DMVMUG_DAC_Clone_Final
advertisement

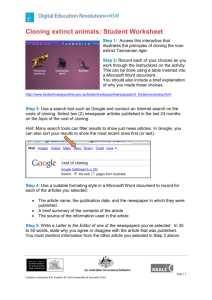
AD for Windows 2012 Deeper Dive - Dynamic Access Control and Domain Controller Cloning JONATHAN CORE – DOMAIN CONTROLLER CLONING KEITH BREWER – DYNAMIC ACCESS CONTROL DMVMUG Reston, VA http://dmvmug.com Dynamic Access Control The access control challenge Dynamic Access Control Technical Features Kerberos support for user claims and device authorization information Support for conditional expressions in permission and audit entries File classification, and central access policies provide an end-to-end authorization management solution. Include conditional expression support in Global Object Access Auditing. Automatic Rights Management Services (RMS) encryption for sensitive Office documents (not included in this document). Access denied remediation to ease the burden of troubleshooting share access problems (not included in this document). Dynamic Access Control New features included in Windows Server 2012 Scenarios Identify data – Automatic and manual classification of files can be applied to tag data in file servers across the organization Control access to files - Central access policies enable organizations to apply safety net policies. For example, you could define who can access health information within the organization. Audit access to files - Central audit policies for compliance reporting and forensic analysis. For example, you could identify who accessed highly sensitive information. Apply RMS protection - Automatic Rights Management Services (RMS) encryption for sensitive Office documents. For example, you could configure RMS to encrypt all documents containing HIPAA information. Dynamic Access Control Benefits Central access policy for access to files – enable organizations to set safety net policies that reflect the business and regulatory compliance. Auditing for compliance and analysis – Enable targeted auditing across file servers for compliance reporting and forensic analysis Protecting sensitive information – Identifying and protecting sensitive information both in a Windows Server 2012 environment and when it leaves the Windows Server 2012 environment Access denied assistance– Improve access denied experience to reduce the helpdesk load and incident time for troubleshooting access denied Dynamic Access Control Prerequisites Windows Server 2012 At least one Windows Server 2012 domain controller accessible by the Windows client in the user's domain At least one Windows Server 2012 domain controller in each domain when using claims across a forest trust Windows 8 client (required when using device claims) Dynamic Access Control Building Blocks Expression-Based ACEs User and Device Claims Classification Enhancements Central Access and Audit Policies Access Denied Assistance • ACEs with conditions, including Boolean logic and relative operators • User and computer attributes can be used in ACEs • File classifications can be used in authorization decisions • Continuous automatic classification • Automatic RMS encryption based on classification • Central authorization/audit rules defined in AD and applied across multiple file servers • Allow users to request access • Provide detailed troubleshooting info to admins Expression-Based Access Conditions Country x 50 Department x 20 Restricted Access User and Device Claims Allow Write if User.MemberOf(Finance) and User.EmployeeType=FullTime and Device.Managed=True Central access policies File Server AD DS User claims User.Department = Finance User.Clearance = High Device claims Device.Department = Finance Device.Managed = True Resource properties Resource.Department = Finance Resource.Impact = High ACCESS POLICY Applies to: @Resource.Impact = High Allow | Read, Write | if (@User.Department == @File.Department) AND (@Device.Managed == True) 11 Claim Support in Windows Server 2012 Claim Information within the PAC Previously included information User security identifiers Group security identifiers Windows Server 2012 User claims Device security identifiers Device group security identifiers Device claims (optional) KDC asks DSA to retrieve claim information from Active Directory KDC inserts claims retrieved by DSA into PAC Claim Support in Windows Server 2012 Flexible Authentication Secure Tunnel (FAST) Known as Kerberos Armoring in Windows 8 (RFC6113) Benefits Protects user pre-authentication data generated from passwords from offline dictionary attacks Protects user Kerberos authentication from KDC error spoofing to downgrade to NTLM Creates a tunnel between the client and the KDC during AS and TGS exchanges Windows 8 armors the AS exchange by using the device’s TGT to protect the request Windows 8 armors the TGS exchange by using the user’s TGT to protect the request Microsoft Confidential - For Internal Use Only Claim Support in Windows Server 2012 Compound Authentication An extension of Kerberos armoring (FAST) that allows clients to provide the device’s TGT Compound Authentication enables a Windows 8 KDC to issue service tickets that include device authorization data Device authorization data includes: Device groups Device claims Access tokens created from issued service tickets also include device authorization data Microsoft Confidential - For Internal Use Only Claim Support in Windows Server 2012 Compound Authentication - Requirements Windows 8 Domain Controller Support for Dynamic Access Control and Kerberos armoring Device must support Compound Authentication (Windows 8) Resource device must support Compound Authentication Applications that support Compound Authentication should register their support for Compound