SHA-1
advertisement

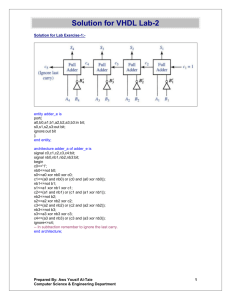
SHA-1 Secure Hash Algorithm 1 SHA-1 – Brief Introduction 家族是美國國家安全局 (NSA) 設計,美國國家 標準與技術研究院 (NIST) 發佈的一系列密碼雜 湊函數,發表於1993年 從一個最大 264 位元的訊息中產生一串 160 位 元的摘要 設計 MD4 及 MD5 訊息摘要演算法的 MIT 教 授 Ronald L. Rivest 類似的原理為基礎來加 密 SHA-1 – Definitions of Bit Strings and Integers Hex Digit為16進位,可用4-bit的string表現 7 = 0111, A = 1010 一個word可表示成32-bit的string,而每4-bit就 等同一個Hex Digit 1010 0001 0000 0011 1111 1110 0010 0011 = A103FE23. 一個介於0到232-1的數字也可以轉換成16進位,而成 為八位的Hex Digit 當一整數232<= Z? Block = 512-bit string. 所以一個Block可以 代表16個words所組成的序列. SHA-1 – Operations on Words AND , OR, XOR, NOT The operation X + Y (where 0 <= x < 232 and 0 <= y < 232.) The circular left shift operation Sn(X) SHA-1 – Message Padding 在字串後面增加“1”. “01010000”,進行此步驟後會變成 “010100001” “0”的填置. 01100001 01100101 61626364 00000000 00000000 00000000 01100010 01100011 (1). 65800000 00000000 00000000 00000000 00000000 00000000 00000000. 01100100 00000000 00000000 00000000 如果string長度小於232如上例 l = 40 Hex過後將變成00000000 00000028. 而完成的sequence就被之後當成M(n)使用 SHA-1 – Functions and Constants Used 在SHA-1裡方程式f (0), f (1)……f (79) 每一個方程式解as a 32-bit word as output f (t;B,C,D) F (t;B,C,D) ( 0 <= t <= F (t;B,C,D) F (t;B,C,D) AND D) F (t;B,C,D) = (B AND C) OR ((NOT B) AND 19) = B XOR C XOR D (20 <= t <= = (B AND C) OR (B AND D) OR (40 <= t <= 59) = B XOR C XOR D (60 <= t <= D) 39) (C 79). A sequence of constant words K(0), K(1), ... , K(79) is used in the SHA-1. In hex these are given by K K K K (t) (t) (t) (t) = = = = 5A827999( 0 6ED9EBA1(20 8F1BBCDC(40 CA62C1D6(60 <= <= <= <= t t t t <= <= <= <= 19) 39) 59) 79). SHA-1 – Computing the Message Digest Before processing any blocks, the H’s are initialized as follows: in hex, H0 H1 H2 H3 H4 = = = = = 67452301 EFCDAB89 98BADCFE 10325476 C3D2E1F0. SHA-1 – Computing the Message Digest MASK = 0000000F. Then processing of M(i) is as follows: a. Divide M(i) into 16 words W[0], ... , W[15], where W[0] is the left-most word. b. Let A = H0, B = H1, C = H2, D = H3, E = H4. SHA-1 – Computing the Message Digest c. For t = 0 to 79 do s = t AND MASK; if (t >= 16) W [s] = S1 (W [(s + 13) AND MASK] XOR W [(s + 8) AND MASK] XOR W [(s + 2) AND MASK] XOR W [s]); TEMP = S5 (A) + f (t;B,C,D) + E + W [s] + K (t); E = D; D = C; C = S30(B); B = A; A = TEMP; d. Let H0 = H0 + A, H1 = H1 + B, H2 = H2 + C, H3 = H3 + D, H4 = H4 + E. SHA-1 – graph SHA-1 – code (Initialize variables:) a = h0 = 0x67452301 b = h1 = 0xEFCDAB89 c = h2 = 0x98BADCFE d = h3 = 0x10325476 e = h4 = 0xC3D2E1F0 (Pre-processing:) paddedmessage = (message) append 1 while length(paddedmessage) mod 512 <> 448: paddedmessage = paddedmessage append 0 paddedmessage = paddedmessage append (length(message) in 64-bit format) (Process the message in successive 512-bit chunks:) while 512-bit chunk(s) remain(s): break the current chunk into sixteen 32-bit words w(i), 0 <= i <= 15 (Extend the sixteen 32-bit words into eighty 32-bit words:) for i from 16 to 79: w(i) = (w(i-3) xor w(i-8) xor w(i-14) xor w(i-16)) leftrotate 1 (Main loop:) for i from 0 to 79: temp = (a leftrotate 5) + f(b,c,d) + e + k + w(i) (note: all addition is mod 2^32) where: (0 <= i <= 19): f(b,c,d) = (b and c) or ((not b) and d), k = 0x5A827999 (20 <= i <= 39): f(b,c,d) = (b xor c xor d), k = 0x6ED9EBA1 (40 <= i <= 59): f(b,c,d) = (b and c) or (b and d) or (c and d), k = 0x8F1BBCDC (60 <= i <= 79): f(b,c,d) = (b xor c xor d), k = 0xCA62C1D6 e = d d = c c = b leftrotate 30 b = a a = temp h0 =