PAPER TITLE (UP TO 6 INCHES IN WIDTH AND CENTERED,
advertisement

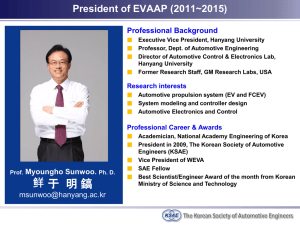
US14-GASKA EXPLORING SECURITY SYNERGIES IN DRIVERLESS CAR AND UAS INTEGRATED MODULAR ARCHITECTURES (IMAS) Thomas D. Gaska* There is a future opportunity to leverage COTS security technology being developed for the driverless car into future Unmanned Air System (UAS) Integrated Modular Architectures (IMAs). Infrastructure and Information Security are critical issues in networked UAS team configurations with increasing degrees of autonomy and collaboration. Key university and automotive industry level research is underway toward addressing similar challenges of information and infrastructure security in solutioning the driverless car by 2020 1. Information security is typically associated with Information Assurance (IA) and infrastructure security is typically associated with Tamper Resistant Computing. Both of these security infrastructures need to be properly addressed and incrementally extended to enable future levels of autonomy. This paper identifies the emerging parallels in driverless car and UAS security challenges, describes advanced security initiatives being explored for the automotive industry, and then provides a starting context for alignment of these initiatives into a cross domain view for synergy analysis between driverless cars and UAS platforms. INTRODUCTION A recent publication from the author developed an initial taxonomy for dual use analysis of driverless car security in avionics IMAs including the UAS subset 2. This paper extends that taxonomy with additional automotive research security programs and also provides additional focus on derivative embedded security product trends. This paper is organized as follows: 1.) Common Security Challenges – UAS and Driverless Cars 2.) Dual Use Security Taxonomy 3.) Automotive Industry Security Initiatives Mapped to Potential UAS Relevance 4.) Future Embedded Security Product Directions 5.) Conclusions * Principal Systems Engineer, Lockheed Martin MST, Owego, NY, 13927 & PhD Student at Binghamton University 1 COMMON SECURITY CHALLENGES – UAS AND DRIVERLESS CARS Common security challenges for manned/unmanned avionics IMAs and driverless cars include: Increased cooperative platform autonomy => Mixed capability management and levels of autonomy o Need to cooperate with less and more capable manned systems with goal of optionally piloted capability Connectivity to the Cloud and GIG => Every platform will interact as a sensor for situation awareness o Need to offload system-of-system management to an adhoc, trusted infrastructure Connectivity within the platform for storage and onboard/offboard services at multiple trust levels => Multiple Levels of Security o Need Multiple security domains within and across the platforms Protection of critical program information and tamper resistance => Trusted Computing Elements o Need to balance open architecture and enforce trust Increase standardization to support collapsing into a common component infrastructure => Next Generation Integrated Modular Avionics (IMA) o Need to leverage Moore’s Law multicore explosion while maintaining safety and security Increase cross platform reuse => Domain standardization initiatives o Need Hardware agnostic software components and uniform software interfaces Affordability consistent with the threat, policy, and customer => Early demonstration of advanced solution capability for acceptance/validation o Need for incremental technology insertion across a wide range of affordability targets Just as in the future UAS platforms, the driverless car will be part of a community of interest based Internet Systems-of-Systems architecture. The community of interest for the driverless car will be a node on the VehiculAR InterNETworking (VANET) infrastructure. The VANET infrastructure will need to address at the platform level security elements shown in Figure 1 and will need to address mixed levels of trust with safety critical elements, security critical elements and general purpose infotainment systems 3. Structured research programs like Secure Vehicle Communications (SEVECOM) and many others described in this paper are exploring vehicle security architectures with innovative hardware and software components, standards, and topologies. 