86788-top - Cisco Support Community
10.10.3.4
security
78.93.56.21
78.93.56.20
78.93.60.100
172.16.34.253
SYST
RPS
MASTR
STAT
DUPLX
SPEED
STACK
MODE
SYST
RPS
MASTR
STAT
DUPLX
SPEED
STACK
MODE
MODE
SYST
RPS
MASTR
STAT
DUPLX
SPEED
STACK
MODE
SYST
RPS
MASTR
STAT
DUPLX
SPEED
STACK
10.10.2.254
1X
1 2 3 4 5 6 7 8 9 10 11 12
11X
2X
1X
1
2
3
4
5
6
7
8
12X
9
10
11 12
11X
2X 12X
Catalyst 3750 SERIES
10 11 12
Catalyst 3750 SERIES
10 11 12
13X
13 14 15 16 17 18 19 20 21 22 23 24
23X
Catalyst 3750
SERIES
14X 24X
13X
13 14 15 16 17 18 19 20 21 22 23 24
23X
1
Catalyst 3750 SERIES
2
1 2
14X 24X
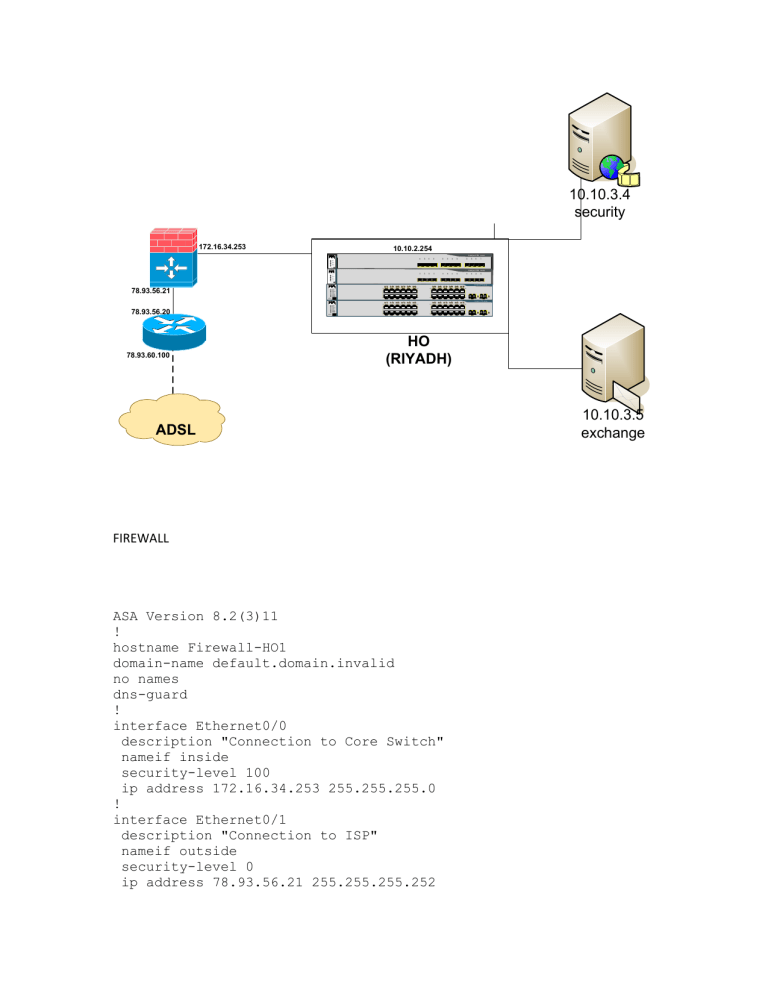
HO
(RIYADH)
ADSL
FIREWALL
ASA Version 8.2(3)11
! hostname Firewall-HO1 domain-name default.domain.invalid no names dns-guard
! interface Ethernet0/0
description "Connection to Core Switch"
nameif inside
security-level 100
ip address 172.16.34.253 255.255.255.0
! interface Ethernet0/1
description "Connection to ISP"
nameif outside
security-level 0
ip address 78.93.56.21 255.255.255.252
10.10.3.5
exchange
! interface Ethernet0/2
description "Connection to ISP backup SIM"
shutdown
nameif backup
security-level 0
ip address 172.16.33.253 255.255.255.0
! interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
! interface Management0/0
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0
management-only
! boot system disk0:/asa823-11-k8.bin ftp mode passive dns server-group DefaultDNS
domain-name default.domain.invalid access-list traffic_for_IPS remark IPS traffic redirection access-list traffic_for_IPS extended permit ip any any access-list 101 extended permit icmp any any echo-reply access-list 101 extended permit icmp any any source-quench access-list 101 extended permit icmp any any unreachable access-list 101 extended permit icmp any any time-exceeded access-list 101 remark Allow IP Camera Surveilance access-list 101 extended permit tcp any host 78.93.56.21 eq 50001 access-list 101 extended permit tcp any host 78.93.56.21 eq 50000 access-list 101 remark allow camera ports range access-list 101 extended permit tcp any host 78.93.56.21 eq 9014 access-list 101 extended permit tcp any host 78.93.56.21 eq 9013 access-list 101 extended permit tcp any host 78.93.56.21 eq 9012 access-list 101 extended permit tcp any host 78.93.56.21 eq 9011 access-list 101 extended permit tcp any host 78.93.56.21 eq 9010 access-list 101 extended permit tcp any host 78.93.56.21 eq 9009 access-list 101 extended permit tcp any host 78.93.56.21 eq 9008 access-list 101 extended permit tcp any host 78.93.56.21 eq 9007 access-list 101 extended permit tcp any host 78.93.56.21 eq 9006 access-list 101 extended permit tcp any host 78.93.56.21 eq 9005 access-list 101 extended permit tcp any host 78.93.56.21 eq 9004 access-list 101 extended permit tcp any host 78.93.56.21 eq 9003 access-list 101 extended permit tcp any host 78.93.56.21 eq 9002 access-list 101 extended permit tcp any host 78.93.56.21 eq 9001 access-list 101 extended permit tcp any host 78.93.56.21 gt 50001 access-list 101 extended permit tcp any host 78.93.56.21 eq 9015 access-list accounting extended permit icmp any any echo-reply access-list accounting extended permit icmp any any source-quench
