~n used
used
~ inin the
the
Space-time diagrams
have
been
widely
literature for the analysis of multiple access protocols,
One would
throuh~ut
expect
performance
the former
because
of
bus
network
where (I+a) equals exactly
whre (I+a) equals sdacey
has been
They
showstudicd
tha?,
to have
channel
model, a slot has the same Icngth as the length of a
reuse, point-to-point transmissions are generally less
demanding
for channel
resources
than broadcast
better
bidirectional
Lto the
of stations [10],
on the[1I].
by
Levynumber
bus,
and Kleinrock
provided there is no carrier sensing, the maximum
prov
throughput of any slotted contention-based
multiple
access protocol in such a network approaches i,'e as
the number of stations becomes very large.
In their
model, a slot has the same
nth as the lenth
of a
in bus networks: e.g. [4], [5].
for channel
rebuse, point-o-soint transmissions Allowing
are generally
Icss
transmissions.
cd
may stabilize such systems [9].
In this pacer.
we
simplify the analysis of the slotted ALOHA prtocole
by
assuming that it is possible to achieve statistical
equilibrium.
reuse.
Such distincton is seldom emphasized in the
literature because
the difference is insignificant in
amost
conventional
useuhe
bidirectional
s incos
is n
aa
spd
of operation
operational is
bus networks whose
speed
of
isbidirectional
low.
packet transmission.
We study slotted ALOHA in the
same network, with the assumption that a slot lasts 'er
packet transmission time plus the end-o-cnd
propagation delay.
Our analysis indicates that, in such
mxum
a network, the maximum throughput of slotted ALOtIA
is at least 1/2.
2
Slotted
2
In this section, we review the slotted ALOHA protocol
in a bidirectional bus, of length D=l, which is assumed
to have perfectly non-reflecting terminations at both
Let there be N stations on the bus. Assuming
ends.
that all packet transmissions are of a constant length,
we show below the throughput performance of the
protocol under the conventional assumption that
there is no channel reuse.
In slotted ALOHA, time is divided into slots of length
(l+a) units of packet transmission time, and a packet
arriving at a station during a slot is transmitted at the
beginning of the following slot. The length of a slot
must be at least (l+a) units of packet transmission
time, or the end-stations cannot communicate with
Each transmitting station receives an
each other.
immediate error-free feedback about the success or
If a transmission
failure of- its transmitted packets.
fails, the packet is transmitted again in each
subsequent slot with some fixed non-zero probability,
We
independent of past slots and other packets.
summarize below the slotted ALOHA model used in this
paper.
Finite population of users;
Synchronous transmissions at discrete points
in time with period (l+a);
t Immediate feedback from receiver specifying
success or failure;
· Offered traffic including retransmissions is
approximately a memoryless random process;
* Symmetric traffic configuration;
* Statistical equilibrium.
·
·
Conventional analysis of the slotted ALOHA protocol
without channel reuse is based on the assumption of a
single receiver, so that a transmission in a given slot
is successful only if there are no other transmissions
Let G be the average offered
within the same slot.
traffic per slot, in packets per packet transmission
The offered traffic is assumed to be uniform
time.
each station is
By symmetry,
across all stations.
Thus,
active during a slot with probability (l+a)G/N.
the probability of success is
Pa(OG)
=
N-1 1
(NG
l- (I +a) Q
The throughput is then Sa(G) = G.Pa(G).