2 Figure 1. Driverless Car Security Components 3. Similar to future UAS platform focus, affordability will direct the driverless car architecture toward Integrated Modular Avionics (IMA) and cross platform/domain reuseable software component approaches. The complexity and throughput requirements of the driverless car will need to leverage IMA common infrastructure building blocks that can easily scale across product lines. A representative subsystem view of the Driverless car functional complexity that drives an IMA platform approach is shown in Figure 2 3. This architecture is very comparable to a UAS platform with complex sensors, multiple communication links, onboard/offboard processing, and scalable capabilities. The driverless car security architecture needs to support selected trusted interactions with the cloud infrastructure, the driver operator interface, onboard passengers mobile interfaces, the platform itself, other vehicles, maintenance and repair interfaces, infotainment, and national transportation safety/security infrastructure. 3 Figure 2. Representative Driverless Car as an IMA. DUAL USE SECURITY TAXONOMY The derived dual use security taxonomy used for this paper includes the following classification categories for research focus that can be relevant to both driverless car and UAS security. The taxonomy attempts to map avionics including UAS, into Information Assurance and Trusted Processing Components. Those components are then mapped into relevant terminology used in university research and into advanced automotive security research initiatives. This taxonomy includes: 1. Cloud (public, private, hybrid) to Platform Exchanges 2. Platform to Platform Exchanges 3. Off-board Communication Security 4. Platform Storage Security 5. Platform Network Security 6. Embedded Processing Node SW/HW Security 7. Platform Application/Infrastructure Software A high level mapping of this taxonomy and its relationship from UAS avionics to leverage university and automotive security industry focus is provided in Table 1. The author’s previous paper on this subject developed the rationale for the taxonomy listed 2. The focus of this paper is to extend the automotive security industry focus to include additional research activities and how those initiatives are influencing industry security component development. Representative Infor- 4 mation Assurance and Trusted Processing component development for driverless cars is shown in Ошибка! Источник ссылки не найден. and Ошибка! Источник ссылки не найден. respectively. Figure 3 shows an example of the advanced automotive information security architecture elements required that can be explored for dual use3. Figure 4 shows an example of the advanced automotive trusted computing security architecture elements can be explored for dual use 4 . The next section summarizes some of the key automotive security research focus activities mapped into this taxonomy. These automotive security initiatives are developing requirements, performing trade studies, developing demonstration systems, and establishing standards/specifications/acceptance for security components in an open environment. Table 1. Proposed Taxonomy for Assessment of Dual Use Security. 5 Figure 3. Representative Driverless Car Information Assurance Mechanisms 3. Figure 4. Representative Driverless Car Trusted Processing Mechanisms 3. 6 INDUSTRY/UNIVERSITY SECURITY INITIATIVES MAPPED TO POTENTIAL UAS RELEVANCE This section provides an overview of the automotive industry/university security initiatives that are exploring solutions with potential dual-use relevance to next generation UAS systems. Secure Vehicle Communications (SeVeCOM) Description: European initiative, started in 2005, to address security challenges of V2X external communication. Taxonomy Focus Level 2 – Platform-to-Platform Exchanges: Privacy-preserving trustworthy V2X communication use case development, protocol development, and architecture development Web: http://www.sevecom.org/ CAR2CAR Communications Consortium Description: European initiative, started in 2008, to develop a path forward for Cooperative Intelligent Transport Systems (C-ITS) including development of specifications for Vehicle to Infrastructure (V2I), Vehicle to Vehicle (V2V) and facilitating proof-of-concept implementations. Taxonomy Focus Level 2 - Platform to Platform Exchanges: Focus on automation to avoid accidents using platform V2V exchanges Web: http://www.car-to-car.org/ PREparing SEcuRe Vehicle-to-X Communication Systems (PRESERVE) Description: European initiative to research future vehicular communication modes and types: Car-to-car, car-to-nomadic device, and Car-to-infrastructure. Taxonomy Focus Level 2 - Platform to Platform Exchanges: Systems communication hierarchy analysis and protocols Web: http://www.preserve-project.eu/ Open VEhiculaR SEcurE platform (OVERSEE) Description: European initiative, started in 2012, focused on researching security elements for a next generation, networked