access-list accounting extended permit icmp any any unreachable access-list accounting extended permit icmp any any time-exceeded access-list nonat extended permit ip 10.10.0.0 255.255.0.0
10.13.113.0 255.255.255.0 access-list nonat extended permit ip 10.10.0.0 255.255.0.0
10.13.213.0 255.255.255.0 access-list nonat extended permit ip 10.11.0.0 255.255.0.0
10.13.113.0 255.255.255.0 access-list nonat extended permit ip 10.11.0.0 255.255.0.0
10.13.213.0 255.255.255.0 access-list nonat extended permit ip 10.12.0.0 255.255.0.0
10.13.113.0 255.255.255.0 access-list nonat extended permit ip 10.12.0.0 255.255.0.0
10.13.213.0 255.255.255.0 access-list nonat extended permit ip 172.16.35.0 255.255.255.0
10.13.113.0 255.255.255.0 access-list nonat extended permit ip 172.16.35.0 255.255.255.0
10.13.213.0 255.255.255.0 access-list nonat remark ****** Link to AdslRouter ACL NONAT
****** access-list nonat extended permit ip 172.16.35.0 255.255.255.0
10.21.211.0 255.255.255.0 access-list nonat extended permit ip 172.16.35.0 255.255.255.0
10.21.111.0 255.255.255.0 access-list nonat extended permit ip 172.16.35.0 255.255.255.0
10.21.10.0 255.255.255.0 access-list nonat extended permit ip 10.10.0.0 255.255.255.0
10.21.211.0 255.255.255.0 access-list nonat extended permit ip 10.10.0.0 255.255.255.0
10.21.111.0 255.255.255.0 access-list nonat extended permit ip 10.10.0.0 255.255.255.0
10.21.10.0 255.255.255.0 access-list nonat extended permit ip 10.11.0.0 255.255.255.0
10.21.211.0 255.255.255.0 access-list nonat extended permit ip 10.11.0.0 255.255.255.0
10.21.111.0 255.255.255.0 access-list nonat extended permit ip 10.11.0.0 255.255.255.0
10.21.10.0 255.255.255.0 access-list nonat extended permit ip 10.12.0.0 255.255.255.0
10.21.211.0 255.255.255.0 access-list nonat extended permit ip 10.12.0.0 255.255.255.0
10.21.111.0 255.255.255.0 access-list nonat extended permit ip 10.12.0.0 255.255.255.0
10.21.10.0 255.255.255.0 access-list nonat extended permit ip 10.10.3.0 255.255.255.0
10.21.211.0 255.255.255.0 access-list nonat extended permit ip 10.10.3.0 255.255.255.0
10.21.111.0 255.255.255.0 access-list nonat extended permit ip 10.10.3.0 255.255.255.0
10.21.10.0 255.255.255.0 access-list nonat extended permit ip 10.10.0.0 255.255.0.0
10.21.211.0 255.255.255.0
access-list nonat extended permit ip 10.10.0.0 255.255.0.0
10.21.111.0 255.255.255.0 access-list nonat extended permit ip 10.10.0.0 255.255.0.0
10.21.10.0 255.255.255.0 access-list nonat extended permit ip 10.11.0.0 255.255.0.0
10.21.211.0 255.255.255.0 access-list nonat extended permit ip 10.11.0.0 255.255.0.0
10.21.111.0 255.255.255.0 access-list nonat extended permit ip 10.11.0.0 255.255.0.0
10.21.10.0 255.255.255.0 access-list nonat extended permit ip 10.12.0.0 255.255.0.0
10.21.211.0 255.255.255.0 access-list nonat extended permit ip 10.12.0.0 255.255.0.0
