Networks - PEGSnet
advertisement

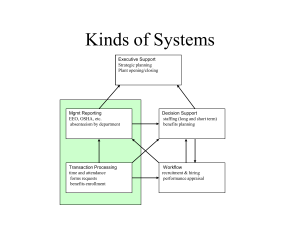
Networks Software Development Unit 2 2010 What is a network? A network is two or more computers connected together for the purpose of: sharing resources (printers, files, software, hardware) communication How are they classified? Their size: LAN, WAN Their configuration: client-server, peer-to-peer (no servers) The rules they use to exchange data: protocols How they are linked together: cable, wireless Their logical shape (topology): bus, tree, star, ring, mesh Types of networks: Local Area Networks (LAN) One location Wide Area Networks (WAN) Centralised WAN: Servers in one location Distributed WAN: Servers distributed throughout the network (the Internet is an example of this) LAN WAN Network configurations Client-server File server Application server Files stored and accessed from central location Applications installed and executed from central location. Often used in combination with file servers Peer-to-peer No servers Applications installed on each PC, files shared Protocols A protocol is a convention or a standard that controls or enables the connection, communication and data transfer between computers on a network Contains rules governing the syntax, semantics and synchronization of communication May be implemented by hardware, software or a combination Like two people agreeing to speak the same language… Communication protocols Communication protocols are specifically designed to control data transfer over a communications channel Some common examples: TCP/IP: Two protocols that control communication across the Internet and These examples are some networks often referred to as the POP3, IMAP, SMTP: Protocols that can ‘Internet protocols’ be used to send and receive email HTTP: Method of publishing and retrieving web pages FTP: Protocol for sending and receiving files Network Protocols Rules and conventions for communication between network devices The commonly used are Ethernet, Wi-Fi Others exist but are not as widely used Ethernet Uses an access method called CSMA/CD (Carrier Sense Multiple Access/Collision Detection) CS – Computers (or nodes) ‘listen’ to the network to see if there are any signals being transmitted MA – All computers (or nodes) can ‘hear’ what is being transmitted on the network at any one time CD – Collision detection: two computers (or nodes) could transmit at the same time, causing a collision Ethernet What happens when there is a collision? Each computer (or node) waits a random amount of time and then retransmits The random time delay is usually enough to ensure the collision does not reoccur The Ethernet specified speed is 10Mb/s The Fast Ethernet standard increases this to 100Mb/s Wi-Fi Based on the 802.11x standard Cannot do collision detection and instead uses RTS/CTS RTS: Request to send – packet sent by the sender CTS: Clear to send – packet sent by the intended recipient that alerts all other nodes to be ‘quiet’ TCP/IP TCP/IP consists of two protocols: TCP and IP protocol TCP (Transport Control Protocol) Used to divide data that needs to be transmitted into a number of packets, each with a sequence number The TCP at the destination address assembles the data and notifies the sender if any packets are not received within a certain time (‘timeout’) IP (Internet Protocol) Defines how information gets sent between network nodes TCP/IP: IP Address In order for packets to be able to be sent across the Internet or a network, each node must have a unique IP address (just like a street address) Domain Name Servers (DNS) translate URLs to IP addresses An IP address consists of 4 bytes (32 bits) For example: 255.255.255.255 TCP/IP: Packets TCP divides data to be sent into packets Each packet contains: A header consisting of: a destination address a source address the packet number the total number of packets a checksum and some other things… The data itself (known as the payload) A trailer TCP/IP: From source to destination If a packet arrives at a destination with an incorrect checksum, it is discarded The path from the source to destination is in flux, therefore packets ‘get lost’, are corrupted or are duplicated If a ‘timeout’ occurs or a packet is corrupted, a request for a resend of that packet is sent After several unsuccessful attempts at receiving a packet, the connection is broken Network Hardware Network hardware includes: Network Interface Controllers (NICs) Switches / Hubs Repeaters Bridges Routers Transmission media (cabling) Network interface controller NICs provide a physical connection from a computer (or node) to the network Can be integrated on the motherboard Each has a unique 48-bit MAC address Stored in ROM Media Access Control Acts like a name for the card No two the same http://en.wikipedia.org/wiki/Network_card Hubs Connects a number of NICs together Consists of a number of ports Signals arriving at one port and sent to all other ports Large number of collisions: a “dumb device” http://en.wikipedia.org/wiki/Ethernet_hub Switches Sends data only to the port that requires it – a “clever hub” Reduces collisions – and in many cases can eliminate them altogether Much better than hubs – traditionally were much more expensive, but this is no longer the case http://en.wikipedia.org/wiki/Network_switch Repeaters As a network signal degrades as it travels over large distances, a repeater can be used to boost the signal Both switches and hubs act as repeaters http://www.unitedsale.net/products/image02/D-Link-DWL-G710-Range-Extender2.jpg Bridges Network devices that can be used to connect two different physical networks together For example, a bridge could be used to join an ethernet network and a fast ethernet network or a star and a bus topology http://www.streamshop.ru/Modems/P6212.jpg Routers Acts as a junction between two or more networks