Sa(G) = G e
(1)
for aO0
-(I+a)G
For large N,
for a>0
-
-
ta)e
for a>0
(3)
point-to-point
maximum
the maximum
communications, the
point-to-point communications,
known to be
well
is
ALOHA
unslotted
of
throughput
of station
b
independent
all
aŽX0,
throl/(2hc)for
For
For
configuration.
maximum
Thus,
throughput
of
without
channel
slotted
ALOHA
reuse,
is
In any contention-based multiple access system,
If
every transmission is vulnerable to collisions.
then the
delay,
no propagation
were
there
vulnerability of a transmission may be characterized
by the time interval over which any other packet
During this time
transmitted could cause a collision.
interval, which is known as the vulnerable period,
the given transmission is vulnerable everywhere on
In a bidirectional bus network with
the bus.
propagation delay, the vulnerable periods do not
of
vulnerability
the
characterize
adequately
We need to consider vulnerable
transmissions.
regions in space and time, instead of vulnerable
A vulnerable region associated with a
periods.
transmission is the space-time region over which any
other packet arriving at the network could cause a
The size of the vulnerable regions is a
collision.
limiting factor on the performance of a contentionIn general, for a given protocol, the
based protocol.
larger the size of the vulnerable regions, the smaller
is the probability of success of each transmission.
The conventional vulnerable region for broadcast
communications in unslotted ALOHA is shown in
The length of this vulnerable region is
Figure 2(a).
The
2(1+a) units of packet transmission time.
vulnerable region for unslotted ALOHA with point-toNote
point communications is shown in Figure 2(b).
that the space-time area of this vulnerable region is
always equal to 2, regardless of the value of a.
In slotted ALOHA, the vulnerable region for a
transmission in a given slot lies in the previous slot.
For broadcast communications, the entire previous
slot is normally taken to be the vulnerable region.
Since the length of a slot is (1+a) units of packet
transmission time, the vulnerable regions increase in
size with increasing values of a. In this respect, the
broadcast throughput of the slotted ALOHA protocol
degrades as a increases, but with a factor of 2 more
slowly than that of unslottcd ALOHA.
Consider point-to-point transmissions for slotted
No simultaneous transmissions are possible if
ALOHA.
0< a 1, because every vulnerable region coincides
Hence, for point-to-point
with the entire slot.
communications, the maximum throughput of slotted
For a>i, the
ALOHA is given by (3) for 0<a <1.
smaller than
may be considerably
recions
vulnerable
as the slot
show tha
We will later show
a whole slot.
that as the slot
slot.whole We
a
1:1
will
later
length increases with a, the width of the vulnerable
Since
regions decreases in inverse proportion to a.
the size of the
the length of the slot is (l+a),
vulnerable regions tends to a non-zero constant with
In this respect, the throughput of
increasing a.
slotted ALOHA does not degrade indcfinitely as a
becomes very large.
(2)
whose maximum with respect to G is
Sa* = (
Regions
Vulnerable
3
ALOHA
the
indeed
greater than that of unslotted ALOHA, only forIn
Note that tnhe maximum throughput of slotted
AL
OHA
1.
ALOHA also vanishes as a becomes very large.e
In
Figures
and
3(a)
3(b),
we
show
how
two
transmitted packets may collide
simultaneously
We call the Vdestructively in the same time slot.
shaped
space-time
region Covered by
a transmission a
In the first case, the packets
respective transmission regions
the other case. the
transmission regions overlap side-by-side each other.
separatciy.
cases spratciy.
two cases
these to
examine these
We examine
transmission region.
collide with their
3
In the first case, two transmission regions cross each
other, and there is a potentially destructive collision.
The collision is non-destructive if neither
designated receivers is located within
interval where the transmission regions
other. This spatial interval is (I/a)' units
Bounds
4
Throughput
Maximum
on
of the two
the spatial
cross each
long, where
we evaluate the throughput
In this section,
performance of slotted ALOHA in bidirectional passive
in the form of
bus networks, where transmissions are
We will consider two
packets of constant length.
In the probabilistic
kinds of station configurations.
each station, except for the endconfiguration,
at a uniformly
stations, is independently located
independently located at a uniforly
is
transmissiontions,
other
no
which
in
interval
spatial
The
In the deterministic
distributed point on the bus.
potentially
a
causing
without
originate
may
of the stations on the bus
positions
the
configuration,
vulnerable
potentially
a
called
destructive collision is
A special case of the deterk inistic
are fixed.