connected vehicle. Research included requirements analysis, platform design, platform implementation, and proof of concept for security infrastructure. Taxonomy Focus Level 6 - Embedded Processing Node HW/SW Security: Use cases, virtualized I/O service definition, communications analysis, and Hardware Security Module (HSM) definition. Web: https://www.oversee-project.com/ E-safety Vehicle InTrusion protected Applications (EVITA) Description: European initiative, started in 2008, to design, verify, and prototype building blocks for secure automotive on-board networks protecting security-relevant components against tampering and sensitive data against compromise. Taxomony Focus Level 6 - Embedded Processing Node HW/SW Security: Hardware Security Module (HSM) with three levels of hierarchy (Full, Medium, Lite) for establishing platform trust as shown in Ошибка! Источник ссылки не найден.. Web: http://evita-project.org/ 7 System Security (SysSec) Description: European research initiative, started in 2012, to develop solutions for managing threats and vulnerabilities in the future Internet, The relevant report here was an Intermediate Report on the Security of the Connected Car. Taxonomy Focus Level 1 to 7: SysSec is part of a larger focus across embedded domains to protect against Internet of Things (IoTs) security challenges. This same view will be required with the DoD directive to connect every system to the Internet in the 2020 vision. Web: http://www.syssec-project.eu AUTomotive Op Systems ARchitecture (AutoSAR) Description: Worldwide development partnership of car manufacturers, suppliers and other companies from the electronics, semiconductor and software industry focused on a common modular architecture. Taxonomy Focus Level 7 - Software Components: AutoSAR can provide a potential direct access for leveraging selected interoperable automotive standards for software components and model driven design framework. AutoSAR provides a global product line reference example for common solutions and a model for plug and play vendor agnostic complex software system. Web: http://www.autosar.org/ SAE Vehicle Electrical System Security Committee Description: SAE initiative to evaluate challenges and technical solutions and draft standards and best practices to help ensure the safety of vehicle electronic control systems and safeguards against cyber-security threats in current and future motor vehicles Taxonomy Focus Levels 1 to 7 – Standards: SAE automotive initiatives will address many of the same security tradeoffs as for UAS with regard to when the threat drives a new solution enhancement or when vulnerability needs to be addressed as across the industry. Web: www.SAE.org EURO-MILS: Architecture Description: European research initiative, stared in 2012, to mature secure virtualization technology for trustworthy applications in support of critical domains. A MILS solution will provide strong guarantees for isolation of resources by means of Common Criteria certification along with usage of formal methods. Taxonomy Focus Level 6 - Embedded Processing Node HW/SW Security: MILS technology is a key enabler for next generation UAS enhanced domain separation achieving improved SWAP with extensions to multicore MILS. Web: http://www.euromils.eu/ Embedded Security in Cars (ESCAR) Description: Forum for collaboration among private industry, academia, and government regarding modern in-vehicle cyber security threats, vulnerabilities, and risk mitigation/countermeasures. This forum provides the opportunity for information exchange, networking, and collaboration among your peers and a forum to define research needs. Taxonomy Focus Levels 2 to 7 - Security Research: Provides forum for UAS dual use monitoring and access to mainstream automotive market security research and standards. 8 Web: https://www.escar.info/ Center for Automotive Embedded System Security Description: Collaboration between researchers at the University of California San Diego and Washington University, started in 2009, to address security, privacy, and safety of future automotive embedded systems Their classic work on Comprehensive Experimental Analyses of Automotive Attack Surfaces was presented at the USENIX Security Symposium in August 2011 and showed the current security vulnerabilities in current automotive products 5. Taxonomy Focus Levels 3 to 6 – Vulnerabilities: CAES like research testbeds provide focused insight into system vulnerabilities and are “poster childs” for the meed for improved platform information and infrastructure security. Web: http://www.autosec.org/ Secure & Interconnected Mobility: Integrated Security for Mobile, Automotive, and