better_format - Cisco Support Community
advertisement

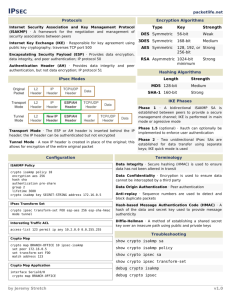
Good day, I have a problem connecting through the tunnel from my internal network. I can telnet from the router to the destination IP (70.70.70.70) and I can also ping the destination from the router. I can see the tunnel is up and the packets flow looks good. The client should only see traffic coming from the public interface IP 80.80.80.80.So all the other source IP's from within our network ( sources on access-list 105 below ) will be NAT'ed behind the interface IP. So I would like to know where I went wrong. Routing: Our internal network -> Our Firewall-> Router(80.80.80.80-Public IP)->TuNNEL-> Client's firewall (100.100.100.100) ----interface GigabitEthernet0/1 ip address 90.90.90.90 secondary ip address 80.80.80.80 255.255.255.248 ip flow ingress ip nat inside ip virtual-reassembly in duplex full speed auto no cdp enable crypto map CISCO ---------------- ROUTER ---------------crypto isakmp policy 20 encr 3des hash sha authentication pre-share group 2 lifetime 86400 crypto isakmp key ***** address 100.100.100.100 crypto ipsec transform-set CLIENT esp-3des esp-sha-hmac crypto map CISCO 20 ipsec-isakmp set peer 100.100.100.100 set security-association lifetime seconds 28800 set transform-set CLIENT set pfs group2 match address 100 ip route 70.70.70.70 255.255.255.255 100.100.100.100 name CLIENT-IPSec ip access-list extended 100 remark CLIENT permit ip host 80.80.80.80 host 70.70.70.70 ip nat inside source list 105 interface GigabitEthernet0/1 overload ip access-list extended 105 remark CLIENT permit ip 80.80.80.76 0.0.0.7 host 70.70.70.70 permit ip 192.168.0.0 0.0.255.255 host 70.70.70.70 permit ip 172.20.0.0 0.0.255.255 host 70.70.70.70 permit ip 172.21.0.0 0.0.255.255 host 70.70.70.70 interface GigabitEthernet0/1 crypto map CISCO