Note that this spatial interval does not exist
interval.
is the regular bus network, in which
configuration
falls
yE[O0,1,
station,
receiving
the
of
position
if the
spatial interval between any two adjacent stations
the
is a constant.
outside the following range.
W
Ya(X)
1
1
1
_(), +
2x+
2
a
2
[2(x .
1
1)nlr[0,1]
(5)
a
1]
is the position of the transmitting
where xE [ 0 ,
the potentially vulnerable
Ya(x),
Y
When
station.
wide. The width of the
units
(2/a)most
at
is
interval
potentially vulnerable interval is smaller than (2/a)For a>>l, such end
when it falls partially outside [0,1].
effects are negligible, and the length of Ya(x) is
Ya( x)-[x/2,(x+1)/2].
1/2 because
approximately
Suppose that y is uniformly distributed within the
interval (0,11. Then, one can show that the expected+a
width of the potentially vulnerable interval is at most
half of (2/a)-, with equality if end effects are ignored.
In the second case, two transmitting stations are
within (l/a)- units of distance from each other.
The spatial
There is a totally destructive collision.
interval, in which no other transmission may
without causing a totally destructive
originate
The
collision, is called a totally vulnerable interval.
width of this totally vulnerable interval is at most
It is smaller than (2/a)- when the totally
(2/a)-.
For
vulnerable interval falls partially outside [0,I].
a>>I, such end effects are negligible. Assuming that x
is uniformly distributed within the interval [0,1], one
can easily show that the expected width of the totally'
vulnerable interval is at most (2/a)-, with equality if
end effects are ignored.
In Figure 4, we show a typical transmission, and its
and totally vulnerable
corresponding potentially
regions, which arc respectively specified by the
The
potentially and totally vulnerable intervals.
throughput of slotted ALOHA depends on the size of
the union of the vulnerable intervals, which we call
The union of the
the vulnerable interval-set.
regions will be
vulnerable
totally
and
potentially
The larger the
referred to as the vulnerable union.
size of the vulnerable union, the smaller is the
maximum throughput of the protocol. As we show in
Theorem 1 below, the space-time area of the
vulnerable union for slotted ALOHA tends to a
constant between 2 and 3, as the value of a becomes
On the other hand, the space-time area of
very large.
the vulnerable region for unslotted ALOHA is always
more efficient
equal to 2. Hence, unslottcd ALOHA ispoint-to-point
ALOHAffor orpoint-to-point
unslotted
n
tha slotted
equal
ALOHA
than
communications in a very high speed bidirectional
bus network
Probabilistic
4.1
Station
Configuration
1
Th
Consider a bidirectional bus network with a
For large N, the
probabilistic station configuration.
maximum throughput of the slotted ALOHA is bounded
as follows.
_2 +
+
e
for a>0
-a Sa-
(6)
where
(7)
(*)+ = max(*,l)
Thus, for 0<a<l, the maximum throughput of slotted
For very large a, the
ALOHA is the same as in (3).
maximum throughput of slotted ALOHA is bounded
Note that the lower bound
between 1/(3e) and 1/(2e).
in (6) is at least 1/(4c) for all a20.
The above bounds are shown in Figure 5.
Proof of Theorem
I
Let Va(x,y) be the space-time area of the vulnerable
union associated with a transmission from a station
The
located at xE[,O] to a station located at y E0,l1.
probability of success is
1
I
Pa(G) = fdxfdy I - Va(x,y)
0
NN
By Jensen's Inequality, we have
Pa(G)
>
1-
v
dxd Va(xy)
Va(x,y)}
0
0Idxfdy
(9)
Let Va denote the expected value of Va(xv)
respect to x and y. Let VP and Vat rprcsen
with
th
area of the
expected value of the space-time of
that the the totally
and ro
vulnerable region
potentially
Zudis
vulnerable region respectively.
From the discussion
vulnerable region respectively.
in Section 3, we obtain the following bounds.
