Cyber Security in KOREA
advertisement

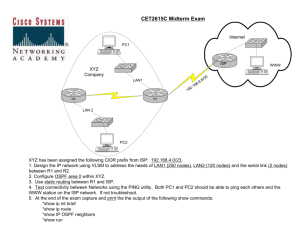
AVAR 2004, 25-26, Nov. 2004 Network Security in Korea Joongsup CHOI KISC/KrCERT Contents I. Positive Aspects of Internet II. Negative Aspects of Internet III. Big BANG, Triggering Point IV. KISC’s Role V. Hand-on Experience -2- I. Positive Aspects of Internet Network & Connectivity Src. : www.caida.org AS Path Length Graph `Yearly' Graph (1 Day Average) Max avg. length 5.0 Average avg. length 4.0 Max max. length 33.0 Average max. length 29.0 Src. : http://www.cymru.com/BGP/asnpalen01.html -3- Current avg. length 5.0 Current max. length 30.0 I. Positive Aspects of Internet Application Change Client/Server Type Pure Distributed Type Peer Server Peer Peer Peer Client Client Peer Client Peer Peer Src. : www.boardwatch.com -4- I. Positive Aspects of Internet Volume Size of Internet Items Internet Users % in Global ’00-’04 CAGR No. of IPv4 Broadband Users (K) Pop. (K) China Japan Korea World 87,000K 77,300K 30,000K 785,710K 10.1% 9.8% 3.7% Others: 76.4% 253.3% 37.1% 53.5% 118.9% 47,584K 112,587 K 31,504K 4,300M 17,700 13,150 11,500 N/A 1,327,976 127,944 47,136 6,453,311 Src.: www.internetstats.com & etc. -5- I. Positive Aspects of Internet Korea Internet Infrastructure Internet 70+ ISPs 11+ Million High Speed Internet 86,000+ Leased Line -6- I. Negative Aspects of Internet Worldwide Malicious Codes Yr. Worm Virus RAT 1991 16 1,000 15 1992 17 2,600 20 1993 17 4,000 21 1994 17 5,900 21 30,000 1995 18 8,000 23 20,000 1996 22 15,000 27 10,000 1997 24 16,500 104 1998 127 24,000 443 1999 165 30,000 1,679 2000 271 49,000 4,754 2001 1,102 60,000 9,742 2002 1,978 ? 13,085 2003 2,488 ? 14,432 -7- Worm Virus RAT 60,000 55,000 50,000 45,000 40,000 35,000 25,000 15,000 5,000 0 03 20 02 20 01 20 00 20 99 19 98 19 97 19 96 19 95 19 94 19 93 19 92 19 91 19 Src. : www.pestpetrol.com Mal. Code (Worm, Virus, Trojan/RAT) RAT: [Remote Administration Tool] is a Trojan that when run, provides an attacker with the capability of remotely controlling a machine via a "client" in the attacker's machine, and a "server" in the Victim's machine. II. Negative Aspects of Internet Vulnerability Points among Internet IOS/JuNOS Hijacking, Conf. Error KRNET ISP1 ISP2 Dial-Up D/UModem Peering ISP3 ISP ISP4 ISP5 ISP N B-O/F CPE BGP4 Foreign International Internet ISP …. …. Cable Modem Splitter GigaPOPCATV Head End Gateway CM DSLAM BIND DNS Mail Router SendMail DBMS SQL Web Mail L/L Video RP Web 2W HDSLRT 4W GigaPOP FTP Server Farm Home ONU GigaPOP ISP Network Home WLL Apache/ IIS -8- Explorer MS : Patch !! II. Negative Aspects of Internet Incidents depending on OS Windows Incidents are increasing now and malicious traffic are overwhelming …. Linux 11.3% Solaris 1.8% Linux 3.7% etc. 0.8% Windows NT/X P/2000 44.8% Windows 95/98 41.3% Solaris etc. 0.2% 0.1% Windows 95/98 33.5% Windows NT/X P/2000 62.6% 2003 2002 Src. : www.krcert.org -9- III. Big Bang - Triggering Point Slammer Worm (’03.1/25) Some Parts of Slammer Source Code PSEUDO_RAND_SEND: mov eax, [ebp-4Ch] lea ecx, [eax+eax*2] lea edx, [eax+ecx*4] shl edx, 4 add edx, eax shl edx, 8 sub edx, eax lea eax, [eax+edx*4] add eax, ebx mov [ebp-4Ch], eax [Worldwide Phenomena] Too fast to Response : Warhol Too many impacted Server Too wide-spread to co-ordinate Too many re-tries to connect → Most Effective WORM ! Src: www.internetpulse.net -10- III. Big Bang - Triggering Point Lessons from Slammer Worm Gov. :Law Enforcement & Sec. Awareness PR Agency : On-Line Surveillance System ISP : Network Security Investment & Enhancement Secure Internet Home: Up-to-date Patch Corp.: Security Awareness & CERT SW Vender : More Secure SW and Application -11- III. Big Bang - Triggering Point What Korean Government Have Done Law Enforcement : 2004. 