the Presentation
advertisement

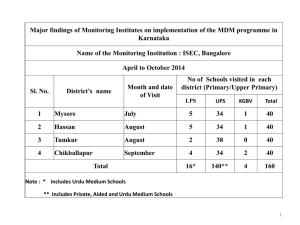
ZIXCORP The BYOD Tug-of-War: Security versus Privacy Neil Farquharson January, 2015 1 ABOUT ZIXCORP Founded in 1998 as an email encryption company More than 11,000 active customers including: Six divisions of the U.S. Treasury All of the FFIEC U.S. federal financial regulators (incl. FDIC and OCC) The U.S. Securities and Exchange Commission 24 U.S. state financial regulators More than 2,000 U.S. financial institutions 25% of all banks in the U.S. 20% of all hospitals in the U.S. 32 Blue Cross Blue Shield organizations 2 3 BYOD REQUIRES… MDM Mobile Device Management = EMM Enterprise Mobility Management MAM Mobile Application Management MCM Mobile Content Management 4 MOBILE DEVICE MANAGEMENT (MDM) Advantages o Device inventory and management capabilities o Access to multiple platforms from personal or corporate devices o Secure access to corporate data o Support for a wide range of wireless vendors and operating systems o Some data protection with wiping capabilities 5 PROLIFERATION OF MDM VENDORS 6 MDM COMPARISON Source: MOBIwm.com 7 HUNDREDS OF APPLICATIONS 8 MOST POPULAR MOBILE BUSINESS APPS EMAIL, CALENDAR AND CONTACTS Source: BYOD and Mobile Security Report, 2014, Holger Schulze, Information Security Community on LinkedIn 9 MARKET RESPONSE TO BYOD Survey results indicate 45% of respondents report that within the previous 12 months, one or more employees lost a mobile device containing company data InformationWeek’s 2014 Mobile Security Report 3.1 Million smartphones were stolen in the USA during 2013 - sixty per minute Consumer Reports’ Annual State of the Net survey, 2014 72% of respondents say their top mobile security concern is data loss from lost or stolen devices InformationWeek’s 2014 Mobile Security Report 10 MOBILE DEVICE USERS’ FRUSTRATION 11 ADDING TO BYOD CHALLENGES 12 MOBILE SECURITY Trust the Platform or Container Example: EMM Security by Management Trust the App Example: App Wrapper Security by Isolation Trust the Viewer Example: Email Streaming Trust Nothing Example: Virtual Security by Abstraction From Gartner Spectrum of Trust for Mobile Enterprise Design, published April 4, 2014 13 TYPICAL MDM SOLUTION EMAILS ARE RETAINED IN PERMANENT MEMORY 14 ZIXONE SOLUTION EMAILS ARE VIEWED ONLY 15 ACCESSIBLE JAILBREAKING SOFTWARE 16 MDM SECURITY DISASTER OFFLINE PREVENTS WIPE 17 ZIXONE A COMPLETELY NEW PHILOSOPHY Mail Server ZixOne 18 ZixONE app that delivers a view of corporate email, calendar and contacts on mobile devices ZixONE server connects to Exchange or Office365 Efficient, secure protocols deliver information quickly 19 SUMMARY Advantages o Device inventory and management capabilities o Access to multiple platforms from personal or corporate devices o Some data protection with wiping capabilities Disadvantages o o o o Leaves data on the device – exposes offline weakness Loss of employee control and privacy Employee acceptance issues Corporate liability 20