RE16
© 2003, Cisco Systems, Inc. All rights reserved.
1
1
Module 14
PIX VPN
RE16
2
Learning Objectives
•
Upon completion of this module, you will be able to perform the
following tasks:
–
–
–
–
–
Identify how the PIX Firewall enables a secure VPN.
Identify the tasks to configure PIX Firewall IPSec support.
Identify the commands to configure PIX Firewall IPSec support.
Configure a VPN between PIX Firewalls.
Describe the Cisco VPN Client.
RE16
3
Overview
This module will cover the creation and configuration of secure VPNs.
VPNs are a very useful tool in securing traffic between two remote
networks. Both site-to-site and remote access VPNs will be covered.
Key Terms
•
•
•
•
•
•
•
•
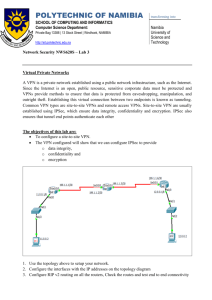
IPSec
IKE
DES, 3DES, AES
SHA-1, MD5
RSA
Digital Certificates
Pre-shared keys
Diffie-Hellman
The PIX Firewall
Enables a Secure VPN
RE16
6
PIX Firewall VPN Topologies
RE16
7
IPSec Enables PIX Firewall
VPN Features
–
–
–
–
Data confidentiality
Data integrity
Data authentication
Anti-replay
RE16
8
What Is IPSec?
•
IETF standard that enables
encrypted communication between
peers
– Consists of open standards for
securing
private communications.
– Network layer encryption
ensuring data
confidentiality, integrity, and
authentication.
– Scales from small to very large
networks.
– Included in PIX Firewall version
5.0 and later.
RE16
9
IPSec Standards Supported
by the PIX Firewall
– IPSec (IP Security protocol)
•
•
–
–
–
–
–
–
–
–
Authentication Header (AH)
Encapsulating Security Payload (ESP)
Internet Key Exchange (IKE)
Data Encryption Standard (DES)
Triple DES (3DES)
Diffie-Hellman (DH)
Message Digest 5 (MD5)
Secure Hash Algorithm (SHA)
Ravist, Shamir, Adelman signatures (RSA)
Certificate Authorities (CA)
RE16
10
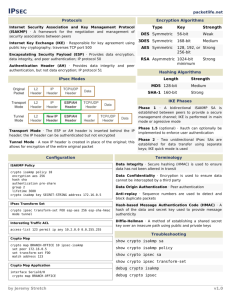
IPSec Configuration Tasks
RE16
11
Task 1—Prepare to
Configure VPN Support
RE16
12
IPSec Configuration
Tasks Overview
–
–
–
–
Task 1—Prepare to configure VPN support.
Task 2—Configure IKE parameters.
Task 3—Configure IPSec parameters.
Task 4—Test and verify VPN configuration.
RE16
13
Task 1—Prepare to
Configure VPN Support
–
–
–
–
Step 1—Determine the IKE (IKE phase one) policy.
Step 2—Determine the IPSec (IKE phase two) policy.
Step 3—Ensure that the network works without encryption.
Step 4—Implicitly permit IPSec packets to bypass PIX Firewall
access lists, access groups, and conduits.
RE16
14
Plan for IKE
IKE Phase One
Policy Parameters
Determine IKE
Phase One Policy
Parameter
Site 1
Site 2
Encryption algorithm
DES
DES
Hash algorithm
SHA
SHA
Authentication method
Pre-share
Pre-share
Key exchange
768-bit D-H
768-bit D-H
IKE SA lifetime
86,400 seconds
86,400 seconds
Plan for IPSec
Determine IPSec
(IKE Phase Two) Policy
Ensure the Network Works
pixfirewall# ping 172.30.2.2
RE16
20
Ensure ACLs do not Block IPSec Traffic
RE16
21
Task 2—Configure IKE Parameters
RE16
22
Step 1—Enable or Disable IKE
pixfirewall (config)#
isakmp enable interface-name
– Enables or disables IKE on the
PIX Firewall interfaces.
– IKE is enabled by default.
– Disable IKE on interfaces not used
for IPSec.
pixfirewall(config)# isakmp enable outside
RE16
23
Step 2—Configure an IKE
Phase One Policy
pixfirewall(config)# isakmp
encryption des
pixfirewall(config)# isakmp
sha
pixfirewall(config)# isakmp
authentication pre-share
pixfirewall(config)# isakmp
pixfirewall(config)# isakmp
lifetime 86400
–
–
–
policy 10
policy 10 hash
policy 10
policy 10 group 1
policy 10
Creates a policy suite grouped by priority number.