Directs traffic in the same way as a switch, but can also translate and filter (firewall) Used to connect LANs to the Internet For example, a router may connect to the Internet and be assigned an IP address by an ISP IP addresses may exist within the LAN that duplicate those on the Internet, but the router ensures these are private to the LAN http://shopproducts.howstuffworks.co m/Linksys+WRT54GS+Wireless+Ro uter/SF-1/PID-20664068 Bridges vs Routers Bridges and routers work in different ways (on different OSI layers – look up the definition of this if you want to know more) Bridges are not able to convert from one protocol to another where routers can http://images.amazon.com/images/P/ B000H1L5W4.01._AA280_SCLZZZ ZZZZ_V61775592_.jpg Network Cabling Cables transmit data from one network node to another Several types of cable exist, each having a particular bandwidth Coaxial cable UTP cable Fibre optic cable Different types can be used within the same network, but this can affect bandwidth Coaxial cable http://searchnetworking.techtarget.co m/sDefinition/0,,sid7_gci211806,00.h tml http://www.fotosearch.com/resu lts.asp?keyword=coaxial+cable &category=&searchtype=sss Consists of a round conducting wire, surrounded by an insulating spacer, surrounded by a cylindrical conducting sheath Highly resistant to signal interference Not used much today Bayonet style connectors Often associated with bus networks Bandwidth: 10Mb/s UTP Cable Unshielded Twisted Pair (UTP) is the most popular cabling used currently Also comes in a Shielded Twisted Pair version, that prevent interference Cables are twisted together to decrease interference Length limit is 100 metres Cheap UTP Cable Connector on the end is called an RJ45 CAT5 is most common version and provides a bandwidth of 100Mb/s CAT5e can provide 1000Mb/s (or a gigabit/s) CAT6a is a future specification designed for 10Gb/s! http://en.wikipedia.org/wiki/Image:U TP_ethernet_cable_8pin_modular_ja ck_endings.jpg http://en.wikipedia.org/wiki/Category _5_cable Fiber Optic Cable Transmits light using the concept of critical angle As a result, cannot bend through tight angles Not affected by interference Can carry multiple signals at the same time Very hand bandwidth possible Expensive and difficult to install http://www.fotosearch.com/PD S084/aa031778/ Wireless LANs Wireless network hardware is available Wireless router Wireless NIC Wireless Access Point (equivalent to a switch) Relatively cheap and easy to install Encryption a must! WAP (Wireless Application Protocol) WPA, WPA2 are better Wireless LANs 802.11x is a set of standards defining the way signals are formatted, the frequencies they use and ultimately, transfer speed 802.11a: (1999), max 54Mb/s 802.11b: (1999), max 11Mb/s 802.11g: (2003), max 54Mb/s 802.11n (draft): (2007), max 540Mb/s Typical speeds are often half the max speeds due to other network traffic Most devices are backwards compatible, for example a device might be 802.11bg http://en.wikipedia.org/wiki/I mage:Linksys_Router.png Topology The arrangement of nodes within a network Main types : Bus Star Ring* Tree Mesh* * Not examinable http://en.wikipedia.org/wiki/I mage:NetworkTopologies.png Bus Contains a backbone which usually runs the length of the network Ends are normally terminated using special connectors Often associated with coaxial cable http://compnetworking.about.com/od/networkdesi gn/ig/Computer-Network-Topologies/BusNetwork-Topology-Diagram.htm Star In a star network, a central point is used to connect all other network nodes The central point is usually a hub or a switch All messages are routed through the central computer which acts as a traffic cop to prevent collisions. http://compnetworking.about.com/od/networkdesi gn/ig/Computer-Network-Topologies/RingNetwork-Topology-Diagram.htm Any connection failure between a node and the hub will not affect the overall system. Common network topology Easy and cheap to implement Tree Topology In a hierarchical network, one computer, usually the mainframe, controls the entire network. It can be described as a multiple star network with various levels of computers with their own smaller network, and so on down the hierarchical chain. The network branches out similar to a tree. A tree topology combines star and bus topologies Usually this takes the form of star networks linked by a network backbone (or a bus network) http://compnetworking.about.com/od/networkdesign/ig/ComputerNetwork-Topologies/Tree-Network-Topology-Diagram.htm These networks are a lot easier to repair than other topologies because you can isolate the problem and it will not have too much of an effect on the rest of the network. Server Switch Switch Mesh Topology In a mesh topology system every computer is connected to every other computer. Designed to offer the maximum amount of reliability for data transit and fault-tolerance. The major problem is the amount of cabling necessary to create this topology, plus each link from one device to another requires an individual network card. Not only are physical components wasted, but the overall capacity to carry data is grossly under-utilised unless all computers are transmitting to one another almost constantly. Typically, a mesh network is used by governments and the defence forces, so if one computer or a number of components are knocked out by warfare, enough links still exist for all of the remaining computers to be able to talk to each other. A mesh topology is one in which paths between network nodes are often changing as the status of nodes changes The Internet is a perfect example of a mesh topology http://compnetworking.about.com/od/networkdesign/ig/ComputerNetwork-Topologies/Mesh-Network-Topology-Diagram.htm Hybrid Topology A Hybrid topology can be formed by using elements from more than one of four topologies - star, ring, bus, mesh. Ring