Mobile Communications

Mobile Networks
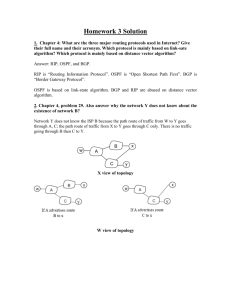
Module B
WLAN – Engineering Aspects
Prof. JP Hubaux http://mobnet.epfl.ch
1
twisted pair
Reminder on frequencies and wavelenghts
coax cable optical transmission
1 Mm
300 Hz
10 km
30 kHz
100 m
3 MHz
1 m
300 MHz
10 mm
30 GHz
100
m
3 THz
1
m
300 THz
VLF LF MF HF VHF UHF SHF EHF
VLF = Very Low Frequency
LF = Low Frequency
MF = Medium Frequency
HF = High Frequency
VHF = Very High Frequency infrared visible light
UV
UHF = Ultra High Frequency
SHF = Super High Frequency
EHF = Extra High Frequency
UV = Ultraviolet Light
Frequency and wave length:
= c/f wave length
, speed of light c
3x10 8 m/s, frequency f
2
Frequencies for mobile communication
VHF-/UHF-ranges for mobile radio
simple, small antenna for cars deterministic propagation characteristics, reliable connections
SHF and higher for directed radio links, satellite communication
small antenna large bandwidth available
Wireless LANs use frequencies in UHF to SHF spectrum
some systems planned up to EHF limitations due to absorption by water and oxygen molecules
(resonance frequencies)
weather dependent fading, signal loss caused by heavy rainfall etc.
3
Frequency allocation
Mobile phones
Cordless telephones
Wireless
LANs
Europe
NMT 453-457MHz,
463-467 MHz;
GSM 890-915 MHz,
935-960 MHz;
1710-1785 MHz,
1805-1880 MHz
CT1+ 885-887 MHz,
930-932 MHz;
CT2
864-868 MHz
DECT
1880-1900 MHz
IEEE 802.11
2400-2483 MHz
HIPERLAN 1
5176-5270 MHz
USA
AMPS , TDMA , CDMA
824-849 MHz,
869-894 MHz;
TDMA , CDMA , GSM
1850-1910 MHz,
1930-1990 MHz;
PACS 1850-1910 MHz,
1930-1990 MHz
PACS-UB 1910-1930 MHz
IEEE 802.11
2400-2483 MHz
Japan
PDC
810-826 MHz,
940-956 MHz;
1429-1465 MHz,
1477-1513 MHz
PHS
1895-1918 MHz
JCT
254-380 MHz
IEEE 802.11
2471-2497 MHz
4
Characteristics of wireless LANs
Advantages
flexibility
(almost) no wiring difficulties (e.g., historic buildings) more robust against disasters like, e.g., earthquakes, fire - or users pulling a plug...
Disadvantages
lower bitrate compared to wired networks (1-10 Mbit/s)
More difficult to secure
5
Design goals for wireless LANs
low power no special permissions or licenses needed to use the LAN robust transmission technology easy to use for everyone, simple management protection of investment in wired networks (internetworking) security (no one should be able to read my data), privacy (no one should be able to collect user profiles), safety (low radiation) transparency concerning applications and higher layer protocols, but also location awareness if necessary
6
Comparison: infrared vs. radio transmission
Infrared
uses IR diodes
Advantages
simple, cheap, available in many mobile devices
no licenses needed simple shielding possible
Disadvantages
interference by sunlight, heat sources etc.
many things shield or absorb IR light low bandwidth
Example
IrDA (Infrared Data Association) interface available everywhere
Radio
typically using the license free
ISM band at 2.4 GHz
Advantages
coverage of larger areas possible (radio can penetrate walls, furniture etc.)
