Designing VLANs in Networks
advertisement

Securing Layer 2 Access
Mitigating Layer 2 Attacks
Layer 2 Security Issues
Campus access devices and Layer 2 communication
are left largely unconsidered in most security
discussions, and there is lack of security at this layer.
Many security features are available for switches and
routers, but they must be enabled to be effective.
However, as with access control lists (ACL) for upperlayer security, a policy must be established and
appropriate features configured to protect against
potential malicious acts while maintaining daily
network operations.
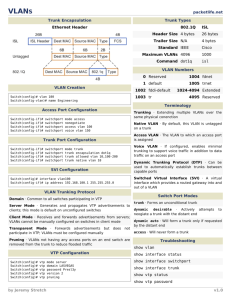
Security Infrastructure Services
Server Farm
Core
Distribution
Access
•Use private VLANs, IPS, logging and ACLs
•Do not perform security operations –
increases performance
•Use ACLs to provide security and filtering.
•Use switchport security to control access to
the network.
Layer 2 Malicious Attacks
Layer 2 malicious attacks are typically launched by
a device connected to the campus network. This
can be a physical rogue device placed on the
network or an external intrusion that takes control of
and launches attacks from a trusted device.
In either case, the network sees all traffic as
originating from a legitimate connected device.
The following lists the types of attacks launched
against switches and Layer 2:
1.
2.
3.
4.
MAC layer attacks (e.g. MAC address flooding).
VLAN attacks (e.g. VLAN hopping).
Spoof attacks (e.g. DHCP, MAC & ARP spoofing).
Switch device attacks (e.g. CDP manipulation,
Telnet attacks).
MAC Flood Attack
•To mitigate against MAC flooding, port security is configured to define the
number of MAC addresses that are allowed on a given port.
•Port security can also specify which MAC address is allowed on a given port.
Switch Configuration – Port Security
•To limit the number of addresses that can be learned on an
interface switches provide a feature called port security.
•The number of MAC addresses per port can be limited to 1.
•Secure addresses can be assigned statically or dynamically
learned by the switch.
S1(config)#interface fa0/1
S1(config-if)# switchport port-security ?
aging
mac-address
maximum
violation
Port-security aging commands
secure mac address
max secure addrs
security violation mode
Switch Configuration – Port
Security
Static secure MAC addresses: MAC addresses are
manually configured by using the switchport portsecurity mac-address interface configuration command.
MAC addresses configured in this way are stored in the
address table and are added to the running
configuration on the switch.
Dynamic secure MAC addresses: MAC addresses are
dynamically learned and stored only in the address
table. MAC addresses configured in this way are
removed when the switch restarts.
Sticky secure MAC addresses: You can configure a port
to dynamically learn MAC addresses and then save
these MAC addresses to the running configuration.
Port Security: Violation
Switch(config-if)#switchport port-security violation
{protect | restrict | shutdown}
By default, if the maximum number of connections is achieved and a new MAC
address attempts to access the port, the switch must take one of the following
actions:
Protect: Frames from the non-allowed address are dropped, but there is no log of
the violation. The protect argument is platform or version dependent.
Restrict: Frames from the non-allowed address are dropped, a log message is
created and Simple Network Management Protocol (SNMP) trap sent.
Shut down: If any frames are seen from a non-allowed address, the interface is
errdisabled, a log entry is made, SNMP trap sent and manual intervention (no
shutdown) or errdisable recovery must be used to make the interface usable. Port
LED is switched off.