Authentication, or You can enable the Kerberos Group Policy setting Support compound authentication Never: KDC will not provide compound authentication. Automatic: Once a Dynamic Access Control aware application is installed, the KDC will always provide compound authentication and after the last Dynamic Access Control aware application is removed the KDC will not provide compound authentication. Always: KDC will always provide compound authentication. Microsoft Confidential - For Internal Use Only Claim Support in Windows Server 2012 17 Microsoft Confidential - For Internal Use Only Kerberos and The New Token Windows 8 Kerberos extensions Compound ID – binds a user to the device to be authorized as one principal Pre-2012 Token DC enumerates user claims Claims delivered in Kerberos PAC User Account User Account User Groups User & Device data Claims and Groups! 2012 Token [other stuff] Groups User Claims Device Groups Claims [other stuff] Incrementally add capabilities Current infrastructure Windows Server 2012 File Servers • Access and Audit Policies based on security groups and file tagging • Expression-Based ACEs Windows Server 2012 DCs • Centrally defined access and audit policies • User claims can be used by access and audit policies Windows 8 clients • Add device claims to access and audit policies • Better access denied experience How Access Check Works Share Security Descriptor Share Permissions File/Folder Security Descriptor Central Access Policy Reference NTFS Permissions Access Control Decision: 1)Access Check – Share permissions if applicable 2)Access Check – File permissions 3)Access Check – Every matching Central Access Rule in Central Access Policy Active Directory (cached in local Registry) Cached Central Access Policy Definition Cached Central Access Rule Cached Central Access Rule Cached Central Access Rule AD Domain Controller Cloning AD Domain Controller Cloning Before you clone When it makes sense to use Considerations before using Preparation and Pre-Reqs How it works What is this VM Generation ID you speak of? From then (prior to 2012) to now Step – by – Step Before you Clone When to use it Primarily for rolling out a number of Virtual Domain Controllers Initial rollout of 2012 Disaster Recovery Restore Lab or Test environment Increase capacity in large environments (Cloud) Things to consider History – Microsoft wanted to implement a safeguard for VMs Volume Generation ID must be supported by Virtualization Technology Name of DC will be that of original appended w/ -CLNnnnn Prep includes a few commands STILL not recommended to restore from snapshots (Safeguard) Before you Clone (cont’d) Prep and Pre-Reqs Hypervisor that supports VM-Generation ID (Server 2012) Deployed 2012 DC in a domain containing 2012 PDCe Add Source DC to “Cloneable Domain Controllers” group Run PowerShell cmdlets Get-ADDCCloningExcludedApplicationList New-ADDCCloneConfigFile Export then import VM NOTE: The following server roles are not supported for cloning: Dynamic Host Configuration Protocol (DHCP) Active Directory Certificate Services (AD CS) Active Directory Lightweight Directory Services (AD LDS) How it works What is VM Generation ID AD DS initially stores the VM GenerationID identifier as part of the msDS-GenerationID attribute on the domain controller’s computer object From then….. Problems occur when replication is attempted and we experience USN Rollback (Event ID 2095) How it works (Cont’d) What is VM Generation ID AD DS initially stores the VM GenerationID identifier as part of the msDS-GenerationID attribute on the domain controller’s computer object To now (Server 2012) When VM restored or rebooted, VMGID is compared to what’s in the DIT (AD Database) If different, invocationID reset & RID pool discarded How it works Step-by-Step (Assuming you’ve added the clone-able DC to the Security Group) Create the configuration file Shutdown the Source DC / VM Export and Import VM Power New VM on and verify IF there is a failure – Reboot will result in DSRM More on troubleshooting can be found HERE Create Configuration File New-ADDCCloneConfigFile -IPv4Address 10.2.1.10 -IPv4DefaultGateway 10.2.1.1 -IPv4SubnetMask 255.255.255.0 -IPv4DNSResolver 10.1.1.10,10.1.1.11 -Static -SiteName CORPDR 1. Checks for PDCe unless offline switch used 2. Verify Source DC is member of “Cloneable Domain Controllers” group 3. Check against applications that may not support cloning Allow List: C:\Windows\System32\ DefaultDCCloneAllowList.xml Create Configuration File (Cont’d) Get-ADDCCloningExcludedApplicationList XML Files Used DefaultDCCloneAllowList.xml - Default of allowed Services on a DC CustomDCCloneAllowList.xml - Created if GenerateXML switch used when using PS cmdlet above DCCloneConfig.xml - This is what is ultimately used on boot for cloning and renamed once used. - Location can be one of the following - %windir%\NTDS - Location of DIT - Root of any recoverable media Short Q & A References Domain Controller Cloning Introduction to AD DS Virtualization http://technet.microsoft.com/en-us/library/hh831734.aspx Detect and Recover from USN Rollback http://support.microsoft.com/kb/875495 TechNet Blog – AskPFE : Virtual Domain Controller Cloning in Windows Server 2012 http://blogs.technet.com/b/askpfeplat/archive/2012/10/01/virtual-domain-controller-cloningin-windows-server-2012.aspx DC Cloning Troubleshooting http://technet.microsoft.com/en-us/library/jj574207.aspx DMVMUG Reston, VA http://dmvmug.com Email: JCore@Microsoft.com Keith.Brewer@Microsoft.com Speakers Blog: http://blogs.technet.com/b/askpfeplat/ Need more information on DMVMUG Visit www.dmvmug.com Questions?