Creates policy suites that match peers.
Can use default values.
RE16
24
Step 3—Configure the IKE
Pre-shared Key
pixfirewall(config)#
isakmp key keystring address peer-address
[netmask]
– Pre-shared keystring must be identical at both peers.
– Use any combination of alphanumeric characters up to 128 bytes for
keystring.
– Specify peer-address as a host or wildcard address.
– Easy to configure, yet is not scalable.
pixfirewall(config)# isakmp key cisco123
address 192.168.6.2
RE16
25
Step 4—Verify IKE
Phase One Policies
pixfirewall# show isakmp policy
Protection suite of priority 10
encryption algorithm:
hash algorithm:
authentication method:
Diffie-Hellman group:
lifetime:
Default protection suite
encryption algorithm:
hash algorithm:
authentication method:
Diffie-Hellman group:
lifetime:
–
DES - Data Encryption Standard (56 bit keys).
Secure Hash Standard
Pre-Shared Key
#1 (768 bit)
86400 seconds, no volume limit
DES - Data Encryption Standard (56 bit keys).
Secure Hash Standard
Rivest-Shamir-Adleman Signature
#1 (768 bit)
86400 seconds, no volume limit
Displays configured and default IKE protection suites.
RE16
26
Task 3—Configure
IPSec Parameters
RE16
27
Step 1—Configure
Interesting Traffic
pixfirewall(config)#
access-list acl_ID {deny | permit} protocol
source_addr source_mask destination_addr
destination_mask
–
–
–
permit = encrypt
deny = do not encrypt
access-list selects IP traffic by address, network, or subnet
pixfirewall# access-list 101 permit ip host
192.168.1.10 host 192.168.6.10
RE16
28
Example Crypto ACLs
PIX1
pix1(config)# show static
static (inside,outside) 192.168.1.10 10.0.1.11 netmask 255.255.255.255
0 0
pix1(config)# show access-list
access-list 110 permit ip host 192.168.1.10 host 192.168.6.10
PIX6
pix6(config)# show static
static (inside,outside) 192.168.6.10 10.0.6.11 netmask 255.255.255.255
0 0
pix2(config)# show access-list
access-list 101 permit ip host 192.168.6.10 host 192.168.1.10
–
Lists should always be symmetrical.
Step 2—Configure an
IPSec Transform Set
pixfirewall(config)#
crypto ipsec transform-set transform-set-name
transform1 [transform2 [transform3]]
– Sets are limited to up to one AH and up to two ESP transforms.
– Default mode is tunnel.
– Configure matching sets between IPSec peers.
pix1(config)# crypto ipsec transform-set
pix6 esp-des
RE16
30
Available IPSec Transforms
ah-md5-hmac
ah-sha-hmac
esp-des
esp-3des
esp-md5-hmac
esp-sha-hmac
AH-HMAC-MD5 transform
AH-HMAC-SHA transform
ESP transform using DES cipher (56 bits)
ESP transform using 3DES cipher(168 bits)
ESP transform using HMAC-MD5 auth
ESP transform using HMAC-SHA auth
RE16
31
Step 3—Configure the Crypto
Map
pixfirewall(config)# crypto map MYMAP 10 ipsec-isakmp
pixfirewall(config)# crypto map MYMAP 10 match address 101
pixfirewall(config)# crypto map MYMAP 10 set peer
192.168.6.2
pixfirewall(config)# crypto map MYMAP 10 set transform-set
pix6
pixfirewall(config)# crypto map MYMAP 10 set pfs group1
pixfirewall(config)# crypto map MYMAP 10 set securityassociation lifetime seconds 28800
–
–
Specifies IPSec (IKE phase two) parameters.
Map names and sequence numbers group entries into a policy.
RE16
32
Step 4—Apply the
Crypto Map to an Interface
pixfirewall(config)#
crypto map map-name interface interface-name
– Applies the crypto map to an interface.