Cloud Computing Description: Intel/University initiative focused on addressing the car ecosystem, secure system software, and hardware trust anchor and privacy primitives. Taxonomy Research Focus: Intel/University initiatives that address security from the cloud to the platform are critical to future system-of-system challenges. Web: http://www.icri-sc.org EMBEDDED SECURITY PRODUCT DIRECTIONS Mainstream driverless car architecture analysis, research, and industry directions will have direct relevance on the availability of low cost, affordable embedded security solutions that can accept the level of proliferation and residual vulnerabilities. This section provides some examples of how the previous automotive security programs are driving industry solutions. At the same time, there are cost, scalability, and residual vulnerability tradeoffs that will drive their suitability within Information Assurance, Trusted Computing, and Trusted Application Software components when applied to UAS platforms. Infrastructure Communication Networks Based on identification of automotive security needs, companies are starting to incorporate network infrastructure products with automotive community of interest protocol support for secure network gateways. These gateways will have multicore processing capable of performing intrusion detection and supporting application firewalls, and providing hardware accelerated cryptographic services. Virtualization and Multicore The automotive industry is recognizing that virtualization and multicore are critical enablers to affordable automobiles that will contain 20 million lines of code. It is no longer possible to procure dedicated blackbox hardware with every dedicated software application. An IMA based approach for shared processing clusters will become the norm. The incorporation of security into the IMA platform will benefit from the research programs to date and are focused on supporting AutoSAR like initiatives. 9 Multiple Levels of Security Secure Microcontroller Operating Systems companies like Green Hills are already talking about the need for Multiple Independent Levels of Security Operating System (MILS OS) technology in the automobile as is EURO-MILS. This will be necessary to avoid physically separate networks for infotainment, safety critical, security critical, and base infrastructure to enable third party servicing and repair. Multiple Levels of Tamper Resistant Controllers Companies like Bosh and Infineon are already adopting Hardware Security Module (HSM) capabilities into their automotive microcontrollers that was originally derived and demonstrated in the EVITA program shown in Ошибка! Источник ссылки не найден.. Automotive microcontrollers are also being enhanced to support redundant physical processing channels. Secure Software APIs Companies derived from automotive security research are now exploring extensions to AutoSAR to include security service APIs to ensure interoperability in security operations. These services include both network gateway services and crypto services. There is Not One Solution - Residual Vulnerability versus Cost The cloud, avionics both manned and UAS, and automotive domains will all require proper security analysis and updates to defense-in-depth. Proper threat and vulnerability security analysis will be critical to incorporating protections based on the threat, likely of occurrence, and the cost required. For both driverless cars and avionics, there are a range of solutions include the following components from the earlier taxonomy both future avionics and emerging automotive architectures: 1. Information Assurance Components HW/SW Network Intrusion Detection Systems HW/SW Cross Domain Solutions HW/SW Trusted Workstations and Operator Interfaces HW/SW Network Infrastructure Security Protocols 2. HW/SW Virtualization Trusted Computing Components Trusted FPGAs with Security Secure Microcontrollers Trusted Processor Modules (TPMs) with HW Virtualization Secure Microprocessors 3. Trusted Application Components Model Based with Trusted Synthesis Checked via Formal Proofs, Static and Dynamic Code Analysis APIs for access to hardware crypto acceleration University Focus in Protecting Embedded Systems Many of the automotive security initiatives listed strongly leverage university research in cooperation with industry. The level of research in security at the university level for embedded system security also has increased exponentially with similar needs for medical and critical infra- 10 structure security driving research. A future publication will analyze centers of excellence by taxonomy. CONCLUSIONS Ошибка! Источник ссылки не