POLYTECHNIC OF NAMIBIA transforming into
advertisement
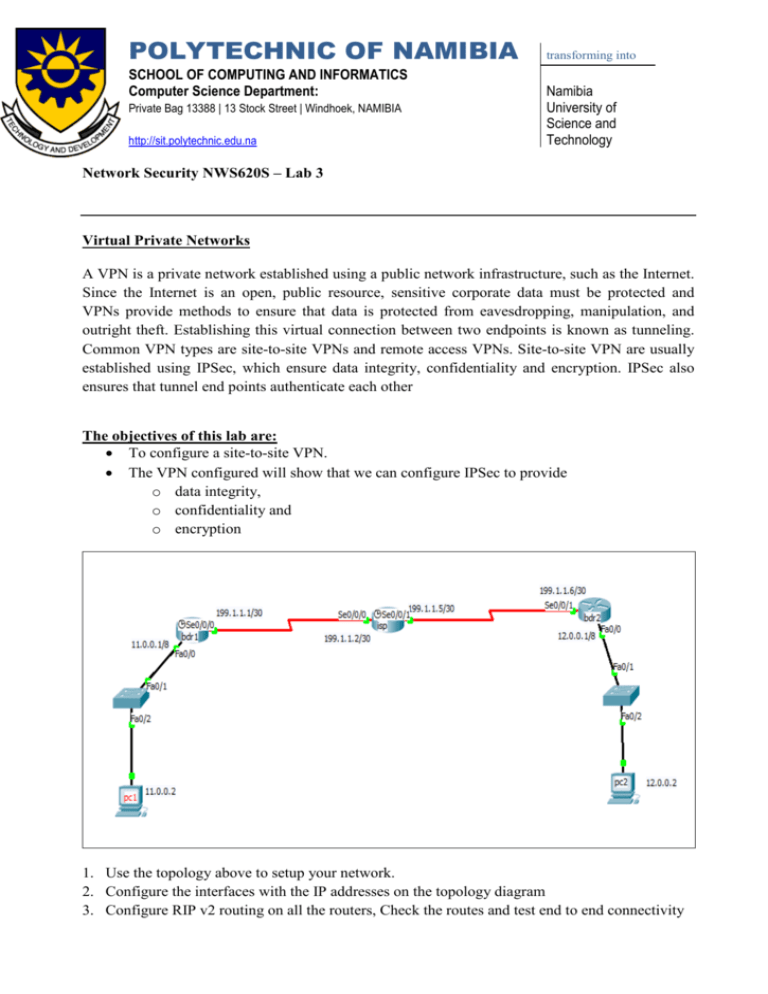
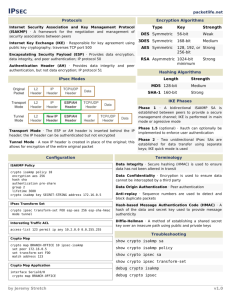
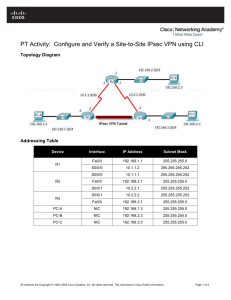
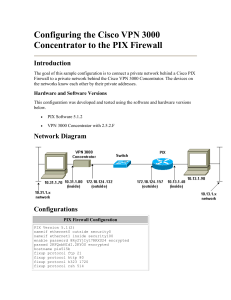
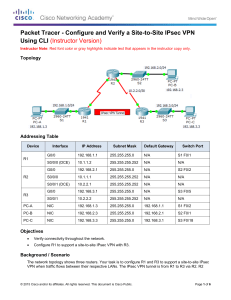
POLYTECHNIC OF NAMIBIA SCHOOL OF COMPUTING AND INFORMATICS Computer Science Department: Private Bag 13388 | 13 Stock Street | Windhoek, NAMIBIA http://sit.polytechnic.edu.na transforming into Namibia University of Science and Technology Network Security NWS620S – Lab 3 Virtual Private Networks A VPN is a private network established using a public network infrastructure, such as the Internet. Since the Internet is an open, public resource, sensitive corporate data must be protected and VPNs provide methods to ensure that data is protected from eavesdropping, manipulation, and outright theft. Establishing this virtual connection between two endpoints is known as tunneling. Common VPN types are site-to-site VPNs and remote access VPNs. Site-to-site VPN are usually established using IPSec, which ensure data integrity, confidentiality and encryption. IPSec also ensures that tunnel end points authenticate each other The objectives of this lab are: • To configure a site-to-site VPN. • The VPN configured will show that we can configure IPSec to provide o data integrity, o confidentiality and o encryption 1. Use the topology above to setup your network. 2. Configure the interfaces with the IP addresses on the topology diagram 3. Configure RIP v2 routing on all the routers, Check the routes and test end to end connectivity 4. For the IPSec tunnel do the following a. bdr1(config)#crypto isakmp enable starting IPsec in the router b. bdr1(config)#crypto isakmp policy 1 After issuing this command you specify the parameters that are going to be used by IPSec. The ISAKMP policy specifies the details for the initial key and secure parameters exchange. c. bdr1(config-isakmp)#authentication pre-share d. bdr1(config-isakmp)#encryption aes e. bdr1(config-isakmp)#hash sha f. bdr1(config-isakmp)#group 2 g. bdr1 (config-isakmp)#exit h. bdr1(config)#crypto isakmp key password address 199.1.1.6 The key must match on both endpoints i. bdr1 (config)#crypto ipsec transform-set lab7 esp-aes esp-sha-hmac transform set for data protection (data encapsulation method) j. bdr1(config)#crypto ipsec security-association lifetime seconds 86400 lifetime of the key you defined above k. bdr1 (config)#access-list 120 permit ip 11.0.0.1 0.255.255.255 12.0.0.0 0.255.255.255 ACL identifies the traffic that will be encrypted through the tunnel l. bdr1(config)#crypto map lab7 10 ipsec-isakmp % NOTE: This new crypto map will remain disabled until a peer and a valid access list have been configured. Tunnel information is identified by a crypto map which joins the ISAKMP policies, IPsec data detail, the peer address, and the crypto ACL. m. n. o. p. q. bdr1(config-crypto-map)#match address 120 bdr1 (config-crypto-map)#set peer 199.1.1.6 bdr1 (config-crypto-map)#set pfs group2 bdr1(config-crypto-map)#set transform-set lab7 bdr1 (config-crypto-map)#exit r. bdr1(config)#int s 0/0/0 s. bdr1(config-if)#crypto map lab7 identifies interface partipating in the tunnel CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON 5. Save your configurations 6. REPEAT STEPS 4 -5 ON bdr2 ROUTER MAKING SURE TO CHANGE THE PARAMETERS TO SUIT bdr2 WHERE NECESSARY 7. Issue the following show commands on router bdr1 and bdr2 a. show crypto Isakmp policy b. show crypto isakmp sa status should be active c. show crypto map d. sh crypto ipsec transform-set e. show crypto ipsec sa you should see that the tunnel has not yet been used 8. Ping PC2 from PC1 and vice versa a. show crypto ipsec sa you should see that the tunnel has been used