All network nodes are connected in a ring A token is passed around the network from one computer to another Only the node that holds the token can transmit data No collisions http://compnetworking.about.com/od/networkdesi gn/ig/Computer-Network-Topologies/RingNetwork-Topology-Diagram.htm Used to be implemented using coaxial cable and is sometimes used with fibre optic cable today Two rings transmitting data in different directions can be used Other Network Components Cont Network Operating System (NOS) Network Operating Systems The most popular NOSes are: •Novell Netware (better, more expensive at first, cheaper over time) •Microsoft Server 2003 (now dominant) They offer similar services. Network Operating System (NOS) Server is a generic term applied to any machine running a ‘service’ application. Eg access to shared files (file server) or access to shared printers (print server). These tasks, and many more, are controlled by the Network Operating System. A NOS operates in the same way to the operating system of a PC; however it has special capabilities that enable it to connect computers and peripheral devices, such as printers, to a LAN. All networking software has a range of functions to perform once the connection has been made: These functions are: 1. 2. 3. 4. Administration File Management Other Resource Management Security 1. Administration - the management of users is the main task. Their authorisation details need to be added, deleted and organised into groups. Backup procedures need to be run. 2. File Management - the location and transfers of files being used needs to be managed between users and storage locations. 3. Other Resource Management such as printer management that involves the spooling of print tasks and the allocation of these tasks to the appropriate printer. 4. Security - the access rights of users need to be set up and monitored. Popular Network Operating Systems Unix - a multi-user, multi-tasking operating system that can be used on a variety of computers ranging from a mainframe to a personal computer. Novell NetWare - the most popular of all NOS. provides users with a regular interface that is self-sufficient of the hardware being used at the time. It is a stand-alone system which is situated on the server. Windows 2000, Windows Server 2003 & Windows Server 2008 - is the major upgrade of Windows NT; it allows for plug-and-play, which enables the addition of peripheral devices. It also uses ‘active directory’ which makes network administration simpler and more stable. Linux - is a version of Unix that runs on a number of hardware platforms. Because of its stability it is very popular with Internet Service Providers (ISPs) as an operating system for web servers. Mac OSX Server -is a line of computer operating systems developed, marketed, and sold by Apple Inc, the latest of which is pre-loaded on all currently shipping Macintosh computers. Mac OS X is the successor to the original Mac OS, which had been Apple's primary operating system since 1984. Unlike its predecessors, Mac OS X is a Unix-based operating system built on technology that had been developed through the second half of the 1980s. Servers Robust central computers at the heart of a network. File servers are the most common server type. File Servers File servers run the Network operating system (NOS) which handles: •authenticating users during login •controlling users’ access to resources based on their rights •managing print queues •doing backups •running centralised software such as virus scanners •running services like DHCP to give out IP addresses to workstations • controlling internet services File Servers Servers don’t really have anything special in terms of hardware. Expensive because of their high-quality components, and “scalability” (expandability). •Memory – servers love lots of RAM. •Storage –need large and fast hard disks – often RAID (discussed soon) File Servers vs Desktops 1 •CPU Processing power – not very important in a file server •Backup – most servers have inbuilt high-capacity tape backup drives to protect against data loss. Tape drives usually use QIC (Quarter Inch Cartridge) DAT (Digital audio tapes) tapes. Servers are the muscle men in the computer world File Servers vs Desktops 2 Connectivity – servers often have two or more gigabit NICs to increase their data-throughput. Robustness - servers run all day for years, and need rugged high-quality components Scalability –the ability to increase the size and power of equipment and networks as required e.g. add 8 hard disks, two power supplies, two NICs, two CPUs, lots of RAM etc. Designing and engineering this expandability is expensive. R.A.I.D. Redundant Array of Independent [or Inexpensive] Disks) arrays for reliability and/or speed. RAID uses a group of hard disks that work as a single disk under a RAID controller. Flavours of RAID: RAID0 to RAID10 (RAID 1 + RAID 0) offer reliability and/or speed (at ever-increasing cost). Includes mirroring (for reliability) and striping (for speed). RAID disks are usually "Hot Swap". EXPENSIVE – needs justifying for small organisation 3-disk RAID array Server farms On smaller networks, network services are performed by software in a single server. On busy LANs, multiple servers share the work… •Login servers – authenticate users •Proxy servers – cache downloads •DHCP servers – allocate IP addresses •Print servers –manage print job queues •Web/FTP servers – serve web pages or files •Email servers –handle email Proxy Servers A proxy server is a program on a special server computer that is used to access websites on behalf of other computers; hence it acts as a proxy for the actual Internet. When a computer wants a website, it is retrieved by the proxy server and then sent to the requesting computer after it has passed the firewall program. Security