Invitation - Blogs @ Butler

Tyler Pollock
Cryptography Invitation
The object of this invitation is to address
Standards Addressed
INTASC Mathematics
A2.2.2 Use substitution, elimination, and matrices to solve systems of two or three equations in two or three variables.
DM.2.1 Use matrices to organize and store data.
DM.2.2 Use matrix operations to solve problems.
DM.2.4 Use the inverse of a matrix to solve problems.
Annotated Bibliography
Hill cipher. Wikipedia: The Free Encyclopedia. 6 December 2011, from http://en.wikipedia.org/wiki/Hill_cipher
Leon, Steven J. (1994) Linear Algebra with Applications. New York: Macmillan College Publishing
Company, Inc.
Neal, Dr. David. Cryptography with Matrices. Western Kentucky University. Retrieved 7 December
2011, from http://www.wku.edu/~david.neal/307/Crypt.pdf
Steven Leon’s book will be used as a guide for the mathematical operator of multiplication. Section 1.3 explains the procedure of using dot products to multiply matrices. Section 1.4 teaches how to make the inverse of a non-singular matrix. These are the three components of math that will be used in this invitation.
The two websites above are to be used to explore how matrices are used to form encoded messages.
They show how to use non-singular matrices to encrypt a message. Then explain how to use the inverse of the encryption matrix (called decryption matrix) to then decode the message. This process uses the mathematical operator of matrix multiplication.
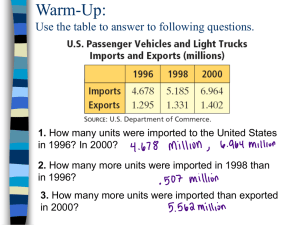
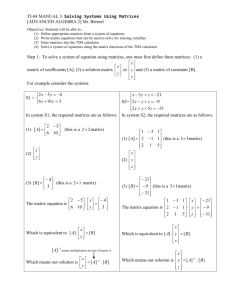
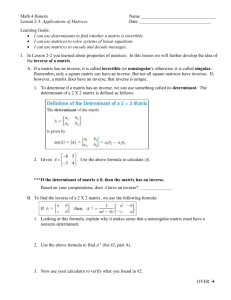
Warm-up.
Use your textbook as a guide for solving the following problems. If you feel like you don’t need any more practice, continue on to Engagement 1.
1.
(
3 2
−1 −2
) ( 𝑥
7 𝑦) = ( −9
)
2.
(
1 2
3 4
) ( 𝑥 𝑦) = (
5
11
)
3.
(
−2 6
1 1
) ( 𝑥 𝑦) = (
0
4
)
4.
(
7 1
2 3
) (
1 −2
8 9
)
2 0 −1
5.
( 1 2 6
2 1 1
8 5 0
) ( 3 0 7 )
7 1 2
Engagement 1
Try to figure out what this code says. Try as many different ways as you possibly can. When you think you have the decrypted message, check your answer with a classmate. If you have different answers, go back and try it again. If you can’t crack the code in 10 minutes, continue onto Engagement 2.
Hint: 𝐴 −1 =
0
−
1
1
4
( 2
1
−
2
1
4
−
1
1
2
0 −
1
2 )
Code: 97 91 65 56 68 50 81 87 57
Engagement 2
Use the following websites to discover how to use matrices to send an encrypted message:
http://www.wku.edu/~david.neal/307/Crypt.pdf
http://en.wikipedia.org/wiki/Hill_cipher
Using the Hill cipher, encrypt the message “ILOVEMATH” with encryption matrix A:
1 2 3
𝐴 = ( 3 2 1 )
1 2 1
Discuss this method of writing encrypted messages with a classmate. What do you like about it? What don’t you like?
Engagement 3
Look up the following questions on the internet. These questions are just a guide. If you find something interesting that is related to one of these questions, write a bit about that.
When was the Hill cipher used and why was it important?
How is the Hill cipher connected the Enigma machine? What was the effect of the Enigma machine in
WWII?
What other uses for matrices can you find? Are they used in other jobs other than the military?
Engagement 4
Create your own encrypted message using your own encryption matrix. Send an encrypted message to a classmate along with the encryption matrix. Your classmate will use his calculator to compute the decryption matrix (inverse of encryption matrix). Have your classmate decrypt the message. If they get it successfully, come show me.