4
V
1
VaP < 2(l+a)
}
(().
follows that
(10)It
(10)
M
and
(lI+a)C(' }
Vat <
<
(1+a)
Since Va <min{(l+a),(VaP+Vat)}, it follows that
ia )
=
a
G2
= (l+a)
(Iia)
Va*
=Va*
< 1
{1- Va*
}
N
1(13)
For
The proof for the upper bound is rather simple.
0 < a < 1, there is no channel reuse, and the maximum
For
throughput of slotted ALOHA is the same as in (3).
The upper bound can also be
a 1>l,Sa* <S I *=1/(2e).
derived from the space-time area of the totally
vulnerable region.
Q.E.D.
In Lemma 2, we derive a lower bound on the maximum
throughput.
Lemma
2
The maximum throughput of slotted ALOHA in a
bidirectional bus network with a deterministic station
configuration satisfies the following bound.
{ ha(N)+1
Sa*
Station
Deterministic
(17)
Note that the above upper bound on Sa* is valid for
any slotted protocol without carrier sensing, and for
A family of the upper
any station configuration.
bounds on Sa* for various number of stations are
shown in Figure 6.
Maximizing with respect to G, we obtain the lower
bound on Sa*.
4.2
fora20
Since there are N stations, and M<N, we obtain the
upper bound on Sa*.
Q.E.D.
(
(12)
The throughput is then lower bounded as follows.
Sa(G) >
(16)
And, we have
(11)
Sa*-<i
3Va <
Va < (I+a) a
for a20
Configuration
We now consider a bidirectional bus network with a
For simplicity,
deterministic station configuration.
we restrict our discussion primarily to a regular bus
network of unit length, where the spatial interval
between each pair of adjacent stations is 1/(N-1).
e
for a20
(18)
is the maximum number of
where ha(N)•(N-1)
the vulnerable
stations which can be located within
transmission.
in
with
Proof of Lemma 2
The probability of success is lower bounded as follows.
In Lemma 1, we derive an upper bound on the
slotted
with
achievable
throughput
maximum
The upper bound is derived by
transmissions.
considering only the totally vulnerable regions.
for
fora0
1- (+a)
Pa(G)
(19)
(19)
Maximizing
The throughput is then Sa(G) = G.Pa(G).
Sa(G) with respect to G, we obtain, for a>0,
Lemma
1
Suppose that all packets arc of the same length.
For
transmissions which may begin only at discrete
points in time. with a regular interval of (I+a) units
of packet transmission time, Sa*, the maximum
throughput is upper bounded as follows.
Sa*
<
< 1
( -i)
for a>0
(
Sa*
(0)
ha( N
I
){ ha(N)-l
It is easy to verify that
{
h-
1
ha(N)
I
-forha(N)20
>
}ha(N)+21
(21)
(14)
Hence, we have
Proof of Lemma
1
Sa* >
For successful synchronous transmissions, no two
packets may originate from stations that are less than
Otherwise, there is a
D/a units of distance apart.
Let M be the maximum
totally destructive collision.
synchronous
of
successful
number
possible
transmissions on the bus. Then, we have
I
ha(N)+l
fora>0
(15)
I
for aŽ0
for
(22)
(
Q.E.D.
For 05 a<1, there is no channel reuse.
ha(N) = (N-l)
(M-l) aD < D
+a
for 0 <a
<
Hence,
I
(23)
5
For a>(N-I), no stations are sufficiently close to each
other to allow any simultaneous transmissions that
are totally destructive.
Moreover, there can be at
most one station located within the potentially
destructive interval of any transmission.
Hence,
ha(N) = 1
for a>(N-1)
(24)
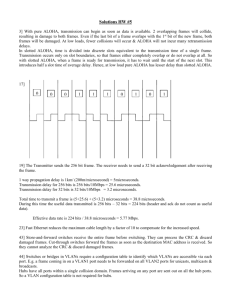
An example of such a very high speed bidirectional
bus network with N=8 stations is shown in Figure 7.
transmission, there are (N-l) potential receiving
points.