10.21.111.0 255.255.255.0 access-list nonat extended permit ip 10.12.0.0 255.255.0.0
10.21.10.0 255.255.255.0 access-list nonat remark "Site2Site VPN NONAT PALACE" access-list nonat extended permit ip 172.16.35.0 255.255.255.0
10.14.212.0 255.255.255.0 access-list nonat extended permit ip 172.16.35.0 255.255.255.0
10.14.112.0 255.255.255.0 access-list nonat extended permit ip 172.16.35.0 255.255.255.0
10.14.10.0 255.255.255.0 access-list nonat extended permit ip 10.10.0.0 255.255.255.0
10.14.212.0 255.255.255.0 access-list nonat extended permit ip 10.10.0.0 255.255.255.0
10.14.112.0 255.255.255.0 access-list nonat extended permit ip 10.10.0.0 255.255.255.0
10.14.10.0 255.255.255.0 access-list nonat extended permit ip 10.11.0.0 255.255.255.0
10.14.212.0 255.255.255.0 access-list nonat extended permit ip 10.11.0.0 255.255.255.0
10.14.112.0 255.255.255.0 access-list nonat extended permit ip 10.11.0.0 255.255.255.0
10.14.10.0 255.255.255.0 access-list nonat extended permit ip 10.12.0.0 255.255.255.0
10.14.212.0 255.255.255.0 access-list nonat extended permit ip 10.12.0.0 255.255.255.0
10.14.112.0 255.255.255.0 access-list nonat extended permit ip 10.12.0.0 255.255.255.0
10.14.10.0 255.255.255.0 access-list nonat extended permit ip 10.10.3.0 255.255.255.0
10.14.212.0 255.255.255.0 access-list nonat extended permit ip 10.10.3.0 255.255.255.0
10.14.112.0 255.255.255.0 access-list nonat extended permit ip 10.10.3.0 255.255.255.0
10.14.10.0 255.255.255.0 access-list nonat extended permit ip 10.10.0.0 255.255.0.0
10.14.212.0 255.255.255.0 access-list nonat extended permit ip 10.10.0.0 255.255.0.0
10.14.112.0 255.255.255.0
access-list nonat extended permit ip 10.10.0.0 255.255.0.0
10.14.10.0 255.255.255.0 access-list nonat extended permit ip 10.11.0.0 255.255.0.0
10.14.212.0 255.255.255.0 access-list nonat extended permit ip 10.11.0.0 255.255.0.0
10.14.112.0 255.255.255.0 access-list nonat extended permit ip 10.11.0.0 255.255.0.0
10.14.10.0 255.255.255.0 access-list nonat extended permit ip 10.12.0.0 255.255.0.0
10.14.212.0 255.255.255.0 access-list nonat extended permit ip 10.12.0.0 255.255.0.0
10.14.112.0 255.255.255.0 access-list nonat extended permit ip 10.12.0.0 255.255.0.0
10.14.10.0 255.255.255.0 access-list CENTSET extended permit ip 10.10.0.0 255.255.0.0
10.13.113.0 255.255.255.0 access-list CENTSET extended permit ip 10.10.0.0 255.255.0.0
10.13.213.0 255.255.255.0 access-list CENTSET extended permit ip 10.11.0.0 255.255.0.0
10.13.113.0 255.255.255.0 access-list CENTSET extended permit ip 10.11.0.0 255.255.0.0
10.13.213.0 255.255.255.0 access-list CENTSET extended permit ip 10.12.0.0 255.255.0.0
10.13.113.0 255.255.255.0 access-list CENTSET extended permit ip 10.12.0.0 255.255.0.0
10.13.213.0 255.255.255.0 access-list CENTSET extended permit ip 172.16.35.0 255.255.255.0
10.13.113.0 255.255.255.0 access-list CENTSET extended permit ip 172.16.35.0 255.255.255.0
10.13.213.0 255.255.255.0 access-list test extended permit ip host 10.10.3.10 host