Disadvantages
very limited license free frequency bands
shielding more difficult, interference with other electrical devices
more difficult to secure
Examples
IEEE 802.11, Bluetooth
7
Infrastructure vs. ad hoc networks
infrastructure network
AP: Access Point
AP
AP wired network
AP
Ad hoc network
8
STA
1
ESS
802.11 LAN
BSS
1
Access
Point
Portal
Distribution System
Access
Point
STA
2
IEEE 802.11 - Architecture of an infrastructure network
BSS
2
802.11 LAN
802.x LAN
STA
3
Station (STA)
terminal with access mechanisms to the wireless medium and radio contact to the access point
Basic Service Set (BSS)
group of stations using the same radio frequency
Access Point
station integrated into the wireless
LAN and the distribution system
Portal
bridge to other (wired) networks
Distribution System
interconnection network to form one logical network (ESS:
Extended Service Set) based on several BSS
9
STA
1
802.11 - Architecture of an ad-hoc network
BSS
1
802.11 LAN
STA
2
STA
3
Direct communication within a limited range
Station (STA): terminal with access mechanisms to the wireless medium
Basic Service Set (BSS): group of stations using the same radio frequency
802.11 LAN
BSS
2
STA
5
STA
4
10
Interconnection of IEEE 802.11 with Ethernet
mobile station server infrastructure network access point fixed terminal application
TCP
IP
802.11 MAC
802.11 PHY
802.11 MAC
802.11 PHY
802.3 MAC
802.3 PHY application
TCP
IP
802.3 MAC
802.3 PHY
11
802.11 - Layers and functions
MAC
access mechanisms, fragmentation, encryption
MAC Management
synchronization, roaming, MIB, power management
PLCP
(Physical Layer Convergence Protocol)
clear channel assessment signal (carrier sense)
PMD
(Physical Medium Dependent)
modulation, coding
PHY Management
channel selection, MIB
Station Management
coordination of all management functions
IP
MAC
PLCP
PMD
MAC Management
PHY Management
12
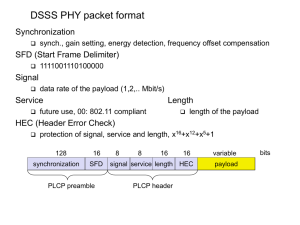
802.11 - Physical layer
3 versions: 2 radio: DSSS and FHSS (both typically at 2.4 GHz), 1 IR
data rates 1, 2, 5 or 11 Mbit/s
DSSS (Direct Sequence Spread Spectrum)
DBPSK modulation (Differential Binary Phase Shift Keying) or DQPSK
(Differential Quadrature PSK) chipping sequence: +1, -1, +1, +1, -1, +1, +1, +1, -1, -1, -1 (Barker code) max. radiated power 1 W (USA), 100 mW (EU), min. 1mW
FHSS (Frequency Hopping Spread Spectrum)
spreading, despreading, signal strength min. 2.5 frequency hops/s, two-level GFSK modulation (Gaussian
Frequency Shift Keying)
Infrared
850-950 nm, diffuse light, around 10 m range carrier detection, energy detection, synchronization
13
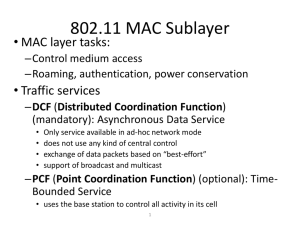
802.11 - MAC layer principles (1/2)
Traffic services
Asynchronous Data Service (mandatory)
exchange of data packets based on “best-effort”
support of broadcast and multicast
Time-Bounded Service (optional)
implemented using PCF (Point Coordination Function)
Access methods (called DFWMAC: Distributed Foundation Wireless
MAC)
DCF CSMA/CA (mandatory)
collision avoidance via randomized „back-off“ mechanism
minimum distance between consecutive packets
ACK packet for acknowledgements (not for broadcasts)
DCF with RTS/CTS (optional)
avoids hidden terminal problem
PCF (optional)
access point polls terminals according to a list
DCF: Distributed Coordination Function
PCF: Point Coordination Function
14
802.11 - MAC layer principles (2/2)
Priorities
defined through different inter frame spaces no guaranteed, hard priorities
SIFS (Short Inter Frame Spacing)
highest priority, for ACK, CTS, polling response
PIFS (PCF IFS)
medium priority, for time-bounded service using PCF
DIFS (DCF, Distributed Coordination Function IFS)
lowest priority, for asynchronous data service
DIFS DIFS
PIFS
SIFS medium busy direct access if medium is free
DIFS contention time slot
Note : IFS durations are specific to each PHY next frame t
15
DIFS
802.11 - CSMA/CA principles
DIFS contention window
(randomized back-off mechanism) medium busy direct access if medium has been free for at least DIFS next frame time slot t
station ready to send starts sensing the medium (Carrier Sense based on CCA, Clear Channel Assessment) if the medium is free for the duration of an Inter-Frame Space (IFS), the station can start sending (IFS depends on service type) if the medium is busy, the station has to wait for a free IFS, then the station must additionally wait a random back-off time (collision avoidance, multiple of slot-time) if another station occupies the medium during the back-off time of the station, the back-off timer stops (to increase fairness)
16
DIFS
802.11 – CSMA/CA broadcast
=
DIFS bo e bo r
DIFS bo e bo r
DIFS bo e busy station
1 bo e busy station
2 busy station
3 bo e busy (detection by upper layer) station
4 station
5 bo e bo r bo e busy (detection by upper layer) t
Here St4 and St5 happen to have the same back-off time busy medium not idle (frame, ack etc.) packet arrival at MAC