найден. illustrates a summary of the parallel domain security extensions being driven by automotive industry and avionics industry initiatives. At this time, the driverless car and automotive industry have the benefit of focused research programs, large business cases, and a strong market pull for spiral mobile and networked solutions. At the same time the driverless car initiative has the challenge of market acceptance based on safety, regulation, and affordability, funding availability, and interest. There will not be many second chances before trust is broken if autonomy is inserted without proper security and safety, As UAS systems widen their penetration into civil security and industrial applications, information security, and infrastructure security will be key drivers across a much larger market space. In additional the driverless car market will evolve through spiral of ever increasing autonomy and add more unified interoperable architectures. This paper did not explicitly address IMA in the large but focused on security for an IMA based system. A recent publication by this author described the next generation COTS industry trends likely to influence next generation IMA hardware and software 6. A second publication by this author described the potential impacts of cloud computing, smart phone packaging/electronics accelerating Moore’s law, and driverless autonomy software codesign environments on IMA architecture decisions going forward 7. Figure 6 is an extension of those thoughts with regard to next generation IMA security architecture evolution in avionic platforms including UAS. Part of the challenge is to extend terms like IMA into the automotive system architecture with common hardware software and hardware building blocks. In the future, the block diagram for an avionics system and an automobile will be more similar than different. Cost challenges on the automobile will force more consolidation to common hardware and software building blocks with additional network unification. Insertion of automotive security technology will likely first occur in Class 1 and Class 2 UAS platforms where embedded controllers are the core of the architectures and mixed networking includes CAN and Ethernet. One of the challenges for UAS and avionics is that we don’t have the same level of public research and industry collaboration opportunities. Efforts to collaborate on UAS reams have often focused on information sharing to support community of interest teaming 8.To fill part of this gap, it is the future plan of this author to continue to explore the potential dual use security opportunities being driven by the driverless car into the UAS domain in PhD system architecture research, Effort at the system architecture level will enable greater understanding of future potential synergies by using a common framework without getting too deep in one detail to support tradeoffs in using adjacent market, dual use technology. 11 Figure 5. Parallel Domain Security Extensions. Figure 6. Future UAS IMA Decisions. 12 CONCLUSIONS 1 Gaudin, Sharon, 2012, Autonomous cars will arrive within 10 years, Intel CTO says, Computerworld, Web Page, 2 Gaska, T., 2013, Assessing Dual Use Embedded Security for IMA, Syracuse, NY, DASC 2013 Groll, André, Jan Holle, Marko Wolf, Thomas Wollinger, 2010, Next Generation of Automotive Security: Secure Hardware and Secure Open Platforms, ITS World 2010 3 4 Kumar, S., S. Gollakota, D. Katabi, 2012, A Cloud-Assisted Design for Autonomous Driving, MIT 5 Koscher, Carl, Alexei Czeskis, Franziska Roesner, Shwetak Patel, Tadayoshi Kohno, Stephen Checkoway, Damon McCoy, Brian Kantor, Danny Anderson, Hovav Shacham, and Stefan Savage, 2010, Experimental Security Analysis of a Modern Automobile, Oakland 2010 6 Gaska, T., 2012, Leveraging Emerging Embedded Processing Trends In Rotorcraft Advanced Open System Architectures (AOSA), Fort Worth, Tx, .American Helicopter Society Forum 68 7 Gaska, T., 2013, Selecting Components, Standards, and Topologies for Next Generation Integrated Modular Avionics (IMA) Architectures, Phoenix, Az, American Helicopter Society Forum 69 8 Gaska, T., 2008, Airborne Platform CONOPS and Net-Centric Processing Extensions to Support Next Generation Tactical Manned/Unmanned Teaming” – Association of Unmanned Vehicle International (AUVSI), North America 2008, Poster Session The organization initiatives for automotive research have their inline web addresses provided for convenience in Section 4 of the paper. The level of information presented is available from their website home page. Each web site has numerous publication and presentations listed for further investigation. 13