10.21.10.253 access-list test extended permit ip host 10.21.10.253 host
10.10.3.10 access-list test extended permit ip any host 10.10.3.14 access-list test extended permit ip host 10.10.3.14 any access-list Jedmap remark ****** Link to AdslRouter ACC MAP
****** access-list Jedmap extended permit ip 172.16.35.0 255.255.255.0
10.21.211.0 255.255.255.0 access-list Jedmap extended permit ip 172.16.35.0 255.255.255.0
10.21.111.0 255.255.255.0 access-list Jedmap extended permit ip 172.16.35.0 255.255.255.0
10.21.10.0 255.255.255.0 access-list Jedmap extended permit ip 10.10.0.0 255.255.0.0
10.21.211.0 255.255.255.0 access-list Jedmap extended permit ip 10.10.0.0 255.255.0.0
10.21.111.0 255.255.255.0 access-list Jedmap extended permit ip 10.10.0.0 255.255.0.0
10.21.10.0 255.255.255.0 access-list Jedmap extended permit ip 10.11.0.0 255.255.0.0
10.21.211.0 255.255.255.0
access-list Jedmap extended permit ip 10.11.0.0 255.255.0.0
10.21.111.0 255.255.255.0 access-list Jedmap extended permit ip 10.11.0.0 255.255.0.0
10.21.10.0 255.255.255.0 access-list Jedmap extended permit ip 10.12.0.0 255.255.0.0
10.21.211.0 255.255.255.0 access-list Jedmap extended permit ip 10.12.0.0 255.255.0.0
10.21.111.0 255.255.255.0 access-list Jedmap extended permit ip 10.12.0.0 255.255.0.0
10.21.10.0 255.255.255.0 access-list Pmap remark ****** Link to Palace ADSL router****** access-list Pmap extended permit ip 172.16.35.0 255.255.255.0
10.14.212.0 255.255.255.0 access-list Pmap extended permit ip 172.16.35.0 255.255.255.0
10.14.112.0 255.255.255.0 access-list Pmap extended permit ip 172.16.35.0 255.255.255.0
10.14.10.0 255.255.255.0 access-list Pmap extended permit ip 10.10.0.0 255.255.0.0
10.14.212.0 255.255.255.0 access-list Pmap extended permit ip 10.10.0.0 255.255.0.0
10.14.112.0 255.255.255.0 access-list Pmap extended permit ip 10.10.0.0 255.255.0.0
10.14.10.0 255.255.255.0 access-list Pmap extended permit ip 10.11.0.0 255.255.0.0
10.14.212.0 255.255.255.0 access-list Pmap extended permit ip 10.11.0.0 255.255.0.0
10.14.112.0 255.255.255.0 access-list Pmap extended permit ip 10.11.0.0 255.255.0.0
10.14.10.0 255.255.255.0 access-list Pmap extended permit ip 10.12.0.0 255.255.0.0
10.14.212.0 255.255.255.0 access-list Pmap extended permit ip 10.12.0.0 255.255.0.0
10.14.112.0 255.255.255.0 access-list Pmap extended permit ip 10.12.0.0 255.255.0.0
10.14.10.0 255.255.255.0 access-list ved extended permit tcp any any eq 9003 access-list ved extended permit tcp any eq 9003 any access-list ved extended permit tcp any any eq 9006 access-list ved extended permit tcp any eq 9006 any access-list last_cap extended permit ip host 10.14.212.82 host
10.10.3.4 access-list last_cap extended permit ip host 10.10.3.4 host
10.14.212.82 access-list cisco extended permit ip host 10.10.3.4 host
10.14.212.62 access-list cisco extended permit ip host 10.14.212.62 host
10.10.3.4 pager lines 24 logging enable logging buffer-size 1048576 logging buffered debugging logging trap debugging