Switch Configuration – Port Security
Server
DLS1
Fa0/1
PC1
Fa0/2
DLS1(config)# interface FastEthernet 0/1
DLS1(config-if)# switchport
DLS1(config-if)# switchport mode access
DLS1(config-if)# switchport port-security
DLS1(config-if)# switchport port-security mac-address 0000.0000.0008
DLS1(config-if)# switchport port-security maximum 1
DLS1(config-if)# switchport port-security aging static
DLS1(config-if)# switchport port-security violation restrict
DLS1(config-if)# switchport block unicast
DLS1(config)# interface FastEthernet 0/2
DLS1(config-if)# switchport
DLS1(config-if)# switchport mode access
DLS1(config-if)# switchport port-security
DLS1(config-if)# switchport port-security mac-address sticky
DLS1(config-if)# switchport port-security maximum 2
DLS1(config-if)# switchport port-security aging static
DLS1(config-if)# switchport port-security violation shutdown
Verify Port Security
DLS1# show running-config fastethernet 0/2
interface FastEthernet0/1
switchport access vlan 2
switchport mode access
switchport port-security maximum 2
switchport port-security
switchport port-security violation shutdown
switchport port-security mac-address sticky
switchport port-security mac-address sticky 001b.d513.2ad2
DLS1# show port-security address
Secure Mac Address Table
-----------------------------------------------------------------------Vlan
Mac Address
Type
Ports Remaining Age
(mins)
---2
----------001b.d513.2ad2
--SecureSticky
-----
------------Fa0/2
-
VLAN Hopping – Switch Spoofing
Attacker
Trunk
802.1q
Native VLAN 1
VLANS 10 & 20
Trunk
VLAN 20
S1
VLAN 10
802.1q
Native VLAN 1
VLAN 20
S2
VLAN 20
•In a switch spoofing attack, the network attacker configures a system to spoof
itself as a switch by performing Inter-Switch Link (ISL) or 802.1Q trunking,
along with DTP negotiations, to establish a trunk connection to the switch.
•By default, a trunk connection provides an attacker with access to all VLANs in
the network.
VLAN Hopping – Double Tagging
Data
VLAN20
VLAN 10
Data
VLAN10
Access
Port
Trunk
S1
802.1q
Native VLAN 10
Data
VLAN 10
S2
VLAN20
VLAN 10
VLAN 20
1.
Attacker sends a double-tagged broadcast packet into the local access-LAN.
2.
Switch 1 forwards this across the trunk, removing the first tag, as it matches
the native VLAN.
3.
Switch 2 receives the packet, and forwards it into VLAN 20.
Mitigating VLAN Hopping
Switch Spoofing:
Configure all unused ports as access ports so that
trunking cannot be negotiated across those links.
Place all unused ports in the shutdown state and
associate with a VLAN designated only for unused
ports, carrying
no user data traffic.
• Switch
Spoofing:
•Configure the native VLAN with an unused VLAN, which can then be
pruned off the trunk:
S1(conf)#vlan 800
S1(conf-vlan)# name bogus_native
S1(conf)#int fa0/1
S1(conf-if)#switchport trunk encap dot1q
S1(conf-if)#switchport trunk native vlan 800
S1(conf-if)#switchport trunk allowed vlan remove 800
S1(conf-if)# Switchport mode trunk
VLAN Access Control Lists
Router access control list (RACL): Applied to Layer 3 interfaces such
as SVI or L3 routed ports. It controls the access of routed traffic between
VLANs. RACLs are applied on interfaces for specific directions (inbound
or outbound). You can apply one access list in each direction.
Port access control list (PACL): Applied on a Layer 2 switch port, trunk
port, or EtherChannel port. PACLs perform access control on traffic
entering a Layer 2 interface. With PACLs, you can filter IP traffic by using
IP access lists and non-IP traffic by using MAC addresses. When you
apply a PACL to a trunk port, it filters traffic on all VLANs present on the
trunk port.
VLAN access control list (VACL): Supported in software on Cisco
multilayer switches. Filtering based on Layer 2 or Layer 3 parameters
within a VLAN. Unlike RACLs, VACLs are not defined by direction (input
or output).
VACL Configuration
Host 2
192.168.20.20/24
VLAN 20
DLS1
Computer
Computer
Server
192.168.10.10/24
VLAN 10
Host 1
192.168.10.20/24
VLAN 10
Deny all traffic from
VLAN 20 reaching the
VLAN 10 server
1.Create ACL to define traffic to block:
DLS1(config)#ip access-list extended DENY_SERVER
DLS1(conf-ext-nacl)#permit ip 192.168.20.0 0.0.0.255 host 192.168.10.10
2. Create VLAN map to block and forward traffic:
DLS1(config)# vlan access-map DENY_MAP 10
DLS1(config-access-map)#match ip address DENY_SERVER
DLS1(config-access-map)#action drop
DLS1(config-access-map)#exit
DLS1(config)#vlan access-map DENY_MAP 20
DLS1(config-access-map)#action forward
3. Apply VLAN map to VLAN 10
DLS1(config)#vlan filter DENY_MAP vlan-list 10