The size of the contention window can be adapted
(if more collisions, then increase the size) bo e elapsed backoff time bo r residual backoff time
Note: broadcast is not acknowledged
17
802.11 - CSMA/CA unicast
Sending unicast packets
station has to wait for DIFS before sending data receiver acknowledges at once (after waiting for SIFS) if the packet was received correctly (CRC) automatic retransmission of data packets in case of transmission errors
DIFS data sender
SIFS
ACK receiver other stations
DIFS waiting time
Contention window
The ACK is sent right at the end of SIFS
(no contention) data t
18
802.11 – DCF with RTS/CTS
Sending unicast packets
station can send RTS with reservation parameter after waiting for DIFS
(reservation determines amount of time the data packet needs the medium) acknowledgement via CTS after SIFS by receiver (if ready to receive) sender can now send data at once, acknowledgement via ACK other stations store medium reservations distributed via RTS and CTS sender receiver
DIFS
RTS
SIFS
CTS
SIFS data
SIFS
ACK other stations
NAV: Net Allocation Vector
NAV (RTS)
NAV (CTS) defer access
DIFS data t
Contention window
RTS/CTS can be present for some packets and not for other
19
Fragmentation mode
sender
DIFS
RTS
SIFS
CTS
SIFS receiver frag
1
SIFS
ACK
1
SIFS frag
2
SIFS
ACK
2
NAV (RTS)
NAV (CTS) other stations
NAV (frag
1
)
NAV (ACK
1
)
DIFS contention data t
• Fragmentation is used in case the size of the packets sent has to be reduced (e.g., to diminish the probability of erroneous frames)
• Each frag i
(except the last one) also contains a duration (as RTS does), which determines the duration of the NAV
• By this mechanism, fragments are sent in a row
• In this example, there are only 2 fragments
20
802.11 – Point Coordination Function (1/2)
t
0 t
1
SuperFrame medium busy
PIFS point coordinator wireless stations stations‘
NAV
D
1
SIFS
U
1
SIFS
NAV
D
2 contention free period
SIFS
U
2
SIFS
• Purpose: provide a time-bounded service
• Not usable for ad hoc networks
• D i
• U i represents the polling of station i represents transmission of data from station i
21
802.11 – Point Coordination Function (2/2)
t
2 t
3 t
4 point coordinator wireless stations stations‘
NAV
D
3
PIFS
D
4
SIFS
NAV
U contention free period
4
SIFS
CF end contention period t
• In this example, station 3 has no data to send
22
802.11 - MAC frame format
Types
control frames, management frames, data frames
Sequence numbers
important against duplicated frames due to lost ACKs
Addresses
receiver, transmitter (physical), BSS identifier, sender (logical)
Miscellaneous
sending time, checksum, frame control, data bytes
2
Frame
Control
2
Duration
ID
6
Address
1
6
Address
2
6
Address
3
2
Sequence
Control
6
Address
4
0-2312
Data
4
CRC version, type, fragmentation, security, ...
detection of duplication
23
MAC address format
scenario ad-hoc network infrastructure network, from AP infrastructure network, to AP infrastructure network, within DS to DS from
DS
0
0
0
1 address 1 address 2 address 3 address 4
DA
DA
SA
BSSID
BSSID
SA
-
-
1
1
0
1
BSSID
RA
SA
TA
DA
DA
-
SA
DS: Distribution System
AP: Access Point
DA: Destination Address
SA: Source Address
BSSID: Basic Service Set Identifier
- infrastructure BSS : MAC address of the Access Point
- ad hoc BSS (IBSS): random number
RA: Receiver Address
TA: Transmitter Address
24
802.11 - MAC management
Synchronization
Purpose
for the physical layer (e.g., maintaining in sync the frequency hop sequence in the case of FHSS)
for power management
Principle: beacons with time stamps
Power management
sleep-mode without missing a message periodic sleep, frame buffering, traffic measurements
Association/Reassociation
integration into a LAN roaming, i.e. change networks by changing access points scanning, i.e. active search for a network
MIB - Management Information Base
managing, read, write
25
Synchronization (infrastructure case)
beacon interval access point medium
B B B busy busy busy value of the timestamp
B beacon frame busy
B t
• The access point transmits the (quasi) periodic beacon signal
• The beacon contains a timestamp and other management information used for power management and roaming
• All other wireless nodes adjust their local timers to the timestamp
26
Power management
Idea: switch the transceiver off if not needed
States of a station: sleep and awake
Timing Synchronization Function (TSF)
stations wake up at the same time
Infrastructure case
Traffic Indication Map (TIM)
list of unicast receivers transmitted by AP
Delivery Traffic Indication Map (DTIM)
list of broadcast/multicast receivers transmitted by AP
Ad-hoc case
Ad-hoc Traffic Indication Map (ATIM)
announcement of receivers by stations buffering frames more complicated - no central AP collision of ATIMs possible (scalability?)