mtu inside 1500 mtu outside 1500 mtu backup 1500 mtu management 1500 icmp unreachable rate-limit 1 burst-size 1 asdm image disk0:/asdm-508.bin no asdm history enable arp timeout 14400 nat-control global (outside) 1 interface global (backup) 1 interface nat (inside) 0 access-list nonat nat (inside) 1 172.16.35.0 255.255.255.0 nat (inside) 1 172.16.40.0 255.255.255.0 nat (inside) 1 10.10.0.0 255.255.0.0 nat (inside) 1 10.11.0.0 255.255.0.0 nat (inside) 1 10.12.0.0 255.255.0.0 static (inside,outside) tcp interface 50000 10.10.3.4 50000 netmask 255.255.255.255 static (inside,outside) tcp interface 50001 10.10.3.4 50001 netmask 255.255.255.255 static (inside,outside) tcp interface 9001 10.10.3.22 9001 netmask 255.255.255.255 static (inside,outside) tcp interface 9002 10.10.3.23 9002 netmask 255.255.255.255 static (inside,outside) tcp interface 9003 10.10.3.20 9003 netmask 255.255.255.255 static (inside,outside) tcp interface 9004 10.10.3.16 9004 netmask 255.255.255.255 static (inside,outside) tcp interface 9005 10.10.3.15 9005 netmask 255.255.255.255 static (inside,outside) tcp interface 9006 10.10.3.14 9006 netmask 255.255.255.255 static (inside,outside) tcp interface 9007 10.10.3.19 9007 netmask 255.255.255.255 static (inside,outside) tcp interface 9008 10.10.3.17 9008 netmask 255.255.255.255 static (inside,outside) tcp interface 9009 10.10.3.21 9009 netmask 255.255.255.255 static (inside,outside) tcp interface 9010 10.10.3.13 9010 netmask 255.255.255.255 static (inside,outside) tcp interface 9011 10.10.3.11 9011 netmask 255.255.255.255 static (inside,outside) tcp interface 9012 10.10.3.18 9012 netmask 255.255.255.255 static (inside,outside) tcp interface 9013 10.10.3.12 9013 netmask 255.255.255.255 static (inside,outside) tcp interface 9014 10.10.3.24 9014 netmask 255.255.255.255 static (inside,outside) tcp interface 9015 10.10.3.25 9015 netmask 255.255.255.255
static (inside,outside) tcp interface 50002 10.10.3.4 50002 netmask 255.255.255.255 static (inside,outside) tcp interface 50030 10.10.3.4 50030 netmask 255.255.255.255 static (inside,outside) tcp interface 50040 10.10.3.4 50040 netmask 255.255.255.255 static (inside,outside) tcp interface 50050 10.10.3.4 50050 netmask 255.255.255.255 static (inside,outside) tcp interface 50060 10.10.3.4 50060 netmask 255.255.255.255 static (inside,outside) tcp interface 50070 10.10.3.4 50070 netmask 255.255.255.255 static (inside,outside) tcp interface 50080 10.10.3.4 50080 netmask 255.255.255.255 static (inside,outside) tcp interface 50090 10.10.3.4 50090 netmask 255.255.255.255 static (inside,outside) tcp interface 50110 10.10.3.4 50110 netmask 255.255.255.255 static (inside,outside) tcp interface 50120 10.10.3.4 50120 netmask 255.255.255.255 static (inside,outside) tcp interface 50130 10.10.3.4 50130 netmask 255.255.255.255 static (inside,outside) tcp interface 50140 10.10.3.4 50140 netmask 255.255.255.255 static (inside,outside) tcp interface 50150 10.10.3.4 50150 netmask 255.255.255.255 static (inside,outside) tcp interface 50160 10.10.3.4 50160 