For each transmission, at least half of the
potential receiving points are not vulnerable to any
collision.
Any of the remaining receiving points will
suffer a destructive collision only if the one and only
one station within the corresponding potentially
vulnerable region is also transmitting a packet
during the slot.
By symmetry, each station is active
during a slot with probability (I+a)G/N.
Thus, the
probability of success is
In general, one can verify that
ha(N)
l
<
min ((N-l), fa(N)}
for a>0
I
12+2
Pa(G)
-( +a) N
for a2(N-1)
(30)
fora>(N-1)
(31)
(25)
It follows that
where
' +
N-l
fa(N)=
Theorem
*: N-
1
> 1- (I+a) 2}G
f~~~~~Sa(G)
(26)
lMaximizing with respect to GC,we obtain
Sa*
2
>
I(N
In a bidirectional regular bus network with N
stations, the maximum throughput of slotted ALOHA is
bounded as follows.
For 0<a<(N-1)),
wa(N)
-if--
e
<
S_ * <1
Sa*1
(27)
where
N(N) ( > 1
wa(N)= ha(N)+1
(28)
represents the gain of maximum throughput over
that of slotted ALOHA without channel reuse. A graph
of wa(N)/N versus a/(N-1) is shown in Figure 8.
fora>(N-I)
fora+(N-l)
(3")
(3)
Q.E.D.
When the stations are not regularly spaced, the
maximum throughput for a>(N-1) may be even
higher because a smaller fraction of the potential
In
receiving points are vulnerable to collisions.
Figure 9, we show a network, in which the fraction of
potentially destructive collisions is small.
It is
obvious
from the
figure
that the maximum
throughput for slotted ALOHA in this network is very
close to the upper bound in (29).
It is natural to
wonder, for a given number of stations on the bus,
which station configuration offers the maximum
throughput.
We leave this open question for further
research.
For a>(N-1).
S
2(+a)
<
Sa
I
<) I
(29)
Nuote that the lowcr bound on Sa* for aŽ(N-1) can Soe
as large as 1/2. This is the case when a = (N-l).
Proof of Theorem
2
The upper bounds in both cases follow from Lemma 1.
The lower bound in (27), which is actually valid for
all a20, follows from Lemma 2. For 0<a< 1, wa(N)= 1.
For I <a <(N-1). wa(N) increases monotonically with
a. For a>(N-1), wa(N) = N/2. For a>(N-1), we prefer
the tighter lower bound in (29).
This bound is
derived by taking into consideration the absence of
the
potentially
destructive
regions
for some
transmissions.
The lower bound for a>(N-1) is derived as follows.
For large a, many stations fall outside the vulnerable
intcrval-set.
In the network of interest, a
transmission can result in a destructive collision only
if it is ovcrlapcd by another transmission at the
For each
receiving poin: in space and time.
Conclusion
Channel reuse is part and parcel of many contentionbased multiple access protocols.
In this paper, we
have evaluated the throughput performance of slotted
ALOHA in a bidirectional bus network by giving
special attention to the protocol's inherent channel
reuse characteristics.
We
have shown that
conventional
analysis
often
overestimates
the
maximum broadcast throughput by neglecting the
effect of propagation delay, and underestimates the
by
not
point-to-point
throughput
maximum
considering channel reuse.
While the maximum
broadcast throughput vanishes with increasing a, the
maximum point-to-point throughput degrades rather
gracefully with a.
For a bidirectional bus network
the
with a probabilistic
station configuration,
maximum point-to-point throughput is no less than
For a
1/(4c), regardless of the speed of operation.
bidirectional bus nctwrok with a deterministic station
maximum
point-to-point
configuration,
the
with conventional
throughput is underestimated
analysis by at least a factor of wa(N)> 1. In addition. if
the stations are sparsely located along the bus, the
maximum point-to-point throughput may exceed the
classic limit of l/e when a>(N-l).