1 .29, Rev. 2004.7.30 Security Inspection (ISP, IDC, Main Portal..) Information Sharing Obligation with KISC Emergency Response to Block Malicious Port # Launching KISC : 2003. 12. 17 24h X 7d Operation 5 min. Information Analysis (Traffic, port, incidents) Korea Internet Security Coordination (KrCERT/CC) Security Awareness : 2003 – 2004 Security Inspection for the SME ( Free of Charge ) Incidents Handling Manual for PC, ISP, IDC, Corp. Monthly Information Security Campaign -12- IV. KISC’s Role National Cyber-Security Framework Public Sector Gov. Agencies NIS SPPO Private Sector ISPs,AV, MSSP Incident Reports & Case Study Information Sharing Info. Sharing System Co-Work Technology & Information NPA Public Sectors : *NIS : National Information Service *SPPO : Supreme Public Prosecutors’ Office *NPA : National Police Agency Private Sectors : *ISP : KT, DACOM, Hanaro .. MSSP : Coconut.. AV : Ahnlab, Hauri -13- IV. KISC’s Role KISC’s Task and Job Flow Detect Major ISPs & MSSP Analysis Propagation ISP Hot Liners ISP/ESM Mail Remote Agent IDS/Firewall KISC FAX Private Sectors Vul. Foreign Ptn SMS Notice Mail Web. Home Users S/W,H/W Mess enger Analysis AV/Vaccine Detect KISC Recovery User -14- Propa gation Press & TV/Radio TRS IV. KISC’s Role KISC’s Today & Tomorrow OSS Unix/Linux Vul Ctr. For Ststem Vul. Net/ Vul Maker Sec. Info. Exchange Net/ Vul Foreign Organization BackUp Windows Vul. US, Jp.Cn CERT Nat’l Cyber Help Desk Patch Info. www.krcert.org Foreign Agency Global co-work APEC,Global VC HoneyNet VC 1 VC 2 IDC/SO/IDC Telecom ISAC Domestic Agency Virus/Attack Sample Bank/Stock ISAC Security ASP I S Ps Cororate. -15- Home Users Hacker/Intruder V. Hand-on Experience Phishing Scam Reported by : foreign CERTs or victim organizations, Response with ISPs Major Victim : US-Bank, City Bank, Bank of America, Brazilian Bank ITAU etc 35 35 No. of Incidents reported to KISC 30 25 24 20 22 15 10 5 0 6 5 2 Jan 2 Feb 0 Mar Apr May -16- Jun July Aug V. Hand-on Experience Anti-SPAM Activities Procedure : Reported by Users or ISP(Mail Service Providers) Countermeasure : On-site Inspection and Criminal Inspection with Prosecutors ⑥SPAM Users Mail Server Over Load DNS Server 과부하 Abettor ⑤ SPAMMing ④ Mail Server DNS Query ① Zombie Server ③ Lists Update , ② Malicious Code Instal Spammer Compromised PCs -17- V. Hand-on Experience Sec. Awareness and Support Security Awareness Activity 1). Security Education for : Security Divide Sector ( SME, PC Plaza, Users etc. ) 2). Publishing Cyber Security Manuals (Manual + CDs ) Individual User, Corporate Network Operator ISP, IDC, PC-Plaza Operator Encouraging to establish CERT Operation of CONCERT ( CONsortium of CERT : 228 in Korea ) On-Site Security Inspection for the SME ( ~ 2004 ) Target : 1,000 SME with Security Divide Sectors Inspection and Training ( Free of Charge ) -18- V. Q&A For any further information Please contact: Choi, Joongsup : jschoi@kisa.or.kr Thanks ! -19-