netmask 255.255.255.255 access-group 101 in interface outside route outside 0.0.0.0 0.0.0.0 78.93.56.20 1 route inside 10.10.0.0 255.255.0.0 172.16.34.254 1 route inside 10.11.0.0 255.255.0.0 172.16.34.254 1 route inside 10.12.0.0 255.255.0.0 172.16.34.254 1 route inside 172.16.35.0 255.255.255.0 172.16.34.254 1 route inside 172.16.40.0 255.255.255.0 172.16.34.254 1 timeout xlate 3:00:00 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sipdisconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute timeout tcp-proxy-reassembly 0:01:00 dynamic-access-policy-record DfltAccessPolicy aaa authentication ssh console LOCAL aaa authentication enable console LOCAL aaa authentication serial console LOCAL http server enable http 192.168.1.0 255.255.255.0 management http 0.0.0.0 0.0.0.0 inside snmp-server host inside 10.10.3.5 community alsayed no snmp-server location
no snmp-server contact snmp-server community alsayed snmp-server enable traps snmp authentication linkup linkdown coldstart snmp-server enable traps syslog snmp-server enable traps entity config-change fru-insert fruremove crypto ipsec transform-set CENTSET esp-des esp-md5-hmac crypto ipsec transform-set JSET esp-des esp-md5-hmac crypto ipsec transform-set Pset esp-des esp-md5-hmac crypto ipsec security-association lifetime seconds 28800 crypto ipsec security-association lifetime kilobytes 4608000 crypto ipsec df-bit clear-df outside crypto map CENTMAP 10 match address CENTSET crypto map CENTMAP 10 set pfs crypto map CENTMAP 10 set peer 78.93.244.114 crypto map CENTMAP 10 set transform-set CENTSET crypto map CENTMAP 20 match address Jedmap crypto map CENTMAP 20 set pfs crypto map CENTMAP 20 set peer 78.93.253.180 crypto map CENTMAP 20 set transform-set JSET crypto map CENTMAP 30 match address Pmap crypto map CENTMAP 30 set pfs crypto map CENTMAP 30 set peer 78.93.253.189 crypto map CENTMAP 30 set transform-set Pset crypto map CENTMAP interface outside crypto isakmp identity address crypto isakmp enable outside crypto isakmp policy 10
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400 crypto isakmp nat-traversal 33 telnet timeout 5 ssh 0.0.0.0 0.0.0.0 inside ssh 0.0.0.0 0.0.0.0 outside ssh timeout 60 console timeout 0 management-access inside dhcpd address 192.168.1.2-192.168.1.254 management dhcpd enable management
! threat-detection basic-threat threat-detection statistics access-list no threat-detection statistics tcp-intercept webvpn tunnel-group 78.93.244.114 type ipsec-l2l tunnel-group 78.93.244.114 ipsec-attributes
pre-shared-key cisco123
tunnel-group 78.93.239.122 type ipsec-l2l tunnel-group 78.93.239.122 ipsec-attributes
pre-shared-key cisco10293 tunnel-group 78.93.253.180 type ipsec-l2l tunnel-group 78.93.253.180 ipsec-attributes
pre-shared-key cisco10293 tunnel-group 78.93.253.189 type ipsec-l2l tunnel-group 78.93.253.189 ipsec-attributes
pre-shared-key cisco10293
! class-map IPS_class_map
match access-list traffic_for_IPS class-map inspection_default
match default-inspection-traffic
!