6
i
Acknowledgement
This research was conducted at the Laboratory for
Information and Decision Systems at MIT, under
contracts with the Defense Advanced Research
Projects Agency (N00014-84-K-0357), the National
Science Foundation (NSF-ECS-7919880), and the Army
Research Office (ARO-DAAL03-86-K-0171).
The
support is greatly appreciated.
¶ % ,v
D=1----
5
D=-1 -
No
Channel
Reuse
time
References
[11 L.G. Roberts, "ALOHA Packet System with and
without Slots and Capture," Computer Communications
Review, Vol.5, No.2, April 1975.
[2] W. Lee, "Channel Reuse Multiple Access in
Bidirectional
Bus
Networks,"
doctoral
thesis,
Department of Electrical Engineering & Computer
Science, Massachusetts Institute of Technology,
February 1989.
[3] W. Lee & P. Humblct, "Channel Reuse Multiple
Access Protocol for Bidirectional Bus Networks," IEEE
ICC '90, Atlanta, Georgia, April 1990.
(a)
?%
.
Vulnerable Region
..for Broadcast
Communications I
Communications
ji
-
Vulnerable Region
for Point-to-Point
Communications
C
u
t
Unslotted
A A
[7] S.R. Sachs, "Alternative Local Area Network
Access Protocols," IEEE Communications Magazine,
Vol.26, No.3, March 1988.
[11] L. Kleinrock & H. Levy, "On the Behavior of a
Very Fast Bidirectional Bus Network," IEEE Trans. on
Communications, Vol.38, No.10, October 1990. (Also in
IEEE ICC '87, Seattle Washington, June 1987).
-a..
time
[6] R. Gallager, "A Perspective on Multiaccess
Channels," IEEE Trans. on Information Theory, Vol.IT31, No.2, March 1985.
[10] H.
Levy,
"Non-Uniform
Sturctures
and
Synchronization
Patterns
in
Shared-Channel
Communication Networks," doctoral dissertation, Dept.
of Computer Science, UCLA, August 1984.
¶?
!
5
a
[5] M.L. Molle, et.al., "Space-Time Models of
Asynchronous CSMA Protocols for Local Area
Networks," IEEE Journal on Selected Areas in
Communications, Vol.SAC-5, No.6, July 1987.
[9] Y. Onozato, ct.al., "Effect of Propagation Delays on
ALOHA Systems," Computer Networks and ISDN
Systems, Vol.12, 1986.
1
Figure
[4] Sohraby, et.al., "Why Analytical Models of
Ethernet-Like Local Networks are so Pessimistic," IEEE
GlobeCom '84, Atlanta, Georgia, November 1984.
[8] N.
Maxemchuk,
"Twelve Random
Access
Strategies for Fiber Optic Networks," IEEE Trans. on
Communications, Vol.36, No.8, August 1988.
(b)
Unslotted
ALOA
(a)
(b)
Figure
2
[i5
~
v
D=1
--4
D=1--------- - -,--I----Potentially
Destructive
ally
estructiveDestructive
Totally
Destructive
time
a
a
(a)
(b)
Figure
----
3
l
Y
7
4-------
D=1
DI
-
Vun-0.6
D
2':9
Potentially
Totally
Vulnerable
Region
D
4---
*
Region
Slotted
Slotted
~-0.4
>
Region
Rgio ...
,
JY .°
tVulnerable
<
-
^~~~
upper bound
le
lower bound
n
potentially destuctive collision
1/e0:.
/(3e)/
-1.0
1(4e)
l/0.0
,~o e)
1/(11
lm ireuse
-1.6
-.4O
upper bound
no
-1
04
0.2 '
o. o
0.4
02
0.1
0.4.
1/e
1.0
1.2
collision-frchannel
a/(N-1)
1
log(a)
Figure 8
Figure
5
T
log(maximum throughput)
1
=10
time
Y Y
D
-
--
N=1000
-2
Y
-4
i0.
I
1I-I9--
-3 -
potentially destructive collision
-4
Ocollsion-free4
log(a)
Figure
6
Figure
9
ot