27
Power saving (infrastructure case)
Here the access point announces data addressed to the station
TIM interval DTIM interval access point medium station
D B busy busy
T
T
TIM
D
DTIM busy
T p awake d d busy
D B t
B broadcast/multicast d data transmission to/from the station p Power Saving poll: I am awake, please send the data
28
802.11 - Roaming
No or bad connection? Then perform:
Scanning
scan the environment, i.e., listen into the medium for beacon signals or send probes into the medium and wait for an answer
Reassociation Request
station sends a request to one or several AP(s)
Reassociation Response
success: AP has answered, station can now participate failure: continue scanning
AP accepts Reassociation Request
signal the new station to the distribution system the distribution system updates its data base (i.e., location information) typically, the distribution system now informs the old AP so it can release resources
29
Security of 802.11
WEP: Wired Equivalent Privacy
Objectives:
Confidentiality
Access control
Data integrity
Integrity checksum
M
C(M)
P = M C(M) k
IV RC4 k
IV RC4
P = M C(M)
Note: several security weaknesses have been identified
30
The new solution for 802.11 security: standard 802.1x
EAPOL
(over Ethernet or 802.11)
Encapsulated EAP,
Typically on RADIUS
Supplicant
Authenticator
EAP: Extensible Authentication Protocol (RFC 2284, 1998)
EAPOL: EAP over LAN
RADIUS: Remote authentication dial in user service (RFC 2138, 1997)
Authentication Server
Features:
- Supports a wide range of authentication schemes, thanks to the usage of EAP
- One-way authentication
- Optional encryption and data integrity
31
More on IEEE 802.1x
Example of authentication, using one-time passwords (OTP):
Supplicant Authenticator
EAP-request/identity
Authentication server
EAP-response/identiy (MYID)
EAP-request/OTP,
OTP challenge
EAP-response/OTP,
OTPpassword
EAP-success
Authentication successfully completed
Port authorized
: exchange of EAPOL frame
: exchange of EAP frames in a higher layer protocol (e.g., RADIUS)
Notes :
1.
Weaknesses have been found in 802.1x as well, but are corrected in the various implementations.
2.
New standard in the making : IEEE 802.11i
32
IEEE 802.11 – Standardization efforts
IEEE 802.11b
2.4 GHz band
Bitrates 1 – 11 Mbit/s
IEEE 802.11a
5 GHz band transmission rates up to 54 Mbit/s close cooperation with BRAN (ETSI Broadband Radio Access Network)
Coverage is not as good as in 802.11b
IEEE 802.11g
Available since 2003, highly popular
2.4 GHz band (same as 802.11b)
Bitrates up to 54Mb/s
IEEE 802.11i
Security, makes use of IEEE 802.1x
IEEE 802.11p
For vehicular communications
IEEE 802.11s
For mesh networks
+ many other…
33
ETSI - HIPERLAN
ETSI standard
European standard, cf. GSM, DECT, ...
Enhancement of local Networks and interworking with fixed networks integration of time-sensitive services from the early beginning
HIPERLAN family
HIPERLAN 1 standardized since 1996
HIPERLAN 2 under standardization
Very uncertain future: few products available so far…
34
Conclusion on Wireless LANs
IEEE 802.11
Very widespread
Often considered as the system underlying larger scale ad hoc networks (although far from optimal, not designed for this purpose)
Tremendous potential as a competitor of 3G cellular networks in hot spots
Hiperlan
Too ambitious standard?
Bluetooth
Products available
Not as successful as initially thought
Security perceived as a major obstacle; initial solutions were flawed in both IEEE 802.11 (WEP) and Bluetooth
Future developments
Ultra Wide Band?
35
References
J. Schiller: Mobile Communications, Addison-Wesley, Second Edition,
2004
Leon-Garcia & Widjaja: Communication Networks, McGrawHill, 2000
IEEE 802.11 standards, available at www.ieee.org
www.bluetooth.com
J. Edney and W. Arbaugh: Real 802.11 Security, Addison-Wesley,
2003
36