! policy-map type inspect dns migrated_dns_map_1
parameters
message-length maximum 512 policy-map global_policy
class inspection_default
inspect dns migrated_dns_map_1
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
! service-policy global_policy global prompt hostname context call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
Cryptochecksum:620d0fe61ddca98eb25eeff3ecfaec8c
: end
ROUTER
=~=~=~=~=~=~=~=~=~=~=~= PuTTY log 2011.05.23 10:29:28
=~=~=~=~=~=~=~=~=~=~=~= login as: admin
-----------------------------------------------------------------
------
Cisco Router and Security Device Manager (SDM) is installed on this device.
This feature requires the one-time use of the username "cisco" with the password "cisco". The default username and password have a privilege level of 15.
Please change these publicly known initial credentials using SDM or the IOS CLI.
Here are the Cisco IOS commands. username <myuser> privilege 15 secret 0 <mypassword> no username cisco
Replace <myuser> and <mypassword> with the username and password you want to use.
For more information about SDM please follow the instructions in the QUICK START
GUIDE for your router or go to http://www.cisco.com/go/sdm
-----------------------------------------------------------------
------
Using keyboard-interactive authentication.
Password:
Primary_Router_HO#sh run
Building configuration...
Current configuration : 6192 bytes
! version 12.4 no service pad service tcp-keepalives-in
service tcp-keepalives-out service timestamps debug datetime msec localtime show-timezone service timestamps log datetime msec localtime show-timezone service password-encryption service sequence-numbers
! hostname Primary_Router_HO
! boot-start-marker boot-end-marker
! logging buffered 51200 logging console critical
! no aaa new-model clock timezone PCTime 3
--More-- _________ _________! crypto pki trustpoint TP-self-signed-3747486160
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-3747486160
revocation-check none
rsakeypair TP-self-signed-3747486160
!
! crypto pki certificate chain TP-self-signed-3747486160
certificate self-signed 01
30820255 308201BE A0030201 02020101 300D0609 2A864886 F70D0101
04050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D
43657274
69666963 6174652D 33373437 34383631 3630301E 170D3039 31303239
31373031
32345A17 0D323030 31303130 30303030 305A3031 312F302D 06035504
03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D33
37343734
38363136 3030819F 300D0609 2A864886 F70D0101 01050003 818D0030
81890281
8100BDA4 095E9EDD 15CB2DC4 DF921343 20A982E4 1C46A0EC 00CCCE90
311F1903
4367EAE3 225F1C5A 6935D510 EFFCC079 771BE7F4 30B0EDA3 57B1969B
A364C4EE
D5142921 6F599FB9 AA4EFCCD 2BB6A1E4 AE56549F F45036E0 50CD612B
2115AC79
58F42F7F 81E1396E 49854C3D 4400C781 BD01C01C 2D9C073E 4ED20F93
97DA1A51
A84B0203 010001A3 7D307B30 0F060355 1D130101 FF040530 030101FF
30280603
551D1104 21301F82 1D507269 6D617279 5F526F75 7465725F 484F2E61
6C736179
65642E63 6F6D301F 0603551D 23041830 168014A2 5E1C938F 4399B6BF
C3EA4580
--More-- _________ _________ D998ED7D BBD43330 1D060355
1D0E0416 0414A25E 1C938F43 99B6BFC3 EA4580D9
98ED7DBB D433300D 06092A86 4886F70D 01010405 00038181 00808736
83D49C4E
CCEC47B2 3951B109 9AABA65E 622EA0FD C707167D C345D603 0211D727
683BD16A
93235C16 395E1756 3463E2D5 0C97FDFF E85AE314 4A6DAD42 68E102C0
9BBF16BA
D06800A1 5E099827 5473E197 45DBBC66 4DE60A75 22B04D20 C48BF237
487D83F4
3AB7E3AA 1B08563A 6E5FD869 323D8292 10D0A145 579317FC CA quit dot11 syslog no ip source-route
!
! ip cef
!
! no ip bootp server ip domain name alsayed.com
! multilink bundle-name authenticated
! vpdn enable
! vpdn-group pppoe
request-dialin
--More-- _________ _________ protocol pppoe
l2tp tunnel receive-window 1024
!