– Activates IPSec policy.
pixfirewall(config)# crypto map MYMAP
interface outside
RE16
33
Example Crypto Map for PIX1
pix1(config)# show crypto map
Crypto Map "peer2" 10 ipsec-isakmp
Peer = 192.168.2.2
access-list 101 permit ip host 192.168.1.11 host 192.168.2.11 (hitcnt=0)
Current peer: 192.168.2.2
Security association lifetime: 4608000 kilobytes/28800 seconds
PFS (Y/N): N
Transform sets={ pix2, }
Example Crypto Map for PIX2
pix2(config)# show crypto map
Crypto Map "peer1" 10 ipsec-isakmp
Peer = 192.168.1.2
access-list 101 permit ip host 192.168.2.11 host 192.168.1.11 (hitcnt=0)
Current peer: 192.168.1.2
Security association lifetime: 4608000 kilobytes/28800 seconds
PFS (Y/N): N
Transform sets={ pix1, }
Task 4—Test and Verify
VPN Configuration
RE16
36
Task 4—Test and Verify
VPN Configuration
– Verify ACLs and interesting traffic.
show access-list
– Verify correct IKE configuration.
show isakmp
show isakmp policy
– Verify correct IPSec configuration.
show crypto ipsec transform-set
RE16
37
Task 4—Test and Verify VPN
Configuration (cont.)
– Verify the correct crypto map configuration.
show crypto map
– Clear the IPSec SA.
clear crypto ipsec sa
– Clear the IKE SA.
clear crypto isakmp sa
– Debug IKE and IPSec traffic through the
PIX Firewall.
debug crypto ipsec
debug crypto isakmp
RE16
38
The Cisco VPN Client
RE16
39
Topology Overview
Cisco VPN Client Features
– Support for Windows ME, Windows 2000, and
Windows XP
– Data compression
– Split tunneling
– User authentication by way of VPN central-site device
– Automatic VPN Client configuration
– Internal MTU adjustment
– CLI to the VPN Dialer
– Start Before Logon
– Software update notifications from the VPN device upon connection
RE16
41
PIX Firewall to VPN Client
Pre-Shared Example
pixfirewall# write terminal
access-list 80 permit ip 10.0.0.0 255.255.255.0 10.0.20.0
255.255.255.0
ip address outside 192.168.0.2 255.255.255.0
ip address inside 10.0.0.1 255.255.255.0
ip local pool MYPOOL 10.0.20.1-10.0.20.254
nat (inside) 0 access-list 80
route outside 0 0 192.168.0.1
aaa-server MYTACACS protocol tacacs+
aaa-server MYTACACS (inside) host 10.0.0.10 tacacskey timeout 5
aaa authentication include any inbound 0 0 0 0 MYTACACS
sysopt connection permit-ipsec
crypto ipsec transform-set AAADES esp-des esp-md5-hmac
crypto dynamic-map DYNOMAP 10 set transform-set AAADES
RE16
42
PIX Firewall to VPN Client
Pre-Shared Example (cont.)
pixfirewall# write terminal
crypto map VPNPEER 20 ipsec-isakmp dynamic DYNOMAP
crypto map VPNPEER client authentication MYTACACS
crypto
isakmp
isakmp
isakmp
map VPNPEER interface outside
enable outside
identity address
policy 10 authentication pre-share
isakmp policy 10 encryption des
isakmp policy 10 hash md5
isakmp policy 10 group 2
isakmp policy 10 lifetime 86400
vpngroup TRAINING address-pool MYPOOL
vpngroup TRAINING idle-time 1800
vpngroup TRAINING password ********
RE16
43
VPN Client to
PIX Firewall Example
– A new connection entry
named vpnpeer0 is
created.
– The remote server IP
is the PIX Firewall
outside interface.
vpnpeer0
RE16
44
VPN Client to PIX Firewall
Example (cont.)
– The group name matches the
vpngroup name in the PIX
Firewall.
– The password is the
pre-shared key and must match
the vpngroup password.
– You can use the digital
certificate for authentication.
RE16
TRAINING
TRAINING
TRAINING
45
PIX Firewall Assigns the
IP Address to the VPN Client
Scale PIX Firewall VPNs
RE16
47
CA Server Fulfilling
Requests from IPSec Peers
•Each IPSec peer individually enrolls with the CA server.
Enroll a PIX Firewall
with a CA
–
–
–
–
–
Configure CA support
Generate public or private keys
Authenticate the CA
Request signed certificates from the CA
CA administrator verifies request and
sends signed certificates
RE16
49
Summary
RE16
50
Summary
– The PIX Firewall enables a secure VPN.
– IPSec configuration tasks include configuring IKE and IPSec
parameters.
– CAs enable scaling to a large number of IPSec peers.
– Remote users can establish secure VPN tunnels between PCs
running Cisco VPN Client software and any Cisco VPN-enabled
product, such as the PIX Firewall, that supports the Unified Client
framework.
RE16
51
RE16
© 2003, Cisco Systems, Inc. All rights reserved.
52
52