Managing BYOD
advertisement

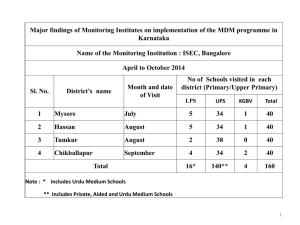
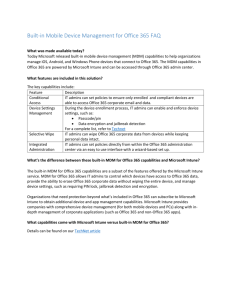
Managing BYOD Legal IT’s Next Great Challenge Agenda The BYOD Trend – benefits and risks Best practices for managing mobile device usage Overview of mobile device management technologies Case Study: Holland & Hart The BYOD Trend – Some History Employee use of company owned computers Using laptops to access the internet Drove usage policies and technology controls RIM Blackberry delivers first mobile device Apple iPhone changes everything BYOD Benefits and Challenges Benefits Improved responsiveness Improved accessibility Greater flexibility Challenges IT support of a wide range of mobile vendors and operating environments Secure access to firm data Mitigate risk of unsecure personal apps 70 million Smartphones lost/stolen in 2011 Only 7% Recovered Source: 2012 Global State of Infosecurity Survey, PriceWaterhouseCoopers 5 17% of businesses Have mobile device breaches Source: Feb 10, 2012 Tabtimes.com, Doug Drinkwater 6 Best Practices Registering devices to insure security: Virus protection, authentication, encryption Provisioning of firm-authorized apps IT use monitoring User education Compliance with firm security policies Mobile Device registration with IT Password protection Use of unsanctioned apps Lost/stolen devices Mobile Device Management IT Control of mobile device usage Enforce authorized and secure access Requires investment, resources and Administration Central server Manages all policies and employee access Provides secure connection to firm data/applications MDM mobile apps for user authentication and control enforcement of third-party apps MDM Functions Mobile app distribution Auto install firm supported apps and updates Policy management User authentication policies Sanctioned and blacklisted apps Inventory management Track employee usage Optimize service plans MDM Functions Security management Block noncompliant devices form the network Password Protection Block specific apps Secure connections to firm data Encryption Require device level encryption MDM secure container encryption MDM Functions Data Loss Prevention Creates secure container on mobile device Custom MDM apps for secure e-mail, calendar and browsers Enforce encryption and selective wipe Control file synchronization Control file access outside secure container File save, print, copy/paste, email attachment Mobile apps outside the secure container MDM Case Study Scott Ainslie, Technical Operations Manager Holland & Hart 12 Real World MDM - History Blackberries to iPhones – How we got here What do we do about it? Protecting the mobile inbox More than just email on phones - Tablets Time entry Documents Intranet/VPN Present Solution Firm issued phone, personal tablet iPhone vs Android – Windows Phone? Firm data requires firm management Mobile Device technology policy Encryption Lock times Certificates Support Official Apps (Time, DM, VPN) Current Projects Network Access Control (NAC/NAP) Enterprise replacement for Dropbox Desktop Virtualization Beyond phones & tablets – laptops Mobilize the Intranet MS Office 2013 - 5 device subscription Q& A 16 Thank you for attending our webinar. If you wish to view this presentation again, please contact us at: sales@biscom.com OR 978-367-3592. Secure Document Delivery Blog On the Web biscomdeliveryserver.com Twitter @biscominc Phone (800) 477-2472 blog.biscom.com Whitepapers Case Studies and more 17