!
!
!
!
!
!
!
!
!
!
!
! voice-card 0
no dspfarm
!
!
!
!
!
!
--More-- _________ _________!
!
! archive
log config
hidekeys
!
! ip tcp synwait-time 10
! track 100 rtr 100 reachability
delay down 10 up 20
!
!
! bba-group pppoe global
virtual-template 2
!
! interface FastEthernet0/0
description "Connection to LAN"
--More-- _________ _________ ip address 78.93.56.20
255.255.255.252
no ip redirects
no ip unreachables
no ip proxy-arp
ip virtual-reassembly
ip route-cache flow
ip tcp adjust-mss 1452
duplex auto
speed auto
no cdp enable
no mop enabled
! interface FastEthernet0/1
description "Connection to ISP"
ip address 172.16.33.253 255.255.255.0
no ip redirects
no ip unreachables
no ip proxy-arp
ip nat outside
ip virtual-reassembly
ip route-cache flow
shutdown
duplex auto
--More-- _________ _________ speed auto
no mop enabled
! interface ATM0/0/0
no ip address
no ip redirects
no ip unreachables
no ip proxy-arp
ip route-cache flow
no atm ilmi-keepalive
dsl operating-mode auto
! interface ATM0/0/0.1 point-to-point
no ip redirects
no ip unreachables
no ip proxy-arp
pvc 0/35
encapsulation aal5snap
pppoe-client dial-pool-number 1
!
! interface Dialer0
ip address negotiated
--More-- _________ _________ no ip redirects
no ip unreachables
no ip proxy-arp
ip route-cache flow
no cdp enable
! interface Dialer1
mtu 1492
bandwidth 4096
ip address negotiated
no ip redirects
no ip unreachables
no ip proxy-arp
ip virtual-reassembly
encapsulation ppp
ip route-cache flow
dialer pool 1
dialer-group 1
no cdp enable
ppp authentication chap pap callin
ppp chap hostname xxxxxxxxxxxxx
ppp chap password 7 101F5C48554441
ppp pap sent-username xxxxxxxxxxxxx password 7 11584C54474158
--More-- _________ _________! ip forward-protocol nd ip route 0.0.0.0 0.0.0.0 Dialer1
!
! no ip http server ip http authentication local ip http secure-server ip http timeout-policy idle 60 life 86400 requests 10000 ip nat inside source list 1 interface Dialer1 overload
!
logging trap debugging access-list 1 permit 172.16.32.0 0.0.0.255 snmp-server community alsayed RO snmp-server community alsayedcisco RW snmp-server enable traps snmp authentication linkdown linkup coldstart warmstart snmp-server enable traps tty snmp-server enable traps flash insertion removal snmp-server enable traps envmon fan shutdown supply temperature status snmp-server enable traps config-copy snmp-server enable traps config snmp-server enable traps entity snmp-server enable traps fru-ctrl
--More-- _________ _________snmp-server enable traps hsrp snmp-server enable traps cpu threshold snmp-server enable traps ipsla snmp-server enable traps syslog snmp-server enable traps vtp no cdp run
!
!
!
!
!
!
!
!
!
!
!
! control-plane
!
!
! banner login ^C
--More-- _________ _________-----------------------------
------------------------------------------
Cisco Router and Security Device Manager (SDM) is installed on this device.
This feature requires the one-time use of the username "cisco" with the password "cisco". The default username and password have a privilege level of 15.
Please change these publicly known initial credentials using SDM or the IOS CLI.
Here are the Cisco IOS commands. username <myuser> privilege 15 secret 0 <mypassword> no username cisco
Replace <myuser> and <mypassword> with the username and password you want to use.
For more information about SDM please follow the instructions in the QUICK START
GUIDE for your router or go to http://www.cisco.com/go/sdm
-----------------------------------------------------------------
------
^C
! line con 0
--More-- _________ _________ login local line aux 0 line vty 0 4
privilege level 15
login local
transport input ssh line vty 5 15
privilege level 15
login local
transport input ssh
! scheduler allocate 20000 1000
! end
Primary_Router_HO#
Primary_Router_HO#
Primary_Router_HO#
Primary_Router_HO#