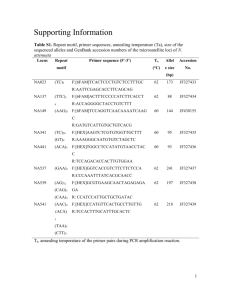
Ned Einsig Lab 2
advertisement

Lab 2 Ned Einsig III SRA 221 2/20/15 Section 1 The stated objectives of the project are to encrypt and decrypt messages using a hex editor and AES algorithm. It is also to capture secret sent messages using Wireshark from classmates. Having already used Wireshark in both academic and work environments my goal in this lab is to find out how the application and cryptography go together. I would also like to gain a better understanding of the Cryptography going on in the background. I’m not the best at math, so maybe I’ll also get a better grip on the math behind this while I’m at it. Section 2 Task 1 a. Describe what was done in Task 1 and analyze your results. In this part of the lab I viewed examples of Sub Bytes, Shift rows, Mix Columns, Add Round Key, and Key schedule. I got to see how it all comes together to form an encrypted message. Task 2 a. Describe what was done in Task 2 and analyze your results. In task 2 I made an Empathy IM Client account and changed my alias to nle5045. I was able to see a few of my classmate’s up on the chat box. (Kind of surprising for 10pm on a Friday night) Task 3 a. Describe what was done in Task 3 and analyze your results. In this step I set up a message and got to see what it looked like in HEX. 20 for example is a black space. Now when I see %20% in place of spaces in URL’s I’ll know why. b. Be sure to include a screenshot of your encrypted Bless message. (Step 2) Task 4 a. Describe what was done in Task 4 and analyze your results. In this step I got to see what was explained in step 1 in action. I applied a cipher key (b2) to by plaintext HEX and got an output (encrypted text). b. Be sure to include a screenshot of your encrypted message from the Rijndaelinspector. (Be sure to include the cipher key and the output in the screenshot). Since output is difficult to read: 76 66 6f 22 9e b1 94 55 6e d3 8c 5e bd fd ab 36 Task 5 a. Describe what was done in Task 5 and analyze your results. In this section I opened up Wireshark and begun packet capture. Being a small network with only a few devices traffic was minimal. All traffic seems to be of the MDNS protocol (Multicast DNS) going out to multiple hosts. Task 6 a. Describe what was done in Task 6 and analyze your results. In this step I sent the message in HEX along with the Cipher (b2). Task 7 a. Describe what was done in Task 7 and analyze your results. In task 7, also part of the picture above, I decrypted a message from a classmate. To do this I entered their HEX into Rijndaelinspector and entered the output into Bless. This HEX converted into characters and numbers to see the hidden message. Task 8 a. Describe what was done in Task 8 and analyze your results. In this step I intercepted Wireshark TCP packets with chat information (longer length) and read them for information to intercept and decrypt. I wasn’t too happy with the results of my first run through so I tried a few runs of the process. Figured out I was doing the ordering wrong. b. Be sure to include a screenshot of the Wireshark detection of an encrypted message. (Step 2) Cipher Text Message: 0A EA 3E 35 3C 7C 1F 50 D6 59 B9 2C E4 D2 B7 D7 Key: 88 Output: 48 69 2C 20 49 53 54 32 32 31 3F 20 42 79 65 21 Hi, IST221? Bye! c. Be sure to include a screenshot of the message you decrypted from the Rijndael inspector from your unsuspecting classmate. (Step 3)

![%SYS-3-OVERRUN : Block overrun at [hex] (red zone [hex])](http://s3.studylib.net/store/data/007301636_1-ac70f3209bae6dd18e3a1bf696206cf5-300x300.png)